Link Analysis
... § Since that eventful year, APageRank has emerged as the dominant link analysis model – due to its query-independence – its ability to combat spamming – Google’s huge business success. Brin, S. and Page, L. (1998) The Anatomy of a Large-Scale Hypertextual Web Search Engine. In: Seventh Internat ...
... § Since that eventful year, APageRank has emerged as the dominant link analysis model – due to its query-independence – its ability to combat spamming – Google’s huge business success. Brin, S. and Page, L. (1998) The Anatomy of a Large-Scale Hypertextual Web Search Engine. In: Seventh Internat ...
Network Security Threats CERT Centers, Software Engineering Institute Carnegie Mellon University
... Make bastion a pain to use directly Enable all auditing/logging Limit login methods/file access Allow minimal file access to directories ...
... Make bastion a pain to use directly Enable all auditing/logging Limit login methods/file access Allow minimal file access to directories ...
Minimising Anonymity Loss in Anonymity Networks under DoS Attacks
... will actively make the targeted nodes very busy, so as to make them become unresponsive to their peers who seek cooperation to forward messages according to the selected anonymity protocol. E ectively, the target nodes remain cut o very soon indeed (cf. e.g. [24]). Throughout the paper, we refer to ...
... will actively make the targeted nodes very busy, so as to make them become unresponsive to their peers who seek cooperation to forward messages according to the selected anonymity protocol. E ectively, the target nodes remain cut o very soon indeed (cf. e.g. [24]). Throughout the paper, we refer to ...
Copy area
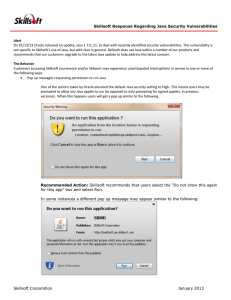
... running on their computer, and if necessary coordinate upgrades with their IT Departments. Skillsoft continually researches new technology that can be leveraged to provide the most compelling and engaging interactions for our users with our products. And while Skillsoft has not formally established ...
... running on their computer, and if necessary coordinate upgrades with their IT Departments. Skillsoft continually researches new technology that can be leveraged to provide the most compelling and engaging interactions for our users with our products. And while Skillsoft has not formally established ...
Risk Assessment: Intercepting VoIP Calls
... The standard pure VoIP architecture is based on a set of IP phones, hardware or software telephones operating over the IP protocol, interconnected by an internet; the IP network can be connected to a traditional phone system (PSTN) by means of a VoIP gateway, transforming VoIP calls and conversation ...
... The standard pure VoIP architecture is based on a set of IP phones, hardware or software telephones operating over the IP protocol, interconnected by an internet; the IP network can be connected to a traditional phone system (PSTN) by means of a VoIP gateway, transforming VoIP calls and conversation ...
PDF
... to connect a BYOD device for the first time. Users must register his or her device using existing Active Directory credentials. During the registration, information about the user’s device, such as its MAC address/ DHCP unique identifier (DUID) and other metadata, are captured through auto-detection ...
... to connect a BYOD device for the first time. Users must register his or her device using existing Active Directory credentials. During the registration, information about the user’s device, such as its MAC address/ DHCP unique identifier (DUID) and other metadata, are captured through auto-detection ...
Marina Papatriantafilou – Application layer
... • cached entries may be out-of-date (best effort name-to-address translation!) – if name host changes IP address, may not be known ...
... • cached entries may be out-of-date (best effort name-to-address translation!) – if name host changes IP address, may not be known ...
Ignify eCommerce Server Configuration
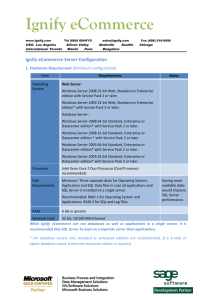
... 5. Ignify eCommerce Deployment Scenarios Ignify eCommerce can be deployed in different scenarios based on your requirements. 1. Web Farm Deployment (Recommended configuration) – Ignify eCommerce Store runs on a load balanced web farm in DMZ. Ignify eCommerce Manager and Services Web Site can run on ...
... 5. Ignify eCommerce Deployment Scenarios Ignify eCommerce can be deployed in different scenarios based on your requirements. 1. Web Farm Deployment (Recommended configuration) – Ignify eCommerce Store runs on a load balanced web farm in DMZ. Ignify eCommerce Manager and Services Web Site can run on ...
Bridgeworks Schools - Bridgeborn Developer Portal
... • Tie in other del.icio.us service outputs to the viz – Create a right-click menu, that when clicked on a given user: • Pops-up his/her top 10 most recent tags • Pops-up his/her top 25 tags as a tag cloud ...
... • Tie in other del.icio.us service outputs to the viz – Create a right-click menu, that when clicked on a given user: • Pops-up his/her top 10 most recent tags • Pops-up his/her top 25 tags as a tag cloud ...
Solving remote access problems
... • Receive connect from PFL and verify access to resource is allowed • Connect to application server using selected protocol • Act as network layer gateway • Send data back to PFL over SSL ...
... • Receive connect from PFL and verify access to resource is allowed • Connect to application server using selected protocol • Act as network layer gateway • Send data back to PFL over SSL ...
Lab1Overview - ECE Users Pages
... corrections/suggestions. General suggestions like add tool xyz to do more capable scanning will not be awarded extras points even if the statement is totally true. Specific text that could be cut and pasted into this lab, completed exercises, and completed solutions may be awarded additional credit. ...
... corrections/suggestions. General suggestions like add tool xyz to do more capable scanning will not be awarded extras points even if the statement is totally true. Specific text that could be cut and pasted into this lab, completed exercises, and completed solutions may be awarded additional credit. ...
Firewall Evolution
... Packet filter firewalls were followed not long afterward by stateful firewalls. These second generation firewalls had the same capabilities as packet filter firewalls, but they monitored and stored the session and connection state. They associated related packets in a flow based on source and destin ...
... Packet filter firewalls were followed not long afterward by stateful firewalls. These second generation firewalls had the same capabilities as packet filter firewalls, but they monitored and stored the session and connection state. They associated related packets in a flow based on source and destin ...
A Proxy For All Your Semantic Needs Vladislav D. Veksler Alex Grintsvayg
... be redesigned if a need for using a new MSR arises. Second, it is not uncommon for researchers to compare various MSRs (e.g. Kaur & Hornof, 2005). Third, MSRs can be used in complement with each other. We are currently exploring the possibility that average MSR scores may actually be more accurate t ...
... be redesigned if a need for using a new MSR arises. Second, it is not uncommon for researchers to compare various MSRs (e.g. Kaur & Hornof, 2005). Third, MSRs can be used in complement with each other. We are currently exploring the possibility that average MSR scores may actually be more accurate t ...
The Evolution of Malicious Agents - Cyber Defense
... trust relationships, and weak user passwords have been frequently exploited to gain unauthorized access to a networked system. If a worm-like agent is programmed to take advantage of several common software vulnerabilities, it will have the ability to rapidly propagate itself across the victim’s net ...
... trust relationships, and weak user passwords have been frequently exploited to gain unauthorized access to a networked system. If a worm-like agent is programmed to take advantage of several common software vulnerabilities, it will have the ability to rapidly propagate itself across the victim’s net ...
Oracle AQADM Privilege Elevation Vulnerability
... Imperva’s Application Defense Center is conducting an extensive research of the Oracle DBMS and Oracle packages. As part of the research the team has identified a privilege elevation vulnerability in the DBMS_AQADM_SYS package. ...
... Imperva’s Application Defense Center is conducting an extensive research of the Oracle DBMS and Oracle packages. As part of the research the team has identified a privilege elevation vulnerability in the DBMS_AQADM_SYS package. ...
McAfee Labs: Combating Aurora
... Data Execution Prevention (DEP) is a set of hardware and software technologies that perform additional checks on memory to help prevent malicious code from running on a system. In Microsoft Windows XP Service Pack 2 (SP2) and Microsoft Windows XP Tablet PC Edition 2005, DEP is enforced by hardware ...
... Data Execution Prevention (DEP) is a set of hardware and software technologies that perform additional checks on memory to help prevent malicious code from running on a system. In Microsoft Windows XP Service Pack 2 (SP2) and Microsoft Windows XP Tablet PC Edition 2005, DEP is enforced by hardware ...
交大資工蔡文能計概
... – Network part all zeros : Means the host on this network – 255.255.255.255 : Means limited broadcast. Used as a destination address to send packets to all hosts on the local network where the source is. – 0.0.0.0 : Means this host, used by machines as source address when they boot up (if they don’t ...
... – Network part all zeros : Means the host on this network – 255.255.255.255 : Means limited broadcast. Used as a destination address to send packets to all hosts on the local network where the source is. – 0.0.0.0 : Means this host, used by machines as source address when they boot up (if they don’t ...
OSI Defense in Depth to Increase Application Security
... Access control is in place when only authorized personnel are allowed physical access to computers and the network. This concept includes permitting only authorized personnel to possess logins and passwords and closing unmanaged wall ports which, if open, could provide unauthorized persons access to ...
... Access control is in place when only authorized personnel are allowed physical access to computers and the network. This concept includes permitting only authorized personnel to possess logins and passwords and closing unmanaged wall ports which, if open, could provide unauthorized persons access to ...
How to test an IPS
... possible to confuse IPS by adding out of session packets or messing established connections. Such techniques are implemented in [fragrouter] which behaves like a router and performs most fragmentation techniques discussed above. However, it is mandatory to make sure that exploits sent through the fr ...
... possible to confuse IPS by adding out of session packets or messing established connections. Such techniques are implemented in [fragrouter] which behaves like a router and performs most fragmentation techniques discussed above. However, it is mandatory to make sure that exploits sent through the fr ...
Organizations That Use TLS/SSL
... or Medicaid, is covered by the Health Insurance Portability and Accountability Act (HIPAA) and must meet certain security standards. Additionally, any organization that stores or transmits user login or patient information may need to be compliant with the HIPAA Security Standard, even if it is not ...
... or Medicaid, is covered by the Health Insurance Portability and Accountability Act (HIPAA) and must meet certain security standards. Additionally, any organization that stores or transmits user login or patient information may need to be compliant with the HIPAA Security Standard, even if it is not ...
Recurrent Security Gaps In 802.11ac Routers
... shared key, or the default four keys which makes it easy to determine the number of plaintext messages encrypted with the same key. The challenge-response scheme used in shared key authentication can lead to man-in-the-middle attack. Manin-the-middle attacks set up illegitimate access points within ...
... shared key, or the default four keys which makes it easy to determine the number of plaintext messages encrypted with the same key. The challenge-response scheme used in shared key authentication can lead to man-in-the-middle attack. Manin-the-middle attacks set up illegitimate access points within ...