Communicating over the Network - Seneca
... – Commonly referred to as hosts (source or destination of a message) – Each host has an address that will identify it on the network – Role of end devices: • Client (software installed so they can request & display info from the ...
... – Commonly referred to as hosts (source or destination of a message) – Each host has an address that will identify it on the network – Role of end devices: • Client (software installed so they can request & display info from the ...
Chapter 2
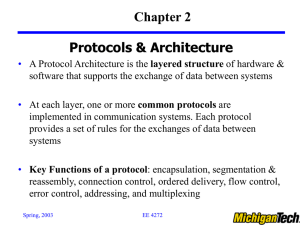
... layers, each with its own functions and protocols Premise of model is information sent from one host is translated and encoded through various layers, from Application layer to Physical layer Physical layer initiates transmission to receiver Receiver translates and decodes message by processin ...
... layers, each with its own functions and protocols Premise of model is information sent from one host is translated and encoded through various layers, from Application layer to Physical layer Physical layer initiates transmission to receiver Receiver translates and decodes message by processin ...
1.Physical Layer & Data Link Layer
... "discovered" at Queensland University of Technology AusCERT Reference #: AA-2004.02 Intrinsic property of wireless model of a shared communications channel AusCERT "recommend(s) that the application of wireless technology should be precluded from use in safety, critical infrastructure and/or o ...
... "discovered" at Queensland University of Technology AusCERT Reference #: AA-2004.02 Intrinsic property of wireless model of a shared communications channel AusCERT "recommend(s) that the application of wireless technology should be precluded from use in safety, critical infrastructure and/or o ...
VIP-172AL IP DoorPhone/Intercom
... Valcom, Inc. warrants its products only to the original purchaser, for its own use, to be free from defects in materials and workmanship under conditions of normal use and service for a period of one year from the date of shipment. This Limited Warranty obligation shall be limited to the replacement ...
... Valcom, Inc. warrants its products only to the original purchaser, for its own use, to be free from defects in materials and workmanship under conditions of normal use and service for a period of one year from the date of shipment. This Limited Warranty obligation shall be limited to the replacement ...
Position Description
... The NIRSA member serving as the Member Network Regional Representative is elected by majority vote through the Regional Representative Elections Process, which is initiated and conducted by the Regional Nominations and Appointments Committee. Term of appointment is two years, beginning May 1 with Re ...
... The NIRSA member serving as the Member Network Regional Representative is elected by majority vote through the Regional Representative Elections Process, which is initiated and conducted by the Regional Nominations and Appointments Committee. Term of appointment is two years, beginning May 1 with Re ...
Sample – Firewall PowerPoint
... Continue to manage the firewall after installation -- it’s not a “set it & forget it” tool Security of distributed systems is only as strong as the security of the weakest system on the network. ...
... Continue to manage the firewall after installation -- it’s not a “set it & forget it” tool Security of distributed systems is only as strong as the security of the weakest system on the network. ...
William Stallings Data and Computer Communications
... Some common service example: • Different Priorities for Different messages • Quality of Service Guarantee Minimum acceptable throughput Maximum acceptable delay ...
... Some common service example: • Different Priorities for Different messages • Quality of Service Guarantee Minimum acceptable throughput Maximum acceptable delay ...
methods of artificial intelligence used in food industry optimization
... diferente targets there are diferent AI methods suitable to be used. For example there are problems wich can not be converted in methemetical methods; in this casethe most eficient method is ANN (artificial neural networks). In other cases it is possible to build a knowledge base; so it is very usef ...
... diferente targets there are diferent AI methods suitable to be used. For example there are problems wich can not be converted in methemetical methods; in this casethe most eficient method is ANN (artificial neural networks). In other cases it is possible to build a knowledge base; so it is very usef ...
Communication Systems - University of Illinois Facilities and Services
... cable and 89 miles of underground fiber optic cable to form a high-speed, multiservice, multi-vendor communications transmission system. AE Requirements: New construction and major remodeling or renovation projects will require the services of a Registered Communications Distribution Designer (RCDD) ...
... cable and 89 miles of underground fiber optic cable to form a high-speed, multiservice, multi-vendor communications transmission system. AE Requirements: New construction and major remodeling or renovation projects will require the services of a Registered Communications Distribution Designer (RCDD) ...
Y. Han, and D.J. Perreault, Analysis and Design of High Efficiency Matching Networks, IEEE Transactions on Power Electronics , Vol. 21, No. 5, Sept. 2006, pp. 1484-1491.
... matching network is a passive two-port circuit designed to provide narrow-band impedance and voltage transformation between the two ports. While most widely associated with communications applications [1]–[3] matching networks also find useful application in resonant inverters, rectifiers, and dc-dc ...
... matching network is a passive two-port circuit designed to provide narrow-band impedance and voltage transformation between the two ports. While most widely associated with communications applications [1]–[3] matching networks also find useful application in resonant inverters, rectifiers, and dc-dc ...
Network Deployment Guide for NovoPRO
... NovoPRO has three network connection types, Ethernet, WiFi Client, and WiFi Hotspot. A) Ethernet – NovoPRO can be plugged into your Ethernet via its RJ45 port. Namely, you can connect NovoPRO to your organization’s backbone network. It is recommended to use Ethernet connection (when possible) since ...
... NovoPRO has three network connection types, Ethernet, WiFi Client, and WiFi Hotspot. A) Ethernet – NovoPRO can be plugged into your Ethernet via its RJ45 port. Namely, you can connect NovoPRO to your organization’s backbone network. It is recommended to use Ethernet connection (when possible) since ...
2 Network topology
... In local area networks with a star topology, each network host is connected to a central hub with a point-to-point connection. In Star topology every node (computer workstation or any other peripheral) is connected to central node called hub or switch. The switch is the server and the peripherals ar ...
... In local area networks with a star topology, each network host is connected to a central hub with a point-to-point connection. In Star topology every node (computer workstation or any other peripheral) is connected to central node called hub or switch. The switch is the server and the peripherals ar ...
rf and microwave engineering
... Chapter – I : Advanced digital filter design techniques : Multiple band optimal FIR filters – design of filters with simultaneous constraints in time and frequency response, optimization methods for designing IIR filters, comparison of optimum FIR filters and delay equalized elliptic filters. Chapte ...
... Chapter – I : Advanced digital filter design techniques : Multiple band optimal FIR filters – design of filters with simultaneous constraints in time and frequency response, optimization methods for designing IIR filters, comparison of optimum FIR filters and delay equalized elliptic filters. Chapte ...
Control System Specification
... network data, message tags, and hardware related parameters. 2.15. Device Resource File: A device’s detailed information file describing any specific interfaces, ...
... network data, message tags, and hardware related parameters. 2.15. Device Resource File: A device’s detailed information file describing any specific interfaces, ...
An Overview of Broadband Over Power Line
... • Power lines are our most ubiquitous infrastructure • Lower cost of deployment – Existing wires ...
... • Power lines are our most ubiquitous infrastructure • Lower cost of deployment – Existing wires ...
Lesson 8
... Denial of service – actions that prevent the system from functioning in accordance with its intended purpose. A piece of equipment may be rendered inoperable or forced to operate in a degraded state. Traffic analysis – a form of passive attack in which an intruder observes information about calls an ...
... Denial of service – actions that prevent the system from functioning in accordance with its intended purpose. A piece of equipment may be rendered inoperable or forced to operate in a degraded state. Traffic analysis – a form of passive attack in which an intruder observes information about calls an ...
When Failure is NOT an Option
... Summary Although there are a variety of Ethernet-based or USB-based devices in the market, they are more for consumer, commercial, or enterprise type equipment that thrive only in indoor or air conditioned environments. Most industrial application measurement devices are still being developed by dev ...
... Summary Although there are a variety of Ethernet-based or USB-based devices in the market, they are more for consumer, commercial, or enterprise type equipment that thrive only in indoor or air conditioned environments. Most industrial application measurement devices are still being developed by dev ...
Md. Zahirul Islam
... Communication systems transmit information from a transmitter to a receiver through the construction of a time- varying physical quantity or a signal. A familiar example of such a system is a wired electronic communication in which information is conveyed from the transmitter by sending an electrica ...
... Communication systems transmit information from a transmitter to a receiver through the construction of a time- varying physical quantity or a signal. A familiar example of such a system is a wired electronic communication in which information is conveyed from the transmitter by sending an electrica ...
VLC
... Similar solution can be used in signal processing domain for VLC The user can be transferred from one light source to another in the area that is under the coverage of both ...
... Similar solution can be used in signal processing domain for VLC The user can be transferred from one light source to another in the area that is under the coverage of both ...
ps3.e.7. all-optical fo-cdma network
... whereas for OOC, it is one transmitter of wavelength 1550 nm and cross correlation plots are obtained respectively, for W/T SPR codes. Further a detailed study is under progress on and 1550.1 nm. The optical pulses from two transmitters are passed similar lines as that of OOCs codes and to compare t ...
... whereas for OOC, it is one transmitter of wavelength 1550 nm and cross correlation plots are obtained respectively, for W/T SPR codes. Further a detailed study is under progress on and 1550.1 nm. The optical pulses from two transmitters are passed similar lines as that of OOCs codes and to compare t ...
A Frequency Quadrupling Optical mm-Wave Generation
... multiplication over sextupling can reduce the requirements dramatically. However, strict demands on the large RF drive power and complex phase matching between the RF drive signal [17]–[21] are required in the frequency multiplication over sextupling. In addition, in the frequency multiplication ove ...
... multiplication over sextupling can reduce the requirements dramatically. However, strict demands on the large RF drive power and complex phase matching between the RF drive signal [17]–[21] are required in the frequency multiplication over sextupling. In addition, in the frequency multiplication ove ...
cs2302 computer networks
... Both the devices A and B are formed by the framed architecture. And the intermediate nodes only having the layers are physical, Datalink and network. In every device each layer gets the services from the layer just below to it. When the device is connected to some other device the layer of one devic ...
... Both the devices A and B are formed by the framed architecture. And the intermediate nodes only having the layers are physical, Datalink and network. In every device each layer gets the services from the layer just below to it. When the device is connected to some other device the layer of one devic ...
IOSR Journal of Computer Engineering (IOSR-JCE)
... In [4], author has proposed a method to detect black hole attack using learning automata. Learning automata is a machine which operates in a random environment. It tries to learn adopting itself with the environment, using feedback. Each automaton has a finite set of actions and each action has a ce ...
... In [4], author has proposed a method to detect black hole attack using learning automata. Learning automata is a machine which operates in a random environment. It tries to learn adopting itself with the environment, using feedback. Each automaton has a finite set of actions and each action has a ce ...
iPhone iPad Essential - 5 S2017.key
... enough of users that they can compete with the phone carriers texting ...
... enough of users that they can compete with the phone carriers texting ...
IMPLEMENTATION OF WIRELESS HART TECHNOLOGY FOR LIQUID LEVEL CONTROL AND MONITORING
... TSMP stands for Time Synchronized Mesh Protocol. it was developed by Dust Networks as a communication protocol for selforganizing networks of wireless devices called motes. TSMP devices stay synchronized to each other and communicate in timeslots, also to other TDM (time/division multiplexing) syste ...
... TSMP stands for Time Synchronized Mesh Protocol. it was developed by Dust Networks as a communication protocol for selforganizing networks of wireless devices called motes. TSMP devices stay synchronized to each other and communicate in timeslots, also to other TDM (time/division multiplexing) syste ...