Unix File System
... Ext2fs does not use fragments; it performs its allocations in smaller units: The default block size on ext2fs is 1Kb, although 2Kb and 4Kb blocks are also supported. ...
... Ext2fs does not use fragments; it performs its allocations in smaller units: The default block size on ext2fs is 1Kb, although 2Kb and 4Kb blocks are also supported. ...
Linux - Spider
... Bin -- contains the basic system binaries Dev -- all the device entries Etc -- can't think of any other place to put it Home -- where all the users live Lib -- system libraries Mnt -- place to mount filesystems Proc -- system information Root -- the root user's home Sbin -- system binaries Usr -- wh ...
... Bin -- contains the basic system binaries Dev -- all the device entries Etc -- can't think of any other place to put it Home -- where all the users live Lib -- system libraries Mnt -- place to mount filesystems Proc -- system information Root -- the root user's home Sbin -- system binaries Usr -- wh ...
ARM Based Customizing an Operating System for the Single Board
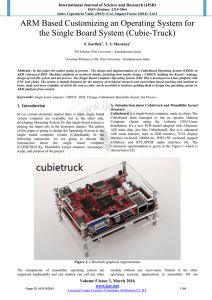
... Cubieboard is a single-board computer, made in china. The Cubieboard team managed to run an Apache Hadoop Computer cluster using the Lubuntu GNU/Linux distribution. It's a new PCB model adopted with Allwinner A20 main chip, just like Cubieboard2. But it is enhanced with some features, such as 2GB me ...
... Cubieboard is a single-board computer, made in china. The Cubieboard team managed to run an Apache Hadoop Computer cluster using the Lubuntu GNU/Linux distribution. It's a new PCB model adopted with Allwinner A20 main chip, just like Cubieboard2. But it is enhanced with some features, such as 2GB me ...
Operating Systems Principles Lecture 1: Introduction
... The Third Generation (1965–1980) ICs and Multiprogramming Time Sharing Technique A variant of multiprogramming technique. Each user has an on-line terminal. Because the user is present and interacting with the computer, the computer system must respond quickly to user requests, otherwise us ...
... The Third Generation (1965–1980) ICs and Multiprogramming Time Sharing Technique A variant of multiprogramming technique. Each user has an on-line terminal. Because the user is present and interacting with the computer, the computer system must respond quickly to user requests, otherwise us ...
Best-Effort Multimedia Networking Outline
... OS as government: protecting users from each other, allocating resources efficiently and fairly, and providing secure and safe communication OS as complex system: keeping OS design and implementation as simple as possible is the key to getting the OS to work ...
... OS as government: protecting users from each other, allocating resources efficiently and fairly, and providing secure and safe communication OS as complex system: keeping OS design and implementation as simple as possible is the key to getting the OS to work ...
Linux Kernel—File Systems
... Use buffer cache management by performing readaheads: when a block has to be read, the kernel code requests the I/O on several contiguous blocks. Block groups are used to cluster together related inodes and data. This will reduce the disk head seeks made when the kernel reads an inode and its data b ...
... Use buffer cache management by performing readaheads: when a block has to be read, the kernel code requests the I/O on several contiguous blocks. Block groups are used to cluster together related inodes and data. This will reduce the disk head seeks made when the kernel reads an inode and its data b ...
Chapter 9 Linux Installation Procedures
... password twice to protect against typing errors. • There are advantages and disadvantages in creating user accounts during the installation. • Understanding these will help any administrator determine which is best based on the security implementations that have been planned. ...
... password twice to protect against typing errors. • There are advantages and disadvantages in creating user accounts during the installation. • Understanding these will help any administrator determine which is best based on the security implementations that have been planned. ...
Unit-5 - Ipemgzb.ac.in
... the major design goal of UNIX compatibility. Its history has been one of collaboration by many users from all around the world, corresponding almost exclusively over the Internet. It has been designed to run efficiently and reliably on common PC hardware, but also runs on a variety of other platform ...
... the major design goal of UNIX compatibility. Its history has been one of collaboration by many users from all around the world, corresponding almost exclusively over the Internet. It has been designed to run efficiently and reliably on common PC hardware, but also runs on a variety of other platform ...
Najwa Knefati operating system chapter 1
... 2- The controller starts the transfer of data from the device to its local buffer. 3- The device controller informs the device driver via an interrupt that it has finished its operation. 4- Device driver then returns control to the OS, possibly returning the data or a pointer to the data if the oper ...
... 2- The controller starts the transfer of data from the device to its local buffer. 3- The device controller informs the device driver via an interrupt that it has finished its operation. 4- Device driver then returns control to the OS, possibly returning the data or a pointer to the data if the oper ...
Operating Systems
... To handle multiple processes and jobs, the process manager uses queues (waiting lists). A job control block or process control block is associated with each job or process. This is a block of memory that stores information about that job or process. The process manager stores the job or process cont ...
... To handle multiple processes and jobs, the process manager uses queues (waiting lists). A job control block or process control block is associated with each job or process. This is a block of memory that stores information about that job or process. The process manager stores the job or process cont ...
Linux-by-Blane-Adcock-Bryan-Knehr-Kevin-Estep-Jason
... – Total time the process has been in the system ...
... – Total time the process has been in the system ...
Lecture 11
... The major burden of program execution has been shifted from the multiuser system to individual clients connected to the server through network. The server may have no direct user facilities of its own, other than those required for management of the system. The server provides file services, print s ...
... The major burden of program execution has been shifted from the multiuser system to individual clients connected to the server through network. The server may have no direct user facilities of its own, other than those required for management of the system. The server provides file services, print s ...
Operating Systems - Metcalfe County Schools
... Must have a NIC Must have the following to send and receive in a network – IP (Internet Protocol) • identifies the computer on the network ...
... Must have a NIC Must have the following to send and receive in a network – IP (Internet Protocol) • identifies the computer on the network ...
Slide 1
... The major burden of program execution has been shifted from the multiuser system to individual clients connected to the server through network. The server may have no direct user facilities of its own, other than those required for management of the system. The server provides file services, print s ...
... The major burden of program execution has been shifted from the multiuser system to individual clients connected to the server through network. The server may have no direct user facilities of its own, other than those required for management of the system. The server provides file services, print s ...
chen-01
... Transparency: To hide the act that its processes and resources are physically distributed across ...
... Transparency: To hide the act that its processes and resources are physically distributed across ...
Chapter 2: Operating-System Structures • Operating-System
... except size, called minidisks in IBM’s VM. The sum of the sizes of all minidisks must be less than the actual amount of physical disk space available. Operating System Concepts ...
... except size, called minidisks in IBM’s VM. The sum of the sizes of all minidisks must be less than the actual amount of physical disk space available. Operating System Concepts ...
Protection in General-Purpose Operating Systems
... Segmentation divides a program into separate pieces. Each piece has a logical unity, a relationship among all of its code or data value. Segmentation was developed as a feasible means to have the effect of an unbounded number of base/bounds registers: a program could be divided into many pieces havi ...
... Segmentation divides a program into separate pieces. Each piece has a logical unity, a relationship among all of its code or data value. Segmentation was developed as a feasible means to have the effect of an unbounded number of base/bounds registers: a program could be divided into many pieces havi ...
UNIX Operating System
... UNIX Operating System Makefile Make goes through the makefile (descriptor) file first starting with the target it is going to create. Make looks at each of the target’s dependencies to see if they are listed as targets. It follows the chain of dependencies until it reaches the end of the chain and ...
... UNIX Operating System Makefile Make goes through the makefile (descriptor) file first starting with the target it is going to create. Make looks at each of the target’s dependencies to see if they are listed as targets. It follows the chain of dependencies until it reaches the end of the chain and ...
PPT
... User app main program; calls kernel for services OS main program; calls user programs as subroutines ...
... User app main program; calls kernel for services OS main program; calls user programs as subroutines ...
Linux Booting Procedure
... intended for normal users. Commands run by LINUX. proc - This filesystem is not on a disk. It is a virtual filesystem that exists in the kernels imagination which is memory ...
... intended for normal users. Commands run by LINUX. proc - This filesystem is not on a disk. It is a virtual filesystem that exists in the kernels imagination which is memory ...
Operating System Architecture and Distributed Systems
... system systems. If performance, rather than portability is goal, then middleware may use facilities of MK directly. ...
... system systems. If performance, rather than portability is goal, then middleware may use facilities of MK directly. ...
Operating System
... – map: points to the map file used by LILO internally during bootup. – install: is one of the files used internally by LILO during the boot process. This holds both the primary and secondary parts of the boot loader. A segment of this boot.b file is written to the MBR (the primary part of the boot l ...
... – map: points to the map file used by LILO internally during bootup. – install: is one of the files used internally by LILO during the boot process. This holds both the primary and secondary parts of the boot loader. A segment of this boot.b file is written to the MBR (the primary part of the boot l ...
Operating System
... CPU utilization and then the interactive computing was introduced. Linus, Torvalds, a Finnish student, developed an ultra small Unix, called Linux, that could easily fit on a personal computer. Linux has a modular design ensuring high dependability and portability. Time-shared systems allowed multip ...
... CPU utilization and then the interactive computing was introduced. Linus, Torvalds, a Finnish student, developed an ultra small Unix, called Linux, that could easily fit on a personal computer. Linux has a modular design ensuring high dependability and portability. Time-shared systems allowed multip ...
Lecture 6
... abnormally (indicating error) – I/O operations - A running program may require I/O, which may involve a file or an I/O device ...
... abnormally (indicating error) – I/O operations - A running program may require I/O, which may involve a file or an I/O device ...
Plan 9 from Bell Labs
.png?width=300)
Plan 9 from Bell Labs is a distributed operating system, originally developed by the Computing Sciences Research Center at Bell Labs between the mid-1980s and 2002. It takes some of the principles of Unix, developed in the same research group, but extends these to a networked environment with graphics terminals.In Plan 9, virtually all computing resources, including files, network connections, and peripheral devices, are represented through the file system rather than specialized interfaces. A unified network protocol called 9P ties a network of computers running Plan 9 together, allowing them to share all resources so represented.The name Plan 9 from Bell Labs is a reference to the Ed Wood 1959 cult science fiction Z-movie Plan 9 from Outer Space. Also, Glenda, the Plan 9 Bunny, is presumably a reference to Wood's film Glen or Glenda. The system continues to be used and developed by operating system researchers and hobbyists.