Datasheet CEX2 - arcutronix GmbH
... The integrated Ethernet OAM test functions monitors single hops or end-to-end connections.Transport of traditional leased line services and IP/Ethernet by using a single access link to a remote location. ...
... The integrated Ethernet OAM test functions monitors single hops or end-to-end connections.Transport of traditional leased line services and IP/Ethernet by using a single access link to a remote location. ...
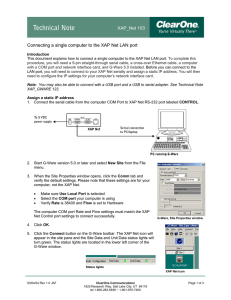
Connecting a Single Computer to the XAP Net LAN Port
... connects, a XAP Net icon appears in the Site pane. The Site Data and Unit Data status lights in the lower left corner of the G-Ware window will turn green. To make a crossover Ethernet cable An Ethernet crossover cable is an unshielded twisted pair Category 5 (UTP-CAT 5) network cable. The XAP Net h ...
... connects, a XAP Net icon appears in the Site pane. The Site Data and Unit Data status lights in the lower left corner of the G-Ware window will turn green. To make a crossover Ethernet cable An Ethernet crossover cable is an unshielded twisted pair Category 5 (UTP-CAT 5) network cable. The XAP Net h ...
Packet Transport Network in BSNL 11-04-13
... Multi-Protocol Label Switching (MPLS) technology that intends to provide the basis for the next generation Packet Transport Network. The fundamental idea of this activity is to extend MPLS where necessary with operations, Administration and Maintenance (OAM) tools that are widely applied in existing ...
... Multi-Protocol Label Switching (MPLS) technology that intends to provide the basis for the next generation Packet Transport Network. The fundamental idea of this activity is to extend MPLS where necessary with operations, Administration and Maintenance (OAM) tools that are widely applied in existing ...
comp412p1
... • Topology: How the devices in the network (called nodes) are arranged – Star networks: A network that uses a host device connected directly to several other devices – Bus networks: A network consisting of a central cable to which all network devices are attached – Mesh networks: A network in which ...
... • Topology: How the devices in the network (called nodes) are arranged – Star networks: A network that uses a host device connected directly to several other devices – Bus networks: A network consisting of a central cable to which all network devices are attached – Mesh networks: A network in which ...
Chapter 8 Internet Protocols
... network from the point of view of the rest of internet • Each subnet is assigned a subnet number • Host portion of address partitioned into subnet number and host number • Local routers route within subnetted network • Subnet mask indicates which bits are network/subnet number and which are host num ...
... network from the point of view of the rest of internet • Each subnet is assigned a subnet number • Host portion of address partitioned into subnet number and host number • Local routers route within subnetted network • Subnet mask indicates which bits are network/subnet number and which are host num ...
Slides Pajek 2.05
... There exist two global views: reduction and hierarchy. Reduction means that we consider all vertices in a cluster as a new vertex – all vertices in a cluster are shrunk to one compound vertex. Even more general global view is hierarchy – vertices in network are hierarchically clustered to larger and ...
... There exist two global views: reduction and hierarchy. Reduction means that we consider all vertices in a cluster as a new vertex – all vertices in a cluster are shrunk to one compound vertex. Even more general global view is hierarchy – vertices in network are hierarchically clustered to larger and ...
ppt
... IP solutions: – IP Packet Forwarding – Routing – Routing Vs Forwarding – Address resolution Protocol (ARP) Wireless Networking: Brief Overview ...
... IP solutions: – IP Packet Forwarding – Routing – Routing Vs Forwarding – Address resolution Protocol (ARP) Wireless Networking: Brief Overview ...
PDF - This Chapter
... ATM adaptation layer. Service-dependent sublayer of the data link layer. The AAL accepts data from different applications and presents it to the ATM layer in the form of 48-byte ATM payload segments. AALs consist of two sublayers:the convergence sublayer and the segmentation and reassembly sublayer. ...
... ATM adaptation layer. Service-dependent sublayer of the data link layer. The AAL accepts data from different applications and presents it to the ATM layer in the form of 48-byte ATM payload segments. AALs consist of two sublayers:the convergence sublayer and the segmentation and reassembly sublayer. ...
Training - Personal.psu.edu
... A network topology is the geometric arrangement of nodes and cable links in a LAN, and is used in two general configurations: bus and star. These two topologies define how nodes are connected to one another. A node is an active device connected to the network, such as a computer or a printer. A node ...
... A network topology is the geometric arrangement of nodes and cable links in a LAN, and is used in two general configurations: bus and star. These two topologies define how nodes are connected to one another. A node is an active device connected to the network, such as a computer or a printer. A node ...
Chapter 19 - William Stallings, Data and Computer
... some members of group may not require delivery from particular source over given time some group members may only be able to handle a portion of the transmission reservation means routers can decide in advance if can meet requirements ...
... some members of group may not require delivery from particular source over given time some group members may only be able to handle a portion of the transmission reservation means routers can decide in advance if can meet requirements ...
Networking-1
... From Layer X’s perspective, the higher-layer headers and the user data form one large data field. Layer(s) ...
... From Layer X’s perspective, the higher-layer headers and the user data form one large data field. Layer(s) ...
Location of Network Components - SJSU ScholarWorks
... technology that would move this trend forward to the network computer. Sun Microsystems, for example, has recently demonstrated a computer card that looks like a typical credit card, but which allows a computer user to carry his most recent desktop in his wallet. Silicon Graphics is working on techn ...
... technology that would move this trend forward to the network computer. Sun Microsystems, for example, has recently demonstrated a computer card that looks like a typical credit card, but which allows a computer user to carry his most recent desktop in his wallet. Silicon Graphics is working on techn ...
An introduction to NTT ’ s NGN and new services in Japan
... carriers fit fit for forthe thenew newage. age. Be versatile as a service providing company Technical innovation ...
... carriers fit fit for forthe thenew newage. age. Be versatile as a service providing company Technical innovation ...
Virtual Private Networks - Mathematics and Computer Science
... “A virtual private network (VPN) is the extension of a private network that encompasses links across shared or public networks like the Internet.” (Microsoft, 2001) ► It ...
... “A virtual private network (VPN) is the extension of a private network that encompasses links across shared or public networks like the Internet.” (Microsoft, 2001) ► It ...
MultiNet: Connecting to Multiple IEEE 802.11 Networks Using a
... Includes the SSID and operational mode of the wireless network. It is also responsible for handling query and set operations meant for the underlying wireless ...
... Includes the SSID and operational mode of the wireless network. It is also responsible for handling query and set operations meant for the underlying wireless ...
Chp. 4, Part III - comp
... – A will immediately send its updated vector to B, E, F. – This update does not affect B’s routing table. – However, E will update its entry to C from 2 to infinity, and then from infinity to 3; and similarly for F. ...
... – A will immediately send its updated vector to B, E, F. – This update does not affect B’s routing table. – However, E will update its entry to C from 2 to infinity, and then from infinity to 3; and similarly for F. ...
Designing and Building for End-to-End Solutions
... • 6LoWPAN is an acronym of IPv6 – Low power wireless personal area networks • Concluded working group in the internet area of the IETF • To apply for smallest devices and low power devices • Limited processing capabilities should be able to participate within IoT • Defined encapsulation and header c ...
... • 6LoWPAN is an acronym of IPv6 – Low power wireless personal area networks • Concluded working group in the internet area of the IETF • To apply for smallest devices and low power devices • Limited processing capabilities should be able to participate within IoT • Defined encapsulation and header c ...
Coruscations and Requirements for Quality of Services in Mobile Ad
... integration: the traditionally best-effort services, real-time services and controlled link-sharing services. Best-effort services are those we currently experience on the internet. They are characterized by absence of any QoS specifications. The network provides the quality that it actually can con ...
... integration: the traditionally best-effort services, real-time services and controlled link-sharing services. Best-effort services are those we currently experience on the internet. They are characterized by absence of any QoS specifications. The network provides the quality that it actually can con ...
Document
... • Must purchase Internet access from ISP – Specialized providers – Companies that provide other services ...
... • Must purchase Internet access from ISP – Specialized providers – Companies that provide other services ...
Lim-TMC09-slide
... TMSP provides a perfect solution for seamless communications TMSP works for point to point communication software such as VoIP and Video conferencing TMSP does not affect the legacy applications running on a nonTMSP-enabled server One biggest limitation of TMSP is that when MN and CN move an ...
... TMSP provides a perfect solution for seamless communications TMSP works for point to point communication software such as VoIP and Video conferencing TMSP does not affect the legacy applications running on a nonTMSP-enabled server One biggest limitation of TMSP is that when MN and CN move an ...
Week_Four_Network_MIMIC
... IETF Integrated Services Working Group QoS Resource Reservation Protocol (RSVP) is considered a set up protocol used by a host to request specific qualities of service from the network for particular application flow. RSVP is used by routers to deliver QoS requests to other routers along the paths o ...
... IETF Integrated Services Working Group QoS Resource Reservation Protocol (RSVP) is considered a set up protocol used by a host to request specific qualities of service from the network for particular application flow. RSVP is used by routers to deliver QoS requests to other routers along the paths o ...
Computer Networks
... o Between adjacent routers o on LAN one router is elected as designated router o Designated router is adjacent to all neighbouring routers Flooding to all routers in an area Within routers of any area o Construct graph o Compute shortest paths between routers in area Extra for backbone area o ...
... o Between adjacent routers o on LAN one router is elected as designated router o Designated router is adjacent to all neighbouring routers Flooding to all routers in an area Within routers of any area o Construct graph o Compute shortest paths between routers in area Extra for backbone area o ...
Hour 1. What Is TCP/IP
... to the need for offices to share computer resources – Early LAN protocols did not provide Internet access – As the Internet became more popular, LAN provide complete support for TCP/IP. ...
... to the need for offices to share computer resources – Early LAN protocols did not provide Internet access – As the Internet became more popular, LAN provide complete support for TCP/IP. ...
$doc.title
... a. If result is set to 1000 when the read system call returns, what can you conclude about how much data the origin server has already sent your proxy? ...
... a. If result is set to 1000 when the read system call returns, what can you conclude about how much data the origin server has already sent your proxy? ...