paper
... switching (OFS) [8,9] as an attractive candidate network architecture that will help support future traffic growth by providing this desired cost-effective access for end users with large bandwidth demands. OFS is an end-to-end transport service, in that it directly connects source and destination e ...
... switching (OFS) [8,9] as an attractive candidate network architecture that will help support future traffic growth by providing this desired cost-effective access for end users with large bandwidth demands. OFS is an end-to-end transport service, in that it directly connects source and destination e ...
IPv6 - DePaul University
... to a destination and requires special handling by routers. The combination of source address and flow label value uniquely identifies a flow of packets. ...
... to a destination and requires special handling by routers. The combination of source address and flow label value uniquely identifies a flow of packets. ...
IPv6
... Flow represents a sequence of packets from one source to one (unicast, anycast, multicast) destination with special handling requriements for the intermediate routers. • Could be a single TCP connection or multiple connections (think FTP) • Special handling conditions must be set up prior to flow co ...
... Flow represents a sequence of packets from one source to one (unicast, anycast, multicast) destination with special handling requriements for the intermediate routers. • Could be a single TCP connection or multiple connections (think FTP) • Special handling conditions must be set up prior to flow co ...
Introduction Chapter 1
... Tsetup, the signalling message requesting the connection is also placed in a queue at each switch to wait for the required resources to be released . Only when the connection request reaches the head of the queue, and its requested resources are available, will the request be passed on to the next s ...
... Tsetup, the signalling message requesting the connection is also placed in a queue at each switch to wait for the required resources to be released . Only when the connection request reaches the head of the queue, and its requested resources are available, will the request be passed on to the next s ...
datagram network
... Transmission Unit (MTU) bytes of data – But not all link-layer protocols can handle the same size packets • Ethernet handles up to 1500 B frames • Some WAN protocols only handle 500 B frames ...
... Transmission Unit (MTU) bytes of data – But not all link-layer protocols can handle the same size packets • Ethernet handles up to 1500 B frames • Some WAN protocols only handle 500 B frames ...
AG31238244
... neighbors containing information about its neighbors and their link status and received by the nodes which are one hop away but they are not passed on to further nodes. OLSR is designed to work in a completely different manner and does not need to transmission of control messages. Control messages c ...
... neighbors containing information about its neighbors and their link status and received by the nodes which are one hop away but they are not passed on to further nodes. OLSR is designed to work in a completely different manner and does not need to transmission of control messages. Control messages c ...
PPT Version
... – If MNs behind NATs initiate sessions with MM then there will be no NAT traversal problems ...
... – If MNs behind NATs initiate sessions with MM then there will be no NAT traversal problems ...
CHAPTER 0 INTRODUCTION TO TCP/IP
... insert the IP datagram in an Ethernet frame (Ethernet packets are called frames), and transmit the frame on the Ethernet network. However, Ethernet frames do not use IP addresses, but have an addressing scheme that is based on 48 bit long MAC (media access control) addresses. MAC addresses are writt ...
... insert the IP datagram in an Ethernet frame (Ethernet packets are called frames), and transmit the frame on the Ethernet network. However, Ethernet frames do not use IP addresses, but have an addressing scheme that is based on 48 bit long MAC (media access control) addresses. MAC addresses are writt ...
Planning Guide version 6.0
... Nova-network is a simple legacy network manager. It can operate with predefined Private IP spaces only. • If you do not want to split your VMs into isolated groups (tenants), you can choose the Nova-network with FlatDHCP topology. In this case, you will have one big network for all tenants and their ...
... Nova-network is a simple legacy network manager. It can operate with predefined Private IP spaces only. • If you do not want to split your VMs into isolated groups (tenants), you can choose the Nova-network with FlatDHCP topology. In this case, you will have one big network for all tenants and their ...
Document
... Each router on the network decapsulates the IP datagram from the frame it receives, process it, and then encapsulates it in another frame. Format and size depends on the incoming and outgoing physical network. IP datagram must be divided to make it possible to pass through these physical networks. T ...
... Each router on the network decapsulates the IP datagram from the frame it receives, process it, and then encapsulates it in another frame. Format and size depends on the incoming and outgoing physical network. IP datagram must be divided to make it possible to pass through these physical networks. T ...
Intel Research Lablet Research Project Proposal Template
... developers of distributed applications Specify network at a high-level Automatically translate specification into executable Hide everything they don’t want to touch Enjoy performance that is good enough ...
... developers of distributed applications Specify network at a high-level Automatically translate specification into executable Hide everything they don’t want to touch Enjoy performance that is good enough ...
Introduction to BACnet Routers
... messages involve router-to-router communication where both source and destination network addresses are specified in the NCPI. Usually one of the requirements of the network layer is to be able to route messages from one network to another over different paths. However, BACnet is explicit about this ...
... messages involve router-to-router communication where both source and destination network addresses are specified in the NCPI. Usually one of the requirements of the network layer is to be able to route messages from one network to another over different paths. However, BACnet is explicit about this ...
Role of Interface Manipulation Style and Scaffolding on
... adjust priority levels or make more informed routing decisions in response to network congestion and changing traffic patterns. SPIN [Heinzelman, 1999 ] makes adaptive decisions to participate in data dissemination based on current energy levels and the cost of communication. In [Woo and Culler 2001 ...
... adjust priority levels or make more informed routing decisions in response to network congestion and changing traffic patterns. SPIN [Heinzelman, 1999 ] makes adaptive decisions to participate in data dissemination based on current energy levels and the cost of communication. In [Woo and Culler 2001 ...
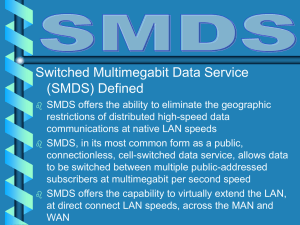
WAN_Unit_8-SMDS
... Access classes are a method of providing bandwidth priorities for times when there is network congestion at the SNI Network congestion occurs when there is an attempt by the network to transfer one or more SMDS data units without an interval of time between the units The access class places a limit ...
... Access classes are a method of providing bandwidth priorities for times when there is network congestion at the SNI Network congestion occurs when there is an attempt by the network to transfer one or more SMDS data units without an interval of time between the units The access class places a limit ...
WiMAX-3GPP Optimized Handover
... ND&S a big issue only for 802.11 networks – Not such a big issue for other networks operating primarily in licensed bands – Inter-RAT Neighbor Advertisements are good enough – Operators skeptical about dedicated IS server ...
... ND&S a big issue only for 802.11 networks – Not such a big issue for other networks operating primarily in licensed bands – Inter-RAT Neighbor Advertisements are good enough – Operators skeptical about dedicated IS server ...
Slide 1
... – Classifier – maps incoming packets into a given class for equal treatment by the packet scheduler – Admission control – determines whether or not a new flow may be established without affecting existing sessions – The ability to mark some packets as eligible for discard under network congestion ...
... – Classifier – maps incoming packets into a given class for equal treatment by the packet scheduler – Admission control – determines whether or not a new flow may be established without affecting existing sessions – The ability to mark some packets as eligible for discard under network congestion ...
Chapter 7 Lecture Presentation
... Routing: mechanisms for determining the set of best paths for routing packets requires the collaboration of network elements Forwarding: transfer of packets from NE inputs to outputs Priority & Scheduling: determining order of packet transmission in each NE ...
... Routing: mechanisms for determining the set of best paths for routing packets requires the collaboration of network elements Forwarding: transfer of packets from NE inputs to outputs Priority & Scheduling: determining order of packet transmission in each NE ...
J045055560
... 3.5 Illustrative example Consider a small network with 5 vertices and 6 edges shown in figure1, where each arc length is represented as a trapezoidal Intuitionistic fuzzy number ...
... 3.5 Illustrative example Consider a small network with 5 vertices and 6 edges shown in figure1, where each arc length is represented as a trapezoidal Intuitionistic fuzzy number ...
Inferring Subnets in Router-Level Topology Collection Studies
... Based on this observation, we use an iterative approach to identify candidate subnets. We first form all candidate /x subnets from the data set by combining the IP addresses whose first x bits match. Next, we recursively form smaller subnets (e.g., /x, /(x+1), . . ., /31 subnets). At this point, we ...
... Based on this observation, we use an iterative approach to identify candidate subnets. We first form all candidate /x subnets from the data set by combining the IP addresses whose first x bits match. Next, we recursively form smaller subnets (e.g., /x, /(x+1), . . ., /31 subnets). At this point, we ...
NETWORK TECHNOLOGIES AND APPLICATIONS
... furnishes transmission protocol knowledge and management and handles errors in the physical layer, flow control and frame synchronization. The data link layer is divided into two sublayers: The Media Access Control (MAC) layer and the Logical Link Control (LLC) layer. The MAC sublayer controls how a ...
... furnishes transmission protocol knowledge and management and handles errors in the physical layer, flow control and frame synchronization. The data link layer is divided into two sublayers: The Media Access Control (MAC) layer and the Logical Link Control (LLC) layer. The MAC sublayer controls how a ...