Document
... – The bit error rate (BER) is the number of bit errors divided by the total number of transferred bits during a studied time interval. BER is a unitless metric for performance measurement and often expressed as a percentage. – In IP network, the traffic stream is based on data packet which may be no ...
... – The bit error rate (BER) is the number of bit errors divided by the total number of transferred bits during a studied time interval. BER is a unitless metric for performance measurement and often expressed as a percentage. – In IP network, the traffic stream is based on data packet which may be no ...
3rd Edition: Chapter 3 - Georgia Institute of Technology
... each datagram carries 1 transport-layer segment each segment has source, destination port number host uses IP addresses & port numbers to direct segment to ...
... each datagram carries 1 transport-layer segment each segment has source, destination port number host uses IP addresses & port numbers to direct segment to ...
Transport and Signaling in the PSTN
... Starting from 1980 (mainly in Europe), CAS was being replaced by SS7. The use of stored program control (SPC) exchanges made this possible. Like CCIS, signalling messages are transmitted over separate signalling channels. Unlike CCIS, SS7 technology is not monolithic, but based on protocol stacks. ...
... Starting from 1980 (mainly in Europe), CAS was being replaced by SS7. The use of stored program control (SPC) exchanges made this possible. Like CCIS, signalling messages are transmitted over separate signalling channels. Unlike CCIS, SS7 technology is not monolithic, but based on protocol stacks. ...
Cisco Unified Fabric with Automation: Acronyms and Abbreviations
... end-host reachability information to the other switches (leaf switches) in the fabric. End-host detection can happen either through ARP or neighbor discovery (ND) or Virtual Station Interface (VSI) Discovery and Configuration Protocol (VDP). When a connected end-host starts and sends an ARP or ND pa ...
... end-host reachability information to the other switches (leaf switches) in the fabric. End-host detection can happen either through ARP or neighbor discovery (ND) or Virtual Station Interface (VSI) Discovery and Configuration Protocol (VDP). When a connected end-host starts and sends an ARP or ND pa ...
Slide presentation with simulation results - OSPF
... – If the router has a lexicographically larger value of (RtrPri, MDR Level, RID) than all of its neighbors, it selects itself as an MDR and selects all MDR neighbors as Dependent Neighbors, and proceeds to Phase 4. – Let Rmax be the neighbor with the lexicographically largest value of (RtrPri, MDR L ...
... – If the router has a lexicographically larger value of (RtrPri, MDR Level, RID) than all of its neighbors, it selects itself as an MDR and selects all MDR neighbors as Dependent Neighbors, and proceeds to Phase 4. – Let Rmax be the neighbor with the lexicographically largest value of (RtrPri, MDR L ...
Diapositiva 1
... mesh node. The subnet assigned to the wireless LAN or hotspot will therefore be the same as with an Ethernet LAN connected to the mesh node. ...
... mesh node. The subnet assigned to the wireless LAN or hotspot will therefore be the same as with an Ethernet LAN connected to the mesh node. ...
Technology Background
... node. If a node does not receive an acknowledgement after forwarding a packet, it sends an acknowledgement request a certain number of times. If no acknowledgement is still received, the node generates a route error message and sends it to the sender of packet that was to be forwarded and to any oth ...
... node. If a node does not receive an acknowledgement after forwarding a packet, it sends an acknowledgement request a certain number of times. If no acknowledgement is still received, the node generates a route error message and sends it to the sender of packet that was to be forwarded and to any oth ...
3rd Edition: Chapter 3 - Communications Systems Center
... each datagram carries 1 transport-layer segment each segment has source, destination port number host uses IP addresses & port numbers to direct segment to ...
... each datagram carries 1 transport-layer segment each segment has source, destination port number host uses IP addresses & port numbers to direct segment to ...
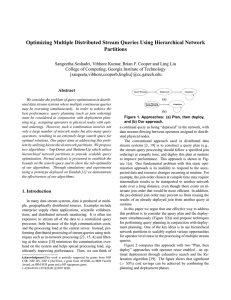
Optimizing Multiple Distributed Stream Queries Using Hierarchical Network Partitions
... data streams flowing between operators assigned to distributed physical nodes. The conventional approach used in distributed data stream systems [3, 19] is to construct a query plan (e.g., the stream query processing should follow a specified join ordering) at compile time, and deploy this plan at r ...
... data streams flowing between operators assigned to distributed physical nodes. The conventional approach used in distributed data stream systems [3, 19] is to construct a query plan (e.g., the stream query processing should follow a specified join ordering) at compile time, and deploy this plan at r ...
PPT - HKU
... How to organize the stack frames (all are in native form now) ? How to make extracted thread states portable and recognizable by the remote JVM ? How to restore the extracted states (rebuild the stack frames) and restart the execution in native form ? Need to modify JIT compiler to instrument native ...
... How to organize the stack frames (all are in native form now) ? How to make extracted thread states portable and recognizable by the remote JVM ? How to restore the extracted states (rebuild the stack frames) and restart the execution in native form ? Need to modify JIT compiler to instrument native ...
Network Layer
... NAT: Network Address Translation Implementation: NAT router must: - outgoing datagrams: replace (source IP address, port #) of every outgoing datagram to (NAT IP address, new port #) ...
... NAT: Network Address Translation Implementation: NAT router must: - outgoing datagrams: replace (source IP address, port #) of every outgoing datagram to (NAT IP address, new port #) ...
Availability and Popularity Measurements of Peer
... recorded the names of files stored by several thousand users of the Napster application in January 2001 and the Gnutella P 2 P file system from March through May of 2002. For the second, we periodically measured the availability of peers on the Gnutella network from March through May of 2002. Our an ...
... recorded the names of files stored by several thousand users of the Napster application in January 2001 and the Gnutella P 2 P file system from March through May of 2002. For the second, we periodically measured the availability of peers on the Gnutella network from March through May of 2002. Our an ...
Collection Tree Protocol
... We assume that the collection layer updates stale routing information by sending control beacons. As with data packets, beacons contain the transmitter’s local cost estimate. Unlike data packets, however, control beacons are broadcasts. A single beacon updates many nearby nodes. Collection protocols ...
... We assume that the collection layer updates stale routing information by sending control beacons. As with data packets, beacons contain the transmitter’s local cost estimate. Unlike data packets, however, control beacons are broadcasts. A single beacon updates many nearby nodes. Collection protocols ...
3rd Edition: Chapter 3
... segments may be: lost delivered out of order to app connectionless: no handshaking between UDP sender, receiver each UDP segment handled independently of others ...
... segments may be: lost delivered out of order to app connectionless: no handshaking between UDP sender, receiver each UDP segment handled independently of others ...
CCNA2 3.1-08 TCPIP Suite Error and Control Messages
... ICMP redirect/change request messages Default gateways only send ICMP redirect/change request messages if the following conditions are met: – The interface on which the packet comes into the router is the same interface on which the packet gets routed out. – The subnet/network of the source IP addr ...
... ICMP redirect/change request messages Default gateways only send ICMP redirect/change request messages if the following conditions are met: – The interface on which the packet comes into the router is the same interface on which the packet gets routed out. – The subnet/network of the source IP addr ...
3rd Edition: Chapter 3
... m no loss of packets r separate FSMs for sender, receiver: m sender sends data into underlying channel m receiver read data from underlying channel ...
... m no loss of packets r separate FSMs for sender, receiver: m sender sends data into underlying channel m receiver read data from underlying channel ...