Layer
... • protocol data unit between customers = letter • service data unit for postal service = letter • protocol data unit = mailbag (aggregation of letters) • (what is the SDU header?) ...
... • protocol data unit between customers = letter • service data unit for postal service = letter • protocol data unit = mailbag (aggregation of letters) • (what is the SDU header?) ...
02_tcom5272_lan
... LANs (VLANs) through microsegmentation Bridges switch use software; switches typically switch using hardware (called the ...
... LANs (VLANs) through microsegmentation Bridges switch use software; switches typically switch using hardware (called the ...
network
... WAN (wide area network) Long distance, low speed connection A series of packet switches, connected by long-distance communication lines User computer attached to packet switches Network is expanded by adding packet switch & communication line ...
... WAN (wide area network) Long distance, low speed connection A series of packet switches, connected by long-distance communication lines User computer attached to packet switches Network is expanded by adding packet switch & communication line ...
File - all.about.gold
... channels are used to transmit data and timing information. The timing channel transmits clock pulses to the receiver. Upon receipt of a clock pulse, the receiver reads the data channel and latches the bit value found on the channel at that moment. The data channel is not read again until the next cl ...
... channels are used to transmit data and timing information. The timing channel transmits clock pulses to the receiver. Upon receipt of a clock pulse, the receiver reads the data channel and latches the bit value found on the channel at that moment. The data channel is not read again until the next cl ...
17.4 IEEE 802.11 MEDIUM ACCESS CONTROL
... Association-Related Services The primary purpose of the MAC layer is to transfer MSDUs between MAC entities; this purpose is fulfilled by the distribution service. For that service to function, it requires information about stations within the ESS that is provided by the association-related services ...
... Association-Related Services The primary purpose of the MAC layer is to transfer MSDUs between MAC entities; this purpose is fulfilled by the distribution service. For that service to function, it requires information about stations within the ESS that is provided by the association-related services ...
Networking Theory (Part 1)
... Interconnection (OSI) model created by the International Standards Organization (ISO) ...
... Interconnection (OSI) model created by the International Standards Organization (ISO) ...
Network protocols
... waits, otherwise it transmits BIT 1102: Communications Technology & the Internet ...
... waits, otherwise it transmits BIT 1102: Communications Technology & the Internet ...
Document
... Interconnection (OSI) model created by the International Standards Organization (ISO) ...
... Interconnection (OSI) model created by the International Standards Organization (ISO) ...
1_hProtocolsOSI
... • This layer is responsible for two main functions – network addressing and routing. • It identifies systems uniquely on an internetwork, and also handles how to get from one part of the network to another. • Most of the network configuration takes place, since protocols such as IP, IPX, and equipme ...
... • This layer is responsible for two main functions – network addressing and routing. • It identifies systems uniquely on an internetwork, and also handles how to get from one part of the network to another. • Most of the network configuration takes place, since protocols such as IP, IPX, and equipme ...
CSC 335 Data Communications and Networking I
... • A node receiving link state packets forwards them to all of its neighbors except the one from which it receives the packet. • As link state packets are exchanged, each node eventually learns about the network topology, the cost, and the status of each link. ...
... • A node receiving link state packets forwards them to all of its neighbors except the one from which it receives the packet. • As link state packets are exchanged, each node eventually learns about the network topology, the cost, and the status of each link. ...
PPT_2
... Hubs are essentially physical-layer repeaters: bits coming from one link go out all other links at the same rate no frame buffering no CSMA/CD at hub: adapters detect collisions provides net management functionality ...
... Hubs are essentially physical-layer repeaters: bits coming from one link go out all other links at the same rate no frame buffering no CSMA/CD at hub: adapters detect collisions provides net management functionality ...
Chord
... node is more important than any other, improves robustness Scalability: logarithmic growth of lookup costs with the number of nodes in the network, even very large systems are feasible Availability: chord automatically adjusts its internal tables to ensure that the node responsible for a key can alw ...
... node is more important than any other, improves robustness Scalability: logarithmic growth of lookup costs with the number of nodes in the network, even very large systems are feasible Availability: chord automatically adjusts its internal tables to ensure that the node responsible for a key can alw ...
Lecture 1 Introduction
... Direct link between routers represented by edge Edge “cost” c(x,y) denotes measure of difficulty of using link E ...
... Direct link between routers represented by edge Edge “cost” c(x,y) denotes measure of difficulty of using link E ...
Fundamentals of Computer Networks
... master and is allowed to transmit. All other machines are required to refrain from sending. • An arbitration mechanism is needed to resolve conflicts when two or more machines want to transmit simultaneously. • IEEE 802.3, popularly called Ethernet is a bus-based broadcast network. • Computers on an ...
... master and is allowed to transmit. All other machines are required to refrain from sending. • An arbitration mechanism is needed to resolve conflicts when two or more machines want to transmit simultaneously. • IEEE 802.3, popularly called Ethernet is a bus-based broadcast network. • Computers on an ...
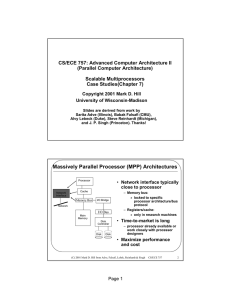
Massively Parallel Processor (MPP) Architectures
... three independent units; one synchronous, 2 asynchronous Synchronous useful for barrier synch Asynchronous useful for passing error conditions independent of other Control unit functions ...
... three independent units; one synchronous, 2 asynchronous Synchronous useful for barrier synch Asynchronous useful for passing error conditions independent of other Control unit functions ...
neural network - WCU Computer Science
... Attribute by attribute, vary xmean to the min and max of that attribute. Find the network output for each variation and compare it to (2). Will discover which attributes the network is more sensitive to ...
... Attribute by attribute, vary xmean to the min and max of that attribute. Find the network output for each variation and compare it to (2). Will discover which attributes the network is more sensitive to ...
Abstract - Chennaisunday.com
... based on Bluetooth devices. Protocol proceeds is device discovery, partitioning of the network into Bluetooth piconets, and interconnection of the piconets into a connected scatternet. It is executed at each node with no prior knowledge of the network topology, thus being fully distributed. The sele ...
... based on Bluetooth devices. Protocol proceeds is device discovery, partitioning of the network into Bluetooth piconets, and interconnection of the piconets into a connected scatternet. It is executed at each node with no prior knowledge of the network topology, thus being fully distributed. The sele ...
Where Have We Been? - Oakton Community College
... • That means media access is controlled on a “first come, first serve” basis. • This results in collisions between the data of two simultaneously transmitting devices. • Collisions are resolved using what method? ...
... • That means media access is controlled on a “first come, first serve” basis. • This results in collisions between the data of two simultaneously transmitting devices. • Collisions are resolved using what method? ...
IEEE 802.11 and NICs
... an RTS control frame to the AP. The RTS frame indicates to the AP and all stations within range, that Vivian wants to reserve the medium for a certain duration of time, message, ACK, and SIFS. The hidden node stations cannot see the RTS. The AP replies to Vivian with a CTS, which all nodes, includin ...
... an RTS control frame to the AP. The RTS frame indicates to the AP and all stations within range, that Vivian wants to reserve the medium for a certain duration of time, message, ACK, and SIFS. The hidden node stations cannot see the RTS. The AP replies to Vivian with a CTS, which all nodes, includin ...
Link Layer
... we learned how to do this already (chapter 3)! seldom used on low bit error link (fiber, some twisted pair) wireless links: high error rates • Q: why both link-level and end-end reliability? 5: DataLink Layer ...
... we learned how to do this already (chapter 3)! seldom used on low bit error link (fiber, some twisted pair) wireless links: high error rates • Q: why both link-level and end-end reliability? 5: DataLink Layer ...