* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Introduction to Healthcare Information Technology
Security-focused operating system wikipedia , lookup
Trusted Computing wikipedia , lookup
Cyber-security regulation wikipedia , lookup
Information privacy law wikipedia , lookup
Information security wikipedia , lookup
Next-Generation Secure Computing Base wikipedia , lookup
Computer security wikipedia , lookup
Mobile security wikipedia , lookup
Medical privacy wikipedia , lookup
HealthCare.gov wikipedia , lookup
Computer and network surveillance wikipedia , lookup
Cryptanalysis wikipedia , lookup
Wireless security wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Social engineering (security) wikipedia , lookup
Post-quantum cryptography wikipedia , lookup
Cryptography wikipedia , lookup
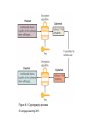
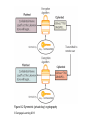
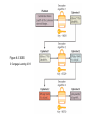
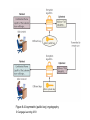
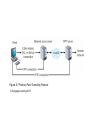
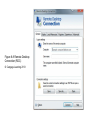
Introduction to Healthcare Information Technology Chapter Eight Advanced Healthcare Information Security Objectives • Define encryption and explain how it can be used to secure information • Describe the vulnerabilities and protections of wireless networks • List the different remote access technologies • Explain how to securely dispose of a document Introduction to Healthcare Information Technology 2 Healthcare IT: Challenges and Opportunities • Properly disseminating protected health information – A growing concern • Solution: apply layers of defense • Encrypting document contents – Second level of protection for important documents • Protecting mobile data – Growing in importance as more data is stored on portable media Introduction to Healthcare Information Technology 3 Encryption • Cryptography – Transforming information into a secure form while it is being transmitted or stored – Information is “scrambled” to prevent unauthorized persons from accessing it Introduction to Healthcare Information Technology 4 Basic Cryptography • Defining cryptography – Origins date back centuries – Used by Julius Caesar • Encryption – Changing the original message into a coded message • Decryption – Decoding the message back to original form • Cleartext data – Data stored or transmitted without encryption Introduction to Healthcare Information Technology 5 Basic Cryptography (cont’d.) • Plaintext – Cleartext data to be encrypted • Algorithm – Procedures based on a mathematical formula used to encrypt the data • Key – Mathematical value entered into the algorithm to produce ciphertext (scrambled text) Introduction to Healthcare Information Technology 6 Figure 8-1 Cryptography process © Cengage Learning 2013 Basic Cryptography (cont’d.) • Five basic protections of cryptography – – – – – Confidentiality Integrity Availability Authenticity of the sender Nonrepudiation • Proves that a user performed an action • Prevents an individual from fraudulently denying an action Introduction to Healthcare Information Technology 8 Basic Cryptography (cont’d.) • Symmetric cryptography – Uses the same single key to encrypt and decrypt a document – Also called private key cryptography – Can provide strong protection as long as key is kept secure • Data Encryption Standard (DES) – One of the first widely popular symmetric cryptography algorithms Introduction to Healthcare Information Technology 9 Table 8-1 Information protections by cryptography © Cengage Learning 2013 Figure 8-2 Symmetric (private key) cryptography © Cengage Learning 2013 Basic Cryptography (cont’d.) • Triple Data Encryption Standard (3DES) – Uses three rounds of encryption instead of one – Ciphertext from one round becomes input for second iteration – Employs a total of 48 iterations in its encryption – Most secure versions of 3DES use different keys for each round Introduction to Healthcare Information Technology 12 Figure 8-3 3DES © Cengage Learning 2013 Basic Cryptography (cont’d.) • Advanced Encryption Standard (AES) – Symmetric algorithm approved in 2000 to replace DES – Designed to be secure well into the future • Asymmetric cryptography – Also known as public key cryptography – Uses two keys – Public key is known to everyone and freely distributed – Private key is known only to one individual Introduction to Healthcare Information Technology 14 Basic Cryptography (cont’d.) • Asymmetric cryptography important principles – Key pairs – Public key • Does not need to be protected – Private key • Should be kept confidential – Both directions • Document encrypted with a public key can be decrypted with the corresponding private key, and vice versa Introduction to Healthcare Information Technology 15 Figure 8-4 Asymmetric (public key) cryptography © Cengage Learning 2013 Applying Cryptography • Cryptography frequently used to protect data in one of two states – At rest • When data is being stored – In motion • As data is transported through electronic communications Introduction to Healthcare Information Technology 17 Applying Cryptography (cont’d.) • Cryptography can be applied to: – – – – Individual files Databases Removable storage devices File server and LAN storage • Network attached storage device – Connected to the network to provide storage • Storage area network – Dedicated network for storage – Not directly accessible to devices through the LAN Introduction to Healthcare Information Technology 18 Applying Cryptography (cont’d.) • Encryption software – Can be used to encrypt or decrypt files one by one • Software products – Pretty Good Privacy (PGP) – GNU Privacy Guard (GPG) • Microsoft’s Encrypting File System (EFS) – Used to protect groups of files in a specific folder – Encrypting and decrypting processes are transparent to the user Introduction to Healthcare Information Technology 19 Applying Cryptography (cont’d.) • Whole disk encryption – Can be used to protect all data on a hard drive – Example: BitLocker drive encryption software • Hardware encryption – Cannot be exploited like software cryptography • Self-encrypting hard disk drives: – Can protect all files stored on them – If authentication process fails, drive can be configured to deny access or perform cryptographic erase on certain data Introduction to Healthcare Information Technology 20 Applying Cryptography (cont’d.) • Trusted Platform Module (TPM) – Chip on the computer motherboard – Provides cryptographic services to all devices – Prevents computer from booting if system files or data have been altered – If hard drive is moved to a different computer, user must enter a recovery password to gain access Introduction to Healthcare Information Technology 21 Applying Cryptography (cont’d.) • Encrypting communications – Cryptography can protect data as it moves across a network • Secure Sockets Layer (SSL) – Protocol for securely transmitting documents over the Internet – Uses a public key to encrypt data over an SSL connection Introduction to Healthcare Information Technology 22 Applying Cryptography (cont’d.) • Transport Layer Security (TLS) – An extension of SSL – Guarantees privacy and data integrity between applications communicating over the Internet • Hypertext Transport Protocol over Secure Sockets Layer (HTTPS) – Encryption protocol to secure Web communications • IP Security (IPsec) – “Transparent” security protocol • No need to install or configure software Introduction to Healthcare Information Technology 23 Applying Cryptography (cont’d.) • Fax – Can be encrypted using an SSL connection – Or a special stand alone fax machine that encrypts and decrypts faxes • E-mail – Encrypted using PGP or similar application • Chat – No single standard exists for encrypting chat – Some clients use SSL or PGP Introduction to Healthcare Information Technology 24 Applying Cryptography (cont’d.) • Telephones – A model telephone exists that will encrypt and decrypt conversations • VoIP – Encrypted using standard LAN encryption technologies • Smartphone – Encrypted with an application installed on the phone Introduction to Healthcare Information Technology 25 Applying Cryptography (cont’d.) • Web sites – Secured using HTTPS • FTP sites – FTP using Secure Sockets Layer (FTPS) – Secure FTP (SFTP) Introduction to Healthcare Information Technology 26 Wireless Security • Wireless networks have been vulnerable targets for attackers • Vulnerabilities of IEEE 802.11 security – MAC address filtering – Wired Equivalent Privacy (WEP) encryption Introduction to Healthcare Information Technology 27 Wireless Security (cont’d.) • MAC address filtering – Limits a device’s access to the access point (AP) – Each device has a unique media access control (MAC) address – Device’s address entered into the software running on the AP • Devices can be permitted or blocked Introduction to Healthcare Information Technology 28 Figure 8-5 MAC address filtering © Cengage Learning 2013 Wireless Security (cont’d.) • Vulnerabilities of MAC address filtering – MAC addresses are initially exchanged in unencrypted format – Difficult to manage a large number of MAC addresses • Wired Equivalent Privacy (WEP) – Relies on a secret key shared between wireless client device and the AP – Has security vulnerabilities – No longer recommended for protecting WLAN transmissions Introduction to Healthcare Information Technology 30 Wireless Security Solutions • Initial approach to security vulnerabilities – Temporary fixes, or patches • Unified approach was needed • Wi-Fi Protected Access (WPA) – Subset of 802.11i – Addresses both encryption and authentication – Uses preshared key technology • Wi-Fi Protected Access 2 (WPA2) – Second generation of WPA security – Introduced in 2004 Introduction to Healthcare Information Technology 31 Wireless Security Solutions (cont’d.) • Remote Authentication Dial In User Service (RADIUS) – Used for more than just dial-in networks – RADIUS client can be a wireless AP or dial-up server • Responsible for sending user credentials – Detailed steps for RADIUS authentication shown in Figure 8-6 Introduction to Healthcare Information Technology 32 Figure 8-6 RADIUS authentication © Cengage Learning 2013 Wireless Security Solutions (cont’d.) • Service Set Identifier (SSID) – Typically set to WLAN, wireless, or the name of the vendor – Should be renamed to a generic word that does not give information about the owner or network location • Site surveys – In-depth examination of a proposed wireless LAN site – Determine the number and placement of access points, and types of antennas needed Introduction to Healthcare Information Technology 34 Wireless Security Solutions (cont’d.) • Antenna placement – Should be located near the center of the coverage area – Recommended to mount as high as possible • Power level controls – Adjust the power so less of the signal leaves the premises Introduction to Healthcare Information Technology 35 Wireless Security Solutions (cont’d.) • Rogue access points – Serious threats to network security – Allow attackers to intercept the RF signal and bypass network security • Methods of detecting rogue access points – Security personnel walk the area with a protocol analyzer – Continually monitor the RF airspace with a wireless probe Introduction to Healthcare Information Technology 36 Wireless Security Solutions (cont’d.) • Types of wireless probes – – – – Wireless device probe Desktop probe Access point probe Dedicated probe Introduction to Healthcare Information Technology 37 Remote Access • Security for remote access connections is important • Three typical types of remote access – Virtual private networks – Terminal emulation – Remote control applications Introduction to Healthcare Information Technology 38 Virtual Private Network • Uses an unsecured public network as if it were a secure private network – Encrypts all data transmitted between remote device and the network – Encrypted packets are encapsulated in a second packet • Endpoint – End of the tunnel between VPN devices – Can be software on a local computer, or a dedicated hardware device Introduction to Healthcare Information Technology 39 Virtual Private Network (cont’d.) • VPNs can be software or hardware-based – Software-based VPNs offer the most flexibility in managing network traffic – Hardware-based VPNs are more secure and have better performance • Tunneling protocols used for VPN transmissions – Point-to-Point Tunneling Protocol (PPTP) • Illustrated in Figure 8-7 – Layer 2 Tunneling Protocol (L2TP) Introduction to Healthcare Information Technology 40 Figure 8-7 Point-to-Point Tunneling Protocol © Cengage Learning 2013 Terminal Emulation • Software application that allows a desktop computer to function as a terminal • Telnet protocol – One of the most widely used applications • Secure Shell (SSH) – Encrypted alternative to Telnet used to access remote computers Introduction to Healthcare Information Technology 42 Table 8-2 SSH commands © Cengage Learning 2013 Remote Control Applications • Remote Desktop Connection (RDC) – Software that allows a user to connect to a remote computer – User can function as if he/she were sitting at the remote computer Introduction to Healthcare Information Technology 44 Figure 8-8 Remote Desktop Connection (RDC) © Cengage Learning 2013 Secure Disposal • Securely destroying sensitive documents: – Important to prevent unauthorized retrieval from the “dumpster” • Types of records – Public records – Private records – Legal health record • Documentation of healthcare services provided to an individual • Contains various types of information Introduction to Healthcare Information Technology 46 Retention of Medical Records • Length of time for record retention varies based on regulations • LHR retention by individual providers – Seven years after the last treatment date – Or three years after the patient’s death • Hospital retention guidelines – 25 years after discharge for adults – Up to age 18 for children – Images of the documents are sufficient Introduction to Healthcare Information Technology 47 Methods of Record Disposal • Secure shredding – Used to destroy paper documents • Sanitizing – Removing only sensitive information from a document – May involve blacking out text • Degaussing – Used with electronic records – Resets magnetic charge to a neutral state Introduction to Healthcare Information Technology 48 Summary • Cryptography transforms information into a secure form so that unauthorized persons cannot access it • Symmetric cryptography uses a single key to encrypt and decrypt a message • Asymmetric cryptography uses two keys: a public and a private key • Cryptography can be applied through hardware or software • Encryption can protect data that is stored or being transmitted across a network Introduction to Healthcare Information Technology 49 Summary (cont’d.) • WPA2 and IEEE 802.11i are foundations of wireless security protections today • A virtual private network uses tunneling protocols to communicate over a public network as if it were a secure private network • A legal health record is the documentation of healthcare services provided to an individual • Legal health records may be disposed of by shredding, sanitizing, or degaussing (for electronic records) Introduction to Healthcare Information Technology 50