* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Ch10b
Survey
Document related concepts
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Computer network wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Airborne Networking wikipedia , lookup
Deep packet inspection wikipedia , lookup
Network tap wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Wireless security wikipedia , lookup
Computer security wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Transcript
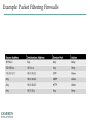
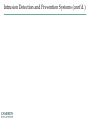
Network Security Announcements • Review Assignment - Assessment 3 (due Tuesday, before class) • Assessment 3 – Next Thursday Reminders: • Network Design Project • No more than 2 per group • Proposals due on the day of presentation • Sign-ups shortly 2 Basics of Network Security • Anti-virus / Anti-Spyware • Access Controls • Firewall • Intrusion Protection/Detection Systems • Identify fast spreading threats 3 Access Controls • The four processes of access control Firewalls Example: Packet Filtering Firewalls Intrusion Detection and Prevention Systems (IDPS) Intrusion Detection and Prevention Systems (cont’d.) Basic Network Facts Primary Core Located in Technology Support Center (TSC) Secondary Core located in CIS Disaster Recovery Facility Comprised of Cisco Systems 6500 series switches Distribution layer, Cisco Catalyst 4500 and 3750 series Total network is 311 switches 1600+ Controller based wireless Access Points All devices monitored 24/7 by Netcom staff. Dual connections to the internet via NCREN. Primary pipe is 10gig and backup is 1gig via NCREN BTOP Network Security Cisco Firewall Service Module UNCW uses Cisco Systems ASA5585 devices Primary and Secondary for Redundancy ASA provides up to 20 individual contexts Allows any VLAN on the switch to be passed through to the device to operate as a firewall port and integrates firewall security inside the network infrastructure. ASA evolved from Cisco PIX technology and uses the same timetested Cisco PIX Operating System, a secure, real-time operating system. Defines the security parameter and enables the enforcement of security policies through authentication, access control lists, and protocol inspection. Network Security Intrusion Prevention Systems UNCW’s Intrusion Prevention Systems – ASA5585 IPS We currently use redundant pairs for continuity. The ASA network intrusion prevention and detection system (IDS/IPS) reputational based, combining the benefits of signature, protocol and anomaly-based inspection. Capable of performing real-time traffic analysis and packet logging on IP networks. Can be used to detect a variety of attacks and probes, such as buffer overflows, stealth port scans, CGI attacks, SMB probes, OS fingerprinting attempts. Has a real-time alerting capability for Network Communications Staff Rules are pushed to all IPS systems nightly. 12 Logical Network Core Traffic Flow Total Network Layout Network Authentication Cisco Identity Services Engine (ISE) is a security policy management and control platform. It automates and simplifies access control and security compliance for wired, wireless, and VPN connectivity. Cisco ISE is primarily used to provide secure access and guest access, support BYOD initiatives. ISE authenticates against Active Directory, meaning credentials are required to access UNCW’s network. ISE is deployed in all building and wireless networks as of fall 2014. STUXNET STUXNET – How it Worked Stuxnet What was it? How did it spread and how far? What are the implications? Stuxnet Precursors: What should we do now? Target – What Happened? Target – How did it happen? Target – How could it have been stopped? Target – Modern Day Hacking Security Discussion • • • • • • TJ Maxx RSA Epsilon Gawker Wikileaks HB Gary 24 11.1 Corporate Security: TJ Maxx • War-Driving to seek vulnerabilities in wireless networks • Breaches took place all the way back to 2005 • Albert Gonzalez was mastermind • 2005 -2007 sold as many as 170 million ATM/Credit Card #s • Typically used SQL injection to launch packet sniffing • Now serving 20 years in a federal prison 11.1 Corporate Security: RSA • Security companies are often the target of many hackers. • Another case of phishing emails to get into the company • Excel Spreadsheet had a Zero-day exploit • Exploit took advantage of Adobe Flash allowing them to install a remote administration tool • Used remote admin tool to get deeper information 11.1 Corporate Security: Epsilon • Occurred earlier this year • Primary purpose for stealing • Phishing – maquerading as a trustworthy entity to gain access to information • Form of Social Engineering • Carried out by email spoofing 11.1 Passwords: Gawker Hack • After hack, the Wall Street Journal Examine a number of passwords (188,279) and here are some of the most commonly found: • • • • • password qwerty letmein trustno1 passw0rd Can anyone guess the most commonly used? 11.1 Corporate Security: Higher Ed Threats • Mobile Devices • Social Media Viruses (hilarious video attack through FB) • Virtualization • Embedded devices (number of devices connected to the network) • Consumerization of IT (personal devices for organizational use) 11.1 Corporate Security: Wikileaks • Exposed major security flaws in the US government • • • Not standardized across agencies No user restrictions on copying data Minimal monitoring of users accessing sensitive data • Recently, new measures are in place to alleviate problems. • Bradley Manning trial begins December 16th 11.1 Corporate Security: HB Gary • Found a flaw in content management system • Used an SQL Injection to gain access • Numerous issues with the system allowed hackers to obtain two passwords: the CEO (Aaron Barr) and COO (Ted Vera) • Key takeaway: passwords! • Don’t use short, easily deciphered • Use different passwords for different accounts