* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Useful Tips for Reducing the Risk of Unauthorized Access
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Computer security wikipedia , lookup
Wireless security wikipedia , lookup
Computer network wikipedia , lookup
Network tap wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Distributed firewall wikipedia , lookup
Airborne Networking wikipedia , lookup
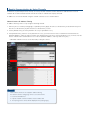
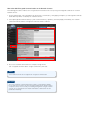
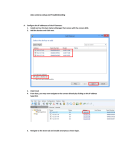
Useful Tips for Reducing the Risk of Unauthorized Access for Network Cameras Important System administrators are advised to read. Overview and Use of this Guide Objectives This guide provides additional information related to the Canon Network Cameras, and in particular, steps you can take to enhance the secure operation of this device. This document will help you better understand how the device functions and will help you feel confident that it operates, stores or transmits device data in a secure and accurate manner, including any potential impact on security and network infrastructure. We recommend that you read this document in its entirety and take appropriate actions consistent with your information technology security policies and practices as an enhancement to your organization’s existing security policies. Since security requirements will vary from customer to customer, you have the final responsibility to ensure that all implementations, re-installations, and testing of security configurations, patches, and modifications are appropriate and required for your environment. Intended Audience This guide is intended for use by network administrators, dealers and other business customers. In order to get the most from this guide, you should have an understanding of: • your network environment, • any restrictions placed on applications that are deployed on that network, and • the applicable operating system. Limitations to this Guidance This guide is meant to help you evaluate the device and the security of your network environment, but it cannot be a complete information source for all potential customers. This guide proposes a hypothetical customer printer environment; if your network environment differs from the hypothetical environment, your network administration team and your dealer or Authorized Canon Service Provider must understand the differences and determine whether any modifications or additional action is needed. Additionally: • T his guide only describes those features within the application that have some discernible impact to the general network environment, whether it be the overall network, security, or other customer resources. • T he guide's information is related to the specified Canon device above. Although much of this information will remain constant through the device life cycle, some of the data is revision-specific, and will be revised periodically. IT organizations should check with their Authorized Canon Service Provider to determine the appropriate deployment for your environment. Thank you for purchasing Canon products. This document outlines how to protect network cameras from unauthorized access from external networks. System administrators are advised to read through the document before use. Preface This document describes methods to prevent unauthorized access to Canon network cameras. Four key points for preventing unauthorized access from external networks 1. Use Private IP addresses 2. Restrict communication by using firewalls 3. Protect network camera with passwords 4. Set SSL encrypted communication NOTE he methods and illustrations included in this document are provided for reference T only and may differ from the user’s network camera. For more details, please refer to the Operation Guide included with the camera. Use Private IP Addresses An IP address is a numeric code assigned to a device on a network. There are two types of IP addresses: global IP addresses, which are used for an Internet connection, and private IP addresses, which are used for local networks such as on a company intranet. A global IP address can be accessed by anonymous users on the Internet. If a network camera is assigned a global IP address, it becomes vulnerable to unauthorized access and viewing. We recommend that network cameras employ a private IP address. The private IP address has to fall within one of the following ranges: Private IP address range xx 10.0.0.0 – 10.255.255.255 xx 172.16.0.0 – 172.31.255.255 xx 192.168.0.0 – 192.168.255.255 Router Global IP address: accessible from internet Private IP address: inaccessible from internet NOTE ven if a network camera is assigned a global IP address, users can limit the E risk of unauthorized access through such means as establishing a firewall to prevent access from an external network. Please consult with a corporate network administrator when setting a global IP address for your network camera. Restrict Communication by Using Firewalls A firewall is a system that prevents not only access by external networks, but also attacks on and intrusions to a local network. We recommend that network cameras be used on networks that employ a firewall. IP addresses can also be filtered using the network camera’s access control features. Network Camera IP Address Filtering IP address filtering can be set up using the following method: 1. From the [Access Control] setting page, set [Enable] for the [Apply Host Access Restrictions,] located within the [IPv4 Host Access Restrictions] or [IPv6 Host Access Restrictions] section. 2. Set the [Default Policy] to either [Authorize Access] or [Prohibit Access]. 3. If the [Default Policy] has been set to [Authorize Access], you must enter the host or network to be blocked into the [Network Address / Subnet], and select [No]. If the [Default Policy] has been set to [Prohibit Access], you must enter the host or network that is authorized for access into the [Network Address / Subnet], and select [Yes]. –– Individual networks or hosts can be filtered by setting the subnet. NOTE xx Some network cameras do not support IP address filtering. xx The network camera’s setting page can be accessed as follows: 1. Launch the Web browser. 2. Input the network camera’s IP address into the address bar. 3. The Top Page for the camera will be displayed. Click [Setting Page]. Protect Network Camera with Passwords Canon’s network cameras offer three user settings: Administrator, Authorized User and Guest User. The Administrator and Authorized User accounts are password protected. The risk of unauthorized access can be reduced by allocating each user with the proper authorization level. The Administrator is a user that has been given complete authorization. The [Setting Page] and the [Administration Tools] are only accessible to the Administrator. Authorized Users can be registered on the setting page: [Access Control] > [Authorized User Account]. On the setting page, access privileges for Authorized Users and Guest Users can be set in [Access Control] > [User Authority]. Please check the boxes for authorized privileges. Privileged Camera Control Can launch the Administrator Viewer Camera Control Can control the camera with the VB Viewer Video Distribution Can view video with the VB Viewer Audio Distribution Can receive audio within the VB Viewer, as well as the Administrator Viewer By prohibiting all privileges for Guest Users, they will not be able to access the camera and will not be required to enter a password. Important xx Please make sure to change the Administrator password from the default setting. xx For security reasons, please change the password on a regular basis. xx Please set a password that is difficult for others to guess. xx Settings may differ by network camera model. Set SSL Encrypted Communication By installing a server certificate in the network camera, users can ensure safe SSL encrypted communications when accessing the Canon network camera via a Web browser. The structure of SSL communication (see figure on right): 1. When a user accesses a network camera from their computer, the server certificate for SSL and the public key for the server are requested. 2. The certificate and the public key are sent to the user’s computer from the network camera. 3. Using the public key received from the network camera, a unique common key is generated and encrypted on the user’s computer. 4. The encrypted common key is sent to the network camera. 5. The network camera uses the private key to decode the encrypted common key. 6. The user’s computer and the network camera both possess the common key and can send/receive data using the common key. 1. Request Access 2. Certificate Authentication Generate Common Key Network Camera Server Certificate Public Key 3. Encrypt with Public Key Key Pair Private Key Encrypted Common Key 4. Encrypted Common Key 5. Decode with Private Key Common Key 6. Communicate with Common Key How to Set SSL Encrypted Communication on the Network Camera The following procedure enables SSL encrypted communication to be set up using a Self-Signed Certificate on a Canon network camera: 1. On the setting page, enter information into [SSL/TLS] > [Certificates], click [Apply] and [Exec.] A Self-Signed Certificate and Public Key will be created by the network camera. 2. Select [Encrypted Communications] > [SSL Communications] > [Enable], and click [Apply and reboot]. The network camera will reboot and the Self-Signed Certificates will be enabled. 3. Access the network camera from the computer using HTTPS. SSL encrypted communications using a Common Key will start. NOTE Some network cameras do not support SSL encrypted communication. Important The server certificate created using this procedure is a Self-Signed Certificate. For security reasons, please only use Self-Signed Certificates in situations where complete security is not necessary, such during testing. When using the network camera, we recommend that users obtain and install a certificate from the CA (Certification Authority). ©© CANON INC. 2015