* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Presentation
Survey
Document related concepts
Transcript
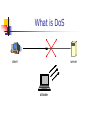
DoS attacks prevention Avital Yachin Under supervision of Gal Badishi SoftLab – June 2006 What is DoS server client attacker What is DDoS zombie zombie server zombie zombie zombie zombie Possible solutions Firewall (specific ports) ? Heuristic (identifying and blocking the attacker) ? Clients Authentication ? At what level ? Selected solution Both sides authenticate the other side at the packet level. Current implementation filters packets at the transport layer (UDP). Can be generalized to the IP layer. How it works IP Header IP Data UDP Header UDP Header IP Header UDP Data UDP Data IP Data Outgoing Packets Key How it works IP Header IP Data UDP Header UDP Header IP Header UDP Data UDP Data Key IP Data Incoming Packets Key ? = How it works Application TCP/IP Driver NDIS Driver Encapsulator NDIS Hook Driver User mode Kernel mode Network Card Authentication Method Hashing (SHA-1) of current time and a secret code. Authentication token changes periodically (not for every packet much cheaper). Clocks synchronization. Client’s secret code is known to server. Conclusions There’s no simple solution to wire flood. Packets can be filtered at lower levels thus preventing system resources abuse. Solution is “cheaper” than IPSEC (but doesn’t handle encryption). Future Enhancements Filtering packets at the IP layer (solution for TCP and others). Auto time synchronization. Full kernel mode implementation (performance / flexibility tradeoff). Demo