* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download TNS07%20PPP
Windows Vista networking technologies wikipedia , lookup
Computer network wikipedia , lookup
Universal asynchronous receiver-transmitter wikipedia , lookup
Packet switching wikipedia , lookup
Quality of service wikipedia , lookup
Serial (radio and television) wikipedia , lookup
Zero-configuration networking wikipedia , lookup
History of telecommunication wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Extensible Authentication Protocol wikipedia , lookup
Point-to-Point Protocol over Ethernet wikipedia , lookup
Telecommunication wikipedia , lookup
Communication protocol wikipedia , lookup
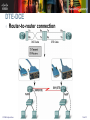
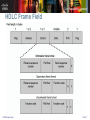
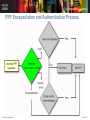
Point-to-Point Protocol (PPP) 點對點網路協定 CCNA Exploration Accessing the WAN – Chapter 2 Introduction to Serial Communication With a serial connection (串列連線) , information is sent across one wire, one data bit at a time. In reality, it is often the case that serial links can be clocked considerably faster than parallel links, and they achieve a higher data rate. CCNA Exploration 2 of 51 Serial Communication Standards There are three key serial communication standards affecting LAN-to-WAN connections: RS-232 • A serial port is a general-purpose interface that can be used for almost any type of device including modems. V.35 • V.35 is the interface standard used by most routers and DSUs that connect to T1 carriers. HSSI • It supports transmission rates up to 52 Mb/s. • Engineers use HSSI to connect routers on LANs with WANs over high-speed lines such as T3 lines. CCNA Exploration 3 of 51 Time Division Multiplexing (分時多工) Bell Laboratories invented time-division multiplexing (TDM) to maximize the amount of voice traffic carried over a medium. TDM divides the bandwidth of a single link into separate channels or time slots. The channels take turns using the link. CCNA Exploration 4 of 51 Time Division Multiplexing At sending end: A multiplexer (MUX,多工器) at the transmitter accepts different signals. The MUX breaks each signal into segments. The MUX puts each segment into a single channel by inserting each segment into a timeslot. At receiving end: A MUX at the receiving end reassembles the TDM stream into the different data streams based only on the timing of the arrival of each bit. CCNA Exploration 5 of 51 Statistical Time Division Multiplexing Problem of TDM: TDM shares this inefficiency when traffic is intermittent, because the time slot is still allocated even when the channel has no data to transmit. Statistical time-division multiplexing (STDM) uses a variable time slot length allowing channels to compete for any free slot space. STDM requires each transmission to carry identification information (a channel identifier). CCNA Exploration 6 of 51 TDM Examples - ISDN and SONET An example of a technology that uses synchronous TDM is ISDN. ISDN basic rate (BRI) has three channels consisting of two 64 kb/s B-channels (B1 and B2), and a 16 kb/s D-channel. The TDM has nine timeslots, which are repeated in the sequence shown in the following figure. CCNA Exploration 7 of 51 TDM Examples - ISDN and SONET On a larger scale, the telecommunications industry uses the SONET or SDH standard for optical transport of TDM data. SONET/SDH takes n bit streams, multiplexes them, and optically modulates the signal, sending it out using a light emitting device over fiber with a bit rate equal to (incoming bit rate) x n. CCNA Exploration 8 of 51 TDM Examples - ISDN and SONET The original unit used in multiplexing telephone calls is 64 kb/s for one phone call. It is referred to as a DS-0 or DS0 (digital signal level zero). In North America, 24 DS0 units, outside North America, 32 DS0 units. CCNA Exploration 9 of 51 TDM Examples - ISDN and SONET T-carrier refers to the bundling of DS0s and E-carrier Hierarchy is similar to T-carrier. CCNA Exploration 10 of 51 Demarcation Point CCNA Exploration 11 of 51 DTE-DCE From the point of view of connecting to the WAN, a serial connection has a DTE device at one end of the connection and a DCE device at the other end. CCNA Exploration 12 of 51 DTE-DCE The router end of the shielded serial transition cable may be a DB-60 connector, which connects to the DB-60 port on a serial WAN interface card. The router interface end of the Smart Serial cable is a 26-pin connector. CCNA Exploration 13 of 51 DTE-DCE Router-to-router connection CCNA Exploration 14 of 51 DTE-DCE Parallel to Serial Conversion Your PC also has a Universal Asynchronous Receiver/Transmitter (UART) chip on the motherboard. • The UART is the DTE agent of your PC and communicates with the modem or other serial device. CCNA Exploration 15 of 51 WAN Encapsulation Protocols To ensure that the correct protocol is used on the WAN link, you need to configure the appropriate Layer 2 encapsulation type. CCNA Exploration 16 of 51 HDLC Encapsulation HDLC is a synchronous Data Link layer bit-oriented protocol developed by ISO. HDLC provides both connection-oriented and connectionless service. HDLC defines a Layer 2 framing structure that allows for flow control and error control through the use of acknowledgments. Each frame has the same format, whether it is a data frame or a control frame. HDLC uses a frame delimiter, or flag, to mark the beginning and the end of each frame. CCNA Exploration 17 of 51 HDLC Encapsulation Cisco has developed an extension to the HDLC protocol to solve the inability to provide multiprotocol support. Cisco HDLC frames contain a field for identifying the network protocol being encapsulated. CCNA Exploration 18 of 51 HDLC Frame Field CCNA Exploration 19 of 51 HDLC Frame Field Flag The flag field initiates and terminates error checking. The frame always starts and ends with an 8-bit flag field. • The bit pattern is 01111110. Address The address field contains the HDLC address of the secondary station. Protocol (only used in Cisco HDLC) This field specifies the protocol type encapsulated within the frame (e.g. 0x0800 for IP). CCNA Exploration 20 of 51 HDLC Frame Field Control The control field uses three different formats, depending on the type of HDLC frame used: • Information (I) frame: – I-frames carry upper layer information and some control information. – This frame sends and receives sequence numbers, and the poll final (P/F) bit performs flow and error control. • Supervisory (S) frame: – S-frames provide control information. – An S-frame can request and suspend transmission, report on status, and acknowledge receipt of I-frames. • Unnumbered (U) frame: – U-frames support control purposes and are not sequenced. – A U-frame can be used to initialize secondaries. CCNA Exploration 21 of 51 HDLC Frame Field Data The data field contains a path information unit (PIU) or exchange identification (XID) information. Variable length field (L3 packets). Frame check sequence (FCS) The FCS is usually a cyclic redundancy check (CRC) calculation remainder. The CRC calculation is redone in the receiver. • If the result differs from the value in the original frame, an error is assumed. CCNA Exploration 22 of 51 Configuring HDLC Encapsulation Cisco HDLC is the default encapsulation method used by Cisco devices on synchronous serial lines. If the default encapsulation method has been changed, use the encapsulation hdlc command to reenable HDLC. Two steps : Enter the interface configuration mode of the serial interface. Enter the encapsulation hdlc command to specify the encapsulation protocol on the interface. CCNA Exploration 23 of 51 Troubleshooting a Serial Interface The show interface serial command returns any of the following five possible problem states in the interface status line: Serial x is down, line protocol is down Serial x is up, line protocol is down Serial x is up, line protocol is up (looped) Serial x is up, line protocol is down (disabled) Serial x is administratively down, line protocol is down CCNA Exploration 24 of 51 Troubleshooting a Serial Interface The show controllers command is used to indicate the state of the interface channels and whether a cable is attached to the interface. CCNA Exploration 25 of 51 Point-to-Point Protocol (PPP) PPP establishes a direct connection using serial cables, phone lines, trunk lines, cellular telephones, specialized radio links, or fiber-optic links. When you need to connect to a non-Cisco router, you should use PPP encapsulation. Advantages of using PPP The link quality management feature monitors the quality of the link. • If too many errors are detected, PPP takes the link down. PPP supports PAP and CHAP authentication. CCNA Exploration 26 of 51 Point-to-Point Protocol (PPP) PPP contains three main components: HDLC protocol for encapsulating datagrams over point-to-point links. Extensible Link Control Protocol (LCP) to establish, configure, and test the data link connection. Family of Network Control Protocols (NCPs) for establishing and configuring different Network layer protocols. CCNA Exploration 27 of 51 PPP Architecture PPP and OSI share the same Physical layer, but PPP distributes the functions of LCP and NCP differently. CCNA Exploration 28 of 51 PPP Architecture At the physical layer, you can configure PPP on a range of interfaces, including: Asynchronous serial Synchronous serial HSSI ISDN CCNA Exploration 29 of 51 PPP Architecture Link Control Protocol Layer LCP has a role in establishing, configuring, and testing the data-link connection. The LCP provides automatic configuration of the interfaces at each end, including: • • • • CCNA Exploration Handling varying limits on packet size Detecting common misconfiguration errors Terminating the link Determining when a link is functioning properly or when it is failing 30 of 51 PPP Architecture Network Control Protocol Layer PPP permits multiple network layer protocols to operate on the same communications link. • For every network layer protocol used, a separate Network Control Protocol (NCP) is provided. • For example, Internet Protocol (IP) uses the IP Control Protocol (IPCP), and Internetwork Packet Exchange (IPX) uses the Novell IPX Control Protocol (IPXCP). CCNA Exploration 31 of 51 PPP Frame Flag - Indicates the beginning or end of a frame (01111110). Address - Consists of the standard broadcast address, 11111111. Control - A connectionless link service is provided. Protocol - identify the protocol encapsulated in the data field of the frame. Data - 0 or more bytes that contain the datagram for the protocol specified in the protocol field. The default maximum length of the data field is 1500 bytes. FCS - for error control purposes. CCNA Exploration 32 of 51 Establishing a PPP Session CCNA Exploration 33 of 51 Establishing a PPP Session Phase 1: Link establishment and configuration negotiation • Before PPP exchanges any Network layer datagrams (for example, IP), the LCP must first open the connection and negotiate configuration options. • This phase is complete when the receiving router sends a configuration-acknowledgment frame back to the router initiating the connection. Phase 2: Link quality determination (optional) • The LCP tests the link to determine whether the link quality is sufficient to bring up Network layer protocols. CCNA Exploration 34 of 51 Establishing a PPP Session Phase 3: Network layer protocol configuration negotiation • After the LCP has finished the link quality determination phase, the appropriate NCP can separately configure the Network layer protocols, and bring them up and take them down at any time. • If the LCP closes the link, it informs the Network layer protocols so that they can take appropriate action. CCNA Exploration 35 of 51 Establishing a PPP Session CCNA Exploration 36 of 51 LCP Operation LCP operation uses three classes of LCP frames to accomplish the work of each of the LCP phases: Link-establishment frames establish and configure a link (Configure-Request, ConfigureAck, Configure-Nak, and Configure-Reject) Link-maintenance frames manage and debug a link (Code-Reject, Protocol-Reject, Echo-Request, Echo-Reply, and Discard-Request) Link-termination frames terminate a link (Terminate-Request and Terminate-Ack) CCNA Exploration 37 of 51 PPP Configuration Options PPP can be configured to support various functions including: Authentication (認證) using either PAP or CHAP Compression using either Stacker or Predictor Multilink (多連結) which combines two or more channels to increase the WAN bandwidth CCNA Exploration 38 of 51 NCP Process After the LCP has configured and authenticated the basic link, the appropriate NCP is invoked to complete the specific configuration of the Network layer protocol being used. When the NCP has successfully configured the Network layer protocol, the network protocol is in the open state on the established LCP link. Reference http://www.netadmin.com.tw/article_conte nt.asp?sn=0805270013 CCNA Exploration 39 of 51 PPP Configuration Commands Enabling PPP on an Interface The following example enables PPP encapsulation on serial interface 0/0/0: • R3#configure terminal • R3(config)#interface serial 0/0/0 • R3(config-if)#encapsulation ppp Configuring PPP compression To configure compression over PPP, enter the following commands: • R3(config)#interface serial 0/0/0 • R3(config-if)#encapsulation ppp • R3(config-if)#compress [predictor | stac] CCNA Exploration 40 of 51 Verifying and debugging CCNA Exploration 41 of 51 Verifying and debugging CCNA Exploration 42 of 51 Password Authentication Protocol (PAP) Characteristics of PAP Two-way process (2-way handsake,雙向握手) PAP is not a strong authentication protocol. • Passwords are sent across the link in clear text and there is no protection from playback or repeated trial-and-error attacks. The remote node is in control of the frequency and timing of the login attempts. Authentication process performs once. CCNA Exploration 43 of 51 Password Authentication Protocol (PAP) When to use PAP PAP may be used in the following environments: • A large installed base of client applications that do not support CHAP • Incompatibilities between different vendor implementations of CHAP • Situations where a plaintext password must be available to simulate a login at the remote host CCNA Exploration 44 of 51 Password Authentication Protocol (PAP) Initiating PAP Completing PAP CCNA Exploration 45 of 51 Challenge Handshake Authentication Protocol (CHAP) Characteristics of CHAP CHAP is used at the startup of a link and periodically verifies the identity of the remote node. The local router or a third-party authentication server is in control of the frequency and timing of the challenges. CHAP provides protection against playback attack through the use of a variable challenge value that is unique and unpredictable. CCNA Exploration 46 of 51 Challenge Handshake Authentication Protocol (CHAP) Initiating CHAP (By remote router) Responding CHAP (By local router) Hash value CCNA Exploration 47 of 51 Challenge Handshake Authentication Protocol (CHAP) Completing CHAP (By remote router) Reference: http://en.wikipedia.org/wiki/Challenge-handshake_authentication_protocol http://www.cisco.com/en/US/tech/tk713/tk507/technologies_tech_note09186a00800b4131.shtml CCNA Exploration 48 of 51 PPP Encapsulation and Authentication Process CCNA Exploration 49 of 51 Configuring PPP Authentication Configuring PAP authentication CCNA Exploration 50 of 51 Configuring PPP Authentication Configuring CHAP authentication CCNA Exploration 51 of 51 End CCNA Exploration 52 of 51