* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Attacks and hacker tools - International Computer Institute
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Wireless security wikipedia , lookup
TCP congestion control wikipedia , lookup
Parallel port wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Deep packet inspection wikipedia , lookup
Distributed firewall wikipedia , lookup
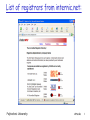
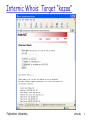
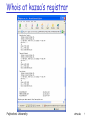
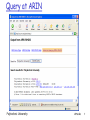
Attacks & Hacker Tools Before talking about defenses, need to look at network from attacker’s perspective Reconnaissance Network mapping Port scanning Sniffing Polytechnic University IP address spoofing Session hijacking DoS DDoS Attacks 1 Reconnaissance “casing the joint” Let’s take a close look at: Reconnaissance with whois Reconnaissance with DNS A few words about a Registrar: Organization where you register a domain name Verifies uniqueness of name Enters domain name into various databases: whois & DNS Polytechnic University Attacks 2 List of registrars from internic.net: Polytechnic University Attacks 3 Whois databases Input: domain name or company name Output: registrar, whois server, dns server Some useful whois sites: www.internic.net For com, net and org top-level domains www.allwhois.com For country-code top-level domains, e.g., jp, fr Two steps First find target’s registrar Then whois target at registrar Polytechnic University Attacks 4 Internic Whois: Target “kazaa” Polytechnic University Attacks 5 Whois: next step Do whois at registrar, eg, register.com Input: domain name, IP address, net administrator name Output: Names of people (administrator, billing contact) Telephone numbers E-mail addresses Name servers and IP addresses Polytechnic University Attacks 6 Whois at kazaa’s registrar Polytechnic University Attacks 7 Reconnaissance: IP Ranges ARIN: American Registry for Internet Numbers Maintains whois database that includes IP address ranges in US RIPE: Europe APNIC: Asia Polytechnic University Attacks 8 Query at ARIN Polytechnic University Attacks 9 Why whois databases needs to be publicly available If you’re under attack, can analyze source address of packets. Can use whois database to obtain info about the domain from where the attack is coming. Can inform admin that their systems are source of an attack Polytechnic University Attacks 10 Reconnaissance: DNS database Let’s quickly review DNS: distributed database implemented in hierarchy of many DNS servers Authoritative name server: for a given domain (e.g., poly.edu), provides server name to IP address mappings for servers (Web, email, ftp, etc) in domain Primary and secondary name server for reliability Polytechnic University Attacks 11 Root DNS Servers com DNS servers yahoo.com DNS servers amazon.com DNS servers org DNS servers pbs.org DNS servers edu DNS servers poly.edu umass.edu DNS servers DNS servers Figure 2.18 Portion of the hierarchy of DNS servers Polytechnic University Attacks 12 DNS: queries root DNS server 2 3 TLD DNS server 4 5 local DNS server dns.poly.edu 1 8 requesting host 7 6 authoritative DNS server dns.cs.umass.edu cis.poly.edu gaia.cs.umass.edu Polytechnic University Attacks 13 DNS records DNS: distributed db storing resource records (RR) RR format: (name, Type=A name is hostname value is IP address Type=NS name is domain (e.g. foo.com) value is IP address of authoritative name server for this domain Polytechnic University value, type, ttl) Type=MX value is name of mailserver associated with name Attacks 14 DNS protocol, messages Name, type fields for a query RRs in reponse to query records for authoritative servers additional “helpful” info that may be used Query and reply messages sent Over UDP on port 53 Polytechnic University Attacks 15 DNS: caching and updating records once (any) DNS server learns mapping, it caches mapping cache entries timeout (disappear) after some time Polytechnic University Attacks 16 Interrogating DNS servers Attacker first gets primary or secondary authoritative server for target organization using whois. Attacker can then query the DNS by sending DNS query messages. Tools (often available in Unix and Windows machines; also available at web sites): nslookup host dig Polytechnic University Attacks 17 nslookup Avaiable in most unix & Windows machines Get dialpad DNS server IP address from whois set type=any “get all” Polytechnic University Attacks 18 Reconnaissance summary Obtaining information from public databases: whois databases • Tool: web sites DNS database • Tool: nslookup Defense Keep to a minimum what you put in the public database: only what is necessary Polytechnic University Attacks 19 Attacks & Hacker Tools Before talking about defenses, need to look at network from attacker’s perspective Reconnaissance Network mapping Port scanning Sniffing Polytechnic University IP address spoofing Session hijacking DoS DDoS Attacks 20 Network mapping Goal: Learn about a remote network attacker 121.27.2.1 121.27.2.4 firewall? Internet firewall? Internal network 121.27.2.16 Polytechnic University Attacks 21 Network mapping Attacker uses ping sweeps to determine live hosts Attacker uses port scans to determine live services Attacker often uses traceroute to determine path to each host discovered during ping sweep. Overlay results from traceroute to create an approximate network diagram Polytechnic University Attacks 22 Traceroute traceroute: gaia.cs.umass.edu to www.eurecom.fr Three delay measements from gaia.cs.umass.edu to cs-gw.cs.umass.edu 1 cs-gw (128.119.240.254) 1 ms 1 ms 2 ms 2 border1-rt-fa5-1-0.gw.umass.edu (128.119.3.145) 1 ms 1 ms 2 ms 3 cht-vbns.gw.umass.edu (128.119.3.130) 6 ms 5 ms 5 ms 4 jn1-at1-0-0-19.wor.vbns.net (204.147.132.129) 16 ms 11 ms 13 ms 5 jn1-so7-0-0-0.wae.vbns.net (204.147.136.136) 21 ms 18 ms 18 ms 6 abilene-vbns.abilene.ucaid.edu (198.32.11.9) 22 ms 18 ms 22 ms 7 nycm-wash.abilene.ucaid.edu (198.32.8.46) 22 ms 22 ms 22 ms trans-oceanic 8 62.40.103.253 (62.40.103.253) 104 ms 109 ms 106 ms link 9 de2-1.de1.de.geant.net (62.40.96.129) 109 ms 102 ms 104 ms 10 de.fr1.fr.geant.net (62.40.96.50) 113 ms 121 ms 114 ms 11 renater-gw.fr1.fr.geant.net (62.40.103.54) 112 ms 114 ms 112 ms 12 nio-n2.cssi.renater.fr (193.51.206.13) 111 ms 114 ms 116 ms 13 nice.cssi.renater.fr (195.220.98.102) 123 ms 125 ms 124 ms 14 r3t2-nice.cssi.renater.fr (195.220.98.110) 126 ms 126 ms 124 ms 15 eurecom-valbonne.r3t2.ft.net (193.48.50.54) 135 ms 128 ms 133 ms 16 194.214.211.25 (194.214.211.25) 126 ms 128 ms 126 ms 17 * * * * means no reponse (probe lost, router not replying) 18 * * * 19 fantasia.eurecom.fr (193.55.113.142) 132 ms 128 ms 136 ms Polytechnic University Attacks 23 Traceroute: How it works Source sends UDP packets to target Each to an unlikely port 3 packets with the same TTL, then increments TTL When router decrements TTL to 0, sends back to source ICMP packet type 11, code 0, TTL expired When target receives packet, sends back to source ICMP packet type 3, code 0, destination port unreachable Polytechnic University Attacks 24 Ping Sweep Ping Recall ICMP messages are directly encapsulated in IP datagrams (protocol 1) To ping a host: send ICMP Echo Request (ICMP type 8) Host responds with ICMP Echo Reply (type 0) So let’s ping the entire IP address range Use automated tool for this ping sweep If firewall blocks ping packets: Try sweeping with TCP SYN packets to port 80 Or try sending UDP packets to possible ports Polytechnic University Attacks 25 Port scanning Now that we have a map with some hosts, let’s find out what ports are open on a target host 65,535 TCP ports; 65,535 UDP ports Web server: TCP port 80 DNS server: UDP port 53 Mail server: TCP port 25 Port scanning tools can scan: List of ports Range of ports All possible TCP and UDP ports Attacker may scan a limited set of ports, to avoid detection Polytechnic University Attacks 26 Interlude TCP segment structure 32 bits source port # ACK: ACK # valid sequence number acknowledgement number head not UA P R S F len used checksum RST, SYN, FIN: connection estab (setup, teardown commands) Polytechnic University dest port # counting by bytes of data (not segments!) Receive window Urg data pnter Options (variable length) application data (variable length) Attacks 27 Interlude: TCP seq. #’s and ACKs Seq. #’s: byte stream “number” of first byte in segment’s data ACKs: seq # of next byte expected from other side Host A User types ‘C’ Host B host ACKs receipt of ‘C’, echoes back ‘C’ host ACKs receipt of echoed ‘C’ simple telnet scenario Polytechnic University Attacks time 28 Interlude: TCP Connection Establishment Three way handshake: Step 1: client host sends TCP SYN segment to server SYN=1, ACK=0 specifies initial seq # no data Step 2: server host receives SYN, replies with SYN-ACK segment SYN=1, ACK=1 server host allocates buffers specifies server initial seq. # Step 3: client receives SYN-ACK, replies with ACK segment, which may contain data SYN=0, ACK=1 Polytechnic University Attacks 29 TCP: Reset packet If machine receives a TCP packet it is not expecting, it responds with TCP packet with RST bit set. For example when no process is listening on destination port For UDP, machine returns ICMP “port unreachable” instead Polytechnic University Attacks 30 Nmap (1) Extremely popular usually run over linux rich feature set, exploiting raw sockets need root to use all features Ping sweeping over any range of IP addresses with ICMP, SYN, ACK OS determination Polytechnic University Port scanning Over any range of ports Almost any type of TCP, UDP packet Source IP address spoofing Decoy scanning Packet fragmentation Timing Options Excellent reference: Nmap man page Attacks 31 Nmap (2) Input: nmap [Scan Type] [Options] <target hosts> Default for port scanning: ports 1-1024 plus ports listed in nmap service file Output: open ports: syn/ack returned; port is open unfiltered ports: RST returned: port is closed but not blocked by firewall filtered ports: nothing returned; port is blocked by firewall Polytechnic University Attacks 32 Nmap (3): ping sweep Nmap –sP –v 116.27.38/24 Sends ICMP echo request (ping) to 256 addresses Can change options so that pings with SYNs, ACKs… -sP = ping -v = verbose Polytechnic University Attacks 33 Nmap (4): polite port scan nmap –sT -v target.com Attempts to complete 3-way handshake with each target port Sends SYN, waits for SYNACK, sends ACK, then sends FIN to close connection If target port is closed, no SYNACK returned Instead RST packet is typically returned TCP connect scans are easy to detect Target (e.g. Web server) may log completed connections Gives away attacker’s IP address Polytechnic University Attacks 34 Nmap (5) : TCP SYN port scan nmap –sS -v target.com Stealthier than polite scan Send SYN, receive SYNACK, send RST Send RST segment to avoid an accidental DoS attack Stealthier: hosts do not record connection But routers with logging enabled will record the SYN packet Faster: don’t need to send FIN packet Polytechnic University Attacks 35 Nmap (6): TCP ACK scans Many filters (in firewalls and routers) only let internal systems hosts initiate TCP connections Drop packets for which ACK=0 (ie SYN packet): no sessions initiated externally To learn what ports are open through firewall, try an ACK scan (segments with ACK=1) ACK dest port 2031 firewall ACK dest port 2032 RST Polytechnic University I learned port 2032 is open through the firewall Internal Network Attacks 36 Nmap (7): UDP port scans UDP doesn’t have SYN, ACK, RST packets nmap simply sends UDP packet to target port ICMP Port Unreachable: interpret port closed Nothing comes back: interpret port open • False positives common Polytechnic University Attacks 37 Nmap (8): Obscure source Attacker can enter list of decoy source IP addresses into Nmap For each packet it sends, Nmap also sends packets from decoy source IP addresses For 4 decoy sources, send five packets Attacker’s actual address must appear in at least one packet, to get a result If there are 30 decoys, victim network will have to investigate 31 different sources! Polytechnic University Attacks 38 Nmap (9): TCP stack fingerprinting In addition to determining open ports, attacker wants to know OS on targeted machine: exploit machine’s known vulnerabilities sophisticated hacker may set up lab environment similar to target network TCP implementations in different OSes respond differently to illegal combinations of TCP flag bits. Polytechnic University Attacks 39 Nmap (10): Fingerprinting Nmap sends SYN to open port NULL to open port (no flag bits set) SYN/FIN/URG/PSH to open port SYN to closed port ACK to closed port FIN/PSH/URG to closed port UDP to closed port Nmap includes a database of OS fingerprints for hundreds of platforms Polytechnic University Attacks 40 Nmap (11): examples nmap -v target.com Scans all TCP default ports on target.com; verbose mode nmap -sS -O target.com/24 First pings addresses in target network to find hosts that are up. Then scans default ports at these hosts; stealth mode (doesn’t complete the connections); tries to determine OS running on each scanned host nmap -sX -p 22,53,110,143 198.116.*.1-127 Sends an Xmas tree scan to the first half of each of the 255 possible subnets in the 198.116/16. Testing whether the systems run ssh, DNS, pop3, or imap nmap -v -p 80 *.*.2.3-5 finds all web servers on machines with IP addresses ending in .2.3, .2.4, or .2.5 Polytechnic University Attacks 41 Defenses against network mapping Filter using firewalls and packet-filtering capabilities of routers Block incoming ICMP packets, except to the hosts that you want to be pingable Filter Time Exceeded ICMP messages leaving your network Close all unused ports Scan your own systems to verify that unneeded ports are closed Intrusion Detection Systems Polytechnic University Attacks 42 Attacks & Hacker Tools Before talking about defenses, need to look at network from attacker’s perspective Reconnaissance Network mapping Port scanning Sniffing Polytechnic University IP address spoofing Session hijacking DoS DDoS Attacks 43 Review of interconnection devices Hubs Switches Routers Polytechnic University Attacks 44 Hubs Hubs are essentially physical-layer repeaters: bits coming from one link go out all other links at the same rate no frame buffering no CSMA/CD at hub: adapters detect collisions provides net management functionality twisted pair hub Polytechnic University Attacks 45 Sniffing Attacker is inside firewall Requirements Attacker’s host connected to shared medium NIC should be in “promiscuous mode” • processes all frames that come to NIC Sniffer has two components Capture Packet analysis Polytechnic University Grab and file away: userids and passwords credit card numbers secret e-mail conversations Island hopping attack: Take over single machine (eg virus) Install sniffer, observe passwords, take over more machines, install sniffers Attacks 46 Passive sniffing Easy to sniff: 802.11 traffic Ethernet traffic passing through a hub • Any packets sent to hub is broadcast to all interfaces • Not true for a switch Cable modem traffic Popular sniffers Wireshark (saw this in CS 684) tcpdump (for unix) Snort (sniffing and intrusion detection) Polytechnic University Attacks 47 Active Sniffing through a switch How does attacker sniff packets sent to/from the victim? attacker switch victim Have to get victim’s packets to attacker! Polytechnic University Attacks 48 Sniffing through a switch: flooding switch memory approach Host sends flood of frames with random source MAC addresses Switch’s forwarding table gets filled with bogus MAC addresses When “good packet arrives,” dest MAC address not in switch memory Switch broadcasts real packets to all links Sniff all the broadcast packets Polytechnic University Attacks 49 Defenses Tie MAC addresses to switch ports Available on high-end switches Sophisticated configuration Give priority to existing mappings Only replace them when timeout expires Polytechnic University Attacks 50 Sniffing through LAN: poison victim’s ARP table approach Idea: have client’s traffic diverted to attacker (1) Send fake ARP response, mapping router IP address to attacker’s MAC address (0) Sniff all frames that arrive. Configure so that IP packets arriving from victim are attacker forwarded to default router (3) Packets are forwarded from attacker’s host to default router victim (2) Victim sends traffic switch destined to outside world. Poisoned ARP table causes traffic to be sent to attacker Polytechnic University default router for LAN outside world Attacks 51 Powerful sniffing tools Dsniff and ettercap Flooding switch memory ARP poisoning Poisoning DNS Polytechnic University Attacks 52 Sniffing defenses Encrypt data: IPsec, SSL, PGP, SSH Get rid of hubs: complete migration to switched network Use encryption for wireless and cable channels Configure switches with MAC addresses Turn off self learning Eliminates flooding problem Intrusion detection systems: Lookout for large numbers of ARP replies Honeypot Create fake account and send password over network Identify attacker when it uses the password Polytechnic University Attacks 53 Attacks & Hacker Tools Before talking about defenses, need to look at network from attacker’s perspective Reconnaissance Network mapping Port scanning Sniffing Polytechnic University IP address spoofing Session hijacking DoS DDoS Attacks 54 IP address spoofing (1) SA: 36.220.9.59 DA: 212.68.212.7 145.13.145.67 212.68.212.7 Attacker doesn’t want actions traced back Simply re-configure IP address in Windows or Unix. Or enter spoofed address in an application e.g., decoy packets with Nmap Polytechnic University Attacks 55 IP address spoofing (2) 145.13.145.67 SA: 36.220.9.59 DA: 212.68.212.7 attacker 36.220.9.59 212.68.212.7 victim SA: 212.68.212.7 DA: 36.220.9.59 But attacker cannot interact with victim. Unless attacker is on path between victim and spoofed address. Polytechnic University Attacks 56 IP spoofing with TCP? Can an attacker make a TCP connection to server with a spoofed IP address? Not easy: SYNACK and any subsequent packets sent to spoofed address. If attacker can guess initial sequence number, can attempt to send commands Send ACK with spoofed IP and correct seq #, say, one second after SYN But TCP uses random initial sequence numbers. Polytechnic University Attacks 57 Defense: Ingress filtering: access ISP 127.32.1.1 x 127.32.1.1 privately administered x Internet 222.22/16 Polytechnic University Attacks 58 Ingress Filtering: Upstream ISP (1) 12.12/24 regional ISP BGP update: 12.12/24, 34.35/24 34.34/24 tier-1 ISP 56.56/24 BGP update: 56.56/24, 78.78/24 regional ISP 78.78/24 Polytechnic University Attacks 59 Ingress Filtering: Upstream ISP (2) 12.12/24 BGP update: 12.12/24, 34.34/24 Filter all but 12.12/24 and 34.34/24 34.34/24 56.56/24 BGP update: 56.56/24, 78.78/24 Filter all but 56.56/24 and 78.78/24 78.78/24 Polytechnic University Attacks 60 Ingress Filtering: Upstream ISP (3) 12.12/24 regional ISP 56.56.1.1 x Filter all but 12.12/24 and 34.34/24 34.34/24 tier-1 ISP Filter all but 56.56/24 and 78.78/24 56.56/24 regional ISP 78.78/24 Polytechnic University Attacks 61 Ingress Filtering: Upstream ISP (3) 12.12/24 34.34.1.1 regional ISP Filter all but 12.12/24 and 34.34/24 34.34/24 spoofed packet gets through! tier-1 ISP Filter all but 56.56/24 and 78.78/24 56.56/24 regional ISP 78.78/24 Polytechnic University Attacks 62 Ingress filtering: summary Effectiveness depends on widespread deployment at access ISPs Deployment in upstream ISPs helps, but does not eliminate IP spoofing Filtering can impact router forwarding perf Even if universally deployed at access, hacker can still spoof another address in its access network 12.12/24 See RFC 2827 “Network Ingress Filtering: Defeating DDoS” Polytechnic University Attacks 63 Attacks & Hacker Tools Before talking about defenses, need to look at network from attacker’s perspective Reconnaissance Network mapping Port scanning Sniffing Polytechnic University IP address spoofing Session hijacking DoS DDoS Attacks 64 Session hijacking Take control of one side of a TCP connection Marriage of sniffing and spoofing Alice telnet Bob Alice Attacker Polytechnic University Attacks 65 Session hijacking: The details Attacker is on segment where traffic passes from Alice to Bob Attacker sniffs packets Sees TCP packets between Bob and Alice and their sequence numbers Attacker jumps in, sending TCP packets to Bob; source IP address = Alice’s IP address Bob now obeys commands sent by attacker, thinking they were sent by Alice Principal defense: encyrption Attacker does not have keys to encrypt and insert meaningful traffic Polytechnic University Attacks 66 Session hijacking: limitation 2. to resync, Alice sends segment with correct seq # 1. weird ACK # for data never sent Alice Bob is getting segments from attacker and Alice. Source IP address same, but seq #’s different. Bob likely drops connection. Polytechnic University Attacker Bob Attacker’s solution: • Send unsolicited ARP replies to Alice and Bob with non-existent MAC addresses • Overwrite IP-to-MAC ARP tables • Alice’s segments will not reach Bob and vice-versa • But attacker continues to hear Bob’s segments, communicates with Bob Attacks 67 Session Hijacking Tools: Hunt http://lin.fsid.cvut.cz/~kra/index.html Provides ARP poisoning Netcat General purpose widget Very popular Polytechnic University Attacks 68 Denial-of-Service Prevent access by legitimate users or stop critical system processes Vulnerability attack: Send a few crafted messages to target app that has vulnerability Malicious messages called the “exploit” Remotely stopping or crashing services Connection flooding Overwhelming connection queue with SYN flood Bandwidth flooding attack: Polytechnic University Overwhelming communications link with packets Strength in flooding attack lies in volume rather than content Attacks 69 DoS and DDoS DoS: source of attack small # of nodes source IP typically spoofed DDoS From thousands of nodes IP addresses often not spoofed Good book: Internet Denial of Service by J. Merkovic, D. Dittrich, P. Reiher, 2005 Polytechnic University Attacks 70 Interlude: IP datagram format 32 bits header length (bytes) “type” of data max number remaining hops (decremented at each router) upper layer protocol to deliver payload to type of ver head. len service length fragment 16-bit identifier flgs offset upper time to Internet layer live checksum total datagram length (bytes) for fragmentation/ reassembly 32 bit source IP address 32 bit destination IP address Options (if any) data (variable length, typically a TCP or UDP segment) Polytechnic University Attacks 71 IP Fragmentation and Reassembly Example 4000 byte datagram MTU = 1500 bytes 1480 bytes in data field offset = 1480/8 Polytechnic University length ID fragflag offset =4000 =x =0 =0 One large datagram becomes several smaller datagrams length ID fragflag offset =1500 =x =1 =0 length ID fragflag offset =1500 =x =1 =185 length ID fragflag offset =1040 =x =0 =370 Attacks 72 DoS: examples of vulnerability attacks Land: sends spoofed packet with source and dest address/port the same Ping of death: sends oversized ping packet Jolt2: sends a stream of fragments, none of which have offset of 0. Rebuilding consumes all processor capacity. Polytechnic University Teardrop, Newtear, Bonk, Syndrop: tools send overlapping segments, that is, fragment offsets incorrect. Patches fix the problem, but malformed packet attacks continue to be discovered. Attacks 73 Connection flooding: Overwhelming connection queue w/ SYN flood (1) Recall client sends SYN packet with initial seq. number when initiating a connection. TCP on server machine allocates memory on its connection queue, to track the status of the new halfopen connection. For each half-open connection, server waits for ACK segment, using a timeout that is often > 1 minute Polytechnic University Attack: Send many SYN packets, filling connection queue with half-open connections. Can spoof source IP address! When connection queue is exhausted, no new connections can be initiated by legit users. Need to know of open port on victim’s machine: Port scanning. Attacks 74 DoS: Overwhelming connection queue with SYN flood (2) amateur attack: attacker Connection queue freed up with RST segment victim Alice Polytechnic University Expert attack: Use multiple source IP addresses, each from unresponsive addresses. Attacks 75 SYN flood defense: SYN cookies (1) SYN with ISNA Host A SYN-ACK with ISNB= cookie Host B When SYN segment arrives, host B calculates function (hash) based on: Source and destination IP addresses and port numbers, and a secret number Host B uses resulting “cookie” for its initial seq # (ISN) in SYNACK Host B does not allocate anything to half-open connection: Does not remember A’s ISN Does not remember cookie Polytechnic University Attacks 76 SYN flood defense: SYN cookies (2) If SYN is legitimate Host A returns ACK Host B computes same function, verifies function = ACK # in ACK segment Host B creates socket for connection Legit connection established without the need for half-open connections Polytechnic University If SYN-flood attack with spoofed IP address No ACK comes back to B for connection. No problem: B is not waiting for an ACK What if Host A sends only ACK (no SYN)? Will host B establish a connection? Attacks 77 Overwhelming link bandwidth with packets Attack traffic can be made similar to legitimate traffic, hindering detection. Flow of traffic must consume target’s bandwidth resources. Attacker needs to engage more than one machine => DDoS May be easier to get target to fill-up its upstream bandwidth: async access Example: attacking BitTorrent seeds Polytechnic University Attacks 78 Distributed DoS: DDos bot Attacker takes over many machines, called “bots”. Potential bots are machines with vulnerabilities. bot attacker Internet victim bot bot processes wait for command from attacker to flood a target bot Polytechnic University Attacks 79 DDoS: Reflection attack DNS server reply request request DNS server reply request attacker reply DNS server victim request reply Source IP = victim’s IP DNS server Polytechnic University Attacks 80 DDoS: Reflection attack Spoof source IP address = victim’s IP Goal: generate lengthy or numerous replies for short requests: amplification Without amplification: would it make sense? January 2001 attack: requests for large DNS record generated 60-90 Mbps of traffic Reflection attack can be also be done with Web and other services Polytechnic University Attacks 81 DDoS Defenses Don’t let your systems become bots Keep systems patched up Employ egress antispoof filtering on external router. Filter dangerous packets Vulnerability attacks Intrusion prevention systems Polytechnic University Over-provisioning of resources Abundant bandwidth Large pool of servers ISP needs abundant bandwidth too. Multiple ISPs Signature and anomaly detection and filtering Upstream hopefully Rate limiting Limit # of packets sent from source to dest Attacks 82 DNS attacks Reflector attack: already discussed Leverage DNS for attacks on arbitrary targets Denying DNS service Stop DNS root servers Stop top-level-domain servers (e.g. .com domain) Stop local (default name servers) Use fake DNS replies to redirect user Poisoning DNS: Insert false resource records into various DNS caches False records contain IP addresses operated by attackers Polytechnic University Attacks 83 DDos DNS Attack Oct 21, 2002 Ping packets sent from bots to the 13 DNS root servers. Goal: bandwidth flood servers Minimal impact: DNS caching rate limiting at upstream routers: filter ping when they arrive at an excessive rate During attack, some networks filtered pings; corresponding root servers remained up. Root server attack is easy to defend: download root server database to local (default) name servers Not much data in root server; changes infrequently TLD servers are more volatile Similar kind of attack in May 2004, Feb 2007 Polytechnic University Attacks 84 DNS attack: redirecting hub or WiFi 1 network client 2 attacker 1. Client sends DNS query to its local DNS server; sniffed by attacker 2. Attacker responds with bogus DNS reply Polytechnic University local DNS server Issues: • Must spoof IP address: set to local DNS server (easy) •Must match reply ID with request ID (easy) •May need to stop reply from the local DNS server (harder) Attacks 85 Poisoning DNS Cache (1) Poisoning: Attempt to put bogus records into DNS name server caches Bogus records could point to attacker nodes Attacker nodes could phish But unsolicited replies are not accepted at a name server. Name servers use IDs in DNS messages to match replies to queries So can’t just insert a record into a name server by sending a DNS reply message. But can send a reply to a request. Polytechnic University Attacks 86 Poisoning local DNS server (2) authoritative DNS for poly.edu 2. iterative DNS queries 1. DNS query poly.edu=? 3. DNS reply poly.edu= 17.32.8.9 Attacker in Australia: 17.32.8.9 Polytechnic University Local DNS Server (eg, Berkeley) Goal: Put bogus IP address for poly.edu in local Berkeley DNS server 1) Attacker queries local DNS server 2) Local DNS makes iterative queries 3) Attacker waits for some time; sends a bogus reply, spoofing authoritative server for poly.edu. Attacks 87 Poisoning local DNS server (3) authoritative DNS for poly.edu 1. DNS query ftp.poly.edu=? Poisoned local DNS server (eg, Berkeley) 2. DNS query ftp.poly.edu=? Attacker in Australia 17.32.8.9 Polytechnic University DNS response can provide IP address of malicious server! Attacks 88 DNS Poisoning (4) Issues: Attacker needs to know sequence number in request message sent to upstream server • Not easy! Attacker may need to stop upstream name server from responding • So that server under attack doesn’t get suspicious • Ping of death, DoS, overflows, etc Polytechnic University Attacks 89 DNS attacks: Summary DNS is a critical component of the Internet infrastructure But is surprisingly robust: DDoS attacks against root servers have been largely unsuccessful Poisoning and redirection attacks are difficult unless you can sniff DNS requests • And even so, may need to stop DNS servers from replying DNS can be leveraged for reflection attacks against non-DNS nodes Polytechnic University Attacks 90 Attacks & Hacker Tools Before talking about defenses, need to look at network from attacker’s perspective Reconnaissance Network mapping Port scanning Sniffing Polytechnic University IP address spoofing Session hijacking DoS DDoS Attacks 91