* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Recon
Computer network wikipedia , lookup
Parallel port wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Remote Desktop Services wikipedia , lookup
Network tap wikipedia , lookup
Distributed firewall wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Airborne Networking wikipedia , lookup
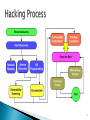
BCIS 4630 Fundamentals of IT Security re·con·nais·sance Dr. Andy Wu Network Scanning ◦ Host discovery ◦ OS fingerprinting ◦ Service discovery Network mapping/Host discovery ◦ DNS zone transfer 2 3 Organizational ◦ ◦ ◦ ◦ ◦ Website Company directory Location, phone numbers, addresses Leadership Employees ◦ ◦ ◦ ◦ Domain name IP address blocks Connectivity devices Rogue websites, wifi routers ◦ ◦ ◦ ◦ User accounts Groups Shares Platforms Network System 4 Social engineering works, for the most part, because people have the innate tendency to help and to avoid confrontation. The success or failure of social engineering depends on the ability of hackers to manipulate human psychology, contacts, and physical workstations. Shoulder surfing Dumpster diving 5 Reconnaissance ◦ The act of locating targets and developing the methods necessary to attack those targets successfully. ◦ May be extremely flexible and creative. ◦ May be tedious and time consuming. Don’t forget the “No-Tech” measures! Reconnaissance is not by definition illegal. ◦ Many reconnaissance techniques are completely legal. 6 Dumpster diving is often the mother lode of sensitive information as well as actual hardware and software. Hackers look specifically for sales receipts and paperwork that contain personal data or credit card information ◦ Shredded documents can lead to data leaks. ◦ Drafts of letters are routinely left whole in the trash. ◦ Company directory sheets, catalog lists, unused or misprinted labels, and policy manuals. 7 Search for company’s information in major search engines, e.g., Google, GoogleMaps, Bing. Using web data extractors, e.g., webextractor.com. Website scraping, e.g., binarypool.com. People search websites, e.g., pipl.com. Social media sites. Reports filed with SEC. 8 Creative use of search keywords Public facing website Guessing internal URLs ◦ ◦ ◦ ◦ marketing.foo.com hr.foo.com foo.com/accounting foo.com/legal 9 Operator Effect [cache:] Pages stored in Google cache [link:] Pages that link to the specific page [site:] Only those pages within the site specified [inurl:] Only results containing the search keyword in the URL [related:] Similar results [info:] Information Google has about the page [intitle:] Only results containing the search keywords in the title 10 http://www.hackersforcharity.org/ghdb/ 11 Tools are available to copy an entire website for later analysis, e.g., ◦ ◦ ◦ ◦ httrack.com surfoffline.com pagenest.com keepni.com Archive.org provides archived versions of websites. 12 www.archive.org 13 Attackers may collect sensitive information about organizations and their employees through social network sites such as Facebook, LinkedIn, Twitter, Pinterest, etc. Clever use of such information may booster attackers’ credibility when they try social engineering on people in the target organization. 14 https://www.scmagazineuk.com/facebook-a-treasure-trove-of-personally-identifiableinformation/article/546127/ 15 Domain name registration information Range of IP addresses assigned to target organization Protocols used Connectivity devices Typology of network DNS info Port scanning allows you to find: ◦ IP addresses and open ports of live hosts ◦ Operating systems and system architecture ◦ Services running on hosts 16 https://www.shodan.io/ 17 WHOIS databases contain personal information of domain owners. They are maintained by regional Internet registries (RIRs): ◦ ◦ ◦ ◦ ◦ AfriNIC (Africa) ARIN (America) APNIC (Asia Pacific) LACNIC (Latin America) RIPE NCC (Europe) Commandline whois tool Whois apps 18 https://www.iana.org/numbers 19 www.whois.com 20 http://whois.domaintools.com/ 21 22 23 24 Helps an attacker to figure out the map of the target network ARIN database RIRs Whois sites 25 26 Domain name service database of a network contains important information about the network hosts, e.g., ◦ ◦ ◦ ◦ ◦ A – Host MX – Mail server NS – Name server Cname – Canonical names (aliases) SOA – Authority of domain 27 DNS Lookup ◦ Tools help Internet users discover the DNS names of target computers. ◦ There are Web sites that provide DNS lookup tools. DNS Zone Transfer ◦ Zone transfer is a DNS feature that lets a DNS server update its database with the list in another DNS server. ◦ An incorrectly configured DNS server may allow any Internet user to perform a zone transfer. ◦ nslookup 28 To lookup the IP address of a FQDN, the command is nslookup <fqdn> 29 To perform a zone transfer, first enter just the command nslookup (without the FQDN argument). Then enter the server command followed by the IP address of the DNS server. Finally, enter the listing command: ls –d <domain_name> 30 https://www.paterva.com/web7/buy/maltego-clients/maltego-ce.php 31 32 ping ◦ Helps to verify whether a host is active. ◦ Command is available for all platforms. ◦ Part of ICMP and uses echo request and echo reply messages. ping sweep ◦ Is used to determine the live hosts from a range of IP addresses but sending ICMP echo requests to multiple hosts. 33 traceroute (tracert on Windows) ◦ A packet from a host makes numerous “hops” before it reaches the destination. ◦ Command can track all of the intermediate nodes. ◦ Uses the TTL field in the header to work. Nmap (Zenmap) ◦ Zenmap is the GUI front of nmap. ◦ Use nmap host discovery switch to perform scanning for live hosts. 34 To obtain a quick list of live hosts on the network without scanning for open ports on each, use the –sP (ping scan) switch. The syntax is: nmap –sP <network ID>/mask ◦ Replace <network ID> with the real network ID. It may be in the FQDN or resolved IP format. ◦ Use the CIDR notation for the mask. 35 OS fingerprinting is the method to determine the operating system running on a remote target system. Passive OS fingerprinting use sniffers to capture packets and analyze them for OS information. ◦ For example, Windows and Linux systems pad the ping packets differently. By looking in the data portion for the padding characters, the attacker can guess the type of OS. 36 Active OS fingerprinting sends specially crafted packets to the remote target and analyze the response. The response are then compared with a fingerprint database to determine the OS running on the remote machine. Use OS fingerprinting switch in Nmap to perform OS fingerprinting. 37 Nmap may be used to fingerprint the OS running on the target. The switch is –O. 38 The attacker then will look up whether there are known vulnerabilities in the service. Chances are, some vulnerabilities have been found and reported, and often times, tools have been created to take advantage of those vulnerabilities. If the attacker runs those tools, he/she has a good chance of compromising the target. Service discovery is a critical step in the hacking process. 39 Each network service is allocated a wellknown port number. If the service is running on the server, the port must be open. The reverse is true too – if a port is found open on the server, the attacker can deduce that the server is running the service. The same goes for many registered ports that are related to common applications, e.g., Port 3306 for MySQL. 40 Switch Scan Type -sS SYN scan (default) -sT Connect scan -sN Null scan -sX Xmas scan -O OS fingerprinting -sP Host discovery -p Port range 41 Banner grabbing uses Telnet to connect to a port on the remote target and observes the response coming back from it. Different protocols (services) have distinctive responses that can be used to verify the existence of those services on the target. ◦ Attacker may be fooled by a honeypot or port emulator. Response may contain OS or service information that may be used to determine the OS running on the target. 42 netstat ◦ Allows all the transmission Control Protocol (TCP), User Datagram Protocol (UDP), and IP connections on a computer to be viewed. ◦ Also helps to locate IP address of computers IP addresses of the hosts connected to the computers Port of the host to which a computer is connected 43