* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Denial of Service Resilience in Ad Hoc Networks
Survey
Document related concepts
Transcript
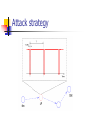
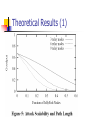
Denial of Service Resilience in Ad Hoc Networks Imad Aad, Jean-Pierre Hubaux, and Edward W. Knightly Designed by Yao Zhao Motivation Do ad hoc networks have sufficiently redundant paths and counter-DoS mechanisms to make DoS attacks largely ineffective? Or are there attack and system factors that can lead to devastating effects? Outline Introduction and system model DoS attacks Analytical model Evaluation Related works Conclusion Introduction to Ad hoc networks System Model (1) Ensure node authentication Ensure message authentication Ensure one identity per node Prevent control plane misbehavior (query floods, rushing attacks) System Model (2) Outline Introduction and system model DoS attacks JellyFish Black holes Analytical model Evaluation Related works Conclusion JellyFish Attack Protocol Compliance Protocols with congestion control such as TCP Just like any IP service, it can: But Drop packets, Reorder packets, Delay / jitter packets in a MALICIOUS way Detection and diagnosis are time consuming! Three attack ways JF Reorder Attack JF Periodic Dropping Attack JF Delay Variance Attack JF Reorder Attack Facts TCP’s use of cumulative acknowledgements All such TCP variants assume that reordering events are rare Attack strategy deliver all packets, yet after placing them in a re-ordering buffer rather than a FIFO buffer. Attack strategy Impact of JF Reorder Attack JF Periodic Dropping Attack Facts If losses occur periodically near the retransmission time out (RTO) timescale (in the 1s range as RTO is intended to address severe congestion), then end-to-end throughput is nearly zero Endpoint attack Attack strategy Periodic dropping attack in which attacking nodes drop all packets for a short duration (e.g., tens of ms) once per RTO Passive Attack strategy Impact of JF Periodic Dropping Attack JF Delay Variance Attack High delay will cause TCP to send traffic in bursts due to “selfclocking,” leading to increased collisions and loss cause mis-estimations of available bandwidth for delay-based congestion control protocols such as TCP Westwood and Vegas, lead to an excessively high RTO value Attack strategy wait a random time before servicing each packet, maintaining FIFO order, but significantly increasing delay variance. Attack strategy Impact of JF Delay Variance Attack Black Hole Attacks (1) Passive Forwards routing packets "Absorbs" all data packets Hard to detect Black Hole Attacks (2) Misbehavior Diagnosis Detection of MAC Layer Failure Passive Acknowledgement (PACK) Cross-layer design in DSR Watchdog Endpoint Detection If severe loss detected Can find the malicious guy? PACK Energy Efficient Transmission: i cannot overhear j Directional Antennas: j pretends to i to forward to k Variable Power: j pretends to i to forward to k Victim Response Establish an alternate path Employ multipath routing Establishment of backup routes Outline Introduction and system model DoS attacks Analytical model Evaluation Related works Conclusion Analytical Model N nodes and pN nodes are JF or Black Holes If the selected nodes represent a random sample of the N network nodes, then the path contains no attacking nodes with probability (1-p)h. Theoretical Results (1) Theoretical Results (2) Outline Introduction and system model DoS attacks Analytical model Evaluation Related works Conclusion Methodology System fairness Number of hops for received packets Total system throughput Probability of interception Baseline 200 nodes move randomly in a 2000m×2000m topology Maximum velocity of 10 m/s, pausing for 10 s on average. (Random Walk) IEEE 802.11 MAC with a node receive range of 250 m. 100 of these nodes communicate with each other to create 50 flows UDP packets are transmitted at a constant rate of 800 bits/s, corresponding to one 500 byte packet every 5 s. JF nodes are placed in grid JF Placement Distribution of the number of hops for received packets Fairness Average number of hops for received packets Extensive simulations Offered Load and TCP JellyFish Placement Mobility Node Density System Size Related Work Securing Routing Protocols Usage of Multiple Routes Securing Packet Forwarding Conclusion TCP collapses with malicious Dropping, reordering, jitter ... More generally, all closed-loop mechanisms are vulnerable to malicious tampering “Protocol-compliance” makes defense more problematic First paper to quantify DoS effects on ad-hoc networks: DoS increases capacity! BUT… Network gets partitioned Fairness decreases System throughput, alone, is not enough to measure DoS impacts