* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download network_layer
SIP extensions for the IP Multimedia Subsystem wikipedia , lookup
IEEE 802.1aq wikipedia , lookup
Asynchronous Transfer Mode wikipedia , lookup
Internet protocol suite wikipedia , lookup
Multiprotocol Label Switching wikipedia , lookup
Dynamic Host Configuration Protocol wikipedia , lookup
Distributed firewall wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Network tap wikipedia , lookup
Computer network wikipedia , lookup
Deep packet inspection wikipedia , lookup
Airborne Networking wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Routing in delay-tolerant networking wikipedia , lookup
Wake-on-LAN wikipedia , lookup
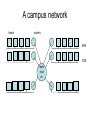
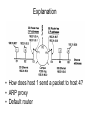
Network Layer and Routing NL responsibility • Main responsibilities – Host to Host delivery. – Finding path to destination. • Services provided to TL, receive from DL – Connectionless and connection oriented services – Identifying source and destination uniquely and thereby use NL address. Fragments TL data if necessary. Uses packet switching (store and forward) with datagram approach. – In the router NL finds the appropriate interface from which it will reach the destination. – At the destination matches the address and check corrupt packets, and assembly fragmented units and then sent to TL Switching • How is a packet sent from one node to another node. – Circuit switching – Packet switching • VC approach – call set up before message transfer • Datagram approach – independent packet, does not need call setup phase. Internet Protocol • Network layer of datagram-oriented network such as internet has three major components: – Network protocol, e.g IP Transport Layer:TCP, UDP – Path determination Protocols: IP Protocols: – Error reporting Routing • path selection •RIP, OSPF, BGP Routing Table • addressing conventions •Datagram format •Packet handling conventions ICMP protocol: • error reporting •Router “signaling” Link Layer Internet structure • At the NL internet can be viewed as a collection of subnets or Autonomous systems (AS) that are interconnected. Internet working • TL takes data streams and breaks them up into datagrams. Datagrams cab be up to 64Kbytes each, but usually not more than 1500 bytes. If necessary the fragments them and sent to internet. When all pieces finally reaches the destination they are reassembled by NL to original datagram. It is then handed over to TL which inserts it into receiving process. IPv4 addressing • IPv4 is 32 bits long • Usually written in dotted decimal notation, eg. 193.32.216.9 • In the globak internet each interface must have a unique IP address. • Network address and host address. • Subnet mask • Meaning of 223.1.1.0/24 IPv4 header 4 bits 4 bits Version IHL 6 bits 16 bits Type of Service Total length D MF F Identification TTL 2 protocol Fragment offset Header checksum Source Add Destination Add options ( 0 or more words) • • • header has 20bytes fixed part and a variable length optional part. Version keeps track of which version of the protocol the datagram belongs to IHL – header length in 32 bit words. minimum IHL = 5 words = 20 bytes. maximum is 15 words. types of service – 6 bit field. voice, text etc. different classes of service. total length – 65,535 bytes including both data and header. • • • • • • • • • • • • Identification – identifies the fragment which datagram it belongs to. An unused bit fields. DF stands for Don’t Fragment. MF stands for More Fragment – all fragments except the last one has this bit set. Fragment offset – where in the current datagram this fragment belongs. there is a maximum 213 fragments per datagram. TTL – counter to limit packet lifetimes in seconds. max. value 255. it must be decremented on each hop, and supposed to be decremented when queued for long time in a router. when it hits 0 the packet is discarded and a warning message is sent back to source. Protocol – TCP or UDP etc. checksum – for header only. source and destination address – IP addresses. Options – security, strict source routing, loose source routing, record routes, timestamp etc. Classful addressing A 0 network B 10 C 110 D 1110 E 1111 1.0.0.0 – 127.255.255.255 Host 128.0.0.0 – 191.255.255.255 Host network network Mutlicast address For future use 192.68.1.20/255.255.255.0 or 192.168.1.20/24 network number or address – 192.68.1.0 host number of address – 20 Broadcast address = 198.68.1.255 Host 192.0.0.0 – 223.255.255.255 224.0.0.0 – 239.255.255.255 240.0.0.0 – 255.255.255.255 Special IP • 0.0.0.0 – this host; used when the machine is booting. • IP address with 0 as the network number refer to the current network. • IP with all 1s allows broadcasting on local network, typically a LAN. • IP address with all 1s in host field allows broadcasting on the remote network that matches the network number. • 127.x.x.x - loopback Transporting a datagram • Addressing and routing • Key fields of IP datagram A 223.1.2.2 223.1.1.4 223.1.2.9 Hub 223.1.1.3 Source IP Desti.IP fields address Data address E 223.1.1.1 223.1.1.2 Misc 223.1.2.1 223.1.3.27 Dest. Net Next router Nhop s 223.1.1.0/24 - 1 223.1.2.0/24 223.1.1. 4 2 223.1.3.0/24 223.1.1. 4 2 Routing table in A B Dest. Net Next router Nhops interface 223.1.1.0/24 - 1 223.1.1.4 223.1.2.0/24 - 1 223.1.2.9 1 223.1.3.27 223.1.3.0/24 Routing table in router • How is this table created in the router? • Internet corporation for Assigned Names and Numbers (ICANN) – manages IP numbers and DNS root servers • ICANN appointed some regional authority called Internet registry who are now responsible for IP address assignment for a particular region – North america: American registry for internet – Reseaux IP Europeans – Asia pacific Network Information center (APNIC) A campus network hosts routers APE CSE main rout er Subnets • Splitting a network into several subnetworks. – Reduced network traffic • Routers create broadcast domains. The smaller broadcast domains you create, the less network traffic on that network segment. – Optimized network performance • This is a result of reduced network traffic – Simplified management • It’s easier to identify and isolate network problems in a group of smaller connected networks than within one gigantic network. – Facilitated spanning of large geographical distances Subnetting example • Let a class B network 130.50.0.0/16 1 0 0 0 0 0 1 0.0 0 1 1 0 0 1 0.0 0 0 0 0 0 0 0.0 0 0 0 0 0 0 0 16 bit 10 network 16 bit subnet host 11111111111111111111110000000000 Number of subnets = 26 = 64, new subnet mask = 255.255.252.0 = 22 bits First subnet address – 130.50.0.0/22 2ndnd subnet address – 130.50.4.0/22 3rd subnet address – 130.50.8.0/22 Last subnet address – 130.50.252.0/22 CIDR • Problem with classfull addressing: • Practice of organizing the address space in classes wastes millions of them. For most organization Class A with 16 million addresses is too big, and a Class C with 256 addresses is too small. However, an organization with 2000 hosts will also waste many IPs if it has a class B network. • Routing table explosion problem: more bits for net address makes larger routing table. • Classless InterDomain Routing • Variable size block without regard to classes. If we need 2000 addresses we will be assigned 2048 address. • The address is written as a.b.c.d/subnet mask in bits. 172.16.4.5/20 • Needs longest prefix match. CIDR example • We are to asked to create an ip block of 2048 addresses starting with 194.24.0.0. • 2048 = 11 bits host • So 21 bits network. 11000010.00011000. 00000000. 00000000 =>194.24.0.0/21 00000000.00000000. 00000111. 11111111 => Complement of the subnet mask OR 11000010.00011000. 00000111.11111111 => 194.24.7.255 /21 Next block of 2048 start from 194.24.8.0/21 to 194.24.15.255/21 Next block of 2048 start from 194.24.16.0/21 to 194.24.23.255/21 However, if you have to allocate a block of 4096 ips to an university, then what would be the range of ips and subnet mask? Internet control protocols • To send some control message, in addition to data, network layer has control protocols like ICMP, ARP, RARP, BOOTP and DHCP. ICMP • When an unexpected event occurs in the network, router informs it by ICMP. • Some important events and corresponding ICMP messages are listed below: Message type Event description Destination unreachable Packet could not be delivered. DF bit set, small packet network on the way. Time exceeded TTL field hit 0 Parameter problem Invalid header field Source quench Choke packet. Receiver slow down the sending rate. Redirect Teach a router about geography. Packet seems to be routed wrong. Echo Ask if the machine is alive Echo reply Yes, I am alive Timestamp request Same as echo but with timestamp Timestamp reply Same as echo reply, with timestamp ARP • Address Resolution Protocol – used to get the physical address of a host. – Ethernet physical address is called MAC address: 48 bits long. e.g. 00.1c.3d.6f.23.a8 • How does the IP addresses get mapped onto physical address? – Source machines IP software sends a broadcast message asking “who has IP 192.31.65.5? Tell 192.31.65.7” this is called ARP broadcast. – Only machine with ip 192.31.65.5 reply with its MAC address (say, E2) to machine with IP 192.31.65.7 • ARP table – cache the address, age after a while Explanation • How does host 1 send a packet to host 4? • ARP proxy • Default router RARP, BOOTP,DHCP • Reverse Address Resolution Protocol. – Used to get ip by a newly-booted machine. – No more usage. • Given an IP address what is the physical address? Broadcast message. • RARP broadcast is not routed. • BOOTP – Used to boot a diskless machine over the network. – BOOTP messages are forwarded by the router. – Manual entry of any new machine added in the network. DHCP • Dynamic Host Configuration Protocol. • Special server DHCP server is responsible for offering IP against a MAC request over the network. Allows both manual and automatic assignment. • DHCP relay agent is needed on each LAN. • DHCP DISCOVER (broadcast). • Relay agent relays the discover message as unicast to dhcp server possibly on a distant network. • DHCPOFFER from the servers. • DHCPREQUEST to the selected server. • DHCPACK from the selected server. • Leasing time. Mobile IP Problems: when a machine with an IP goes from one network to another network, packets destined to it still goes to its old network, and is lost. 1. assigning a new ip to a new host is not practical because this would involve a huge information changes in existing databases in the networks. 2. routers with complete IP addresses for routing, instead of just the network; however, this strategy would require each router to have millions of table entries! impractical. IETF working group considers the following goals to be achieved in any solution for the mobile net user: 1. each mobile host must be able to use its home ip address anywhere. 2. software changes to the fixed hosts were not permitted. 3. changes to the router software and tables were not permitted. 4. most packets for mobile hosts should not make detours on the way. 5. no overhead should be incurred when a mobile host in at home. every site that wants to allow its user to roam has to create a home agent. every site that wants to allow visitors has to create a foreign agent. when a mobile host shows up at a foreign site, it contacts the foreign agent there and registers. the foreign agent then contacts the user’s home agent and gives it a care of address, normally the foreign agent’s won IP address. when a packet arrives at the user’s home LAN, it comes in at some router attached to the lan. the router then tries to locate the host in the usual way, by broadcasting an ARP packet asking, ethernet address of the host. the home agent responds to this query by giving his its own ethernet address. the router then sends the packet for the mobile host to the home agent. It, in turn, tunnels then to the careof-address by encapsulating then in the payload field of an iP packet addressed to the foreign agent. the foreign agent then decapsulates and delivers them to the data link address of the mobile host. In addition the home agent gives the care of address to the sender, so future packets can be tunneled directly to the foreign agent.