* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download firewalls - Faculty Personal Homepage
Airborne Networking wikipedia , lookup
Asynchronous Transfer Mode wikipedia , lookup
Net neutrality law wikipedia , lookup
Multiprotocol Label Switching wikipedia , lookup
Network tap wikipedia , lookup
Wireless security wikipedia , lookup
Computer network wikipedia , lookup
TCP congestion control wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Internet protocol suite wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Proxy server wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
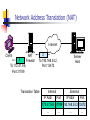
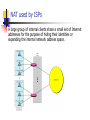
Firewall Technology Firewall Technology - Outline Defining the types of firewalls. Developing a firewall configuration. Designing a firewall rule set. Firewall: Origin of the Term Since old days, brick walls were built between buildings in apartment complexes so that if a fire broke out, it would not spread from one building to another. Quite naturally, the walls were called " firewalls ". Castle and Moat Analogy A network firewalls is more like the moat around a castle than a firewall Restricts access from the outside Restricts outbound connections (i.e. filter out undesirable activity from internal hosts) Overview A firewall is a network access control device. It can perform a centralized security management function. It denies all traffic except that which is explicitly allowed. It can be configured based on services, source or destination IP address, User ID, … etc. Why use Firewalls? Prevent denial of service attacks: SYN flooding: attacker establishes many bogus TCP connections, no resources left for “real” connections. Prevent illegal modification/access of internal data. e.g., attacker replaces Company's homepage with something else Allow only authorized access to inside network (set of authenticated users/hosts) Prevent insider attacks on critical systems: Critical systems (human resources, payroll, etc.) can be hidden behind their own firewalls to prevent attacks from the inside. The Unprotected Network Web Server Internet Router What could possibly be wrong with this setup? Hackers paradise & administrators nightmare! What Can We Do? Firewalls give good protection against attacks from the Internet. The problem is that there are various firewall techogies and deployment strategies. To choose the right solution, we need to know a bit more about the underlying TCP/IP protocols used on the Internet. The TCP/IP-Protocol stack The IP-protocol Important fields: Source Address, Destination Address, Protocol The TCP-protocol Important fields: Source Port and Destination Port ACK and SYN flags The UDP-protocol Important fields: Source Port and Destination Port Common Ports and Services Windows: %windir%\System32\drivers\etc\services Linux: /etc/services Examples: SMTP = port 25 HTTP = port 80 POP3 = port 110 PPTP = port 1723 Types of Firewalls Packet filtering firewall (network layer) Statefull Inspection firewall (connection state of the transport layer protocol) Application layer firewall (known as Application Gateway or Proxy) Hybrid: combination of the above or a generic service proxy (i.e. a Socks Proxy work for all TCP-based apps). Packet Filter Firewalls (Chokes)Should arriving packet be allowed in? Departing packet let out? Internet They are IP routers restricting flow of packets between an internal network and external networks. packet-by-packet decision to forward/drop based on: Source/Destination IP Addresses Protocol Value (i.e. drop ICMP packets) TCP/UDP Source Port/Destination Port TCP SYN and ACK bits Packet Filtering Examples Example 1: Block incoming and outgoing datagrams with IP protocol field = 17 or with either source or destination port = 23. All incoming and outgoing UDP flows and telnet connections are blocked. Example 2: Block inbound TCP segments with (SYN=1 & ACK=0). Prevents external clients from making TCP connections with internal clients, but allows internal clients to connect to outside. Packet Filter Firewall - Pros They are fast because they operate on IP addresses and TCP/UDP port numbers alone, ignoring the data part of packets. Due to the fact that packet payload is ignored, application independence exists. Least expensive of the three types of firewalls. Packet filtering rules are relatively easy to configure. There are no configuration changes necessary to the protected workstations. Packet Filter Firewall - Cons Allow a direct connection between endpoints through the firewall. This leaves the potential for a vulnerability to be exploited. There is no screening of packet payload available. It is impossible to block users from visiting web sites deemed off limits, for example. Logging of network traffic includes only IP addresses and TCP/UDP port numbers, no packet payload information is available. Complex firewall policies are difficult to implement using filtering rules alone. Rely on IP addresses for authentication rather than user authentication. Stateful packet inspection It is an advanced packet filter that keeps track of the state of the network connections going through it. Take into account the state of the connection; an incoming packet is matched to its outbound request for the packet to be allowed in. Examine and filter based on packet content; for example, drop incoming mail with certain type of attachments Stateful packet inspection - Pros Offers improved security over basic packet filters due to packet examination. Offers a degree of application independence, based on level of stateful packet examination. Better logging of activities over basic packet filters. Good performance. Configuration changes to the protected workstations are unnecessary. Stateful packet inspection - Cons Allow a direct connection between endpoints through the firewall. This leaves the potential for a vulnerability to be exploited. No hiding of your private systems. Setting up stateful packet examination rules is more complicated. Only supported protocols at the application layer. No user authentication. Application Gateway (Proxy) Firewalls Typically, an application proxy is a program that runs on a MULTI-HOMED HOST and emulates both client and server ends of some application protocol. For example, an HTTP proxy (web proxy) acts as an HTTP server for local users and an HTTP client for web servers on the Internet. Application Gateway (Proxy) Firewall Application Gateway (Proxy) Firewall connections Application Gateway creates an illusion Characteristics of Proxy Firewalls Outbound connections terminate on the firewall. A set of policy rules defines how traffic from one network is transported to any other. If no rule exists, firewalls deny or drop the data packets. Policy rules are enforced through the use of proxies. Each protocol on a firewall must have its own proxy. Proxy/Gateway Firewall Example host-to-gateway telnet session Example: allow select internal users to telnet outside. application gateway router and filter 1. Require all telnet users to telnet through gateway. 2. For authorized users, gateway sets up telnet connection to destination host. Gateway relays data between the two connections. 3. Router packet filter blocks all telnet connections not originating from gateway. Application proxies - Pros end points do not communicate directly with one another. A vulnerability in a protocol which could slip by a packet filter or stateful packet inspection firewall could be overcome by the proxy program. Provide content filtering capability. Hide internal addresses. Web Proxy often do caching to improve response and reduce load on the Internet link Robust user authentication. Offers logging and auditing of user’s activities on the Internet . Policy rules are usually easier than packet filtering rules. (i.e. amount and timing of communication) Application proxies - Cons Performance problems; much slower than the other two Must have a proxy for every protocol. Failure to have a proxy may prevent a protocol from being handled correctly by the firewall. TCP is the preferred transport. UDP may not be supported. Limited transparency, clients may need to be modified. Setting up the proxy server in a browser, for example. No protection from all protocol weaknesses. Hybrids Hybrid firewalls provide a way for handling protocols for which specific proxies do not exist. The generic services proxy (GSP) allows application layer proxies to handle other protocols. In a hybrid system, the GSP behaves like packet filtering firewalls. Developing a Firewall Configuration Screened Host Configuration. Screened Subnet Configuration. Dual Firewall Configuration. Screened Host Configuration Gateway/Proxy firewall internal network Internet Packet filter firewall Built using a packet filter firewall and a gateway/proxy firewall The gateway is a specially chosen computer running network servers and proxy servers. Only external packets destined for the gateway are allowed through the packet filter firewall. All internal packets destined for outside must go through a proxy server; otherwise, they are dropped by the packet filter firewall. Screened Subnet Configuration SMTP Server Proxy firewall internal network Internet Packet filter firewall Use a single packet filtering firewall with three network interface cards Place systems that need to be accessed from outside on a network separate from the internal network Dual Firewall Configuration gateway FW 1 DMZ network Internet FW 2 For higher security, two chokes and a gateway are used The external choke and gateway are configured as in a screened host firewall. The second choke is a failsafe – if an attacker gains access to the gate, the internal choke prevents further attacks against the internal network. Internet accessible servers are placed in the DMZ (DeMilitarized Zone) network between FW1 and FW2. SOHO Configuration Internet Service Provider Ethernet Switch UTP UTP User PC UTP Broadband Modem (DSL or Cable) SOHO Router --Router DHCP Sever, NAT Firewall, and Limited Application Firewall Many Access Routers Combine the Router and Ethernet Switch in a Single Box User PC User PC Developing a Firewall Configuration Organization’s Internet policy allows users to use services such as HTTP, HTTPS, FTP, Telnet, and SSH. Based on the Internet policy, a set of policy rules for various architectures can be constructed. Designing a Firewall Rule Set When designing a firewall rule set, the first match algorithm dictates: The most specific rules to be placed at the top of the rule set. The least specific rules to be placed at the bottom of the rule set. Designing a Firewall Rule Set To define a general rule set, examine: The expected traffic load of the firewall. Rank the traffic types in order. The Internet service with the largest traffic at the top of the rule set. Place any deny rules pertaining to the protocol. Firewall Rule Set: Special Rules To define a general rule set, examine: Cleanup Rule – deny everything not explicitly allowed: Cleanup rule is always the last (bottommost) rule Stealth Rule : to protect firewall itself Fom any any To any any – Deny From any any To firewall any – Deny Stealth Rule is placed first (topmost) rule Internet Accessible Systems Firewall Rules for Internet Systems Accessible Outside the Firewall. Single Firewall Architecture #2: Single firewall. Single Firewall - Rule Set Firewall Rules for the Single Firewall Architecture. Dual Firewalls Architecture #3: Dual Firewalls. Dual Firewalls Firewall Rules for Firewall #1 in the Dual Firewall Architecture. Dual Firewalls Firewall Rules for Firewall #2 in the Dual Firewall Architecture. NAT and PAT Because the firewall keeps track of all live connections through it, the firewall is able to make both NAT and PAT, or any combination thereof. NAT: Network Address Translation PAT: Port Address Translation A firewall performing NAT or PAT is often referred to as a masquerading firewall. NAT Explained A NAT firewall hides internal IP addresses by replacing internal source IP address of an outgoing packet to that of the firewall device (e.g. – see figure - 200.24.5.8). Allow hosts with private IP addresses (not-Internetregistered) to access the Internet. NAT Explained The NAT device replaces the source IP address in an outgoing packet by its own address and saves some information to enable reverse translation for the reply packet that come back from the Internet Network Address Translation (NAT) From 172.47.9.6, Port 31789 From 192.168.34.2, 1 Port 13472 2 Internet Client NAT Firewall Translation Table Server Host Internal External IP Addr Port IP Addr Port 172.47.9.6 31789 192.168.34.2 13472 … … … … Network Address Translation (NAT) Internet Client NAT 4 Firewall To 172.47.9.6, Port 31789 3 To 192.168.34.2, Port 13472 Translation Table Server Host Internal External IP Addr Port IP Addr Port 172.47.9.6 31789 192.168.34.2 13472 … … … … NAT used by ISPs A large group of internal clients share a small set of Internet addresses for the purpose of hiding their identities or expanding the internal network address space. Loading Balancing Translation A single IP address and port is translated to a pool of identically configured servers so that a single public address can be served by a number of servers.