* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Security in VoIP - Florida Atlantic University
Technological convergence wikipedia , lookup
Airborne Networking wikipedia , lookup
Wireless security wikipedia , lookup
Net neutrality law wikipedia , lookup
Computer security wikipedia , lookup
Computer network wikipedia , lookup
SIP extensions for the IP Multimedia Subsystem wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Internet protocol suite wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Deep packet inspection wikipedia , lookup
Distributed firewall wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
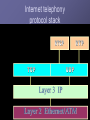
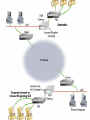
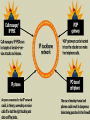
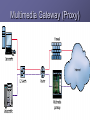
Security in VoIP Networks Juan C Pelaez Florida Atlantic University What is VoIP? VoIP (Voice over Internet Protocol), sometimes referred to as Internet telephony, is a method of digitizing voice, encapsulating the digitized voice into packets and transmitting those packets over a packet switched IP network. Overview of VoIP(1) VoIP enables people to use the Internet as the transmission medium for telephone calls. For users who have free, or fixed-price, Internet access, Internet telephony software essentially provides free telephone calls anywhere in the world. To date, however, Internet telephony does not offer the same quality (easy target of security attacks) of telephone service as direct telephone connections. Overview of VoIP(2) VoIP: yet another Internet service (Telephone, Radio, Video) over IP Services: email/web/calendar integration, emergency services, call scheduling, Interactive Voice Response (IVR), instant messaging, personal mobility… VoIP Protocols Most implementations use H.323 protocol – Same protocol that is used for IP video. – Uses TCP for call setup – Traffic is actually carried on RTP (Real Time Protocol) which runs on top of UDP. SIP defines a distributed architecture for creating multimedia applications, including VoIP VoIP = Transport + QoS + Signaling Transport : RTP QoS : RTCP (Real-Time Transport Protocol) Signaling: H.323, SIP, MGCP/Megaco Internet telephony protocol stack H.323 Signaling and Media Channels H.225.0/RAS Channel RAS(Registration, Admission & Status) control between Endpoints (terminals, gateways, MCUs) and its Gatekeeper H.225.0 Call Signaling Channel Call remote endpoint Establish H.245 address H.245 Control Channel Open control channel; Terminal capability negotiation Open/close logical channels Establish UDP ports for A/V RTP/RTCP Logical Channels for Media Stream Carry media (audio, video, data, etc.) data within logical channels H.323 VoIP Components H.323 defines four logical components Terminals, Gateways, Gatekeepers and Multipoint Control Units (MCUs). Terminals, gateways and MCUs are known as endpoints. IP telephony Public Switched Telephone Network PSTN PSTN Gateway Call Signaling (RAS) Call Processing IP PBX Call Control Call Setup Media Exchange VoIP requires…. Handsets Softphones Gateways Gatekeepers Conference Bridge IP PBX H.323, SIP, MGCP/Megaco VoIP requires….(Cont.) Gatekeeper IP PBX PSTN PSTN GATEWAY MCU SOFTPHONES Security Threats and Defense Mechanisms Denial-of-service (DOS) - Separation of the voice and data segments using VPNs Call interception (Invasion of privacy) - Encrypt VOIP traffic where possible - Lawful interception Call Interception - Example Security Threats and Defense Mechanisms(2) Theft of service (Traditional fraud) - Getting free service or free features - Use strong authentication - Call-processing Manager will not allow unknown phones to be configured Signal protocol tampering -capture the packets that set up the call. -user could manipulate fields in the data stream and make VOIP calls without using a VOIP phone. Other Security Threats and Defense Mechanisms Masquerading/Man-in-the-middle attacks Endpoint authentication Spoofing/connection hijacking User/message authentication and integrity Message manipulation Message authentication Virus and Trojan-horse applications -Host based virus scanning Repudiation - Call-processing manager Scope of H.235 AV applications Audio Video G.xxx H.26x Encryption RTP Auth. Terminal control and management RTCP H.225.0 Terminal To GK Signaling H.225.0 Call Signaling (Q.931) Transport Security (TLS) (RAS) Unreliable Transport/UDP, IPX H.245 Call Control Reliable Trans./TCP Network Layer/IP, Network Security/IPsec Link Layer Physical Layer Challenges for IP Telephony NAT/Firewall Traversal Problem NAT= Network Address translation IP Telephony uses UDP as transmission protocol IP Telephony uses dynamic port address For these protocols to pass the firewall, the specific static and the range of dynamic ports must be opened for all traffic. IP addresses are embedded in the payload NAT only handles outgoing connections NAT/Firewall Traversal Issue Signaling & Control Transient Ports X Out-bound Media Capabilities and RTP In-bound Media and RTP Firewall/NAT Solutions (1) Proxies (Multimedia Gateway) - Designed to handle real-time communications Gateways - Converts from IP to PSTN voice Application Level Gateways (ALG) - Firewalls programmed to understand IP Protocols Demilitarized Zone (DMZ) - Overcomes problem by placing a MCU Multimedia Gateway (Proxy) Firewall/NAT Solutions (2) Virtual Private Network (VPN) A secure connection between two points across the Internet Tunneling The process by which VPNs transfer information by encapsulating traffic in IP packets and sending the packets over the Internet Conclusion VoIP just adds - more assets, more threat locations, more vulnerabilities – to the data network, because of new equipment, protocols, and processes on the data network To increase security and performance it’s recommended to use VPNs to separate VoIP from data traffic. Instead of using VPN segmentation, users may consider using a multimedia gateway or reverse proxy.