* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Routing Theory Part 2
Net neutrality wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Backpressure routing wikipedia , lookup
Network tap wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Wake-on-LAN wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Net neutrality law wikipedia , lookup
Multiprotocol Label Switching wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Computer network wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Airborne Networking wikipedia , lookup
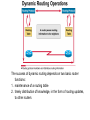
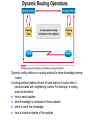
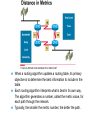
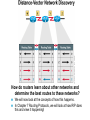
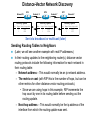
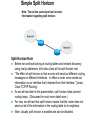
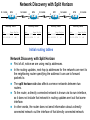
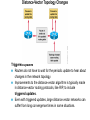
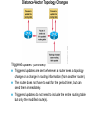
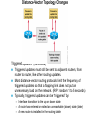
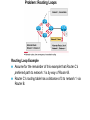
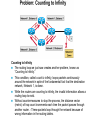
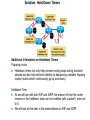
Ch. 6– Routing Theory – Part 2 CCNA Semester 2 Originally by Rick Graziani, Instructor Modified by Prof. Yousif Ch. 6 Routing - Part II Routing Theory and The success of dynamic routing depends on two basic router functions: 1. maintenance of a routing table 2. timely distribution of knowledge, in the form of routing updates, to other routers Dynamic routing relies on a routing protocol to share knowledge among routers. A routing protocol defines the set of rules used by a router when it communicates with neighboring routers. For example, a routing protocol describes: how to send updates what knowledge is contained in these updates when to send this knowledge how to locate recipients of the updates When a routing algorithm updates a routing table, its primary objective is to determine the best information to include in the table. Each routing algorithm interprets what is best in its own way. The algorithm generates a number, called the metric value, for each path through the network. Typically, the smaller the metric number, the better the path. These metrics will be discussed later or in CCNP Advanced Routing, with their appropriate Routing Protocols: RIP – hop count IGRP – bandwidth, delay, reliability, load EIGRP – bandwidth, delay, reliability, load OSPF – bandwidth BGP – attribute values and shortest path Most routing algorithms can be classified as one of two basic algorithms: distance vector link state. The distance-vector routing approach determines the direction (vector) and the cost or metric (distance) to any link in the internetwork. RIP, IPX RIP and IGRP (CCNA) AppleTalk, RTMP and others (non-CCNA) The link-state (also called shortest path first) approach re-creates the exact topology of the entire internetwork (or at least the portion in which the router is situated). OSPF IS-IS The balanced hybrid approach combines aspects of the link-state and distance-vector algorithms. These are really distance-vector routing protocols which apply some of the advantages of a link-state routing protocols, and also known as advanced-distancevector routing protocols. EIGRP When all routers in an internetwork are operating with the same knowledge, the internetwork is said to have converged. Fast convergence is a desirable network feature because it reduces the period of time in which routers would continue to make incorrect/wasteful routing decisions. Topics – (Continued) Part II. Routing Theory and Dynamic Routing Operations Dynamic Routing Operations – Routing Metrics – Classes of Routing Protocols – Convergence Distance Vector Routing Protocols – Distance Vector Concepts – Distance Vector Network Discovery – Simple Split Horizon (Introduction) – Distance Vector Network Discovery with Split Horizon – Network Discovery FAQs – Triggered Updates – Routing Loops – Count to Infinity – Defining a Maximum – Split Horizon – Split Horizon with Poison Reverse – Holddown Timers – TTL – IP’s Time-To-Live Field Distance Vector Concepts The mathematical basis of the distance-vector routing protocols is the Bellman-Ford algorithm. Pure distance-vector routing protocols suffer from long convergence times and possible temporary routing loops (more in a few moments). There are remedies to some situations that may cause these problems which we will examine in a moment. 172.16.0.0/16 Network Discovery and Routing Table Maintenance Distance-vector-based routing algorithms pass periodic copies of a routing table between adjacent routers, from router to router. (RIP every 30 seconds, IPX RIP every 60 seconds, IGRP every 90 seconds). These regular updates between routers help routers discover each other’s networks and communicate topology changes. Routers only learn about other networks from adjacent routers, their directly connected neighbors. Router D learned about Router A’s network 172.16.0.0/16 from Router C, who learned it from Router B, who learned it from Router A. This is why distance-vector routing protocols are also known as routing by rumor. Distance-vector routing protocols do not allow routers to know the topology of the network, as they only know how far a network is (distance: hops) and which way to forward the packet (vector: exit interface). (Link-state routing protocols allow routers to see the exact network topology – later.) – Distances (hops) are cumulative from one router to the next How do routers learn about other networks and determine the best routes to these networks? We will now look at the concepts of how this happens. In Chapter 7 Routing Protocols, we will look at how RIP does this and view it happening! Distance-Vector Network Discovery RTA Network W Network X Routing Table (Distance) (Vector) Net. Hops Exit-int. W 0 <-X 0 --> RTB Network Y Routing Table (Distance) (Vector) Net. Hops Exit-int. X 0 <-Y 0 --> RTC Network Z Routing Table (Distance) (Vector) Net. Hops Exit-int. Y 0 <-Z 0 --> Initial Routing Tables The first routes entered in the routing table are directly connected networks, assigning a metric or cost of “0” (hop count for RIP). – See previous slides on IP Routing Table and Directly Connected Networks. – – 00:28:56: RT: add 192.168.2.0/24 via 0.0.0.0, connected metric [0/0] 00:28:56: RT: interface Ethernet0 added to routing table Remember, these interfaces must be “up” and “up” The next step is for routers to share their complete routing tables with any and all directly connected neighboring routers. Distance-vector routing protocols do not maintain formal relationships with neighboring routers, I.e. they do not know who their neighboring routers are. So how do they know who to send their routing tables to? Distancevector routing protocols use a broadcast or multicast address to send out routing updates, although you can specify a unicast address. (later) Distance-Vector Network Discovery RTA Network W Routing Update Net. Hops Next-hop-add W 1 RTA X 1 RTA Network X RTB Network Y Routing Update Net. Hops Next-hop-add X 1 RTB Y 1 RTB RTC Network Z Routing Update Net. Hops Next-hop-add Y 1 RTC Z 1 RTC Sent via broadcast or multicast (later) Sending Routing Tables to Neighbors (Later, we will see another example with real IP addresses.) In their routing updates to the neighboring router(s), distance-vector routing protocols include the following information for each network in their routing table: – Network address – This would normally be an ip network address. – The metric or cost (with RIP this is the number of hops, but can be other metrics for other distance-vector routing protocols). • Since we are using hops in this example, RIP increments the hop count by one in its routing table before sending out the routing update. – Next-hop address – This would normally be the ip address of the interface from which the routing update was sent. Distance-Vector Network Discovery RTA Network W Routing Update Net. Hops Next-hop-add W 1 RTA X 1 RTA Routing Table (Distance) (Vector) Net. Hops Exit-int. W 0 <-X 0 --> Y 1 RTB Network X RTB Network Y Routing Update Net. Hops Next-hop-add X 1 RTB Y 1 RTB Routing Table (Distance) (Vector) Net. Hops Exit-int. X 0 <-Y 0 --> W 1 RTA Z 1 RTC RTC Network Z Routing Update Net. Hops Next-hop-add Y 1 RTC Z 1 RTC Routing Table (Distance) (Vector) Net. Hops Exit-int. Y 0 <-Z 0 --> X 1 RTB Routers Update their Routing Tables A router will enter this update into its routing table if: – It is a new route, a network which is not currently in its routing table. – It is an existing route, a network which is currently in its routing table, but this update has a better (smaller) metric (fewer hops). – Note: If the update contains a route to an existing route, with the same metric (hops), but via a different interface, the router may or may not add it to its routing table depending upon whether or not the routing protocol is providing load balancing (later). RIP does provide this. A router will not enter this update into its routing table if: – It is an existing route with a worse metric. Distance-Vector Network Discovery RTA Network W Routing Update Net. Hops Next-hop-add W 1 RTA X 1 RTA New Routing Tables Routing Table (Distance) (Vector) Net. Hops Exit-int. W 0 <-X 0 --> Y 1 RTB Network X RTB Network Y Routing Update Net. Hops Next-hop-add X 1 RTB Y 1 RTB Routing Table (Distance) (Vector) Net. Hops Exit-int. X 0 <-Y 0 --> W 1 RTA Z 1 RTC RTC Network Z Routing Update Net. Hops Next-hop-add Y 1 RTC Z 1 RTC Routing Table (Distance) (Vector) Net. Hops Exit-int. Y 0 <-Z 0 --> X 1 RTB Routers Update their Routing Tables (continued) RTA: Ignores the route to X because it has an existing, better route with a cost=0. Accepts the route to Y because it didn’t exist in the routing table. RTB (from RTA): Accepts the route to W because it didn’t exist in the routing table. Ignores the route to X because it has an existing, better route with a cost=0. RTB (from RTC): Ignores the route to Y because it has an existing, better route with a cost=0. Accepts the route to Z because it didn’t exist in the routing table. RTC: Accepts the route to X because it didn’t exist in the routing table. Ignores the route to Y because it has an existing, better route with a cost=0. Distance-Vector Network Discovery RTA Network W Routing Update Net. Hops Next-hop-add W 1 RTA X 1 RTA Y 2 RTA Network X RTB Network Y Routing Update Net. Hops Next-hop-add X 1 RTB Y 1 RTB W 2 RTB Z 2 RTB RTC Network Z Routing Update Net. Hops Next-hop-add Y 1 RTC Z 1 RTC X 2 RTC Next Round of Routing Updates We have still not reached convergence, because all of the routers do not have complete and accurate network information. Which router does have complete information? Which ones do not? In the next round, routers must forward their new routing tables in the form of routing updates, to their directly connected neighbors. Remember, with the distance-vector routing protocol RIP, the router increments the number of hops in its own routing table by one, before sending out the routing update. - “If it is one hop for me to get there, and you are getting there via me, then it is two hops for you.” Distance-Vector Network Discovery RTA RTB RTC Network W Existing Routing Tables Routing Table (Distance) (Vector) Net. Hops Exit-int. W 0 <-X 0 --> Y 1 RTB Routing Update Net. Hops Next-hop-add W 1 RTA X 1 RTA Y 2 RTA New Routing Tables Routing Table (Distance) (Vector) Net. Hops Exit-int. W 0 <-X 0 --> Y 1 RTB Z 2 RTB Network X Network Y Routing Table (Distance) (Vector) Net. Hops Exit-int. X 0 <-Y 0 --> W 1 RTA Z 1 RTC Routing Update Net. Hops Next-hop-add X 1 RTB Y 1 RTB W 2 RTB Z 2 RTB Routing Table (Distance) (Vector) Net. Hops Exit-int. X 0 <-Y 0 --> W 1 RTA Z 1 RTC Network Z Routing Table (Distance) (Vector) Net. Hops Exit-int. Y 0 <-Z 0 --> X 1 RTB Routing Update Net. Hops Next-hop-add Y 1 RTC Z 1 RTC X 2 RTC Routing Table (Distance) (Vector) Net. Hops Exit-int. Y 0 <-Z 0 --> X 1 RTB W 2 RTB Routers Update their Routing Tables - again RTA: (Advertised Cost Compared to current local cost) Ignores the route to X because it has an existing, better route with a cost=0. Ignores the route to Y because it already has that route, with the same cost. Ignores the route to W because it has an existing, better route with a cost=0. – “I am not going to send you the packet, so you can send it back to me, …” – Later, we will see that split-horizon prohibits this route from being sent. Accepts the route to Z because it didn’t exist in the routing table. Distance-Vector Network Discovery RTA RTB RTC Network W Existing Routing Tables Routing Table (Distance) (Vector) Net. Hops Exit-int. W 0 <-X 0 --> Y 1 RTB Routing Update Net. Hops Next-hop-add W 1 RTA X 1 RTA Y 2 RTA New Routing Tables Routing Table (Distance) (Vector) Net. Hops Exit-int. W 0 <-X 0 --> Y 1 RTB Z 2 RTB Network X Network Y Routing Table (Distance) (Vector) Net. Hops Exit-int. X 0 <-Y 0 --> W 1 RTA Z 1 RTC Routing Update Net. Hops Next-hop-add X 1 RTB Y 1 RTB W 2 RTB Z 2 RTB Routing Table (Distance) (Vector) Net. Hops Exit-int. X 0 <-Y 0 --> W 1 RTA Z 1 RTC Network Z Routing Table (Distance) (Vector) Net. Hops Exit-int. Y 0 <-Z 0 --> X 1 RTB Routing Update Net. Hops Next-hop-add Y 1 RTC Z 1 RTC X 2 RTC Routing Table (Distance) (Vector) Net. Hops Exit-int. Y 0 <-Z 0 --> X 1 RTB W 2 RTB Routers Update their Routing Tables – again (continued) RTB: Ignores all routes from both RTA and RTC, because it already has those routes, with the same costs. No new information. Distance-Vector Network Discovery RTA RTB RTC Network W Existing Routing Tables Routing Table (Distance) (Vector) Net. Hops Exit-int. W 0 <-X 0 --> Y 1 RTB Routing Update Net. Hops Next-hop-add W 1 RTA X 1 RTA Y 2 RTA New Routing Tables Routing Table (Distance) (Vector) Net. Hops Exit-int. W 0 <-X 0 --> Y 1 RTB Z 2 RTB Network X Network Y Routing Table (Distance) (Vector) Net. Hops Exit-int. X 0 <-Y 0 --> W 1 RTA Z 1 RTC Routing Update Net. Hops Next-hop-add X 1 RTB Y 1 RTB W 2 RTB Z 2 RTB Routing Table (Distance) (Vector) Net. Hops Exit-int. X 0 <-Y 0 --> W 1 RTA Z 1 RTC Network Z Routing Table (Distance) (Vector) Net. Hops Exit-int. Y 0 <-Z 0 --> X 1 RTB Routing Update Net. Hops Next-hop-add Y 1 RTC Z 1 RTC X 2 RTC Routing Table (Distance) (Vector) Net. Hops Exit-int. Y 0 <-Z 0 --> X 1 RTB W 2 RTB Routers Update their Routing Tables - again RTC: Ignores the route to X because it already has that route, with the same cost. Ignores the route to Y because it has an existing, better route with a cost=0. Accepts the route to W because it didn’t exist in the routing table. Ignores the route to Z because it has an existing, better route with a cost=0. – “I am not going to send you the packet, so you can send it back to me, …” Distance-Vector Network Discovery RTA Network W Routing Tables Routing Table (Distance) (Vector) Net. Hops Exit-int. W 0 <-X 0 --> Y 1 RTB Z 2 RTB Network X RTB Network Y Routing Table (Distance) (Vector) Net. Hops Exit-int. X 0 <-Y 0 --> W 1 RTA Z 1 RTC RTC Network Z Routing Table (Distance) (Vector) Net. Hops Exit-int. Y 0 <-Z 0 --> X 1 RTB W 2 RTB Convergence! All of the routers now have a consistent and accurate view of the network. Later, we will see how RIP handles this operation. Note: The on-line curriculum has incorrect information regarding split horizon. Split Horizon Rule Before we continue looking at routing tables and network discovery, using real ip addresses, let’s take a look at the split horizon rule. “The effect of split horizon is that a router will send out different routing messages on different interfaces. In effect a router never sends out information on an interface that it learned from that interface.” (Lewis, Cisco TCP/IP Routing) As we will see later in this presentation, split horizon helps prevent routing loops. (Discussed in much more detail soon.) For now, we will see that split horizon means that the router does not send out all of the information in the routing table to its neighbors. Note: Usually, split horizon is enabled and can be disabled. Network Discovery with Split Horizon 10.1.1.0/24 .1 RTA 10.1.2.0/24 .1 .2 s0 s0 e0 RTB 10.1.3.0/24 .1 s1 RTC .2 s0 10.1.4.0/24 .1 .2 s1 s0 RTD .1 10.1.5.0/24 e0 Routing Table Routing Table Routing Table Routing Table Net. Hops Ex-Int 10.1.1.0/24 0 e0 10.1.2.0/24 0 s0 Net. Hops Ex-Int 10.1.2.0/24 0 s0 10.1.3.0/24 0 s1 Net. Hops Ex-Int 10.1.3.0/24 0 s0 10.1.4.0/24 0 s1 Net. Hops Ex-Int 10.1.4.0/24 0 s0 10.1.5.0/24 0 e0 Initial routing tables Network Discovery with Split Horizon First of all, notice we are using real ip addresses. In the routing updates, next-hop ip addresses for the networks are sent to the neighboring router specifying the address it can use to forward packets to. The split horizon rule also affects common networks between two routers. To the router, a directly connected network is known via its own interface, so it does not include that network in routing updates sent out that same interface. In other words, the router does not send information about a directly connected network out the interface of that directly connected network. Network Discovery with Split Horizon 10.1.1.0/24 .1 RTA 10.1.2.0/24 .1 .2 s0 s0 e0 RTB 10.1.3.0/24 .1 s1 .2 s0 RTC 10.1.4.0/24 .1 .2 s1 s0 RTD .1 10.1.5.0/24 e0 Routing Table Routing Table Routing Table Routing Table Net. Hops Ex-Int 10.1.1.0/24 0 e0 10.1.2.0/24 0 s0 Net. Hops Ex-Int 10.1.2.0/24 0 s0 10.1.3.0/24 0 s1 Net. Hops Ex-Int 10.1.3.0/24 0 s0 10.1.4.0/24 0 s1 Net. Hops Ex-Int 10.1.4.0/24 0 s0 10.1.5.0/24 0 e0 Routing Update Next-hop Net. Hops Address 10.1.1.0/24 1 10.1.1.1 -----------------------10.1.2.0/24 1 10.1.1.1 X Routing Update Next-hop Net. Hops Address 10.1.2.0/24 1 10.1.3.1 -----------------------10.1.3.0/24 1 10.1.2.2 Routing Update Next-hop Net. Hops Address 10.1.3.0/24 1 10.1.4.1 -----------------------10.1.4.0/24 1 10.1.3.2 Routing Update Next-hop Net. Hops Address 10.1.4.0/24 1 10.1.4.2 -----------------------10.1.5.0/24 1 10.1.4.2 X Network Discovery with Split Horizon - First Round of Updates “The effect of split horizon is that a router will send out different routing messages on different interfaces. In effect a router never sends out information on an interface that it learned from that interface.” (Lewis) RTA’s routing update sent out serial 0 to RTB Includes the network 10.1.1.0/24 which RTB can reach via 10.1.1.1. Split horizon: Does not include the 10.1.2.0/24 network because that network was learned via serial 0 (interface serial 0, ip address 10.1.1.1 …) – a common network between RTA and RTB. Network Discovery with Split Horizon 10.1.1.0/24 .1 RTA 10.1.2.0/24 .1 .2 s0 s0 e0 RTB 10.1.3.0/24 .1 s1 .2 s0 RTC 10.1.4.0/24 .1 .2 s1 s0 RTD .1 10.1.5.0/24 e0 Routing Table Routing Table Routing Table Routing Table Net. Hops Ex-Int 10.1.1.0/24 0 e0 10.1.2.0/24 0 s0 Net. Hops Ex-Int 10.1.2.0/24 0 s0 10.1.3.0/24 0 s1 Net. Hops Ex-Int 10.1.3.0/24 0 s0 10.1.4.0/24 0 s1 Net. Hops Ex-Int 10.1.4.0/24 0 s0 10.1.5.0/24 0 e0 Routing Update Next-hop Net. Hops Address 10.1.1.0/24 1 10.1.1.1 -----------------------10.1.2.0/24 1 10.1.1.1 X Routing Update Next-hop Net. Hops Address 10.1.2.0/24 1 10.1.3.1 -----------------------10.1.3.0/24 1 10.1.2.2 Routing Update Next-hop Net. Hops Address 10.1.3.0/24 1 10.1.4.1 -----------------------10.1.4.0/24 1 10.1.3.2 Routing Update Next-hop Net. Hops Address 10.1.4.0/24 1 10.1.4.2 -----------------------10.1.5.0/24 1 10.1.4.2 X Network Discovery with Split Horizon - First Round of Updates RTB’s routing update sent out serial 0 to RTA Includes the network 10.1.3.0/24 which RTA can reach via 10.1.2.2. Split horizon: Does not include the 10.1.2.0/24 network. Split horizon blocks the 10.1.2.0/24 update from being sent to RTA with a hop count of “1.” (Note: To keep the diagrams less cluttered, omission of the proper red/blue arrow means split horizon is in affect, same as the “X.”) RTB’s routing update sent out serial 1 to RTC Includes the network 10.1.2.0/24 which RTC can reach via 10.1.3.1. Split horizon: Does not include the 10.1.3.0/24 network. Network Discovery with Split Horizon 10.1.1.0/24 .1 RTA 10.1.2.0/24 .1 .2 s0 s0 e0 RTB 10.1.3.0/24 .1 s1 .2 RTC s0 10.1.4.0/24 .1 .2 s1 s0 RTD .1 10.1.5.0/24 e0 Routing Table Routing Table Routing Table Routing Table Net. Hops Ex-Int 10.1.1.0/24 0 e0 10.1.2.0/24 0 s0 Net. Hops Ex-Int 10.1.2.0/24 0 s0 10.1.3.0/24 0 s1 Net. Hops Ex-Int 10.1.3.0/24 0 s0 10.1.4.0/24 0 s1 Net. Hops Ex-Int 10.1.4.0/24 0 s0 10.1.5.0/24 0 e0 Routing Update Next-hop Net. Hops Address 10.1.1.0/24 1 10.1.1.1 -----------------------10.1.2.0/24 1 10.1.1.1 X Routing Update Next-hop Net. Hops Address 10.1.2.0/24 1 10.1.3.1 -----------------------10.1.3.0/24 1 10.1.2.2 Routing Update Next-hop Net. Hops Address 10.1.3.0/24 1 10.1.4.1 -----------------------10.1.4.0/24 1 10.1.3.2 Routing Update Next-hop Net. Hops Address 10.1.4.0/24 1 10.1.4.2 -----------------------10.1.5.0/24 1 10.1.4.2 X Network Discovery with Split Horizon - First Round of Updates Same with updates from RTC and RTD. Your Turn: Write out the new routing tables for each router after this round. Also, find any mistakes I might have made Network Discovery with Split Horizon 10.1.1.0/24 .1 RTA 10.1.2.0/24 .1 .2 s0 s0 e0 RTB 10.1.3.0/24 .1 s1 .2 s0 RTC 10.1.4.0/24 .1 .2 s1 s0 RTD .1 10.1.5.0/24 e0 Routing Table Routing Table Routing Table Routing Table Net. Hops Ex-Int 10.1.1.0/24 0 e0 10.1.2.0/24 0 s0 Net. Hops Ex-Int 10.1.2.0/24 0 s0 10.1.3.0/24 0 s1 Net. Hops Ex-Int 10.1.3.0/24 0 s0 10.1.4.0/24 0 s1 Net. Hops Ex-Int 10.1.4.0/24 0 s0 10.1.5.0/24 0 e0 Routing Update Next-hop Net. Hops Address 10.1.1.0/24 1 10.1.1.1 -----------------------10.1.2.0/24 1 10.1.1.1 Routing Update Next-hop Net. Hops Address 10.1.2.0/24 1 10.1.3.1 -----------------------10.1.3.0/24 1 10.1.2.2 Routing Update Next-hop Net. Hops Address 10.1.3.0/24 1 10.1.4.1 -----------------------10.1.4.0/24 1 10.1.3.2 Routing Table Routing Table Routing Table Routing Table Net. Hops Ex-Int 10.1.1.0/24 0 e0 10.1.2.0/24 0 s0 10.1.3.0/24 1 10.1.2.2 Net. Hops Ex-Int 10.1.2.0/24 0 s0 10.1.3.0/24 0 s1 10.1.1.0/24 1 10.1.2.1 10.1.4.0/24 1 10.1.3.2 Net. Hops Ex-Int 10.1.3.0/24 0 s0 10.1.4.0/24 0 s1 10.1.2.0/24 1 10.1.3.1 10.1.5.0/24 1 10.1.4.2 Net. Hops Ex-Int 10.1.4.0/24 0 s0 10.1.5.0/24 0 e0 10.1.3.0/24 1 10.1.4.1 X Routing Update Next-hop Net. Hops Address 10.1.4.0/24 1 10.1.4.2 -----------------------10.1.5.0/24 1 10.1.4.2 X Answer – Do your routing tables look like these? Now – What do the next round of routing updates look like? Show the routes which are sent (propagated) and those that are not sent because of split horizon. Network Discovery with Split Horizon 10.1.1.0/24 .1 e0 RTA 10.1.2.0/24 .1 .2 s0 s0 RTB 10.1.3.0/24 .1 s1 .2 RTC s0 10.1.4.0/24 .1 .2 s1 s0 RTD .1 10.1.5.0/24 e0 Routing Table Routing Table Routing Table Routing Table Net. Hops Ex-Int 10.1.1.0/24 0 e0 10.1.2.0/24 0 s0 10.1.3.0/24 1 10.1.2.2 Net. Hops Ex-Int 10.1.2.0/24 0 s0 10.1.3.0/24 0 s1 10.1.1.0/24 1 10.1.2.1 10.1.4.0/24 1 10.1.3.2 Net. Hops Ex-Int 10.1.3.0/24 0 s0 10.1.4.0/24 0 s1 10.1.2.0/24 1 10.1.3.1 10.1.5.0/24 1 10.1.4.2 Net. Hops Ex-Int 10.1.4.0/24 0 s0 10.1.5.0/24 0 e0 10.1.3.0/24 1 10.1.4.1 Routing Update Next-hop Net. Hops Address 10.1.3.0/24 1 10.1.4.1 10.1.2.0/24 2 10.1.4.1 -----------------------10.1.4.0/24 1 10.1.3.2 10.1.5.0/24 2 10.1.3.2 Routing Update Next-hop Net. Hops Address X10.1.4.0/24 1 10.1.4.2 X10.1.3.0/24 2 10.1.4.2 -----------------------10.1.5.0/24 1 10.1.4.2 Routing Update Next-hop Net. Hops Address 10.1.1.0/24 1 10.1.1.1 -----------------------10.1.2.0/24 1 10.1.1.1 X 10.1.3.0/24 2 10.1.1.1 X Routing Update Next-hop Net. Hops Address 10.1.2.0/24 1 10.1.3.1 10.1.1.0/24 2 10.1.3.1 -----------------------10.1.3.0/24 1 10.1.2.2 10.1.4.0/24 2 10.1.2.2 Answer – Do your routing updates look like these? Again, omission of the red/blue arrow means split horizon is in affect. For example, RTB is not sending the route 10.1.1.0/24 to RTA to tell RTA it can get to 10.1.1./24 in 2 hops via RTB. - This would make sense! Split horizon - router never sends out information on an interface that it learned from that interface Now – What do the routing tables look like? Network Discovery with Split Horizon 10.1.1.0/24 .1 RTA e0 10.1.2.0/24 .1 .2 s0 s0 RTB 10.1.3.0/24 .1 s1 .2 s0 RTC 10.1.4.0/24 .1 .2 s1 s0 RTD .1 10.1.5.0/24 e0 Routing Table Routing Table Routing Table Routing Table Net. Hops Ex-Int 10.1.1.0/24 0 e0 10.1.2.0/24 0 s0 10.1.3.0/24 1 10.1.2.2 Net. Hops Ex-Int 10.1.2.0/24 0 s0 10.1.3.0/24 0 s1 10.1.1.0/24 1 10.1.2.1 10.1.4.0/24 1 10.1.3.2 Net. Hops Ex-Int 10.1.3.0/24 0 s0 10.1.4.0/24 0 s1 10.1.2.0/24 1 10.1.3.1 10.1.5.0/24 1 10.1.4.2 Net. Hops Ex-Int 10.1.4.0/24 0 s0 10.1.5.0/24 0 e0 10.1.3.0/24 1 10.1.4.1 Routing Update Next-hop Net. Hops Address 10.1.3.0/24 1 10.1.4.1 10.1.2.0/24 2 10.1.4.1 -----------------------10.1.4.0/24 1 10.1.3.2 10.1.5.0/24 2 10.1.3.2 Routing Update Next-hop Net. Hops Address X10.1.4.0/24 1 10.1.4.2 X10.1.3.0/24 2 10.1.4.2 -----------------------10.1.5.0/24 1 10.1.4.2 Routing Update Next-hop Net. Hops Address 10.1.1.0/24 1 10.1.1.1 -----------------------10.1.2.0/24 1 10.1.1.1 X 10.1.3.0/24 2 10.1.1.1 X Routing Update Next-hop Net. Hops Address 10.1.2.0/24 1 10.1.3.1 10.1.1.0/24 2 10.1.3.1 -----------------------10.1.3.0/24 1 10.1.2.2 10.1.4.0/24 2 10.1.2.2 Routing Table Routing Table Routing Table Routing Table Net. Hops Ex-Int 10.1.1.0/24 0 e0 10.1.2.0/24 0 s0 10.1.3.0/24 1 10.1.2.2 10.1.4.0/24 2 10.1.2.2 Net. Hops Ex-Int 10.1.2.0/24 0 s0 10.1.3.0/24 0 s1 10.1.1.0/24 1 10.1.2.1 10.1.4.0/24 1 10.1.3.2 10.1.5.0/24 2 10.1.3.2 Net. Hops Ex-Int 10.1.3.0/24 0 s0 10.1.4.0/24 0 s1 10.1.2.0/24 1 10.1.3.1 10.1.5.0/24 1 10.1.4.2 10.1.1.0/24 2 10.1.3.1 Net. Hops Ex-Int 10.1.4.0/24 0 s0 10.1.5.0/24 0 e0 10.1.3.0/24 1 10.1.4.1 10.1.2.0/24 2 10.1.4.1 Answer – Do your routing tables look like these? Convergence? Note: Newest routing table entries are at the bottom of the routing tables in these diagrams. Now – What do the next round of routing updates look like and the routing tables? (We’ll finish this up ) Network Discovery with Split Horizon 10.1.1.0/24 .1 e0 RTA 10.1.2.0/24 RTB .1 .2 s0 s0 10.1.3.0/24 .1 s1 .2 s0 RTC 10.1.4.0/24 .1 .2 s1 s0 RTD .1 10.1.5.0/24 e0 Routing Table Routing Table Routing Table Routing Table Net. Hops Ex-Int 10.1.1.0/24 0 e0 10.1.2.0/24 0 s0 10.1.3.0/24 1 10.1.2.2 10.1.4.0/24 2 10.1.2.2 Net. Hops Ex-Int 10.1.2.0/24 0 s0 10.1.3.0/24 0 s1 10.1.1.0/24 1 10.1.2.1 10.1.4.0/24 1 10.1.3.2 10.1.5.0/24 2 10.1.3.2 Net. Hops Ex-Int 10.1.3.0/24 0 s0 10.1.4.0/24 0 s1 10.1.2.0/24 1 10.1.3.1 10.1.5.0/24 1 10.1.4.2 10.1.1.0/24 2 10.1.3.1 Net. Hops Ex-Int 10.1.4.0/24 0 s0 10.1.5.0/24 0 e0 10.1.3.0/24 1 10.1.4.1 10.1.2.0/24 2 10.1.4.1 Routing Update Next-hop Net. Hops Address 10.1.2.0/24 1 10.1.3.1 10.1.1.0/24 2 10.1.3.1 -----------------------10.1.3.0/24 1 10.1.2.2 10.1.4.0/24 2 10.1.2.2 10.1.5.0/24 3 10.1.2.2 Routing Update Next-hop Net. Hops Address 10.1.3.0/24 1 10.1.4.1 10.1.2.0/24 2 10.1.4.1 10.1.1.0/24 3 10.1.4.1 -----------------------10.1.4.0/24 1 10.1.3.2 10.1.5.0/24 2 10.1.3.2 Routing Update Next-hop Net. Hops Address 10.1.1.0/24 1 10.1.1.1 -----------------------10.1.2.0/24 1 10.1.1.1 X 10.1.3.0/24 2 10.1.1.1 X 10.1.4.0/24 3 10.1.1.1 X Routing Update Next-hop Net. Hops Address X10.1.4.0/24 1 10.1.4.2 X10.1.3.0/24 2 10.1.4.2 X10.1.2.0/24 3 10.1.4.2 -----------------------10.1.5.0/24 1 10.1.4.2 Routing Table Routing Table Routing Table Routing Table Net. Hops Ex-Int 10.1.1.0/24 0 e0 10.1.2.0/24 0 s0 10.1.3.0/24 1 10.1.2.2 10.1.4.0/24 2 10.1.2.2 10.1.5.0/24 3 10.1.2.2 Net. Hops Ex-Int 10.1.2.0/24 0 s0 10.1.3.0/24 0 s1 10.1.1.0/24 1 10.1.2.1 10.1.4.0/24 1 10.1.3.2 10.1.5.0/24 2 10.1.3.2 Net. Hops Ex-Int 10.1.3.0/24 0 s0 10.1.4.0/24 0 s1 10.1.2.0/24 1 10.1.3.1 10.1.5.0/24 1 10.1.4.2 10.1.1.0/24 2 10.1.3.1 Net. Hops Ex-Int 10.1.4.0/24 0 s0 10.1.5.0/24 0 e0 10.1.3.0/24 1 10.1.4.1 10.1.2.0/24 2 10.1.4.1 10.1.1.0/24 3 10.1.4.1 Answer – Do your routing tables look like these? Convergence? – YES! Good Job! FAQs – Network Discovery Q: How often does initial network discovery happen? A: Only when the network first comes up. Q: Do routers share routing table information after network discovery? A: Yes, distance-vector routing protocols share their entire routing tables periodically (with or without split horizon enabled). Distance vector routing protocols on Cisco routers by default use split horizon with poison reverse (discussed in the next section). Depending upon the distance-vector routing protocol, the frequency of the updates will happen for RIP every 30 seconds, IPX RIP every 60 seconds, and IGRP every 90 seconds. Q: What happens when there is a change in the topology, link goes down, new network is added, new router, is added, etc.? A: Let’s take a look. Triggered Updates Routers do not have to wait for the periodic update to hear about changes in the network topology. Improvements to the distance-vector algorithm is typically made in distance-vector routing protocols, like RIP, to include triggered updates. Even with triggered updates, large distance vector networks can suffer from long convergence times in some situations. Triggered updates: (continued) Triggered updates are sent whenever a router sees a topology change or a change in routing information (from another router). The router does not have to wait for the period timer, but can send them immediately. Triggered updates do not need to include the entire routing table but only the modified route(s). Triggered updates: (continued) Triggered updates must still be sent to adjacent routers, from router to router, like other routing updates. Most distance-vector routing protocols limit the frequency of triggered updates so that a flapping link does not put an unnecessary load on the network. (RIP: random 1 to 5 seconds) Typically, triggered updates can be “triggered” by: – Interface transition to the up or down state – A route has entered or exited an unreachable (down) state (later) – A new route is installed in the routing table Routing Loops Distance vector routing protocols are simple in their implementaton and configuration, but this comes at a price. Pure distance vector routing protocols suffer from possible routing loops. Routing loops can cause major network problems, from packets getting lost (blackholed) in your network, to bringing down your entire network. Several remedies to have been added to distance-vector algorithms to help prevent routing loops including: – Split horizon – Hold-down timers – Defining a maximum metric Routing Loops (continued) What can cause routing loops? Routing loops can occur when there are: – Incorrect or inconsistent routing updates due to slow convergence after a topology change. (Example coming up next.) – Incorrect or incomplete routing information (see presentation on Discard Routes) – Static routes incorrectly configured with an intermediate address which does not become resolved in the routing table. (see presentation on Static Routes – Additional Information) Routing Loop Example Assume for the remainder of this example that Router C’s preferred path to network 1 is by way of Router B. Router C’s routing table has a distance of 3 to network 1 via Router B. Network 1 Fails Router E sends an update to Router A. Router A stops routing packets to network 1. But Routers B, C, and D continue to do so because they have not yet been informed about the failure. Router A sends out its update. Routers B and D stop routing to network1, (via Router A). However, Router C is still not updated. To router C, network 1 is still reachable via router B. Router C sends a periodic update to Router D Router C sends a periodic update to Router D indicating a path to network 1 (by way) of via Router B. (4 hops). Router D’s Routing Table information for Network 1 Current path to Network 1 = Unreachable (down) Information from Router C: Network 1 : 4 hops by way of Router C Normally, RouterD ignores this routing information because it usually has a better route, 2 hops, via Router A, but this route is now down. Router D changes its routing table to reflect this (good) better, but incorrect information, Network 1 by way of Router C (4 hops) Router D propagates the information to Router A. Routers A changes its routing table Router A adds new route to its routing table, get to Network 1 by way of Router D (5 hops). Propagates the information to Routers B and E. Router B (and Router E) change their routing tables Router B now believes it can get to Network 1 by way of Router A (6 hops). Wow! I was about to tell Router C that Network 1 was down via Router B, but now I have new information! Propagates the incorrect information to Router C. Router C changes its routing table Router C still believes it can get to Network 1 by way of Router B (7 hops). Of course now it believes it is 7 hops instead of 3. Propagates the newer but still incorrect information to Router D. Here we go again! Data packets destined for Network 1 get caught in a routing loop, from Routers A to D to C to B to A to D etc. As routing updates continue between the routers, the hop count gets greater – to infinity? (Not quite – we will see in a moment.) Counting to Infinity The routing loop we just saw creates another problem, known as “Counting to Infinity.” This condition, called count to infinity, loops packets continuously around the network in spite of the fundamental fact that the destination network, Network 1, is down. While the routers are counting to infinity, the invalid information allows a routing loop to exist. Without countermeasures to stop the process, the distance vector (metric) of hop count increments each time the packet passes through another router. - These packets loop through the network because of wrong information in the routing tables. Solution to Counting to Infinity: Defining a Maximum metric Distance vector routing protocols remedy the problem by limiting the maximum number of hops for any route in the routing table. When the distance vector routing protocol has a route with a metric that is more than its maximum-value, it is denoted as “infinity” and the route is considered “unreachable.” For RIP the maximum-value is 15 (hops), infinity is 16 (hops). For IGRP the maximum-value 100 (hops), infinity is 101 (hops). – IGRP uses bandwidth, delay, reliability and load for its metric in determining best path. – IGRP does not use hop count as this metric. Hop count is only used by IGRP to stop the counting to infinity behavior. (more later) Solution to Counting to Infinity: Defining a Maximum metric Remember that distance vector routing protocols like RIP, increment the metric (hop count) before sending the routing update to their adjacent routers. – After incrementing the hop count, if the metric (hops) is less than 15, routing updates to other adjacent routes will receive a valid route for this network from this router. – After incrementing the hop count, if the metric (hop count) is equal to 15, this router will be able to route packets to this network, 15 hops away, but routing updates to other adjacent routers will have the incremented hop count of 16 (infinity). - This means other routers cannot reach this network via this router. – After incrementing the hop count, if the metric (hop count) is equal to 16,“infinity”, this router will not be able to route packets to this network. Routing updates to other adjacent routers will also have the hop count of 16 (infinity), which means they cannot reach this network via this router. There is another situation where the router itself will modify the hop count to infinity – split horizon with poison reverse. – Coming up next! FAQs – Defining a maximum-value Q: Why does RIP use a hop count as the route metric, and why is its maximum value limited to 15? A: When RIP was designed and implemented, dynamic routing protocols were not widely used. Instead, networks relied mostly on static routing. RIP, even with its hop-count-metric – which seems very poor to us today – was quite a big improvement. Counting intermediate routes is the simplest method to measure the quality of routes. Setting the infinity value for the metric is always a problem of choosing between wider networks and faster convergence when the protocol starts counting. When RIP was invented, it seemed unlikely to have a network with the maximum diameter of more than 15 routers, so 16 was chosen as the infinity value. (Zinin, Cisco IP Routing) Split Horizon Rule - Reminder “The effect of split horizon is that a router will send out different routing messages on different interfaces. In effect a router never sends out information on an interface that it learned from that interface.” (Lewis, Cisco TCP/IP Routing) Earlier we saw that split horizon meant that the router does not send out all of the information in the routing table to its neighbors. – If a router learned about a network from an adjacent router, it does not include that network in its routing updates to that neighbor. (See previous slides, Network Discovery and Split Horizon.) As we will now see split horizon also helps prevent routing loops. Simple Split Horizon 10.1.1.0/24 .1 RTA 10.1.2.0/24 .1 .2 s0 s0 e0 RTB 10.1.3.0/24 .1 e0 Routing Table Routing Table Net. Hops Ex-Int 10.1.1.0/24 0 e0 10.1.2.0/24 0 s0 Net. Hops Ex-Int 10.1.2.0/24 0 s0 10.1.3.0/24 0 e0 Initial routing tables Split Horizon Rule – Avoiding Routing Loops Routers RTA and RTB have their initial routing tables and are ready to exchange routing information via a distance-vector routing protocol like RIP. Split Horizon disabled If split horizon were disabled the routing updates would include all of the networks in their routing tables including their directly connected networks and any networks learned from any interface. 10.1.1.0/24 .1 RTA 10.1.2.0/24 .1 .2 s0 s0 e0 RTB 10.1.3.0/24 .1 e0 Routing Table Routing Table Net. Hops Ex-Int 10.1.1.0/24 0 e0 10.1.2.0/24 0 s0 Net. Hops Ex-Int 10.1.2.0/24 0 s0 10.1.3.0/24 0 e0 Routing Update Next-hop Net. Hops Address 10.1.1.0/24 1 10.1.1.1 10.1.2.0/24 1 10.1.1.1 Routing Table Net. Hops Ex-Int 10.1.1.0/24 0 e0 10.1.2.0/24 0 s0 10.1.3.0/24 1 10.1.2.2 Routing Update Next-hop Net. Hops Address 10.1.2.0/24 1 10.1.2.2 10.1.3.0/24 1 10.1.2.2 Routing Table Net. Hops Ex-Int 10.1.2.0/24 0 s0 10.1.3.0/24 0 e0 10.1.1.0/24 1 10.1.2.1 Initial routing tables 10.1.2.0/24 network is included because split horizon has been disabled New routing tables Split Horizon Disabled After the initial exchange of updates everything in the routing tables look fine. Because split horizon disabled, the 10.1.2.0/24 network is sent by both routers, but neither router includes the other’s route to 10.1.2.0/24 (1 hop) in the routing table, because it has a current route with a better metric of 0. 10.1.1.0/24 .1 RTA e0 10.1.2.0/24 .1 .2 s0 s0 Routing Table Net. Hops Ex-Int 10.1.1.0/24 0 e0 10.1.2.0/24 0 s0 10.1.3.0/24 1 10.1.2.2 Routing Update Next-hop Net. Hops Address 10.1.1.0/24 1 10.1.1.1 10.1.2.0/24 1 10.1.1.1 10.1.3.0/24 2 10.1.1.1 Routing Table Net. Hops Ex-Int 10.1.1.0/24 0 e0 10.1.2.0/24 0 s0 10.1.3.0/24 1 10.1.2.2 RTB 10.1.3.0/24 .1 e0 Routing Table Net. Hops Ex-Int 10.1.2.0/24 0 s0 10.1.3.0/24 0 e0 10.1.1.0/24 1 10.1.2.1 Routing Update Next-hop Net. Hops Address 10.1.2.0/24 1 10.1.2.2 10.1.3.0/24 1 10.1.2.2 10.1.1.0/24 2 10.1.2.2 Routing Table Net. Hops Ex-Int 10.1.2.0/24 0 s0 10.1.3.0/24 0 e0 10.1.1.0/24 1 10.1.2.1 Previous routing tables Networks in red were included because split horizon has been disabled New routing tables Split Horizon Disabled After the next exchange of updates everything in the routing tables look fine and the routing tables are converged. Because split horizon disabled, the besides the 10.1.2.0/24 network, the networks learned from the other router in the previous update is also sent by both routers. However, neither router includes those networks, because it has a current route with a better metric of 0. 10.1.1.0/24 .1 RTA e0 10.1.2.0/24 .1 .2 s0 s0 Routing Table Net. Hops Ex-Int 10.1.1.0/24 0 e0 10.1.2.0/24 0 s0 10.1.3.0/24 1 10.1.2.2 RTB 10.1.3.0/24 .1 e0 X Routing Table Net. Hops Ex-Int 10.1.2.0/24 0 s0 10.1.3.0/24 0 e0 10.1.1.0/24 1 10.1.2.1 Routing Update Next-hop Net. Hops Address 10.1.1.0/24 1 10.1.1.1 10.1.2.0/24 1 10.1.1.1 10.1.3.0/24 2 10.1.1.1 Routing Table Net. Hops Ex-Int 10.1.1.0/24 0 e0 10.1.2.0/24 0 s0 10.1.3.0/24 1 10.1.2.2 Previous routing tables Networks in red were included because split horizon has been disabled Routing Table Net. Hops Ex-Int 10.1.2.0/24 0 s0 10.1.3.0/24 2 10.1.2.1 10.1.1.0/24 1 10.1.2.1 New routing tables Split Horizon Disabled – 10.1.3.0/24 down Note: Routing tables are not sent at the exactly same time. We will learn about this in Ch. 7 Routing Protocols, that this is done on purpose to avoid collisions on broadcast networks like Ethernet. Here, the 10.1.3.0/24 network fails, and before RTB sends out its routing update, RTB receives a routing update from RTA. 10.1.1.0/24 .1 RTA e0 10.1.2.0/24 .1 .2 s0 s0 Routing Table Net. Hops Ex-Int 10.1.1.0/24 0 e0 10.1.2.0/24 0 s0 10.1.3.0/24 1 10.1.2.2 RTB 10.1.3.0/24 .1 e0 X Routing Table Net. Hops Ex-Int 10.1.2.0/24 0 s0 10.1.3.0/24 0 e0 10.1.1.0/24 1 10.1.2.1 Routing Update Next-hop Net. Hops Address 10.1.1.0/24 1 10.1.1.1 10.1.2.0/24 1 10.1.1.1 10.1.3.0/24 2 10.1.1.1 Routing Table Net. Hops Ex-Int 10.1.1.0/24 0 e0 10.1.2.0/24 0 s0 10.1.3.0/24 1 10.1.2.2 Previous routing tables Networks in red were included because split horizon has been disabled Routing Table Net. Hops Ex-Int 10.1.2.0/24 0 s0 10.1.3.0/24 2 10.1.2.1 10.1.1.0/24 1 10.1.2.1 New routing tables Split Horizon Disabled – 10.1.3.0/24 down RTB notices that it has a route to 10.1.3.0/24 via RTA. Even though it is 2 hops it is certainly better than its current situation of “unreachable” so it accepts this better, but incorrect information from RTA. RTB now forwards all packets destined for 10.1.3.0/24 to RTA at 10.1.2.1. RTA receives these packets and forwards them to RTB at 10.1.2.2. RTB forwards them back to RTA at 10.1.2.1. And so on! The packets get blackholed in this routing loop. 10.1.1.0/24 .1 RTA e0 10.1.2.0/24 .1 .2 s0 s0 Routing Table Net. Hops Ex-Int 10.1.1.0/24 0 e0 10.1.2.0/24 0 s0 10.1.3.0/24 1 10.1.2.2 RTB 10.1.3.0/24 .1 e0 X Routing Table Net. Hops Ex-Int 10.1.2.0/24 0 s0 10.1.3.0/24 2 10.1.2.1 10.1.1.0/24 1 10.1.2.1 Routing Update Next-hop Net. Hops Address 10.1.2.0/24 1 10.1.2.2 10.1.3.0/24 3 10.1.2.2 10.1.1.0/24 2 10.1.2.2 Routing Table Net. Hops Ex-Int 10.1.1.0/24 0 e0 10.1.2.0/24 0 s0 10.1.3.0/24 3 10.1.2.2 Routing Table Net. Hops Ex-Int 10.1.2.0/24 0 s0 10.1.3.0/24 2 10.1.2.1 10.1.1.0/24 1 10.1.2.1 Previous routing tables Networks in red were included because split horizon has been disabled New routing tables Split Horizon Disabled – 10.1.3.0/24 down Meanwhile, its RTB’s turn to send its routing update. RTB increments the hop count to 10.1.3.0/24 to 3 hops and sends it to RTA. When RTA sends out its next routing table it will increment the hop count to 10.1.3.0/24 to 4 hops and sends it to RTB. And on and on, until “infinity” which in RIP is 16 hops. 10.1.1.0/24 .1 RTA e0 10.1.2.0/24 .1 .2 s0 s0 Routing Table Net. Hops Ex-Int 10.1.1.0/24 0 e0 10.1.2.0/24 0 s0 10.1.3.0/24 16 10.1.2.2 RTB 10.1.3.0/24 .1 e0 X Routing Table Net. Hops Ex-Int 10.1.2.0/24 0 s0 10.1.3.0/24 16 10.1.2.1 10.1.1.0/24 1 10.1.2.1 Split Horizon Disabled Once both routers have 16 hops for 10.1.3.0/24, they will both mark this network as unreachable and discontinue forwarding, drop, packets to this network. This temporary routing loop can be easily avoided by enabling split horizon on the serial 0 interfaces. Split horizon rule states that router never sends out information on an interface that it learned from that interface Let’s see! 10.1.1.0/24 .1 RTA 10.1.2.0/24 .1 .2 s0 s0 e0 RTB 10.1.3.0/24 .1 e0 Routing Table Routing Table Net. Hops Ex-Int 10.1.1.0/24 0 e0 10.1.2.0/24 0 s0 Net. Hops Ex-Int 10.1.2.0/24 0 s0 10.1.3.0/24 0 e0 Routing Update Next-hop Net. Hops Address 10.1.1.0/24 1 10.1.1.1 Routing Table Net. Hops Ex-Int 10.1.1.0/24 0 e0 10.1.2.0/24 0 s0 10.1.3.0/24 1 10.1.2.2 Routing Update Next-hop Net. Hops Address 10.1.1.0/24 1 10.1.1.1 Split Horizon Enabled Previous routing tables Routing Update Next-hop Net. Hops Address 10.1.3.0/24 1 10.1.2.2 Routing Table Net. Hops Ex-Int 10.1.2.0/24 0 s0 10.1.3.0/24 0 e0 10.1.1.0/24 1 10.1.2.1 Routing Update Next-hop Net. Hops Address 10.1.3.0/24 1 10.1.2.2 New routing tables 10.1.1.0/24 .1 RTA 10.1.2.0/24 .1 .2 s0 s0 e0 RTB 10.1.3.0/24 .1 e0 Routing Table Routing Table Net. Hops Ex-Int 10.1.1.0/24 0 e0 10.1.2.0/24 0 s0 Net. Hops Ex-Int 10.1.2.0/24 0 s0 10.1.3.0/24 0 e0 Routing Update Next-hop Net. Hops Address 10.1.1.0/24 1 10.1.1.1 Routing Table Net. Hops Ex-Int 10.1.1.0/24 0 e0 10.1.2.0/24 0 s0 10.1.3.0/24 1 10.1.2.2 Routing Update Next-hop Net. Hops Address 10.1.1.0/24 1 10.1.1.1 Previous routing tables Routing Update Next-hop Net. Hops Address 10.1.3.0/24 1 10.1.2.2 Routing Table Net. Hops Ex-Int 10.1.2.0/24 0 s0 10.1.3.0/24 0 e0 10.1.1.0/24 1 10.1.2.1 New routing tables Routing Update Next-hop Net. Hops Address 10.1.3.0/24 1 10.1.2.2 Split Horizon Enabled As you can see, with split horizon enabled, RTA does not send RTB (out s0) information about 10.1.3.0/24 because it learned it from RTB (same s0), and RTB does not send RTA (out s0) information about 10.1.1.0/24 to RTA because it learned it from RTA (same s0). (This also includes the common network between them. 10.1.1.0/24 .1 RTA e0 10.1.2.0/24 .1 .2 s0 s0 Routing Table Net. Hops Ex-Int 10.1.1.0/24 0 e0 10.1.2.0/24 0 s0 10.1.3.0/24 1 10.1.2.2 RTB 10.1.3.0/24 .1 e0 X Routing Table Net. Hops Ex-Int 10.1.2.0/24 0 s0 10.1.3.0/24 (down) e0 10.1.1.0/24 1 10.1.2.1 Previous routing tables Routing Update Next-hop Net. Hops Address 10.1.3.0/24 16 10.1.2.2 Routing Table Net. Hops Ex-Int 10.1.1.0/24 0 e0 10.1.2.0/24 0 s0 10.1.3.0/24 (down) 10.1.2.2 Routing Table Net. Hops Ex-Int 10.1.2.0/24 0 s0 10.1.3.0/24 (down) e0 10.1.1.0/24 1 10.1.2.1 New routing tables Split Horizon Enabled – 10.1.3.0/24 down RTB notices 10.1.3.0/24 is down and puts this route into hold-down state in its routing table. (hold-down coming next) RTB immediately sends out a triggered update for only this route (if there were others in the routing table) with a metric of infinity, 16. RTA receives the triggered update and puts the route for 10.1.3.0/24 into hold-down state. 10.1.1.0/24 .1 RTA e0 10.1.2.0/24 .1 .2 s0 s0 Routing Table Net. Hops Ex-Int 10.1.1.0/24 0 e0 10.1.2.0/24 0 s0 10.1.3.0/24 1 10.1.2.2 RTB 10.1.3.0/24 .1 e0 X Routing Table Net. Hops Ex-Int 10.1.2.0/24 0 s0 10.1.3.0/24 (down) e0 10.1.1.0/24 1 10.1.2.1 Previous routing tables Routing Update Next-hop Net. Hops Address 10.1.3.0/24 16 10.1.2.2 Routing Table Net. Hops Ex-Int 10.1.1.0/24 0 e0 10.1.2.0/24 0 s0 10.1.3.0/24 (down) 10.1.2.2 Routing Table Net. Hops Ex-Int 10.1.2.0/24 0 s0 10.1.3.0/24 (down) e0 10.1.1.0/24 1 10.1.2.1 New routing tables Split Horizon Enabled – 10.1.3.0/24 down Notice that RTA never sends RTB a routing update for 10.1.3.0/24, because split horizon is enabled on these interfaces. Split Horizon with Poison Reverse 10.1.1.0/24 .1 RTA e0 10.1.2.0/24 .1 .2 s0 s0 Routing Table Net. Hops Ex-Int 10.1.1.0/24 0 e0 10.1.2.0/24 0 s0 10.1.3.0/24 1 10.1.2.2 Routing Update Next-hop Net. Hops Address 10.1.1.0/24 1 10.1.1.1 10.1.2.0/24 16 10.1.2.1 10.1.3.0/24 16 10.1.2.1 10.1.3.0/24 .1 e0 Routing Table Net. Hops Ex-Int 10.1.2.0/24 0 s0 10.1.3.0/24 0 e0 10.1.1.0/24 1 10.1.2.1 Routing Update Next-hop Net. Hops Address 10.1.3.0/24 1 10.1.2.2 10.1.2.0/24 16 10.1.2.2 10.1.1.0/24 16 10.1.2.2 Split Horizon with Poison Reverse RTB “Poisoned” routes in red. Routing tables remain the same. Many vendor implementations of distance vector routing protocols like Cisco’s RIP and IGRP apply a special kind of split horizon, called split horizon with poison reverse. “Split horizon with poison reverse means that, instead of not advertising routes to the source, routes are advertised back to the source with a metric of 16, which will make the source router ignore the route. It is perceived that explicitly telling a router to ignore a route is better than not telling it about the route in the first place.” (Lewis, Cisco TCP/IP Routing) One drawback is that routing update packet sizes will be increased when using Poison Reverse, since they now include these routes. Split Horizon Enabled 10.1.1.0/24 .1 RTA e0 10.1.2.0/24 .1 .2 s0 s0 Routing Table Net. Hops Ex-Int 10.1.1.0/24 0 e0 10.1.2.0/24 0 s0 10.1.3.0/24 1 10.1.2.2 Routing Update Next-hop Net. Hops Address 10.1.1.0/24 1 10.1.1.1 10.1.2.0/24 16 10.1.2.1 10.1.3.0/24 16 10.1.2.1 RTB 10.1.3.0/24 .1 e0 Routing Table Net. Hops Ex-Int 10.1.2.0/24 0 s0 10.1.3.0/24 0 e0 10.1.1.0/24 1 10.1.2.1 Routing Update Next-hop Net. Hops Address 10.1.3.0/24 1 10.1.2.2 10.1.2.0/24 16 10.1.2.2 10.1.1.0/24 16 10.1.2.2 “Poisoned” routes in red. Split Horizon Enabled by Default Split horizon with poison reverse is enabled by default for all interfaces except: Physical interfaces or multipoint sub-interfaces using Frame Relay or SMDS encapsulation (CCNA Semester 4 and CCNP Remote Access) To disable split horizon on an interface: Router(config-if)# no ip split-horizon To enable split horizon on an interface: Router(config-if)# ip split-horizon Holddown timers The main function of holddown timers is to prevent the distance vector routing protocol from establishing routing loops during periods of network transition (topology changes). “The rule: Once a route is marked unreachable, it must stay in this state for a period of time assumed sufficient for all routers to receive new information about the unreachable network. In essence, we instruct the routers to let the rumors calm down and then to pick up the truth.” (Zinin, Cisco IP Routing) The amount of time a router remains in “this state” is determined by the holddown timer. Cisco on-line curriculum information You can avoid the count-to-infinity problem by using hold-down timers. When a router receives an update from a neighbor indicating that a previously accessible network is now inaccessible, the router marks the route as inaccessible and starts a hold-down timer. Cisco on-line curriculum information (continued) Same Route from same neighbor: Network is back up (Correct News) If at any time before the hold-down timer expires an update is received from the same neighbor indicating that the network is again accessible, the router marks the network as accessible and removes the hold-down timer. Cisco on-line curriculum information (continued) Better Route from different neighbor (Correct News) If at any time before the hold-down timer expires an update arrives from a different neighboring router with a better metric than originally recorded for the network, the router marks the network as accessible and removes the hold-down timer. Cisco on-line curriculum information (continued) Poorer Route from a different neighbor. (Incorrect News) If at any time before the hold-down timer expires an update arrives from a different neighboring router with a poorer metric than originally recorded for the network the update is ignored and the hold-down timer continues. Ignoring an update with a poorer metric when a hold-down is in effect allows more time for the knowledge of a disruptive change to propagate through the entire network. Additional Information on Holddown Timers Flapping routes Holddown timers not only help prevent routing loops during transient periods but also help network stability by dampening unstable, flapping routes (routes which continuously go up and down). Holddown Time As we will see with both RIP and IGRP, the amount of time the router remains in the holddown state can be modified (with caution!), even set to 0. We will look at this later in the presentations on RIP and IGRP. Additional Information on Holddown Timers Packet forwarding Even though routing tables remain constant and routers do not accept potentially bad updates, an interesting question is whether or not routers should continue use the existing routes that are in holddown state for forwarding packets? “In practice, routes in the holddown state are used for packet forwarding. In the worst case, packets are forwarded toward the router that was previously connected to the destination network, which drops them. In the best case, they are forwarded along a potentially suboptimal but valid path.” (Zinin, Cisco IP Routing) IP’s TTL – Time To Live field IP Header 0 4-bit Version 15 16 4-bit Header Length 8-bit Type Of Service (TOS) 16-bit Total Length (in bytes) 3-bit Flags 16-bit Identification 8 bit Time To Live TTL 31 8-bit Protocol 13-bit Fragment Offset 16-bit Header Checksum 32-bit Source IP Address 32-bit Destination IP Address Options (if any) Data Let’s look at a related item in IP, the TTL field. IP’s TTL – Time To Live field IP Header 0 4-bit Version 15 16 4-bit Header Length 8-bit Type Of Service (TOS) 16-bit Total Length (in bytes) 3-bit Flags 16-bit Identification 8 bit Time To Live TTL 31 8-bit Protocol 13-bit Fragment Offset 16-bit Header Checksum 32-bit Source IP Address 32-bit Destination IP Address Options (if any) Data When a packet is first generated a value is entered into the TTL field. Originally, the TTL field was the number of seconds, but this was difficult to implement and rarely supported. Now, the TTL is now set to a specific value which is then decremented by each router. IP’s TTL – Time To Live field IP Header 0 4-bit Version 15 16 4-bit Header Length 8-bit Type Of Service (TOS) 16-bit Total Length (in bytes) 3-bit Flags 16-bit Identification 8 bit Time To Live TTL 31 8-bit Protocol 13-bit Fragment Offset 16-bit Header Checksum 32-bit Source IP Address Decrement by 1, if 0 drop the packet. 32-bit Destination IP Address Options (if any) Data If the router decrements the TTL field to 0, it will then drop the packet (unless the packet is destined specifically for the router, I.e. ping, telnet, etc.). Common operating system TTL values are: – – – – UNIX: 255 Linux: 64 or 255 depending upon vendor and version Microsoft Windows 95: 32 Other Microsoft Windows operating systems: 128 http://www.switch.ch/docs/ttl_default.html TTL Overview - Disclaimer: The following list is a best effort overview of some widely used TCP/IP stacks. The information was provided by vendors and many helpful system administrators. We would like to thank all these contributors for their precious help ! SWITCH cannot, however, take any responsibility that the provided information is correct. Furthermore, SWITCH cannot be made liable for any damage that may arise by the use of this information. +--------------------+-------+---------+---------+ | OS Version |"safe" | tcp_ttl | udp_ttl | +--------------------+-------+---------+---------+ AIX n 60 30 DEC Pathworks V5 n 30 30 FreeBSD 2.1R y 64 64 HP/UX 9.0x n 30 30 HP/UX 10.01 y 64 64 Irix 5.3 y 60 60 Irix 6.x y 60 60 Linux y 64 64 MacOS/MacTCP 2.0.x y 60 60 OS/2 TCP/IP 3.0 y 64 64 OSF/1 V3.2A n 60 30 Solaris 2.x y 255 255 SunOS 4.1.3/4.1.4 y 60 60 Ultrix V4.1/V4.2A n 60 30 VMS/Multinet y 64 64 VMS/TCPware y 60 64 VMS/Wollongong 1.1.1.1 n 128 30 VMS/UCX (latest rel.) y 128 128 MS WfW n 32 32 MS Windows 95 n 32 32 MS Windows NT 3.51 n 32 32 MS Windows NT 4.0 y 128 128 Assigned Numbers (RFC 1700, J. Reynolds, J. Postel, October 1994): IP TIME TO LIVE PARAMETER The current recommended default time to live (TTL) for the Internet Protocol (IP) is 64. Safe: TCP and UDP initial TTL values should be set to a "safe" value of at least 60 today. IP’s TTL – Time To Live field IP Header 0 4-bit Version 15 16 4-bit Header Length 8-bit Type Of Service (TOS) 16-bit Total Length (in bytes) 3-bit Flags 16-bit Identification 8 bit Time To Live TTL 31 8-bit Protocol 13-bit Fragment Offset 16-bit Header Checksum 32-bit Source IP Address Decrement by 1, if 0 drop the packet. 32-bit Destination IP Address Options (if any) Data The idea behind the TTL field is that IP packets can not travel around the Internet forever, from router to router. Eventually, the packet’s TTL which reach 0 and be dropped by the router, even if there is a routing loop somewhere in the network.