* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Introduction - Gadjah Mada University
Internet protocol suite wikipedia , lookup
Wireless security wikipedia , lookup
Computer security wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Deep packet inspection wikipedia , lookup
Distributed firewall wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Computer network wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Network tap wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
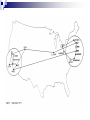
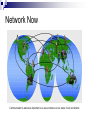
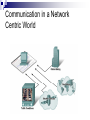
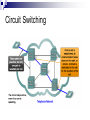
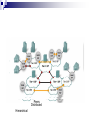
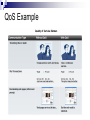
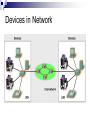
Introduction to Computer Network and Data Communication Widyawan Learning agenda 1. 2. 3. 4. 5. 6. 7. 8. 9. 10. 11. 12. 13. 14. 15. 16. Introduction to Computer Networks OSI Application Layer Transport Layer (TCP/UDP) IP Address IP Address, Sub-netting, NAT Data Link Layer Mid Semester Physical Layer Ethernet Routing Protocol: static and dynamic Planning and Cabling Network Wireless Management, monitoring and optimizations Presentation Final Exam Assessment 40 % tasks 60 % exam (mid and final) Books CCNAB, Cisco Press Network+, Sybex Requirements Active Learn English 75 % of attendance Team work In this session Describe how networks impact our daily lives. Describe the role of data networking in the human network. Describe the characteristics of network architectures: fault tolerance, scalability, quality of service and security. A Little Bit of History In the mid 1960s, mainframe computers were stand alone devices. Computers from different manufactures were unable to communicate each other. 1969 – ARPANET, first packet switched network consist of UCLA, Stanford, UC Santa Barbara and Utah University 1971 – first email program 1980’s – Local Area Networks (LANs) 1990’s – WWW / Internetworking Network Now Communication is almost as important to us as our reliance on air, water, food, and shelter. Early data networks: character-based information between connected computer systems. Current networks have evolved to carry voice, video streams, text, and graphics Converged onto a common platform. Enable communication instantaneously. Global communities. Communication in a Network Centric World Forecast Route and Map Online Banking World News Social Network Instant messaging Real time communication between 2 or more people based on typed text Weblogs Email Leisure (Blogs) Change the way we learn Change the way we work What is Communication Communication is successful when the message May have to agree on and the language Agree on the method used already received confirmedused Before beginning to communicate with each other, we establish rules or agreements to govern the conversation. These rules, or protocols, must be followed in order for the message to be successfully delivered and understood. The techniques that are used in network communications share these fundamentals with human conversations The Internet Architecture Fault Tolerance Scalability QOS Security Fault Tolerance Limits the impact of a hardware or software failure and can recover quickly when such a failure occurs Depend on redundant links, or paths, between the source and destination of a message Fault Tolerance Circuit Switching Packet Switching Scalability Scalability in Internet Architecture Peers Distributed Hierarchical QoS Mekanisme kontrol yang mampu memberikan prioritas yang berbeda pada aliran data/user yang berbeda, atau menjamin kualitas aliran data sesuai permintaan dari program aplikasi QoS Example Priority in QoS Security Network Security Ensure confidentiality through use of User authentication Data encryption Maintain communication integrity through use of Digital signatures Ensure availability through use of Firewalls Redundant network architecture Hardware without a single point of failure Element in Network Devices These are used to communicate with one another Medium This is how the devices are connected together Messages Information that travels over the medium Rules Governs how messages flow across network Network Devices Devices in Network Review Papers Network-based application (example :e-learning) or Internet 2 You can find your own source of papers Put reference where appropriate Use proper references Primary Source Secondary source: PhD thesis, journal paper, monograph, book You should not use Wikipedia