* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Firewalls - Eastern Michigan University
Airborne Networking wikipedia , lookup
Net neutrality law wikipedia , lookup
Point-to-Point Protocol over Ethernet wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Network tap wikipedia , lookup
Computer network wikipedia , lookup
Wireless security wikipedia , lookup
Internet protocol suite wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Asynchronous Transfer Mode wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
TCP congestion control wikipedia , lookup
Serial digital interface wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Multiprotocol Label Switching wikipedia , lookup
Real-Time Messaging Protocol wikipedia , lookup
Packet switching wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
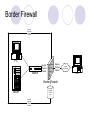
Firewalls Screen packets coming into the Privet Networks from external, Untrusted Networks (Internet) Ingress Packet Filtering Firewall examine incoming packet and either pass or drop (deny) the packet Egress Packet Filtering Firewall examine the packet when the packet is leaving the internal network Border Firewall Internal Corporate Network (Trusted) PC Switch Egress Passed Packet Ingress Passed Packet Attacker Border Firewall Dropped Packet Logs Server Internal Corporate Network (Trusted) Internet (Not Trusted) Firewalls – Type of Protection Packet Inspection IP, TCP, UDP, ICMP Static packet filtering (Stateless filtering) Stateful filtering Application Inspection Application Layer messages Stop malicious executable attachment Network Address Translation (NAT) Spoofs the IP addresses of outgoing packets Firewalls – Type of Protection Denial-of-Services Inspection SYN Flood Cisco PIX – TCP intercept Authentication Only allow the packets from authenticated user Not common Virtual Private Networking Usually work with authentication Provide confidentiality Firewall Hardware and Software Screening Router Firewall High Cost Good place for Egress Filtering Computer-based Firewalls Lower Cost Ease of use Higher risk on Operating System part Firewall Hardware and Software Firewall Appliances Like your toaster Provide rules update Host Firewalls Individual client or server host Defense in depth Hard to manage Static Packet Filter Firewalls The Internet Corporate Network Arriving Packets | IP-H | TCP-H | Application Message | | IP-H | UDP-H | Application Message | | IP-H | ICMP Message | | All Permitted Packets | Denied Packets Static Packet Filter Log File Access Control Lists (ACLs) The way to organize the filtering rules Use If-then Format Sequential Rule Evaluation Deny All Access Control Lists (ACLs) The way to organize the filtering rules Use If-then Format Sequential Rule Evaluation Deny All Sensitivity to Misordering GUI Firewall Rule Maker