* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Security+ Guide to Network Security Fundamentals
Survey
Document related concepts
Transcript
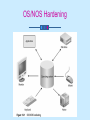
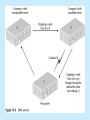
Security Baselines Chapter 13 Learning Objectives Gain an understanding of OS/NOS vulnerabilities and hardening practices Understand the operation of a file system and how to secure a file system Explore common network hardening practices, including firmware updates and configuration best practices continued… Learning Objectives Identify network services commonly exploited by attackers and learn best practices for writing access control lists Explore vulnerabilities regarding network services such as Web, FTP, DNS, DHCP, Mail, File/Print Servers and Data Repositories as well as best practices in securing such services Operating System (OS) Performs basic tasks Recognizes input from keyboard Sends output to display screen Keeps track of files and directories on the disk Controls peripheral devices (disk drives, printers) Network Operating System (NOS) Includes special functions for connecting computers and devices into a LAN Some have built-in networking functions OS/NOS Hardening Process of modifying an OS’s default configuration to make it more secure to outside threats May include removal of unnecessary programs and services May include application of patches to system kernel to limit vulnerability OS/NOS Hardening Actions that Can Disrupt Functionality of a System Attacks Malfunctions Errors Best Practices for System Hardening Remove unused applications, services, and unused or unnecessary file shares Implement and enforce strong password policies; remove or disable expired or unneeded accounts Limit number of administrative accounts Set account lockout policies to discourage password cracking continued… Best Practices for System Hardening Keep track of latest security updates and hot fixes Maintain logging of all user account and administrative activity Back up the system periodically Keep external log of each critical system Maintain records of backups and upgrades File Systems Store data that enable communication between an application and its supporting disk drives Setting privileges and access controls protect information stored on the computer Common privileges: read, write (modify), lock, append, and execute Group users by common needs Additional rights can be granted to a single user in a group Principle of least privilege Creating Needed User Groups System administrator configures operating system to recognize certain user groups Individual users are assigned to appropriate groups Configuring Access Controls System administrator configures access controls for all protected files, directories, devices, and other objects Common Practices for Setting File and Data Privileges Disable write and execute privileges for all executable and binary files Restrict access of OS source files, configuration files, and their directories For UNIX systems: No world-writable files unless specifically required Mount files systems as read only and nosuid continued… Common Practices for Setting File and Data Privileges For NT systems No permissions allowing “Everyone” group to modify files Assign access permission of immutable to all kernel files Establish all log files as “append only” Prevent users from installing, removing, or editing scripts Pay attention to access control inheritance when defining categories of files and users Installing and Configuring File Encryption Capabilities File encryption is useful if the OS Lacks adequate access controls to maintain confidentiality Does not support access control lists Encryption is resource-consuming; carefully weigh benefits Systematic Approach for Addressing Updates Establish procedures for monitoring security-related information Evaluate updates for applicability Plan installation of applicable updates Install updates using a documented plan Deploy new systems with latest software Network Hardening Crucial to have a network with availability as well as adequate security Firmware Updates Made available by vendors as vulnerabilities and malfunctions are discovered with previous versions Configuration Routing functions Designed to route packets efficiently and reliably, but not securely Not to be used to implement a security policy Firewall systems Should govern security of information flow in and out of the network Provide a policy enforcement mechanism at a security domain boundary Assigning Network Addresses for Interfaces on a Firewall Device For the Internet Obtain IP addresses from ISP that connects to the firewall For internal networks Obtain IP addresses from within the organization, typically from RFC 1918 specification Establishing Routing Configuration Should be performed in an environment isolated from the production network Should specify what connectivity is to be permitted with the specific statements and deny all other connectivity Derived from network topology; should not be used to implement aspects of a security policy Best Practices for Configuring Router and Firewall Systems Keep copy of current configurations of network devices in safe location Never allow IP-directed broadcasts through the system Configure devices with meaningful names Use a description for each interface Specify bandwidth on the interfaces continued… Best Practices for Configuring Router and Firewall Systems Configure a loopback address Handle SNMP with care Avoid common names for password and naming schemes Deploy logging about interface status, events, and debugging Restrict data traffic to required ports and protocols only Access Control List (ACL) Set of data that informs a computer’s OS which permissions (access rights) each user or group has to a specific system object Control flow of packets through a device based on certain parameters and information contained within a packet Implement a certain type of security policy, but not considered a policy by themselves Implement packet filtering Packet Filtering Process of deciding disposition of each packet that can pass through a router Provides basic protection mechanism for a routing firewall device through inspection of packet contents Can be based on intrinsic or extrinsic information pertaining to a data packet Best Practices for Designing Filtering Rules for New Networks Add “deny all” rule to articulate the security policy more completely Design antispoofing rules and place them at top of the ACL Identify protocols, ports, and source and destination addresses that need to be serviced continued… Best Practices for Designing Filtering Rules for New Networks Configure filtering rule set of the ACL by protocol and by port Collapse matching protocols rows and consecutive ports rows together into one new row that specifies a range Place all permission rules between antispoofing rules and “deny all” rule at the end of the rule set Enabling and Disabling of Services and Protocols Many services can be easily targeted by attackers unless disabled by system administrators Evaluate every service for need and risks; remove unnecessary ones Evaluate and install required services in a manner to lower potential risk Commonly Exploited Services Remote Procedure Call (RPC) Network File System (NFS) Web services Simple Mail Transfer Protocol (SMTP) Bootstrap Protocol DoS attacks are successful when unnecessary services are running on network devices Commonly Exploited Services on Cisco Platforms Cisco Discovery Protocol (CDP) TCP small servers UDPT small servers Finger HTTP server Bootp server Configuration autoloading IP source Proxy ARP continued… Commonly Exploited Services on Cisco Platforms IP-directed broadcast Classless routing behavior IP unreachable notifications IP mask relay IP redirects NTP service Simple Network Management Protocol Domain Name Service Application Hardening Process of making applications software secure by ensuring that the software contains security enabling technology: Sign in capabilities for authenticated network connections Ability to run properly in secured configurations Applications that Need Hardening Web servers E-mail servers FTP servers DNS servers NNTP servers File and print servers DHCP servers Data repositories Directory services Web Servers Associated with more attacks and vulnerabilities than any type of server Designed to make information accessible, rather than to protect it High Level Best Practices for Securing Web Servers Isolate a Web server on a DMZ Configure a Web server for access privileges Identify and enable Web server-specific logging tools Consider security implications Configure authentication and encryption Isolating a Web Server on a DMZ E-mail Servers Serious risks associated with ability to receive e-mail from the outside world Attachments with malicious contents E-mails with abnormal MIME headers Scripts embedded into HTML-enabled mail Protecting Against E-mail Vulnerabilities Use latest software updates and patches on e-mail server Deploy dedicated e-mail relay (gateway) server between internal network and Internet Deploy virus-scanning tools on the server Use attachment-checking mechanisms on the server Use HTML Active Content removal FTP Servers File Transfer Protocol Used to transfer files between a workstation and an FTP server Vulnerabilities Associated with FTP Protecting against bouncebacks Restricting areas Protecting usernames and passwords Port stealing Other documented vulnerabilities DNS Servers Domain Name Service (DNS) Collective name for system of servers that translate names into addresses in a process transparent to the end user Vulnerabilities Associated with DNS Inaccurate data on IP address ownership Customer registry communication DNS spoofing and cache poisoning Out-of-date root.hints file Recursive queries Denial-of-service attacks NNTP Servers Network News Transfer Protocol (NNTP) Delivers news articles to users on the Internet Stores articles in a central database; users choose only items of interest Makes few demands on structure, content, or storage of news articles NNTP servers can index and cross reference messages, and allow for notification of expiration NNTP Servers Similar vulnerabilities to other network services Effective methods of preventing attacks Use proper authentication mechanisms Disable unneeded services Apply relevant software and OS patches File and Print Servers Store many of an organization’s most valuable and confidential information resources Protecting Against File and Print Server Vulnerabilities Offer only essential network and OS services on a server Configure servers for user authentication Configure server operating systems Manage logging and other data collection mechanisms Configure servers for file backups DHCP Servers Dynamic Host Configuration Protocol (DHCP) Software that assigns dynamic IP addresses to devices on a network Reduces administrative burden No security provisions Preventing Attacks on DHCP Servers Assign permanent addresses Collect Media Access Control (MAC) addresses of all computers on network and bind them to corresponding IP addresses Use dynamic addressing, but monitor log files Use intrusion detection tools continued… Preventing Attacks on DHCP Servers Configure DHCP server to force stations with new MAC addresses on the network to register with the DHCP server Implement latest software and patches Data Repositories Store data for archiving and user access Contain an organization’s most valuable assets in terms of information Should be carefully protected Directory Services Lightweight Directory Access Protocol (LDAP) Industry standard protocol for providing networking directory services for the TCP/IP model Can store and locate information about entities and other network resources Based on simple, treelike hierarchy called a Directory Information Tree (DIT) Directory Service-Oriented Threats Unauthorized access to data by monitoring or spoofing authorized users’ operations Unauthorized access to resources by physically taking over authenticated connections and sessions Unauthorized modification or deletion of data or configuration parameters Spoofing of directory services Excessive use of resources Nondirectory Service-Oriented Threats Common network-based attacks against LDAP servers to compromise availability of resources Attacks against hosts by physically accessing the resources Attacks against back-end databases that provide directory services Security of LDAP Is Dependent on… Authentication Anonymous Simple Simple Authentication and Security Layer (SASL) for LDAPv3 Authorization Principles of Security to Protect Databases Authentication of users and applications Administration policies and procedures Initial configuration Auditing Backup and recovery procedures Chapter Summary Role of operating and file systems as they relate to security of information resources stored on computer systems Operating system vulnerabilities Use of OS hardening practices to prevent attacks and system failures continued… Chapter Summary Vulnerabilities associated with common services installed on computer systems (WWW services, FTP, DNS) and best practices in protecting against threats to these services Maintenance and upgrade of computer systems