* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download No Slide Title
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Deep packet inspection wikipedia , lookup
Computer security wikipedia , lookup
Computer network wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Wireless security wikipedia , lookup
Network tap wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Intel Active Management Technology wikipedia , lookup
Airborne Networking wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
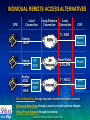
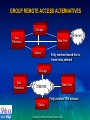
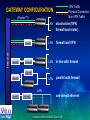
Virtual Private Network Seminar Extend Your Network to Customers, Partners and Employees with Secure VPN Solutions Spring 2000 Copyright © 2000 Intel Network Systems, Inc. AGENDA • • • • • • • Intel Overview Defining VPN How VPNs Work Building a VPN Intel’s VPN Components Demonstration Case Study Copyright © 2000 Intel Network Systems, Inc. INTEL’S STRATEGY Be the pre-eminent building block supplier to the Internet economy Copyright © 2000 Intel Network Systems, Inc. INTEL IS SERIOUS ABOUT NETWORKING Intel Network Systems Vision Trusted and reliable access from any device over any medium, anytime, anywhere at an affordable price. Network Systems Mission Accelerate the use of the Internet as the primary means for business connectivity. Copyright © 2000 Intel Network Systems, Inc. INTEL NETWORK SYSTEMS SOLUTIONS Modular Switches Scalable Stackable Switches Medium Enterprise Data Center/ISP Standalone Switches VPN Gateways Standalone Hubs Appliances Access Concentrator Routers Small Business Access Port Copyright © 2000 Intel Network Systems, Inc. AGENDA • • • • • • • Intel Overview Defining VPN How VPNs Work Building a VPN Intel’s VPN Components Demonstration Case Study Copyright © 2000 Intel Network Systems, Inc. WHAT IS A VPN? A VPN (Virtual Private Network) is a technology that connects individuals and systems over an IP backbone or the Internet Remote LAN Branch Office VPN Server Headquarters Internet VPN Client VPN Server Corporate LAN ISP Modems Traveling Employee or Telecommuter VPNs reduce costs by eliminating expensive leased lines and costly long distance toll charges Communications are protected through encryption and authentication technology Virtual presence on the local area network (LAN) is established with tunneling technology Copyright © 2000 Intel Network Systems, Inc. REMOTE ACCESS APPLICATIONS Telecommuter Individual Remote Access Day-Extender Road Warrior Group Remote Access Supplier or Partner Location Branch Office Customer Site Copyright © 2000 Intel Network Systems, Inc. INDIVIDUAL REMOTE ACCESS ALTERNATIVES CPE Local Connection T1, ISDN Analog ISDN Analog ISDN Long Distance Local Connection Connection PSTN SP POP Analog ADSL Internet Cable POP ISDN SP Network Frame Relay, X.25, ATM T1, HDSL Internet CPE Modem Server Router VPN Gateway • Dial-up Networking through the public switched telephone network • Outsource Networking through a service provider’s private network • Virtual Private Network through the Internet Copyright © 2000 Intel Network Systems, Inc. GROUP REMOTE ACCESS ALTERNATIVES Chicago Internet San Francisco New York Dallas Fully meshed leased line or frame relay network Chicago San Francisco Internet New York Fully meshed VPN network Dallas Copyright © 2000 Intel Network Systems, Inc. THE UPSIDE OF VPN LAN LAN VPN Gateway Firewall Router Dial-up Server Router Internet E-Mail Frame Relay Intranet PSTN Internet World Wide Web TeleExtranet commuter E-Mail Mobile Professional Intranet World Wide Web Extranet TeleMobile Professional commuter • • • • One piece of gear One pipe One network Many applications Copyright © 2000 Intel Network Systems, Inc. BENEFITS OF VIRTUAL PRIVATE NETWORKS • Reduced costs – Eliminate long distance toll charges – Reduce leased line charges • High performance – Every call is a local call – The Internet is a robust public data infrastructure • Increased security – Better than traditional dial up and frame networks • Unparalleled flexibility – Any internet connection – Any access technology (Cable, xDSL, etc) Copyright © 2000 Intel Network Systems, Inc. WHEN TO USE DIAL-UP NETWORKS, OUTSOURCE NETWORKS AND VIRTUAL PRIVATE NETWORKS USE DIAL-UP NETWORKING FOR USE OUTSOURCE NETWORKING FOR USE VIRTUAL PRIVATE NETWORKING • Local telecommuters • Hub and spoke networks • Fully or partially meshed networks • On-line transaction applications • Multi-protocol networks • IP-only networks • Closed user groups • Linking trading partners • Communications within a single country • Road Warrior and site-to-site access • Flexible and rapid implementation • As a back-up for outsource networks and VPN • No additional IP access allowed/required Copyright © 2000 Intel Network Systems, Inc. • International connectivity • Flexible and rapid implementation BENEFITS FOR COMBINING DIRECT DIAL AND VPN BASED SOLUTIONS • VPN over the Internet is the low cost winner for long distance connectivity • Direct Dial over the Telephone Network is the most reliable and affordable solution for local access • Integrated Direct Dial and VPN solutions can also improve performance, security and reliability – Direct dial provides a back up to VPN – VPN supplements local direct dial capacity when exceptional conditions such as snow storms require it – Common security and single authentication methods help implement a unified security policy Copyright © 2000 Intel Network Systems, Inc. REMOTE ACCESS ANALYSIS TOOL Help plan operational costs for remote access networks http://www.shiva.com/remote/vpnroi Copyright © 2000 Intel Network Systems, Inc. AGENDA • Intel Overview • Defining VPN • How VPNs Work – Security technologies • Encryption • Authentication • Firewalls – Networking technologies • Tunneling and tunneling protocols • • • • Building a VPN Intel’s VPN Components Demonstration Case Study Copyright © 2000 Intel Network Systems, Inc. A GENERAL MODEL OF ENCRYPTION Transformation Function Plain Text F Cipher Text Key • Two general types of cryptographic systems: – Asymmetric or ‘public key’ encryption – Symmetric or ‘secret key’ encryption Copyright © 2000 Intel Network Systems, Inc. ASYMMETRIC CRYPTOGRAPHY • Used to establish connections • Key pairs (public / private) – Data encrypted with the public key can only be decrypted by the private key • Relatively slow • Keys relatively long (up to 2048 bits) – Key space 22048 • Example: – Pretty Good Protection (PGP) – Rivest, Shamir, Adelman (RSA) Copyright © 2000 Intel Network Systems, Inc. SYMMETRIC CRYPTOGRAPHY • Used for information moving through the connection • Single shared key – The same key is used to encrypt and decrypt • Relatively fast • Keys relatively short (up to 168 bits) – Key space 2168 • Example: – Data Encryption Standard (DES) – RC4, RC5 Copyright © 2000 Intel Network Systems, Inc. DATA ENCRYPTION STANDARD (DES) • US Data Encryption Standard (DES) • Variants – 56-Bit DES • Single key; good protection – 112-Bit (Triple-pass DES) • Two keys, three passes; better protection – 168-Bit (3DES) • Three independent keys; three passes (encrypt-decrypt-encrypt) • Best protection • Caveats – Encryption algorithms need to be safe from brute force attack because of the increasing speed of modern computers – Need frequent and automated key exchanges – Compute intensive; requires hardware acceleration on server side – US export and International import restrictions Copyright © 2000 Intel Network Systems, Inc. KEY MANAGEMENT Key management controls the distribution and use of encryption keys – Asymmetric algorithms reveal the public key and conceal the private key • Public keys are exchanged • Private keys are secured – Symmetric algorithms require a secure key exchange mechanism • Key secrecy must be maintained during key exchange Copyright © 2000 Intel Network Systems, Inc. VPN AUTHENTICATION SERVICES • Ensure the identity and authority of the VPN participants • Choices include: – Technologies: passwords, challenge phrase, hard and soft tokens with one-time passwords, and X.509 digital certificates – Products: NT Domains*, NDS*, RADIUS, SDI*, Entrust*, Shiva® CA • A VPN solution should allow you to select the authentication method that matches your needs • Recommend the use of digital certificates – – – – X.509 digital certificates are de facto standard Better authentication than passwords and tokens Identify individuals and systems Client and system operate even when certificate authority is unreachable * Such trademarks belong to their respective companies Copyright © 2000 Intel Network Systems, Inc. WHAT ARE CERTIFICATES? • Certificates are digital documents attesting to the binding of a public key to an individual or other entity • Certificates allow verification of the claim that a specific public key does in fact belong to a specific individual • Certificates contain – – – – – A public key and a name Expiration date Name of the certifying authority that issued the certificate A serial number Other information • Most importantly, certificates contain the digital signature of the certificate issuer Copyright © 2000 Intel Network Systems, Inc. VPN FIREWALL SERVICES • Integrated firewall capabilities enhance the flexibility and security of a VPN solution • Integrated firewall capabilities: – Control traffic flow in and out of the corporate network – Limit access of VPN tunnel traffic to specific resources – Provide a stand-alone solution for branch office applications • An integrated firewall should provide: – – – – Packet filtering Network address translation (NAT) for non-VPN traffic Inbound & outbound proxies Sequence-based examination of traffic – State-based examination of traffic Copyright © 2000 Intel Network Systems, Inc. WHAT IS TUNNELING B: 10.0.1.6 ISP B: 10.0.1.5 Destination Source VPN A B Data Internet Server A: 10.0.1.3 D: 200.176.43.11 C: 192.60.75.3 Destination Source Encrypted C D A B Data Copyright © 2000 Intel Network Systems, Inc. TUNNELED PACKETS Des IP Des Enc IP Src Enc IP Src IP Proto -col Proto Des Src -col Port Port = = = UDP 2233 2233 Des Src Port Port Payload Payload Des IP Src IP Proto -col Des Src Por Port t Payload Encrypted with unique Packet Key Copyright © 2000 Intel Network Systems, Inc. VPN TUNNELING STANDARDS • Dedicated point-to-point • Multi-protocol • Security not necessary • SP private networks • Shared multi-point • IP only • Strong security required • Public Internet Start Layer-3 Layer-2 open standard IPSec L2F industry standard PPTP L2TP open standard header & payload protection header protection only Encapsulating Security Payload LAN connections Authentication Header WAN connections Transport Mode Copyright © 2000 Intel Network Systems, Inc. Tunnel Mode COMBINED TUNNEL AND TRANSPORT MODE Enables enforcement of a single security policy VPN Gateway Internet C: 200.176.43.11 VPN Gateway D: 192.60.75.3 tunnel across WAN A: 10.0.1.5 B: 10.0.1.3 transport between hosts • • Protected tunnels across WAN combined with protected transport across LAN to implement unified security policy for LAN and WAN access Protected tunnels are tunnels that: – – – Guarantee the privacy and integrity of the transmitted data Guarantee the authenticity of the parties communicating Hide network topology and application information Copyright © 2000 Intel Network Systems, Inc. IPSec • Authentication Header (AH) – Provides integrity and authentication for IP datagrams [RFC-1826] • Encapsulating Security Payload (ESP) – Provides confidentiality for IP datagrams by encrypting the payload data to be protected – Also provides confidentiality, data origin authentication, connectionless integrity, an anti-replay service, and limited traffic flow confidentiality [RFC-1827] • Internet Key Exchange (IKE) Protocol – Executes communication, authenticates users/systems, negotiates security parameters and establishes keys [RFC-2409] Copyright © 2000 Intel Network Systems, Inc. AGENDA • • • • Intel Overview Defining VPN How VPNs Work Building a VPN – – – – Performance parameters & requirements Service provider considerations Legal constraints VPN Gateway & Client considerations • Intel’s VPN Components • Demonstration • Case Study Copyright © 2000 Intel Network Systems, Inc. PERFORMANCE PARAMETERS AND REQUIREMENTS • Performance starts with the application – VPN solution must take applications into consideration – Different applications have different needs • Performance parameters include – Bandwidth: megabits of encrypted traffic/second – Latency: delay introduced by VPN processing and transmission – Tunnel setup: number of simultaneous VPN connections Copyright © 2000 Intel Network Systems, Inc. VPN PERFORMANCE PARAMETERS BANDWIDTH • Bandwidth – The amount of information that moves across a point in the network per some unit of time – Measured in bits-per-second • Packet size considerations – Effects on performance – Small vs. large packets – Packet encapsulation Copyright © 2000 Intel Network Systems, Inc. VPN PERFORMANCE PARAMETERS LATENCY • Latency – The time it takes information to move from one point in the network to another – Measured in milliseconds • Traffic type considerations – – – – Streaming audio and video File transfer, database backup and Fax-over-IP Application and transaction specific e-Commerce and e-Business Copyright © 2000 Intel Network Systems, Inc. VPN PERFORMANCE PARAMETERS TUNNEL SETUP • Tunnel Setup – Length of time required to establish a tunnel – Affects number of tunnels that can be supported by a VPN solution • Tunnel setup considerations – – – – – Security and encryption algorithms Concurrent connections Authentication Routing Firewall Copyright © 2000 Intel Network Systems, Inc. APPLICATION PERFORMANCE REQUIREMENTS Application Characteristics High Bandwidth Streaming audio & Large volume data, video, Voice over real time IP File transfer, web download, Faxover-IP Large volume data Light client, Small data, many on-line transaction messages, “chatty” systems E-commerce transaction systems Many brief connections Copyright © 2000 Intel Network Systems, Inc. Rapid Low Tunnel Latency Setup SERVICE PROVIDER CONSIDERATIONS ISDN Cable Wireless DSL Analog • Geographical Coverage • Access Technologies – POPs where you need them – Analog, ISDN, DSL, Cable – Easy to find • Support Services • Performance and Reliability – Surveillance and diagnostics – Latency – Break/fix – Bandwidth – Help desk – Availability • Service Level Agreements Copyright © 2000 Intel Network Systems, Inc. SERVICE LEVEL AGREEMENTS (SLA) • VPN cost/performance exceeds traditional methods when customers employ quality VPN products and services • Service level agreements (SLA) cover: – availability: uptime of your connection – latency: average monthly latency of not more than n ms – proactive outage notification: within n minutes of an outage – installation: up and billable by the date quoted to you – 24/7 customer support Copyright © 2000 Intel Network Systems, Inc. LEGAL CONSTRAINTS • Governments may restrict access to encryption technology – Export license – Import license – Restricted countries • Government regulations change frequently – Consult Intel sales for the latest information on export and import restrictions Copyright © 2000 Intel Network Systems, Inc. VPN GATEWAY CONSIDERATIONS • Standards support and interoperability • Performance - bandwidth, latency, tunnel setup – Line speed performance – Hardware encryption – 100’s of tunnels • Management capabilities – – – – – – Ease of operation Automated tunnel and key management Automated client management and distribution SNMP GUI CLI • Reliability and scalability – Client load balancing – Client redundancy with automated fail-over Copyright © 2000 Intel Network Systems, Inc. VPN CLIENT SOFTWARE CONSIDERATIONS • Ease of installation and deployment – Automated deployment and configuration – Ease of client deployment • Ease of operation – Transparent to end-user • Interoperability with existing networking software • Interoperability with ISP platforms and dialers • Support for multiple access technologies – ISDN, Wireless, Cable Modem, DSL • Support for multiple authentication technologies – Digital Certificates, Hard and Soft Tokens, Challenge Phrase, Name and Password, NT Domains, NDS, RADIUS Copyright © 2000 Intel Network Systems, Inc. AGENDA • • • • • • • Intel Overview Defining VPN How VPNs Work Building a VPN Intel’s VPN Components Demonstration Case Study Copyright © 2000 Intel Network Systems, Inc. INTEL’S VPN PRODUCT SUITE • LanRover™ VPN Gateway – – – – • Dedicated Hardware Platform Dedicated Triple-DES acceleration hardware Integrated routing and ICSA-certified firewall Scalability Shiva® VPN Client for Win 95*, 98, NT* – Transparent and works with existing client and server applications – Fail-over & redundancy • Shiva® VPN Client Deployment Tool – Automated distribution of pre-configured VPN Clients • Shiva® Certificate Authority – Most advanced type of security available • Shiva® VPN Manager – Centralized management of distributed gateways * Such trademarks belong to their respective companies Copyright © 2000 Intel Network Systems, Inc. REMOTE CLIENT REDUNDANCY AND AUTOMATED FAIL-OVER VPN Gateway Internet VPN Tunnel VPN Tunnel Established Request • • • Router Firewall VPN Gateway NewTunnel Tunnel VPN Created Lost Automatically VPN Gateway Corporate If the gateway is disconnected, client tunnels automatically Network fail over to the next gateway Improves service, reliability and reduce costs New servers can be deployed for additional capacity Copyright © 2000 Intel Network Systems, Inc. VPN Traffic Physical Connection Non-VPN Traffic GATEWAY CONFIGURATION Internet (Frame/T1) router LAN stand-alone (VPN, firewall and router) router LAN firewall and VPN firewall LAN in-line with firewall LAN parallel with firewall firewall router LAN router firewall one-armed ethernet Copyright © 2000 Intel Network Systems, Inc. SHIVA® VPN CLIENT DEPLOYMENT TOOL What is the VPN Client Deployment Tool? • The first email / web based stand alone deployment tool designed to distribute pre-configured clients • Automates the delivery and update of VPN client files and configuration data Copyright © 2000 Intel Network Systems, Inc. CDT Server CDT Manager SHIVA® VPN CLIENT DEPLOYMENT TOOL ARCHITECTURE Manager CDT Server Database Client Policy Database Web Server The CDT Manager and Server can be on the same or different machines Copyright © 2000 Intel Network Systems, Inc. SHIVA® VPN CLIENT DEPLOYMENT TOOL FEATURES/BENEFITS Feature Function Benefit Automated distribution of clients and configuration Web server with automated email capabilities Encrypted client configuration file CDT encrypts and decrypts the client configuration file Reduces time and effort for centrallized deployment of the VPN client Enhanced security Scalable Deploys anywhere from 25 to thousands of clients Investment protection Copyright © 2000 Intel Network Systems, Inc. SHIVA® ACCESS MANAGER AND SHIVA® CERTIFICATE AUTHORITY LanRover TM Access Switch LanRover TM VPN Gateway Simultaneous Direct Dial and VPN Authentication Simultaneous Radius X.509 Authentication Key Feature Summary • Integrated RADIUS and Certificate Authority management • Full VPN and direct dial accounting • User explorer • Active user monitoring • LDAP support • SNMP support • Multi-level management Shiva® Access Manager 5.0 Simultaneous Direct Dial and VPN Accounting Accounting Server SAM Shiva® Certificate Authority SCA Copyright © 2000 Intel Network Systems, Inc. Complete certificate management capabilities (Add, Mod, Delete) INTEL’S VPN MANAGEMENT • Intel provides efficient and flexible management capability that can help reduce the total cost of ownership of your VPN solution • Intel’s VPN management supports – Tunnel management • Fully automated key management • Tunnel status monitoring & management – Gateway management • Centralized management of distributed devices • GUI, CLI and SNMP (MIB I & MIB II) based control and monitoring – Client deployment, installation and management – Detailed logging • All events from individual connections to failed key negotiations and attempted security breaches are logged Copyright © 2000 Intel Network Systems, Inc. LANROVER VPN GATEWAY FAMILY Product LanRover (TM) VPN Express Number Virtual Encryption of Users Ports 10-150 50 40-bit & 56Bit DES, 112-Bit and 168-Bit Triple-DES LAN Interface Dual 10/100 Ethernet WAN ICSA Suggested Interface Firewall Price (USD) V.35 Serial Included $3,495 LanRover (TM) VPN Gateway 1001500 1000 40-bit & 56- Dual Bit DES, 10/100 112-Bit and Ethernet 168-Bit Triple-DES Dual V.35 Included or Dual X.21 Serial (Optional) $6,014 LanRover (TM) VPN Gateway Plus 2505000 1000 40-bit & 56- Dual Bit DES, 10/100 112-Bit and Ethernet 168-Bit Triple-DES Dual V.35 Included or Dual X.21 Serial (Optional) $9,250 VPN Client and Graphical Management Software Included Copyright © 2000 Intel Network Systems, Inc. AGENDA • • • • • • • Intel Overview Defining VPN How VPNs Work Building a VPN Intel’s VPN Components Demonstration Case Study Copyright © 2000 Intel Network Systems, Inc. DEMONSTRATION Boston, MA ISP POP Intel’s VPN client • Internet Intel’s VPN Gateway Local call to ISP VPN demonstration overview – Remote access with Intel’s VPN Client – Management through Intel’s VPN Manager • Set up of tunnels • Tunnel management • Firewall management Copyright © 2000 Intel Network Systems, Inc. AGENDA • • • • • • • Intel Overview Defining VPN How VPNs Work Building a VPN Intel’s VPN Components Demonstration Case Study Copyright © 2000 Intel Network Systems, Inc. Case Study • The Company: – World’s leading manufacturer of electronic forms • The Challenge – – – – – – Connect 15 regional offices around the world Use existing applications Reduce network communication costs Reduce total cost of ownership Implement enhanced security Centralized management of devices Copyright © 2000 Intel Network Systems, Inc. Case Study • The Company: – World’s leading manufacturer of electronic forms • The Solution – Installed LanRoverTM VPN Gateways at remote offices – Reduced communication costs by $40K per month – Allowed protected, authenticated communications across the Internet – Using the LanRoverTM VPN Gateway to firewall all locations – Doubled network performance (from 56Kbs frame to 128Kbs Internet connection) – Centralized system management made possible with Shiva® VPN Manager and Shiva® Certificate Authority – Same solution will also support remote access for traveling users Copyright © 2000 Intel Network Systems, Inc. Case Study Benefits: • Saving 40K/month on leased line charges • Improved application performance • Add new locations quickly and easily • Minimize number of connections to Internet Sweden router Internet File Servers Workstations router California Shiva® Certificate Authority File Servers Copyright © 2000 Intel Network Systems, Inc. AGENDA • • • • • • • • Intel Overview Defining VPN How VPNs Work Building a VPN Intel’s VPN Components Demonstration Case Study Conclusion Copyright © 2000 Intel Network Systems, Inc. CONCLUSIONS • Remote Access has become a strategic corporate necessity – Connecting employees, partners and customers • Virtual Private Networks help companies implement remote access by – Reducing costs – Improving performance and security – Increasing flexibility • Intel’s product suite provides companies with enhanced VPN capabilities with cost effective and easy to use solutions Copyright © 2000 Intel Network Systems, Inc. PROMOTIONS FREE Shiva® VPN Client Deployment Tool: $5,000 value! (This offer is available to Customers in the United States and Canada only) Get a FREE VPN Client Deployment Tool with your first purchase of a LanRover™ VPN Gateway Plus unit, or 2 LanRover™ VPN Express units, between February 15th and June 30th, 2000 The VPN Client Deployment Tool, Intel's latest addition to its award winning suite of virtual private networking (VPN) products, is an intelligent, web-based solution allowing you to easily, quickly and accurately deploy large numbers of fully-configured Shiva® VPN software clients. Visit www.shiva.com/sales/promotions.html now for details! Copyright © 2000 Intel Network Systems, Inc.