Remote Access VPN Setup (IPSec)
... transport traffic over the internet of any insecure network that uses TCP/IP communications. A remote access VPN (client-to-site) allows employees who are traveling or teleworkers, secure access to company network resources. ...
... transport traffic over the internet of any insecure network that uses TCP/IP communications. A remote access VPN (client-to-site) allows employees who are traveling or teleworkers, secure access to company network resources. ...
Apuntes seguridad Redes Avanzadas 0708
... provide multicast connectivity to a source, using UDP-based encapsulation to overcome the lack of multicast connectivity. AMT builds dynamic tunnels from hosts and can support any host application. Although the AMT protocol is defined for both SSM and ASM traffic, it is primarily intended for use in ...
... provide multicast connectivity to a source, using UDP-based encapsulation to overcome the lack of multicast connectivity. AMT builds dynamic tunnels from hosts and can support any host application. Although the AMT protocol is defined for both SSM and ASM traffic, it is primarily intended for use in ...
PDF
... Platform hardware design guideline summary ................................................................................... 9 Intel® Rack Scale Design Platform Hardware Design General Specifications .................................................... 11 Rack must have one or more Pooled System M ...
... Platform hardware design guideline summary ................................................................................... 9 Intel® Rack Scale Design Platform Hardware Design General Specifications .................................................... 11 Rack must have one or more Pooled System M ...
Remote Access Techniques
... Industry trends toward client/server applications and Graphical user interface-based applications are driving the demand for remote node solutions. The remote node architecture is similar to a client/server application architecture. The remote system acts as a client and the communications server pr ...
... Industry trends toward client/server applications and Graphical user interface-based applications are driving the demand for remote node solutions. The remote node architecture is similar to a client/server application architecture. The remote system acts as a client and the communications server pr ...
Intel® Rack Scale Architecture Platform Hardware Guide
... Platform hardware design guideline summary This section lists the complete requirements for defining how the platform shall be designed to conform to the Intel® Rack Scale Architecture design. Not all requirements are equal, however; some elements may not be immediately available in 2015 designs or ...
... Platform hardware design guideline summary This section lists the complete requirements for defining how the platform shall be designed to conform to the Intel® Rack Scale Architecture design. Not all requirements are equal, however; some elements may not be immediately available in 2015 designs or ...
No Slide Title
... public key to an individual or other entity • Certificates allow verification of the claim that a specific public key does in fact belong to a specific individual • Certificates contain ...
... public key to an individual or other entity • Certificates allow verification of the claim that a specific public key does in fact belong to a specific individual • Certificates contain ...
Introduction to High Performance Computing with
... Hardware for Parallel Computing Parallel computers are classified in terms of streams of data and streams of instructions: • MIMD Computers: Multiple streams of instructions acting on multiple streams of data. • SIMD Computers: A single stream of instructions acting on multiple streams of data. ...
... Hardware for Parallel Computing Parallel computers are classified in terms of streams of data and streams of instructions: • MIMD Computers: Multiple streams of instructions acting on multiple streams of data. • SIMD Computers: A single stream of instructions acting on multiple streams of data. ...
The 802.11 MAC Protocol & Quality of Service
... decide what the higher layers are • If we assume TCP/IP based higher layers, that imposes restrictions on what we can do • We don’t have latitude to rewrite TCP/IP, or the interface to it • We also don’t have latitude to rewrite the applications or the OS ...
... decide what the higher layers are • If we assume TCP/IP based higher layers, that imposes restrictions on what we can do • We don’t have latitude to rewrite TCP/IP, or the interface to it • We also don’t have latitude to rewrite the applications or the OS ...
Improving Network Performance in Multi-Core Systems
... The Intel 82598 10 Gigabit Ethernet Controller is a PCI Expressbased, dual-port, 10-gigabit Ethernet controller, designed for very high-bandwidth needs. It has extensive support for multiple processor cores and is intended for use on large systems, such as enterprise servers, processing appliances, ...
... The Intel 82598 10 Gigabit Ethernet Controller is a PCI Expressbased, dual-port, 10-gigabit Ethernet controller, designed for very high-bandwidth needs. It has extensive support for multiple processor cores and is intended for use on large systems, such as enterprise servers, processing appliances, ...
Sphere of Influence Project owner: Mark Yarvis Intel
... Sensor node informs cluster head when data transfer is complete Cluster repeats the process for each sensor node When all sensors have been collected, the complete cluster is put to sleep until next collection ...
... Sensor node informs cluster head when data transfer is complete Cluster repeats the process for each sensor node When all sensors have been collected, the complete cluster is put to sleep until next collection ...
Intel®10 Gigabit AF DA Dual Port Server Adapter
... Conserve valuable PCI Express (PCIe*) server slots while adding 10 Gigabit Ethernet capability with Intel 10 Gigabit AF DA Server Adapters. The dedicated input/output (I/O) bandwidth of PCIe ensures priority performance on each port – without bus sharing – for 10 Gigabit Ethernet connectivity, as we ...
... Conserve valuable PCI Express (PCIe*) server slots while adding 10 Gigabit Ethernet capability with Intel 10 Gigabit AF DA Server Adapters. The dedicated input/output (I/O) bandwidth of PCIe ensures priority performance on each port – without bus sharing – for 10 Gigabit Ethernet connectivity, as we ...
Intel® Ethernet Server Adapters I350
... This generation of PCIe Intel® Gigabit adapters provides improved performance with the nextgeneration VMDq technology, which includes features such as loop-back functionality for interVM communication, priority-weighted bandwidth management, and doubling the number of data queues per port from four ...
... This generation of PCIe Intel® Gigabit adapters provides improved performance with the nextgeneration VMDq technology, which includes features such as loop-back functionality for interVM communication, priority-weighted bandwidth management, and doubling the number of data queues per port from four ...
Intel® Ethernet Converged Network Adapters X710 10/40 GbE
... warranty arising from course of performance, course of dealing, or usage in trade. This document contains information on products, services and/or processes in development. All information provided here is subject to change without notice. Contact your Intel representative to obtain the latest forec ...
... warranty arising from course of performance, course of dealing, or usage in trade. This document contains information on products, services and/or processes in development. All information provided here is subject to change without notice. Contact your Intel representative to obtain the latest forec ...
Intel Analytics
... different processor families. Go to: http://www.intel.com/products/processor_number Intel, processors, chipsets, and desktop boards may contain design defects or errors known as errata, which may cause the product to deviate from published specifications. Current characterized errata are available o ...
... different processor families. Go to: http://www.intel.com/products/processor_number Intel, processors, chipsets, and desktop boards may contain design defects or errors known as errata, which may cause the product to deviate from published specifications. Current characterized errata are available o ...
Page 1 CHALLENGES With more than 200,000 active students
... Secure out-of-band access to distributed IT equipment has been crucial for enterprise customers to eliminate the need for onsite remote IT staff or service calls to handle outages. Not only does this save travel costs, but out-of-band access also reduces recovery time in the event of unplanned outag ...
... Secure out-of-band access to distributed IT equipment has been crucial for enterprise customers to eliminate the need for onsite remote IT staff or service calls to handle outages. Not only does this save travel costs, but out-of-band access also reduces recovery time in the event of unplanned outag ...
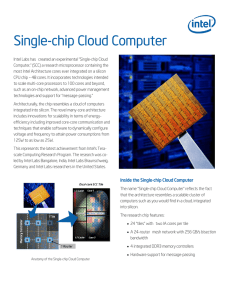
Single-Chip Cloud Computer (SCC)
... most Intel Architecture cores ever integrated on a silicon CPU chip – 48 cores. It incorporates technologies intended to scale multi-core processors to 100 cores and beyond, such as an on-chip network, advanced power management technologies and support for “message-passing.” Architecturally, the chi ...
... most Intel Architecture cores ever integrated on a silicon CPU chip – 48 cores. It incorporates technologies intended to scale multi-core processors to 100 cores and beyond, such as an on-chip network, advanced power management technologies and support for “message-passing.” Architecturally, the chi ...