* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Networking-1
Asynchronous Transfer Mode wikipedia , lookup
IEEE 802.1aq wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Distributed firewall wikipedia , lookup
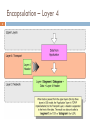
List of wireless community networks by region wikipedia , lookup
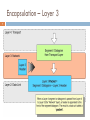
Network tap wikipedia , lookup
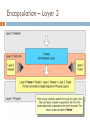
Computer network wikipedia , lookup
Deep packet inspection wikipedia , lookup
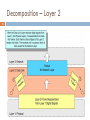
Airborne Networking wikipedia , lookup
Internet protocol suite wikipedia , lookup
Wake-on-LAN wikipedia , lookup
UniPro protocol stack wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
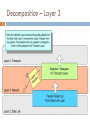
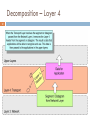
BCIS 4630 Fundamentals of IT Security NETWORKING (Par t1) Dr. Andy Wu OSI Model 2 Network communications protocols are developed using the Open System Interconnection (OSI) model. An ISO standard for worldwide communications. The OSI model defines a framework for implementing protocols in seven distinct layers. Each layer makes use of the services of the layer below it to provide a set of specific services to the layer above it. Adjacent layers communicate with each other through a well-defined interface, so that in principle, we could change one layer or even completely rewrite it without affecting the others. OSI Layers 3 Layer Function Examples Application User interface Program level communication HTTP, SMTP Presentation Presentation format of data Data conversion if needed ASCII, JPEG, MP3, Encryption Session Establish and maintain communication channels OS, Application access scheduling Transport Reliable or unreliable end-to-end communication Identifies upper layer processes that will receive data TCP, UDP, SPX Network Logical addressing and routing Delivering packets from source to destination IP, IPX Data Link Transforming physical layer into a reliable link and presenting it to upper layers Includes MAC (802.3) and LLC (802.2) sublayers Ethernet Physical Transmission of bit stream over physical medium Signaling EIA/TIA 568B OSI Mnemonic 4 Away Application Pizza Presentation Sausage Session Throw Transport Not Network Do Data Link Please Physical Encapsulation 5 When data is passed down from higher layers to lower ones, each layer creates its header and places the data given to it by the next-higher layer behind its own header, thereby encapsulating the higher layer’s data. The Data Link layer also creates a trailer. Encapsulation – Layer 4 6 Encapsulation – Layer 3 7 Encapsulation – Layer 2 8 Network Communication 9 Decomposition – Layer 2 10 Decomposition – Layer 3 11 Decomposition – Layer 4 12 Protocol Data Unit 13 A term that describes a set of bytes that includes the layer’s header and trailer (if any) and all data encapsulated. From Layer X’s perspective, the higher-layer headers and the user data form one large data field. Layer(s) PDU Application, Presentation, Session Data Transport TCP Segment UDP Datagram Network IP Packet Data Link Frame Physical Bit Internet Control Message Protocol 14 Internet Control Message Protocol (ICMP) is a control and information protocol, which is used to determine: Remote network’s availability. Length of time to reach a remote network. The best route for packets to reach a remote network. ICMP can handle the flow of traffic, telling other network devices to “slow down” transmission speeds if packets are coming in too fast. ICMP is not connection-oriented (uses UDP). Designed to carry small messages quickly. Has minimal overhead. Has minimum impact to bandwidth. ICMP Message Types 15 ICMP messages are used to exchange information about network host status, traffic condition, etc. Two important fields in an ICMP message are: Type: A one-byte field to indicate the kind of ICMP message. Code: For message of certain types, a one-byte Code field may have a value to further identify a message. For example, a ping command goes from one host to another and receive a response from the latter. Two types of ICMP messages are involved in this process: Echo Request Echo Reply ICMP Messages 16 Type Description 0 Echo Reply 3 Destination Unreachable 4 Source Quench 5 Redirect Message 8 Echo Request Code Description 0 Network unreachable 1 Host unreachable 3 Port unreachable 6 Destination network unknown 7 Destination host unknown Address Translation 17 Types of Addresses 18 Communications between network computers (hosts) would be impossible without unique addresses for each host. Computers on a local network use MAC addresses to communicate with each other. To access hosts on remote networks, such as those on the Internet, a computer needs to know their IP addresses. Routers will route the packets to the destination network by looking up those IP addresses in the routers’ routing tables. IP addresses are difficult for humans to memorize, so DNS Names (e.g., www.unt.edu) are used by humans. Address Resolution 19 Therefore, two types of address translation (resolution) are essential to network communications. DNS Name-IP Address Resolution When a person uses a human-readable address like www.unt.edu, that address must be resolved into an IP address. IP-MAC Address Resolution Scenario 1: If that IP address is local, the resolution of the IP address into MAC address takes place right away. Scenario 2: If that IP address is remote, the packet is routed to the remote network first. Then, once the packet gets to the remote network, it is resolved into a MAC address on that network. In both scenarios, the host owning that MAC address will take care of the packet. DNS-IP Resolution 20 Domain Name Service (DNS) translates user friendly names (called Fully Qualified Domain Names, or FQDNs) into IP addresses. For example, www.unt.edu = 129.120.188.44 The DNS server handles DNS queries by examining its local records to see if it knows the answer. If it does not, the DNS server queries higher level domain servers. They check records or query the server above them and so on until a match is found. A domain’s DNS servers maintain a database that records all DNS name-IP mappings inside the domain, including those for web servers, directory servers, email servers, hosts, etc. Layer 3: IP Addresses 21 It is common to express the 32-bit IP addresses in a decimal form (dotted decimal notation). The address is divided from the high-order bit to the low-order bit into four 8-bit units called octets. IP addresses are normally written as four separate decimal octets delimited by a period (a dot). Each octets has eight bits and each bit has two possible values: 0 and 1. Thus, in decimal terms, an octet can have 28 or 256 possible values, ranging from 0 to 255. Layer 3: IP Addresses 22 An IP address is broken down into two portions: Network ID and Host ID. Without subnetting, the end of the network ID falls on a 8-bit boundary (e.g., the 16th bit in a Class B subnet). The network ID, or network address, identifies the nodes that are located on the same logical network. The host ID, or host address, identifies a node within a network. An address with a host ID of all zeros is not assigned to any host. It is reserved to define the network itself (network address, e.g., “the 132.170.0.0 network”). If the host ID is all 1s, the address is a broadcast address (e.g., 132.170.255.255). It is used to send a packet to all hosts on a specific network. It can only be a destination address; no host can be assigned this address. IP Addresses 23 Class A Class B Class C Source: Davies and Lee, Windows Server 2003 TCP/IP Protocols and Services. CIDR Notation 24 A shorthand for subnet masks (n.n.n.n stands for an IP address). It indicates the number of bits that are set to 1 in the mask. n.n.n.n/8 for class A default mask, equivalent to 255.0.0.0 n.n.n.n/16 for class B default mask, equivalent to 255.255.0.0 n.n.n.n/24 for class C default mask, equivalent to 255.255.255.0 Private Addresses 25 An organization can use any IP addresses for its network, as long as it is not connected to the Internet. If it wants to use the addresses on the Internet, however, it has to apply for them from Internet Corporation for Assigned Names and Numbers (ICANN). Three blocks of addresses are reserved for private networks. Class A: 10.0.0.0 – 10.255.255.255 Class B: 172.16.0.0 – 172.31.255.255 Class C: 192.168.0.0 – 192.168.255.255 Private addresses are not routable on the Internet. Layer 2: MAC Addresses 26 MAC address is a unique, 48-bit hardware address assigned to a device by the manufacturer. Each manufacturer is assigned a specific block of MAC addresses (the first 24 bits). The manufacturer assigns the device a unique address (the second 24 bits). No two devices can share the same MAC address. For one system to send data to another on the local network, it must first find out the destination system’s MAC address. IP-MAC Address Resolution 27 To find a MAC address, the Address Resolution Protocol (ARP) is used. Using an ARP request, the sending system will broadcast a query – “who is 129.120.188.44”? This broadcast query is examined by every host on the local network, but only the system whose IP address is 129.120.188.44 will respond. IP-MAC Address Resolution 28 That system will send back a response that says “I’m 129.120.188.44 and my MAC address is 00:07:e9:7c:c8:aa.” The sending system will then format the packet for delivery and drop it on the network media, with the MAC address of the destination host. If a host cannot find the destination host in this way, the packet is forwarded to the default gateway, which is the computer/router that knows how to route those packets. What happens if the receiving “host” is 129.120.255.255? The broadcast MAC address is all Fs. Broadcast 29 Used in one-to-everyone communications. A broadcast IP address is designed to be processed by every IP node on the same network segment. It is in the format of Class A: nnn.255.255.255 Class B: nnn.nnn.255.255 Class C: nnn.nnn.nnn.255 The broadcast IP packet is addressed at the Data Link layer using the network technology's broadcast address. For example, for Ethernet and Token Ring networks, all IP broadcasts are sent using the Ethernet and Token Ring broadcast address 0xFF-FF-FF-FF-FF-FF. Unicast 30 Used in one-to-one communications. A packet is sent from an individual source to an individual destination. In a hub-connected network, all hosts on the network segment see the packet. In normal mode, however, all hosts except the intended receipt will pick up and process the packet.