* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download UNIX Operating System
MTS system architecture wikipedia , lookup
Mobile operating system wikipedia , lookup
Copland (operating system) wikipedia , lookup
Distributed operating system wikipedia , lookup
Windows NT startup process wikipedia , lookup
Burroughs MCP wikipedia , lookup
Security-focused operating system wikipedia , lookup
Berkeley Software Distribution wikipedia , lookup
Plan 9 from Bell Labs wikipedia , lookup
Spring (operating system) wikipedia , lookup
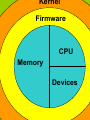
Agenda Administrative Issues Link of the Week This Week’s Expected Outcomes Points of interest Moving around in UNIX Break-Out Problems Upcoming Deadlines Hands-on Information Lab Assistance, Questions, and Answers Announcements Announcements Final exam August 4 through 9. Link of the week Encoding www.fileformat.info/info/unicode/utf8.htm Unicode now replaces ASCII, ISO 8859 and EUC. It enables users to handle not only practically any script and language used on the planet, it also supports a comprehensive set of mathematical and technical symbols to simplify scientific information exchange. With UTF-8 encoding, Unicode can be used in a convenient and backwards compatible way in environments that were designed around ASCII, like UNIX. UTF-8 is the way in which Unicode is used under UNIX, Linux, and other systems. This Week’s Expected Outcomes Upon successful completion of this module, the student will be able to: Manipulate user accounts. Describe how cron is used to invoke repetitive processes. Manipulate process structure including: A. fork/execute, B. Initialization process, C. Background/foreground, D. PS tool. Explain basic UNIX and Linux security issues. Describe disk and file system structure. Use backup and restore archival operations on a system. Establish network services. Investigate the structure of the LDAP directory using LDAP commands. Kernel Firmware CPU Memory Devices UNIX Operating System “Initializing” or “booting” the machine The startup process of a computing system is the installation of software. Many pieces of the software are configured into subsystems and are interdependent upon each other. The boot up procedure utilized by Linux, HPUX UNIX and Solaris is based on the UNIX System V procedure. Red Hat Enterprise Linux 6.0 boot up procedure is based on the Upstart procedure. UNIX Operating System Steps involved in the boot procedure CPU mode is set to RESET CPU is pre-programmed to begin execution at hex address 0Xfffffff0. Address 0Xfffffff0 is mapped to ROM (Read Only Memory). This ROM (BIOS ) address contains a set of routines that are burnt on the chip UNIX Operating System “Initializing” or “booting” the machine The I/O routines on the BIOS continue the boot process by reading Track 0, Sector 1 of the hard disk. This is the location of the Master Boot Record (MBR). The size of the MBR is 512 bytes. The MBR contains the disk partition tables, and executable code which is the first part of the boot loader. The MBR is independent of the kernel. The Linux operating system, most modern boot loaders (such as LILO or GRUB), allows users to change the process the kernel will spawn. UNIX Operating System MBR The information about how a hard disk has been partitioned is stored in its first sector (that is, the first sector of the first track on the first disk surface). The first sector is the master boot record (MBR) of the disk; this is the sector that the BIOS reads in and starts when the machine is first booted. UNIX Operating System The master boot record contains a small program that reads the partition table, checks which partition is active (that is, marked bootable), and reads the first sector of that partition, the partition's boot sector (the MBR is also a boot sector, but it has a special status and therefore a special name). This boot sector contains another small program that reads the first part of the operating system stored on that partition (assuming it is bootable), and then starts it. UNIX Operating System The boot loader is responsible for loading the kernel into memory. Boot loaders are independent of the operating system and are executable code found inside the MBR. The boot loader must share the 512 bytes with the partition table. UNIX Operating System “Initializing” or “booting” the machine The LILO is independent of specific file system, and can boot an operating system from floppy disks and hard drives. There are sixteen different images that can be selected at boot time. LILO can be placed either in the master boot record (MBR) or the boot sector partition. In the latter case, something else like a reference must be placed in the MBR to load LILO. UNIX Operating System Define: Linux initrd The /dev/initrd file is a read-only block device. The /dev/initrd is a RAM disk device that is loaded by the boot loader into memory before the kernel is started. The kernel utilizes this block device for a two phased system boot-up. During the first phase, the kernel starts up and mounts an initial root filesystem from the contents of the /dev/initrd (RAM disk is initialized by the boot loader). The second phase, additional drivers or other module information are loaded from the initial root device as contents. After loading all modules, a new root filesystem (/etc/fstab) is mounted from a different device. UNIX Operating System What is a Block Device? Block device is a device you can read blocks of information. Some block devices are CDROM, hard disk, and floppy disks. The following dd statement reads one 512 byte record. dd if=/dev/sda1 of=/dev/null count=1 Command: ls –l /dev/initrd brw-rw---- 1 root disk 1, 250 Jun 24 2004 initrd brw-rw---- 1 root disk 1, 10 Sep 8 2011ram10 UNIX Operating System Character Device Character special files or character devices relate to devices through which the system transmits data one character at a time. These device nodes often serve for stream communication with devices such as mice, keyboards, virtual terminals, and serial modems, and usually do not support random access to data. In most implementations, character devices use un-buffered input and output routines. The system reads each character from the device immediately or writes each character to the device immediately. crw------- 1 root root 5, 1 Sep 8 2011 console crw--w---- 1 root tty 4, 44 Sep 8 2011 tty44 UNIX Operating System Role of the kernel Once the drivers have been loaded, execution is turned over to the kernel. The kernel then executes a series of steps. - Determines memory size - Initializes Data Structure - Mount root partition - Hardware Configuration Kernel configures information based on probing the system bus, and querying drivers for information. Devices that are missing drivers are considered disabled. - Hand crafted/Spontaneous processes. UNIX Operating System Linux Kernel Data Structure (task_struct) The task_struct data structure contains the following fields: - Process state running returning from system call processing an interrupt routine processing a system call ready waiting - Processes priority - Clock ticks (10ms intervals) which the process can continue executing without being forced rescheduling. - Error number of the last faulting system call UNIX Operating System - Describe a processes: original parent, parent, youngest child, younger sibling, and finally older sibling. - Process ID - Timing information; for example, the amount of time the process has spent in user mode. UNIX Operating System Linux Kernel The Linux kernel process table is a data structure that describes all processes that currently exist. The process table is implemented as an array of pointers to task structures. The kernel process table is limited in size to 512 entries and has its own block size. All Linux blocks are currently 1024 bytes. UNIX Operating System Role of the init process The kernel starts a few spontaneous/handcrafted processes in user space. The origin of the init process is from the kernel and not the fork and execute procedure. The init process has a Process ID (PID) of one (1) and a Parent Process ID of zero (0). The init process is the ultimate parent in the running system and plays an important role in the startup process. All future processes on the system are descendents of the init process. UNIX Operating System Role of the init process Once the system processes are created, then the kernels work is basically completed. The init process performs the following tasks: Executions the /etc/rc.d/rc.sysinit script Sets the system clock Activates the paging process Starts the RAID devices Check and mounts other file systems Executes the /etc/inittab script Executions of run commands Switch to multi user mode UNIX Operating System init process After the run commands (rc) have executed, the system is fully operational. It looks for the file /etc/inittab to see if there is an entry of the type initdefault. The initdefault entry determines the initial run level of the system. Display: /etc/inittab file init login process 1. Init process spawns the getty or minigetty process. 2. The getty process invokes the login process. After the user name has been entered, it is passed to the login process. UNIX Operating System init process 3. The login process prompts the user for a user password, and verifies it. If authentication is successful, the user’s shell is created. Otherwise, a failure causes an error message, ends and then init process will respawn getty or minigetty. 4. The user’s preferred shell will be invoked creating a session. 5. Eventually, the user will logout. UNIX Operating System The /etc/inittab file on the cs.franklin.edu machine has been updated with Red Hat 6.0. This new release affects Lab Assignment 9-1 because information has been removed from the /etc/inittab file. Currently, the new release of the /etc/inittab file is accessed during boot up for the default run level (id:3:initdefault). Otherwise, system initialization, individual run levels, and the Ctrl-Alt_Delete feature are handled by different files. UNIX Operating System UNIX Operating System In UNIX, a process is a name given to a program being executed by the operating system. In Linux, that same program is referred to as a task or process. Linux considers both names as the same. A process consist of: - Program code, data, and stack - Open files (stdin, stdout, stderr) - System data structures - Environment (terminal type, user login directory, $HOME) A Linux system will share code and system libraries among processes so that memory can be conserved and only keep one copy of the code is in memory at a time. UNIX Operating System Process Each Linux process is allocated a unique process identifier (PID). The range of PIDs is usually between 2 and 32,768. A process can be terminated several ways: - Foreground process by typing Ctl-C - Background process with PID=n and typing kill [option] -n UNIX Operating System Process Processes go through various process states during their existence. These transitory states are managed by the operating system (OS). The specifics of these process states vary from one OS to another, as well as the state names. UNIX Operating System Process Process states: 1. Created (fork and exec) 2. Waiting (process scheduler - load from secondary storage to main memory) 3. Running (after a process is assigned a processor by a short –term scheduler, context switch is performed) 4. Blocked (waiting for resources - user input or secondary storage input. Then process is moved back to “waiting”state) 5. Terminated (finished execution, waits to be removed from main memory) UNIX Operating System Process Summary In UNIX-like operating systems, the kernel is invoked when a process issues a system call. All processes have owners. Processes transition through various states. When an original process (parent) creates or spawns another processes (child), it inherits the file access and execution privileges belonging to the parent (basic frame work of the parent). UNIX Operating System UNIX Operating System UNIX Operating System UNIX Operating System What is a thread? The amount of work performed by a process or task. - A single threaded process is a process only performs one task. - A multi-threaded process is a process that performs multiple tasks concurrently without incurring additional overhead needed to create a new process. UNIX Operating System Shutdown command One commonly issued form of this command is shutdown -h now, which will shut down a system immediately. Another one is shutdown -r now to reboot. Another command format allows the user to specify an exact time or a delay before shutdown: shutdown -h 20:00 will turn the computer off at 8:00 PM, and shutdown -r -t 60 will automatically reboot the machine within 60 seconds (one minute) of issuing the command. UNIX Operating System Shutdown command The complete syntax of the Linux version of the command is: usage: shutdown [-akrhfnc] [-t secs] time [message] -a use /etc/shutdown.allow -k don't really shutdown, only warn -r reboot after shutdown -h halt after shutdown -f do a 'fast' reboot (skip fsck) -F force fsck on reboot -n do not go through "init" but go down real fast -c cancel a running shutdown -t secs delay between warning and kill signal UNIX Operating System Kill Command Caveat: The command kill sends the specified signal to the specified process or process group. As a precaution, avoid indiscriminate use of the kill command on jobs involving text editors, databases programs, mail programs, or any other program that has a large amount of user interaction. The kill command terminates a job without saving any of the user input or program results. UNIX Operating System /etc/password File Location: /etc/passwd Field separators: Colon (:) File format: Username:Password:UID:GID:UserID:Home directory:Command/shell Example: dandrear:x:1020:1021:dandrear user:/export/home/dandrear:/bin/bash Permissions on Einstein: -rw-r--r-- 1 root root 1636 Aug 16 10:37 /etc/passwd UNIX Operating System /etc/Passwd File Username: It is used when user logs in. It should be between 1 and 32 characters in length. Password: An x character indicates that encrypted password is stored in /etc/shadow file. User ID (UID): Each user must be assigned a user ID (UID). UID 0 (zero) is reserved for root and UIDs 1-99 are reserved for other predefined accounts. Further UID 100-999 are reserved by system for administrative and system accounts/groups. Group ID (GID): The primary group ID (stored in /etc/group file) User ID Info: The comment field. It allow you to add extra information about the users such as user’s full name, phone number etc. This field use by finger command. UNIX Operating System /etc/Passwd File Home directory: The absolute path to the directory the user will be in when they log in. If this directory does not exists then users directory becomes / Command/shell: The absolute path of a command or shell (/bin/bash). Typically, this is a shell. Please not it does not have to be a shell. UNIX Operating System /etc/shadow File Location: /etc/shadow Field separators: Colon (:) File format: username:passwd:lastpasswdch:min:max:warn:inactive:expire:unused Example: dandrear:$1$dhBysgdhfteM9gd00:13064:0:99999:7::: Permissions on Einstein: -r-------- 1 root root (Permission denied) 1107 Sep 5 15:24 /etc/shadow UNIX Operating System /etc/shadow File User name : It is your login name Password: It your encrypted password. The password should be minimum 6-8 characters long including special characters/digits Last password change (last changed): Days since Jan 1, 1970 that password was last changed Minimum: The minimum number of days required between password changes i.e. the number of days left before the user is allowed to change his/her password Maximum: The maximum number of days the password is valid (after that user is forced to change his/her password) Warn : The number of days before password is to expire that user is warned that his/her password must be changed UNIX Operating System /etc/shadow File Inactive : The number of days after password expires that account is disabled Expire : days since Jan 1, 1970 that account is disabled i.e. an absolute date specifying when the login may no longer be used Unused field: UNIX Operating System /etc/group File Location: /etc/group Field separators: Colon (:) File format: Group name:Password:GID:User_list Example: faculty:x:410: staff:x:430: Permissions on Einstein: -rw-r--r-- 1 root root 833 Aug 16 10:37 group UNIX Operating System /etc/group File Group name: Name of the group. Password: The group password would be encrypted. If this field is empty, no password is needed. GID: The numerical group ID and/or unique group identifier. User_list: All the group member's user names, separated by commas. UNIX Operating System UNIX Operating System UNIX Operating System Adding Users on a system Performed in three ways: 1. Manually through the system interface 2. Adduser/deluser commands (demonstrate on Knoppix software) 3. Using a GUI system administration tool Demonstrate Knoppix adduser/deluser UNIX Operating System Security Features Linux Network daemon uses xinetd to monitor all configured ports and starts system resources usage only on-demand, since the daemons aren’t running all the time. Security and resource usage is the main objective. UNIX Operating System Chroot jail Utilized by Linux and UNIX OS to create an artificial root directory. Creating a temporary root directory prevents a program from accessing or modifying files outside the directory hierarchy starting at its root. Chroot affects only the current process and its child processes. The files need to be placed in the jail directory (such as /users) in directories that mimic their placement in the root (/) file system. So you need to copy all required files. For example, /usr/bin/rssh is located on / file system. If your jail is located at /users, then copy /usr/bin/rssh to /users/usr/bin/rssh. UNIX Operating System SELinux Developed by the U.S. National Security Agency (NSA), implements Mandatory Access Control (MAC) in the Linux kernel. MAC enforces security policies that limit what a user or program can do. It defines a security policy that controls some or all objects, such as files, devices, sockets, and ports, and some subjects like processes. Utilizing SELinux, you can grant a process only those permissions it needs to be functional. UNIX Operating System TCP Wrapper It iis part of the client/server model, and can be used with any daemon that is linked against libwrap.a, and relies on the /etc/hosts.allow and /etc/hosts.deny files are the basis of a simple access control language. This access control language defines rules that selectively allow clients to access server daemons on a local system based on the client’s address and the daemon the client tries to access. UNIX Operating System Security Features The iptables utility builds and manipulates network packet filtering rules in the Linux kernel. You can use iptables to create a firewall that protects a system from outside intruders. UNIX Operating System Points of interest Display the processes running on your system. If you see cupsd, the CUPS daemon, is running, so the system is using CUPS for printing. Moving Around in UNIX sudo - Set user and do. Execute a single command as another user (root is the default). lsof - List open files on the system. Normally, it only lists files you (or processes you own) have open; if run as root, it lists all open files. Moving Around in UNIX ifconfig - Configure network interfaces (e.g. ethernet ports, AirPort cards, etc). printenv - print out environment whois - Internet user name directory service Break-out problems 1. simple_script & 2. What is a zombie process? 3. What files are updated on a Linux system when a new user is added? 4. fork() 5. What information is stored in the /etc/passwd file? 6. What information is stored in the /etc/shadow file? 7. What information is stored in the /etc/group file? 8. What is a background process? 9. What is a foreground process? 10. What is an orphan process? 11. kernel 12. nice command 13. init process Hands on information Lab Assignment 9-1,Startup /Shutdown due July 6, 2014 Lab Assignment 10-1, 10-2 Account/LDAP/Process due July 23, 2014 After class assistance Questions Comments Concerns I am available after this Franklin Live session to discuss any problems and/or concerns regarding the lab assignments Lab Assistance available by phone and/or email