* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download File
Survey
Document related concepts
Transcript
IT 2201 - DATA STRUCTURES AND ALGORITHMS
UNIT I - LINEAR STRUCTURES
PART A
1. Define data structure.
A data structure is a mathematical or logical way of organizing data in
the memory that consider not only the items stored but also the relationship
to each other and also it is characterized by accessing functions.
2. What do you mean by abstract data type? Give its operations.
An ADT is a set of operation. A useful tool for specifying the logical
properties of a data type is the abstract data type. ADT refers to the basic
mathematical concept that defines the data type. Eg. Objects such as list, set
and graph along their operations can be viewed as ADT's. Union,
Intersection, size, complement and find are the various operations of ADT.
3. What do you mean by list ADT? What are the various operations done
under list ADT?
List ADT is a sequential storage structure. General list of the form a1,
a2, a3.…., an and the size of the list is 'n'. Any element in the list at the
position I is defined to be ai, ai+1 the successor of ai and ai-1 is the
predecessor of ai. Print list, Insert, Make empty, Remove, Next, Previous,
Find kth element in the list are the operations performed on list ADT.
4. Define linked list. Give the types of linked list.
Linked list is a kind of series of data structures, which are not
necessarily adjacent in memory. Each structure contains the element and a
pointer to a record containing its successor.
Types of linked list:
Singly linked list
Doubly linked list
Double circular linked list
5. What is the need for the header?
Header of the linked list is the first element in the list and it stores the
number of elements in the list. It points to the first data element of the list.
1
IT 2201 - DATA STRUCTURES AND ALGORITHMS
6. List out some of the applications of list.
Polynomial ADT
Radix sort
Multi lists
7. What is the principle of radix sort?
Radix sort or bucket sort consists of 10 buckets numbered 0 to 9.
First step of bucket sort is to sort by least significant digit.
The next pass includes sorting the next least significant digit
The pass continues till it scans the most significant digit.
8. Define cursor space. What is the use of cursor?
Cursor space is a list of free cells that are not in any list. When linked
has to be used and there is no pointers available, then an alternative
implementation called cursor implementation is used.
9. Define doubly linked list.
In a simple linked list, there will be one pointer named as 'NEXT
POINTER' to point the next element, where as in a doubly linked list, there
will be two pointers one to point the next element and the other to point the
previous element location.
10.What is a stack? Give its operation
A Stack is an ordered collection of items into which new items may be
inserted and from which items may be deleted at one end, called the top of
the stack. The other name of stack is Last-in -First-out list. Operations of
Stack include Push, Pop and Top.
11.List out the application of stack.
Balancing Symbols
Postfix evaluation
Infix to Postfix expression
12.Define queue and its types.
A Queue is an ordered collection of items from which items may be
deleted at one end called the front of the queue and into which items may be
inserted at the other end called rear of the queue. Queue is called as first –inFirst-Out (FIFO).
2
IT 2201 - DATA STRUCTURES AND ALGORITHMS
Types of Queue:
Circular Queue
Priority Queue
13.How do you test for an empty queue?
To test for an empty queue, we have to check whether READ=HEAD
where REAR is a pointer pointing to the last node in a queue and HEAD is a
pointer that pointer to the dummy header. In the case of array
implementation of queue, the condition to be checked for an empty queue is
READ<FRONT.
14.List out some applications of queue.
Queue in real world.
Job queue in printers
Phone calls waiting that has to be connected in a company
15.Give the procedure for converting infix to postfix.
Scan the expression character by character.
When an operand is read, immediately place it onto the output.
If we see a right parenthesis then pop the stack, writing symbols
until we encounter a left parenthesis.
If we see any symbols(‘+’,’*’,’( ‘) the we opp entries from thee
stack until we find an entry of lower priority.
16.Define activation record.
When there is a function call, all the important information that
needs to be saved, such as register values and return address is saved on a
piece of paper in an abstract way and put at the top of a pile. The
information saved is called an activation record or stack frame.
17.What is the use of stack pointer?
The stack pointer always points to the top of the stack. Stack pointer
is increment when a data is pushed onto the stack and the pointer is
decremented when a data is popped from the stack.
18.Explain the usage of stack in recursive algorithm implementation?
In recursive algorithms, stack data structures is used to store the
return address when a recursive call is encountered and also to store the
values of all the parameters essential to the current state of the procedure.
3
IT 2201 - DATA STRUCTURES AND ALGORITHMS
19.What are the exceptional conditions for stack?
Insertion or pushing a data on to the stack when stack is full is not
possible.
Deletion or popping a data when the stack is empty is not possible.
20.What are the postfix and prefix forms of the expression?
A+B*(C-D)/(P-R)
Postfix form: ABCD-*PR-/+
Prefix form: +A/*B-CD-PR
PART B
1.
2.
3.
4.
5.
6.
7.
8.
9.
Explain the linked list implementation of list ADT in detail?
Explain in detail implementation of list ADT?
Explain briefly cursor implementation of list ADT?
Write in detail about the applications of list.
Explain the implementation of stack using Linked List.
Explain the implementation of stack using Array
Briefly explain about applications of stack.
What is a queue? Write an algorithm to implement queue with example.
Give a procedure to convert an infix expression a+b*c+(d*e+f)/g to
postfix notation.
10.Write an algorithm to check given expression contains balanced
parenthesis or not.
4
IT 2201 - DATA STRUCTURES AND ALGORITHMS
UNIT II - TREE STRUCTURES
PART A
1. Define tree?
A tree is a data structure, which represents hierarchical relationship
between individual data items.
2. Define leaf?
In a directed tree any node which has out degree o is called a terminal
node or a leaf.
3. What is meant by directed tree?
Directed tree is an acyclic diagraph which has one node called its root
with indegree zero while all other nodes have indegree I.
4. What are the applications of binary tree?
Binary tree is used in data processing.
a. File index schemes
b. Hierarchical database management system
5. What is meant by traversing?
Traversing a tree means processing it in such a way, that each node is
visited only once.
6. What are the different types of traversing?
The different types of traversing are
a. Pre-order traversal-yields prefix from of expression.
b. In-order traversal-yields infix form of expression.
c. Post-order traversal-yields postfix from of expression.
7. What are the two methods of binary tree implementation?
Two methods to implement a binary tree are,
a. first child/next sibling representation.
b. Doubly linked list representation
8. Define pre-order traversal?
Pre-order traversal entails the following steps;
a. Process the root node
b. Process the left subtree
c. Process the right subtree
5
IT 2201 - DATA STRUCTURES AND ALGORITHMS
9. Define post-order traversal?
Post order traversal entails the following steps;
a. Process the left subtree
b. Process the right subtree
c. Process the root node
10. Define in -order traversal?
In-order traversal entails the following steps;
a. Process the left subtree
b. Process the root node
c. Process the right subtree
11. What is a balance factor in AVL trees?
Balance factor of a node is defined to be the difference between the
height of the node's left subtree and the height of the node's right subtree.
12. What is meant by pivot node?
The node to be inserted travel down the appropriate branch track
along the way of the deepest level node on the branch that has a balance factor
of +1 or -1 is called pivot node.
13. What is the length of the path in a tree?
The length of the path is the number of edges on the path. In a tree
there is exactly one path form the root to each node.
14. Define expression trees?
The leaves of an expression tree are operands such as constants or
variable names and the other nodes contain operators.
15. Define Strictly binary tree?
If every nonleaf node in a binary tree has nonempty left and right
subtrees ,the tree is termed as a strictly binary tree.
16. Define complete binary tree?
A complete binary tree of depth d is the strictly binary tree all of whose
are at level d.
17. What is an almost complete binary tree?
A binary tree of depth d is an almost complete binary tree if :
i. Each leaf in the tree is either at level d or at level d-1
ii. For any node nd in the tree with a right descendant at level d,
all the left descendants of nd that are leaves are at level d.
6
IT 2201 - DATA STRUCTURES AND ALGORITHMS
18. Define right – in-threaded tree?
Right –in –threaded binary tree is defined as one in which threads
replace NULL pointers in nodes with empty right subtrees.
19. Define left – in –threaded tree?
A left-in-threaded binary tree may be defined as one in which each NULL
pointers is altered to contain a thread to that node’s inorder predecessor.
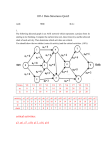
20. Give the prefix, infix and postfix expressions corresponding to the tree
given below. Also find the depth and height.
Prefix:
Postfix:
Infix:
Depth:
Height:
-*
ab*cd+*ea*b*c+d-e
3
3
PART B
1. Explain the operation and implementation of Binary Heap.
2. Define binary search tree? Explain the various operations with an
example?
3. Explain how to find a maximum element and minimum element in BST?
Explain detail about Deletion in Binary Search Tree?
4. Explain in detail (i) Single rotation (ii) double rotation of an AVL tree.
5. Explain the efficient implementation of the priority queue ADT.
6. Show the result of inserting 10,12,1,14,6,5,8,15,3,9,7,4,11,13 and 2 one at
a time into an initially empty binary heap.
7. a) Show that in a binary tree of N nodes, there are N+1 NULL pointers
representing children.
b) Show that the maximum number of nodes in a binary tree of height H
is 2H+1-1
8. a) Show the result of inserting 3, 1,4,6,9,2,5,7 into an initially empty
binary search tree.
b) Show the result of inserting 2, 1,4,5,9,3,6,7 into an initially empty
AVL tree.
7
IT 2201 - DATA STRUCTURES AND ALGORITHMS
UNIT III - HASHING AND SETS
PART A
1. What is the need for hashing?
Hashing is used to perform insertions, deletions and find in
constant average time.
2. Define hash function?
Each key is mapped into some number in the range 0 to
Tablesize-1 and placed in the appropriate cell. The mapping is called hash
function which ideally should be simple to compute and should ensure that
any two distinct keys get different cells.
3. What do you meant by separate chaining?
Separate chaining keep a list of all elements that hash to the same
value. This list have header.
4. What are the problems in hashing?
When two keys compute in to the same location or address in the
hash table through any of the hashing function then it is termed collision.
5. Define open addressing.
Open addressing is an alternative to resolving collisions with linked
lists. In an open addressing hashing system, if a collision occurs, alternative
cells are tried until an empty cell is found.
6. What are the techniques used in open hashing.
Linear probing
Quadratic probing
Double hashing
7. Define linear probing.
In linear probing, f is a linear function of i, f(i)=i. If collision
occurs, alternative cells are tried sequentially until an empty cell is found.
8. What is primary clustering?
If the table is relatively almost empty, blocks of occupied cells
start forming. This is known as primary clustering.
8
IT 2201 - DATA STRUCTURES AND ALGORITHMS
9. What is secondary clustering?
The elements that hash to the same position will probe the same
alternative cells. This is known as secondary clustering.
10.Define rehashing.
If the table gets too full, running time for operations increases and
insertion fails. A solution is to build another table that is about twice as big
and scan down the entire original hash table, computing new hash value for
each element and inserting it in new hash table. This mechanism is called
rehashing.
11.What is equivalence relation?
An equivalence relation is a relation R that satisfies three
properties:
1. (Reflexive) a R a, for all a S.
2. (Symmetric) a R b if and only if b R a.
3. (Transitive) a R b and b R c implies that a R c.
12.Define equivalence class.
The equivalence class of an element a S is the subset of S
that contains all the elements that are related to a.
13.What is disjoint set?
A disjoint-set is a collection ={S1, S2,…, Sk} of distinct
dynamic sets.
Disjoint set operations:
UNION(x,y): combine the two sets containing x and y into one new
set. A new representative is selected.
FIND-SET(x): return the representative of the set containing x.
14.Define path compression.
Path compression is performed during a find operation and
the effect of path compression is that every node on the path from x to the
root has its parent changed to the root
15.List out the application of set.
The application includes the following
a) Transfer of files in computer networks.
b) Generating of maze
16.List out the various techniques of hashing.
Separate chaining
Open addressing
9
IT 2201 - DATA STRUCTURES AND ALGORITHMS
17.What are the two operations performed on disjoint set?
There are two permissible operations. The first is find, which
returns the name of the set (that is, the equivalence class) containing a given
element. The second operation adds relations. If we want to add the relation
a ~ b, then we first see if a and b are already related. This is done by
performing finds on both a and b and checking whether they are in the same
equivalence class. If they are not, then we apply union. This operation
merges the two equivalence classes containing a and b into a new
equivalence class.
18.What is union-by-size?
Union-by-size performs union by making the smaller tree a
subtree of the larger.
19.Define union-by-height.
Union-by-height perform union by making the shallow tree a
subtree of the deeper tree.
20.What are the techniques to overcome hash collision?
Linear probing
Quadratic probing
Double hashing
PART B
1. Explain in detail about Open Addressing
2. Explain any two techniques to overcome hash collision?
3. Given input {4371,1323,6173,4199,4344,9679,1989} and a hash function
h(X)=X(mod10), show the resulting:
i. Separate chaining hash table.
ii. Open addressing hash table using linear probing.
iii. Open addressing hash table using quadratic probing.
iv. Open addressing hash table with second hash function h2(X)
=7-(X mod 7).
4. Describe briefly about dynamic equivalence problem.
5. Explain smart union algorithm with an example.
6. Explain path compression with an example.
10
IT 2201 - DATA STRUCTURES AND ALGORITHMS
UNIT IV - GRAPHS
PART A
1. Define Graph?
A graph G consist of a nonempty set V which is a set of nodes of the
graph, a set E which is the set of edges of the graph, and a mapping from the
set for edge E to a set of pairs of elements of V. It can also be represented as
G= (V, E).
2. Define adjacent nodes?
Any two nodes which are connected by an edge in a graph are called
adjacent nodes. For example, if and edge xÎE is associated with a pair of
nodes (u, v) where u, v Î V, then we say that the edge x connects the nodes u
and v.
3. What is a directed and undirected graph?
A graph in which every edge is directed is called a directed graph. A
graph in which every edge is undirected is called a directed graph.
4. What is a weighted graph?
A graph in which weights are assigned to every edge is called a
weighted graph.
5. Define in degree and out degree of a graph?
In a directed graph, for any node v, the number of edges which have v
as their terminal node is called the indegree of the node v. In a directed
graph, for any node v, the number of edges which have v as their initial node
is called the out degree of the node v.
6. Define path. What is a simple path?
The path in a graph is the route taken to reach terminal node from a
starting node. A path in a diagram in which the edges are distinct is called a
simple path. It is also called as edge simple.
7. What is a cycle or a circuit? Define acyclic graph.
A path which originates and ends in the same node is called a cycle or
circuit.
A simple diagram which does not have any cycles is called an acyclic
graph.
11
IT 2201 - DATA STRUCTURES AND ALGORITHMS
8. What is a forest?
A forest may be defined as an acyclic graph in which every node has
one or no predecessors. A tree may be defined as a forest in which only a
single node called root has no predecessors
9. What is meant by strongly connected in a graph?
An undirected graph is connected, if there is a path from every vertex
to every other vertex. A directed graph with this property is called strongly
connected.
10.When is a graph said to be weakly connected?
When a directed graph is not strongly connected but the underlying
graph is connected, then the graph is said to be weakly connected.
11.Name the different ways of representing a graph?
a. Adjacency matrix
b. Adjacency list
12.What is an undirected acyclic graph?
When every edge in an acyclic graph is undirected, it is called an
undirected acyclic graph. It is also called as undirected forest.
13.What are the two traversal strategies used in traversing a graph?
a. Breadth first search
b. Depth first search
14.What is a minimum spanning tree?
A minimum spanning tree of an undirected graph G is a tree formed
from graph edges that connects all the vertices of G at the lowest total cost.
15.Define Topological sort.
A topological sort is an ordering of vertices in a directed acyclic graph,
such that if there is a path from vi to vj, then vj appears after vi in the ordering.
16. Define single source shortest path problem.
Given as input a weighted graph, G = (V, E), and a distinguished vertex,
s, find the shortest weighted path from s to every other vertex in G.
17.What is Bi connectivity?
A connected undirected graph is biconnected if there are no vertices
whose removal disconnects the rest of the graph.
12
IT 2201 - DATA STRUCTURES AND ALGORITHMS
18.What is Euler Circuit?
We find a path in a graph that visits every edge exactly once. If we are to
solve the extra challenge, then we must find a cycle that visits edge exactly
once. This graph problem is referred to as an Euler path or Euler circuit
problem.
19.Define articulation point.
If a graph is not biconnected, the vertices whose removal would
disconnect the graph are known as articulation points.
20.What is back edge?
It is a dashed line drawn in depth first spanning tree, starting from
unvisited node to visited or marked node.
PART B
1. Formulate an algorithm to find the shortest path using Dijkstra’s
algorithm and explain with an example.
2. Explain the minimum spanning tree algorithms with an example.
3. a) Write short notes on Biconnectivity.
b) Write an algorithm for Topological Sort of a graph.
4. Write and explain weighted and unweighted shortest path algorithm
5. Explain the various applications of Depth First Search.
6. Find a minimum spanning tree for the graph using both Prim’s and
Kruskal’s algorithms.
13
IT 2201 - DATA STRUCTURES AND ALGORITHMS
UNIT V – ALGORITHM DESIGN AND ANALYSIS
PART A
1. How does greedy algorithm works?
Greedy algorithm works in phases. In each phase, a decision is
made that appears to be good, without regards for future consequences. This
means that some local optimum is chosen.
2. List out some of the greedy algorithm.
Coin changing problem.
Scheduling problem.
Huffman codes.
Bin packing.
3. Define bin packing.
Given N items of size s1,s2,s3..,sn. All size satisfy 0<si<=1. The
bin packing problem is to pack these items in the fewest number of bins,
given that each bin has unit capacity.
4. What are the different versions of bin packing?
Online algorithm.
Next fit
First fit
Best fit
Offline algorithm.
5. Define next fit, first fit and best fit algorithms.
Next Fit: When processing any item, check whether it fits in the same
bin as last bin. If it does, place there; otherwise, a new bin created.
First Fit: Scan the bins in order and place the new item in the first bin that is
large enough to hold it.
Best Fit: Instead of placing a new item in the first spot that is found, it is
placed in the tightest spot among all bins.
6. What do you meant by divide and conquer algorithm?
Divide and Conquer consists of two parts:
Divide: Smaller problems are solved recursively.
Conquer: The solution to the original problem is then formed from
the solutions of the sub problems.
Examples: Merge sort, quick sort, closest points problem,
selection problem.
14
IT 2201 - DATA STRUCTURES AND ALGORITHMS
7. What is dynamic programming?
Dynamic programming is defined as rewriting the recursive
algorithm as a non recursive algorithm that systematically records the
answers to the sub problems in a table.
8. Define recurrence.
A recurrence is an equation or inequality that describes a function
in terms of its value on smaller inputs. E.g.: running time of merge sort.
9. Define optimal binary search tree.
Given a list of words w1, w2..Wn and fixed probabilities p1,p2,..pn of
their occurrence. The problem is to arrange these words in a binary search
tree in a way that minimizes the expected total access time. Such tree is
called optimal binary search tree.
10.Define pruning.
The elimination of a large group of possibilities in one step is
known as pruning.
11.What is back tracking?
Backtracking is a refinement of the brute force approach, which
systematically searches for a solution to a problem among all available
options.
12.What are the various methods for solving recurrence?
Substitution method.
Recursion tree.
Master method.
13.Define terminal and successor position.
A position for which the assignments 0 and 1 can be determined by
examining the board is known as terminal position.
A successor position of P is any position Ps that is reachable from P
by playing one move.
14.What is transposition table?
The data structure that records the value of the position is known as
transition table. It is implemented by hashing.
15
IT 2201 - DATA STRUCTURES AND ALGORITHMS
15.Define NP Complete problem.
Among all the problems known to be in NP, there is a subset,
known as the NP-complete problems. NP-complete have the property that
any problem in NP can be polynomially reduced to it.
16.Give the steps in substitution method for solving recurrence.
The substitution method for solving recursion entails two steps
1) Guess the form of the solution.
2) Use mathematical induction to find the constant and show
that the solution works.
17.What is Class NP?
NP stands for nondeterministic polynomial-time. The class NP
includes all problems that have polynomial-time solutions.
18.What is halting problem?
The problems that are harder to solve or impossible to solve are
classified as undecidable problems. One of the undecidable problem is the
halting problem.
19.State the traveling salesman problem.
Given a complete graph G=(V,E), with edge costs, and an integer
K, is there a simple cycle that visits all vertices and has total cost<= K?
20.Give the various asymptotic notations.
Small-oh notation: o (g(n))
Big-oh notation: O(g(n))
Omega notation:
Big-Omega: Ω (g(n))
Small-omega: ω(g(n))
Theta notation: (g(n))
PART B
1.
2.
3.
4.
5.
6.
Describe briefly about Huffman coding algorithm with an example.
Explain divide and conquer algorithm with a suitable example.
Write short notes on bin packing with examples.
Write briefly about backtracking algorithm with examples.
Explain dynamic programming with an application.
Explain in detail NP completeness.
16