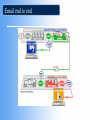
* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Chapter 1: A First Look at Windows 2000 Professional
Survey
Document related concepts
Stored Communications Act wikipedia , lookup
SIP extensions for the IP Multimedia Subsystem wikipedia , lookup
Telecommunication wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
History of telecommunication wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Transcript
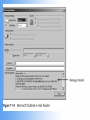
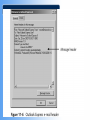
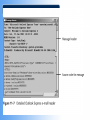
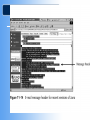
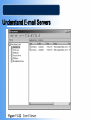
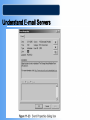
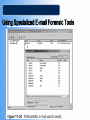
COS/PSA 413 Day 17 Agenda • Lab 8 write-up grades – 3 B’s, 1 C and 1 F – Answer the Questions!!! • Capstone progress report 2 overdue • Today we will be discussing e-Mail investigations – Chap 11 in 1e, Chap 13 in 2e • Lab 10 in OMS tomorrow – 11-1, 11-2, 11-3, 11-4,11-6 – Make sure you know what is you will be doing before you get to the lab – You will need your maine.edu account info • User/password E-mail Investigations Chapter 11 Learning Objectives • Understand Internet Fundamentals • Explore the Roles of the Client and Server in Email • Identify and Investigate E-mail Crimes and Violations • Understand E-mail Servers • Use Specialized E-mail Computer Forensic Tools Understand Internet Fundamentals Internet Service Provider (ISP) – Provides a service or membership that allows you to access the information available on the Internet. Dialup Connection – A connecting device to a network via modem or a public telephone network. Dialup access acts just like a phone connection, except that the two connecting parties are computers instead of people. Understand Internet Fundamentals Understand Internet Fundamentals Code – A group of specialized characters combined in a sequence to provide instructions to a program on how to perform a specific action. Web Browser – A software program used to locate and display web pages. HTML – The authoring language used to create documents on the World Wide Web. It defines the structure and layout of a Web document by using a variety of tags and attributes. Understand Internet Fundamentals Understand Internet Fundamentals Domain Name Service (DNS) – An Internet service that translates domain names to IP addresses. Open Systems Interconnect (OSI) – A standard for worldwide communications that defines a networking framework for implementing protocols in seven layers. Understand Internet Fundamentals Simple Mail Transfer Protocol (SMTP) – A protocol used for sending e-mail messages between servers. Post Office Protocol Version 3 (POP3) – A protocol used to retrieve e-mail messages from an e-mail server. Internet Message Access Protocol version 4 (IMAP) – A protocol for retrieving e-mail messages. Supports more features than POP3. Explore the Roles of the Client and Server in E-mail Mail to and from Email end to end Explore the Roles of the Client and Server in E-mail Universal Naming Convention (UNC) – A PC format that specifies the location of resources on a local area network. It uses the following format: \\servername\shared resource-pathname. Identify and Investigate E-mail Crimes and Violations To Copy an E-Mail Message from Outlook 1. Insert formatted floppy disk into the drive. 2. Start Outlook . 3. Making sure the folders list is open, click the folder that contains the file you would like to copy. 4. Resize the Outlook window so that you can see the message you want to copy and the icon for the floppy disk. 5. Click and drag the message from Outlook to the floppy disk drive. Identify and Investigate E-mail Crimes and Violations Identify and Investigate E-mail Crimes and Violations Investigation Process - Copy the e-mail you would like to investigate. - Print the e-mail message. - View the file header. - Examine the file header and body of the e-mail. - Open any attachments. - Trace the e-mail, record all IP Addresses. - Document all findings. Identify and Investigate E-mail Crimes and Violations Router – A network device that connects a number of local area networks together. Routers use the IP address to determine the destination of a packet. Identify and Investigate E-mail Crimes and Violations Understand E-mail Servers E-mail Server – A computer that is running an operating system such as UNIX or Windows 2000 that is loaded with software to manage the transmission and holding of e-mail messages. Understand E-mail Servers Understand E-mail Servers Understand E-mail Servers Understand E-mail Servers Understand E-mail Servers Understand E-mail Servers Understand E-mail Servers Understand E-mail Servers GroupWise – The Novell e-mail server software; a database server like Microsoft Exchange and UNIX Sendmail. Using Specialized E-mail Forensic Tools Tools That Can Investigate E-mail Messages - EnCase - FTK - FINALe-mail - Sawmill-GroupWise - Audimation for Logging Using Specialized E-mail Forensic Tools Using Specialized E-mail Forensic Tools Chapter Summary - Because e-mail programs employ some protocols used with the internet to exchange messages, you should understand the fundamentals of the Internet to realize how email works. - You can send and receive e-mail via the Internet and local area network. Client computers access e-mail servers to receive messages. - Investigating crimes or policy violations with email is similar to other computer crimes and abuses. Chapter Summary - Once you have determined that a crime has been committed using e-mail, first access the victims computer to recover any evidence, then copy the e-mail messages from the victims computer. - Be sure to copy and print any e-mail messages that will be used in the investigation. - Examine the e-mail header, trace the IP address from the sending computer, and record the date and time stamps of the e-mail message. Chapter Summary - To investigate e-mail, you should know how an e-mail server records and handles e-mail messages. E-mail servers are databases of user information and e-mail messages. All e-mail servers contain a log file which can tell valuable information when investigating a crime. - For many e-mail investigations, you can rely on the message files, e-mail headers, and e-mail server log files to investigate e-mail crimes.