* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Introduction to network security
Survey
Document related concepts
Transcript
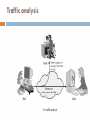
INTRODUCTION TO NETWORK SECURITY L. Tahani Al jehani COMPUTER SECURITY CONCEPTS Information security : Before the widespread use of data processing equipment, the security of information felt to be valuable to an organization was provide primarily by physical and administrative means. An example of the former is the use of rugged filing cabinets with a combination lock for storing sensitive documents. computer security (cyber security) With the introduction of the computer, the need for automated tools for protecting files and other information stored on the computer became evident. Especially the case for a shared system, such as a timesharing system, and for systems that can be accessed over a public telephone network, data network, or the Internet. (server) The generic name for the collection of tools designed to protect data is computer security. Computer security "Security is the ability of a system to protect information and system resources with respect to confidentiality , availability, and integrity." Note that the definition includes system resources, which include CPUs, disks, and programs, in addition to information. Challenges of computer and network security 1. 2. Challenges of computer and network security: Security is not simple as it might first appear to the novice: we need to consider potential attacks . Security mechanisms typically involve more than a paticular algorithm. Having designed various security mechanisms, it is necessary to decide where to use them (physical and logical sense). What points in a network are certain secured mechanisms needed? What layer or layers of our architecture should mechanisms be placed? Key Security Concepts Computer security is frequently associated with three core areas, which can be conveniently summarized by the acronym "CIA“ Confidentiality -- Ensuring that information is not accessed by unauthorized persons Integrity -- Ensuring that information is not altered by unauthorized persons in a way that is not detectable by authorized users Authentication -- Ensuring that users are the persons they claim to be CIA A strong security protocol addresses all three of these areas. Take, for example, Netscape's SSL (Secure Sockets Layer) protocol. It has enabled an explosion in ecommerce which is really about trust (or more precisely, about the lack of trust). SSL overcomes the lack of trust between transacting parties by ensuring confidentiality through encryption, integrity through checksums, and authentication via server certificates CIA Computer security is not restricted to these three broad concepts. Additional ideas that are often considered part of the taxonomy of computer security include: Access control -- Ensuring that users access only those resources and services that they are entitled to access. Nonrepudiation -- Ensuring that the originators of messages cannot deny that they in fact sent the messages Availability -- Ensuring that a system is operational and functional at a given moment, usually provided through redundancy; loss of availability is often referred to as "denial-of-service" Privacy -- Ensuring that individuals maintain the right to control what information is collected about them, how it is used, who has used it, who maintains it, and what purpose it is used for Network security The second major change that affected security is the introduction of distributed systems (telecommunication , internet , wireless sensors network ) and the use of networks and communications facilities for carrying data between terminal user and computer and between computer and computer. Network security measures are needed to protect data during their transmission Protecting network and telecommunications equipment, protecting network servers and transmissions, combatting eavesdropping, controlling access from untrusted networks, firewalls, and detecting intrusions Scenario of massage interception in network User A transmits a file to user B. The file contains sensitive information that is to be protected from disclosure. User C, who is not authorized to read the file, is able to monitor the transmission and capture a copy of the file during its transmission. Security Trends In 1994, the Internet Architecture Board (IAB) issued a report entitled "Security in the Internet Architecture“ The report stated that the Internet needs more and better security. the need to secure the network infrastructure from unauthorized monitoring and control of network traffic and the need to secure end-user-to-end-user traffic using authentication and encryption . OSI The OSI model is a layered model that describes how information moves from an application running on one networked computer to an application running on another networked computer Security Architecture for OSI Security Architecture for OSI defines systematic way to : Defining the requirements for security Characterizing the approaches to satisfying those requirements Examples of Security Requirements confidentiality – student grades integrity – patient information availability – authentication service Security Architecture for OSI The OSI security architecture focuses on security attacks, mechanisms, and services. • Security attack: Any actions that compromises the security of information owned by an organization (or a person) • Security mechanism: a mechanism that is designed to detect, prevent, or recover from a security attack • Security service: a service that enhances the security of the data processing systems and the information transfers of an organization. The services make use of one or more security mechanisms to provide the service Security attacks Passive attack: aims to learn or make use of information from the system but does not affect system resources. Like eavesdropping on, or monitoring of, transmissions. The goal is to obtain information that is being transmitted Active attack: attempts to alter system resources or affect their operation Passive Attacks Passive Attacks : the release of message contents A telephone conversation, an electronic mail message, and a transferred file may contain sensitive or confidential information. We would like to prevent an opponent from learning the contents of these transmissions. Traffic analysis also encrypted data can be read the release of message contents Traffic analysis Passive attacks Passive attacks are very difficult to detect, because they do not involve an alteration of the data. Typically, the message traffic is sent and received in an apparently normal fashion, and neither the sender nor receiver is aware that a third party has read the messages or observed the traffic pattern. Active Attacks Active attacks involve some modification of the data stream or the creation of a false stream and can be subdivided into four categories: Masquerade. Replay. modification of messages. denial of service. Masquerade A masquerade attack usually includes one of the other forms of active attack. For example, authentication sequences can be captured and replayed after a valid authentication sequence has taken place, thus enabling an authorized entity with few privileges to obtain extra privileges by impersonating an entity that has those privileges. Masquerade Replay Replay involves the passive capture of a data unit and its subsequent retransmission to produce an unauthorized effect Modification of messages Modification of messages simply means that some portion of a legitimate message is altered, or that messages are delayed or reordered, to produce an unauthorized effect For example, a message meaning “Allow John Smith to read confidential file accounts” is modified to mean “Allow Fred Brown to read confidential file accounts.” denial of service prevents or inhibits the normal use or management of communications facilities the disruption of an entire network, either by disabling the network or by overloading it with messages so as to degrade performance. denial of service SECURITY SERVICES Network security can provide one of the five services as shown in Figure. Four of these services are related to the message exchanged using the network: message confidentiality, integrity, authentication, and nonrepudiation. The fifth service provides entity authentication or identification. SECURITY SERVICES Message Confidentiality Message confidentiality or privacy means that the sender and the receiver expect confidentiality. The transmitted message must make sense to only the intended receiver. To all others, the message must be garbage. When a customer communicates with her bank, she expects that the communication is totally confidential. Message Integrity Message integrity means that the data must arrive at the receiver exactly as they were sent. There must be no changes during the transmission, neither accidentally nor maliciously. For example, it would be disastrous if a request for transferring $100 changed to a request for $10,000 or $100,000. The integrity of the message must be preserved in a secure communication. Message Authentication Message authentication is a service beyond message integrity. In message authentication the receiver needs to be sure of the sender'sidentity and that an imposter has not sent the message. Message Nonrepudiation Message nonrepudiation means that a sender must not be able to deny sending a message that he or she, in fact, did send. The burden of proof falls on the receiver. For example, when a customer sends a message to transfer money from one account to another, the bank must have proof that the customer actually requested this transaction. Entity Authentication In entity authentication (or user identification) the entity or user is verified prior to access to the system resources(files( For example, a student who needs to access her university resources needs to be authenticated during the logging process. This is to protect the interests of the university and the student. Problem Consider an automated teller machine (ATM) in which users provide a personal identification number (PIN) and a card for account access. Give examples of confidentiality, integrity, and availability requirements associated with the system and, in each case, indicate the degree of importance of the requirement. Solution Confidentiality requirements: the communication channel between the ATM and the bank must be encrypted the PIN must be encrypted (wherever it is stored) Integrity requirements: the actions performed via the ATM must be associated to the account associated with the card Availability requirements: the system must be able to serve at least X concurrent users at any given time the system must be available 99.9% of the time Assignment#1 Choose one of internet protocol (TCP/IP , UDP ,..) Then give an example of integrity , availability and confidentiality