* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download 70-473: Cloud Data Platform
Serializability wikipedia , lookup
Tandem Computers wikipedia , lookup
Entity–attribute–value model wikipedia , lookup
Extensible Storage Engine wikipedia , lookup
Oracle Database wikipedia , lookup
Ingres (database) wikipedia , lookup
Team Foundation Server wikipedia , lookup
Microsoft Access wikipedia , lookup
Concurrency control wikipedia , lookup
Relational model wikipedia , lookup
Database model wikipedia , lookup
Microsoft Jet Database Engine wikipedia , lookup
Open Database Connectivity wikipedia , lookup
Microsoft SQL Server wikipedia , lookup
http://www.ThatAwesomeTrainer.com
70-473 Designing and
Implementing Cloud Data Platform
Solutions
70-475 Designing and Implementing
Big Data Analytics Solutions
Design & implement DB solutions
Big data batch and interactive processing
Manage DBMS security
Big data real-time processing
Design for HA, DR and Scale
Implement Machine Learning
Monitor and Manage
implementations
Operationalize these end-to-end
• 50-60 questions
• ~2 - 3 hours to complete exam
• Can review questions
Exam TIP: Mark what you want to review!
• 3-4 case studies
• Cannot move between case studies
• Look for the Azure Exam Discounts
http://bit.ly/2jvvCf1
Exam TIP: Answer ALL questions!
http://bit.ly/2jcjeB2
https://mva.microsoft.com
https://www.microsoft.com/en-us/learning/exam-70-473.aspx
https://mva.microsoft.com
https://docs.microsoft.com/en-us/azure/sql-database/
Design and Implement
database for SQL Server and
SQL Database (20-25%)
Design for high availability,
disaster recovery, and
scalability (25–30%)
Manage Database
Management Systems
Security (25-30%)
Monitor and manage
database implementations
on Azure (25–30%)
for any reason at any time
from minutes to seconds
http://bit.ly/2j8kmJf
Technology
SQL Server
Version
Zero Data Loss
Scope
# Replicas
Automatic
Failover
Readable
Secondaries
Availability Groups
SQL Server 2012
Yes
(Sync Mode)
DB(s)
4
Yes
(w/ additional
cluster member)
Yes
Yes
(High Safety
Mode)
DB
Yes
(w/ Witness)
Limited
(database
snapshots)
SQL Server 2014
Database Mirroring
SQL Server 2008 R2
SQL Server 2012
9 (1+8)
1
https://azure.microsoft.com/en-us/documentation/articles/virtual-machines-windows-sql-high-availability-dr/
Walkthroughs
Resource Manager Manual - https://azure.microsoft.com/en-us/documentation/articles/virtual-machines-windowsportal-sql-alwayson-availability-groups-manual/
Service Manager Classic - https://azure.microsoft.com/en-us/documentation/articles/virtual-machines-windowsclassic-portal-sql-alwayson-availability-groups/
Classic PowerShell - https://azure.microsoft.com/en-us/documentation/articles/virtual-machines-windows-classicps-sql-alwayson-availability-groups/
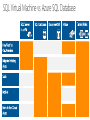
SQL Virtual Machine vs Azure SQL Database
SQL Virtual Machine vs Azure SQL Database
SQL Server in a VM
Best for…
Resources
TCO
benefits
Scalability
Azure SQL Database
https://azure.microsoft.com/en-us/pricing/details/sql-database
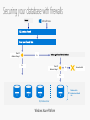
Securing your database with firewalls
Microsoft Azure
Client IP
Address in Range?
No
Yes
Client IP
Address in Range?
No
Connection Fails
Yes
Database with a
database-level firewall
rule
SQL Database Server
Windows Azure Platform
By default, Azure blocks all external connections to port 1433.
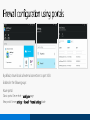
Enabled in the following ways:
Azure portal
Classic portal: Server level – configure page
New portal: Server settings – firewall – firewall settings blade
# PS Enable Azure connections
PS C:\> New-AzureSqlDatabaseServerFirewallRule `
-ServerName "Contoso" `
-AllowAllAzureServices `
-RuleName "myRule2"
-- PS Allow external IP access to SQL Database
PS C:\> New-AzureSqlDatabaseServerFirewallRule `
-ServerName "Contoso" `
-RuleName "myRule1" `
-StartIpAddress 12.1.1.1 `
-EndIpAddress 12.1.1.2
-- T-SQL Enable Azure connections
sp_set_firewall_rule N'Allow Windows Azure',
'0.0.0.0','0.0.0.0'
-- T-SQL Allow external IP access to SQL Database
sp_set_firewall_rule N'myRule1',
'12.1.1.1','12.1.1.2'
Manage SQL Database
firewall rules using code.
Windows PowerShell Azure
cmdlets
New-AzureSqlDatabaseServerFirewallRule
Get-AzureSqlDatabaseServerFirewallRule
Set-AzureSqlDatabaseServerFirewallRule
Transact SQL
sp_set_firewall_rule
sp_set_database_firewall_rule
sp_delete_firewall_rule
sp_delete_database_firewall_rule
POST
https://management.core.windows.net:8443/{subscriptionId}/ser
vices/sqlservers/servers/Contoso/firewallrules
REQUEST BODY
<ServiceResource
xmlns="http://schemas.microsoft.com/windowsazure">
<Name>myRule1</Name>
<StartIPAddress> 12.1.1.1 </StartIPAddress>
<EndIPAddress> 12.1.1.1 </EndIPAddress>
</ServiceResource>
DELETE
https://management.core.windows.net:8443/{subscriptionId}/ser
vices/sqlservers/servers/Contoso/firewallrules/myRule1
GET
https://management.core.windows.net:8443/{subscriptionId}/ser
vices/sqlservers/servers/Contoso/firewallrules
Managing firewall rules through
REST API must be authenticated. For
information, see Authenticating
Service Management Requests.
Server-level rules can be created,
updated, or deleted using REST API
To create or update a server-level
firewall rule, execute the POST
method
To remove an existing server-level
firewall rule, execute the DELETE
method
To list firewall rules, execute the GET
Point of Difference
On-premises/Azure VM SQL Server
Microsoft Azure SQL Database
Where you manage serverlevel security
The Security folder in SQL Server
Management Studio's Object Explorer
The master database
Server-level security role
for creating logins
securityadmin fixed server role
loginmanager database role in the master database
(recommended to use contained dbs instead)
CREATE LOGIN
ALTER LOGIN
DROP LOGIN
CREATE LOGIN
ALTER LOGIN
DROP LOGIN
(parameter limitations and must be connected to master db)
View that shows all logins
sys.syslogins (sys.sql_logins for
SQL Server authentication logins)
sys.sql_logins
(You must be connected to the master database)
Server-level role for
creating databases
dbcreator fixed database role
dbmanager database role in the master database
Commands for managing
logins
https://azure.microsoft.com/en-us/documentation/articles/sql-database-manage-logins/
Azure Key Vault
https://azure.microsoft.com/en-us/documentation/articles/sql-database-always-encrypted-azure-key-vault/
Windows certificate store
https://azure.microsoft.com/en-us/documentation/articles/sql-database-always-encrypted/
https://msdn.microsoft.com/library/mt459280.aspx
https://azure.microsoft.com/en-us/documentation/articles/sql-database-dynamic-data-masking-get-started/
Point-in-time restore
Automatic backup
Full backups weekly, differential backup daily,
log backups every 5 minutes
Daily and weekly backups automatically
uploaded to geo-redundant Azure Storage
SQL Database
backups
sabcp01bl21
Azure Storage
Geo- replicated
Self-service restore
Point-in-time up to a second granularity
REST API, PowerShell, or Portal
Creates a new database in the same logical server
Tiered retention policy
Basic - 7 days
Standard - 14 days
Premium - 35 days
No additional cost to retain backups
Restore from backup
sabcp01bl21
Geo-restore
Self-service restore API
Restores last daily backup
No extra cost, no capacity
guarantee
SQL Database
backups
sabcp01bl21
Azure Storage
Geo- replicated
sabcp01bl21
RTO>=24h, RPO=24h
Database URL will change after
restore
Restore to any
Azure region
Standard geo-replication
North Central US
RTO<2h, RPO<30m
REST and PowerShell API to
opt-in and failover
Automatic data replication
and synchronization
DMV + REST to monitor and
guide failover decisions
Single offline secondary with
matching performance level
in the disaster recovery paired
region
LS OPQ
Failover and
activation of
secondary
(during
incident)
LS ABC
LS XYZ
West US
East US
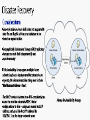
Active geo-replication
RTO<1h, RPO<5m
T-SQL, REST, and PowerShell API to opt-in
and failover
Geo- replicated
DMV+REST to monitor and guide failover
decisions
Automatic data replication and
synchronization
Up to 4 online secondary databases with
matching performance level in any region
Coming soon:
T-SQL support
Switch between primary and secondary
https://docs.microsoft.com/en-us/azure/sql-database/sql-database-geo-replication-overview
Restore deleted database
Recovery after accidental database deletion
Restores the database to the point of deletion
(earlier backups are deleted)
Backups retained for 7/14/35 days
Now
Time
-7 days
Creates a new database on the server used by
the original database
You can choose to failover to the restored
database or use scripts to recover data
Self-service
restore to point
of deletion
Long-term data retention
Introducing Basic and Premium
Elastic Database Pools
Basic Elastic Database Pool
100-1200 eDTUs per pool
Premium Elastic Database Pool
125-1500 eDTU per pool
new
Standard Elastic Database Pool
100-1200 eDTUs per pool
new
Auto-scale up to 5 eDTUs per DB
Auto-scale up to 100 eDTUs per DB
Auto-scale up to 1000 eDTUs per DB
Basic
Standard
Premium
https://msdn.microsoft.com/en-US/library/mt589530.aspx
https://azure.microsoft.com/en-us/documentation/articles/sql-database-service-tier-advisor/
https://azure.microsoft.com/en-gb/documentation/articles/sql-database-performance-guidance/#monitoringresource-use-with-sysresourcestats
https://azure.microsoft.com/en-gb/documentation/articles/sql-database-query-performance/
https://azure.microsoft.com/en-gb/documentation/articles/sql-database-advisor/
https://azure.microsoft.com/en-gb/documentation/articles/sql-database-auditing-get-started/
server
database
database
https://azure.microsoft.com/en-gb/documentation/articles/sql-database-xevent-db-diff-from-svr/
https://azure.microsoft.com/en-gb/documentation/articles/sql-database-elastic-pool-manage-portal/
http://techcommunity.microsoft.com






















































![[Full Version] Lead2pass Latest Microsoft 70](http://s1.studyres.com/store/data/000506143_1-f39b1c7b66032d3919d6b0d8b8776e0e-150x150.png)