* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Network Topologies - CDNIS Community Sites
Deep packet inspection wikipedia , lookup
Distributed firewall wikipedia , lookup
IEEE 802.1aq wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Computer network wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Network tap wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
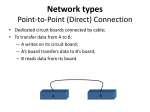
NETWORK TOPOLOGIES This document is maintained by Dr. Benedict Hung. Comments should be sent to [email protected]. Adapted from various publications and online resources. Please refer to the REFERENCES section for details. 1 INTRODUCTION Network topology refers to layout of a network and the arrangement of the nodes in the network. The topological arrangement can either be physical (i.e. the physical layout of the devices on a network) or logical (i.e. the way the signals act on a network and the way the data is transmitted). 1.1 POINT-TO-POINT LINK In a point-to-point link, two devices monopolize a single communication medium. Since the communication medium is not shared, the devices are not addressed. Point-to-point links can be simplex, half-duplex, or full-duplex. When devices are engaged in a bi-directional communication on a half- 1 duplex point-to-point link, there is a mechanism to switch the roles of the devices between being a sender and a receiver. 1.1.1 Simplex Communication There are two stations in the network. The signals in the network flow in one direction from one sender to one receiver. The sender and the receiver operate on the same frequency. Examples of simplex communication include radio broadcasting, television broadcasting, computer to printer communication, and keyboard to computer connections. 1.1.2 Half-Duplex Communication The two stations can both transmit and receive data on the network but not simultaneously. For example, one workstation on the network can send data on the line and then immediately receive data on the line from the same direction in which data was just transmitted. A walkie-talkie is a half-duplex device, because only one party can talk at a time. 1.1.3 2 Full-Duplex Communication The two stations can transmit and receive data simultaneously. The link capacity is shared between the two devices or by two separate transmission paths. An example of a full-duplex communication is a telephone where the two parties at both ends of a call can speak and be heard by the other party simultaneously. Full-duplex has no collisions so time is not wasted by having a retransmit frames or by waiting for an acknowledgement from the receiver. 1.2 MULTI-POINT LINK There are three or more devices connected through a single communication medium. For sharing a common channel, each device needs a way to identify itself and the device to which it wants to send the information. The method used to identify the senders and the receivers is called addressing. 2 NETWORK ADDRESS A network address is an identifier for a node or network interface within a network. All network addressed are theoretically designed to be unique across the network. However, it is possible for more than one type of network address to be used in a single network. One of the best known form of network addressing is the Internet Protocol (IP) address. IP addresses consist of four bytes (32 bits) that uniquely identify all computers on the public internet. Another popular form of address is the Media Access Control (MAC) address. MAC addresses are six bytes (48 bits)that manufacturers of network adapters burn into the products to uniquely identify them. 3 2.1 PUBLIC VS. PRIVATE ADDRESSING An IP address is a unique numerical value that is used to identify a computer on a network. There are two kinds of IP addresses, public (also called globally unique IP addresses) and private. 2.1.1 Public IP Addresses Public IP addresses are assigned by the Internet Assigned Numbers Authority (IANA). The addresses are guaranteed to be globally unique and reachable on the Internet. IANA assures that multiple computers do not have the same IP address. An Internet service provider (ISP) obtains a range of public IP addresses from IANA, and then the ISP assigns the addresses to customers to use when they connect to the Internet through the ISP. Public IP addresses are routable on the Internet, which means that a computer with a public IP address is visible to other computers on the Internet. 2.1.2 4 Private IP Address Private IP addresses cannot be used on the Internet. IANA has set aside three blocks of IP addresses that cannot be used on the global Internet. These three blocks of addresses are private IP addresses, and they are used for networks that do not directly connect to the Internet. A private IP address is within one of the following blocks or range of addresses: 192.168.0.0/16: This block allows valid IP addresses within the range 192.168.0.1 to 192.168.255.254. 172.16.0.0/12: This block allows valid IP addresses within the range 172.16.0.1 to 172.31.255.254. 10.0.0.0/8: This block allows valid IP addresses within the range 10.0.0.1 to 10.255.255.254. Most small businesses and private networks prefer to use private IP addresses for the local network, because ISPs generally charge a fee for each public IP address. As a result, using public IP addresses on a local network is costly. Hence, rather than purchasing a globally unique IP address for each client computer on a local network, the network administrator can purchase one globally unique IP address and use it for the router interface that connects to the ISP. 2.2 IPV4 VS. IPV6 ADDRESSES The version of the IP that is commonly used is version 4 (IPv4), which has not changed substantially since RFC 791 was published in 1981. IPv4 is robust, easily implemented, interoperable, and capable of scaling to a global utility that can function with the Internet. The Internet continues to grow exponentially, and the adoption of broadband technologies, such as cable modems, mobile information appliances, such as personal data assistants or PDAs, and cellular phones, means that many more addresses are needed. IPv6 significantly increases the number of addresses that are available. The most obvious difference between IPv6 and IPv4 is the size of the addresses. An IPv4 address is 32 bits long, and an IPv6 address is 128 bits long, which is four times longer than an IPv4 address. 2.3 DYNAMIC VS. STATIC IP ADDRESSES A local area network can have static and dynamic IP addresses. 2.3.1 Dynamic IP addresses Dynamic IP addresses are acquired from a DHCP server, and they may change from time to time. The DHCP server must be assigned a static IP address. 2.3.2 Static IP addresses A static IP address does not change. It is assigned by the network administrator, and it is manually entered into the properties for the network adapter that is on a server or on a client computer. A static IP address does not require that a DHCP server is running on the network. Certain types of servers must have a static IP address. These servers include DHCP servers, DNS servers, WINS servers, and any server that is providing access to users who are using the Internet. 5 2.4 NETMASK IP addresses are broken into 4 octets (IPv4) separated by dots called dotted decimal notation. An octet is a byte consisting of 8 bits. The IPv4 addresses are in the following form: 192.168.10.1 There are two parts of an IP address: Network ID Host ID The various classes of networks specify additional or fewer octets to designate the network ID versus the host ID. 6 CLASS 1ST OCTET A Net Id B C 2ND OCTET 3RD OCTET 4TH OCTET Host ID Net ID Host ID Net ID Host ID When a network is set up, a netmask is also specified. The netmask determines the class of the network. When the netmask is setup, it specifies some number of most significant bits with a 1's value and the rest have values of 0. The most significant part of the netmask with bits set to 1's specifies the network address, and the lower part of the address will specify the host address. 2.4.1 Class A-E networks The addressing scheme for class A through E networks is shown below. NETWORK TYPE ADDRESS RANGE NORMAL NETMASK CLASS A 001.x.x.x to 126.x.x.x 255.0.0.0 For very large networks CLASS B 128.1.x.x to 191.254.x.x 255.255.0.0 For medium size networks CLASS C 192.0.1.x to 223.255.254.x 255.255.255.0 For small networks CLASS D 224.x.x.x to 239.255.255.255 CLASS E 240.x.x.x to 247.255.255.255 COMMENTS Used to support multicasting There are some network addresses reserved for private use by the IANA which can be hidden behind a computer which uses IP masquerading to connect the private network to the internet. There are three sets of addresses reserved. 10.x.x.x 172.16.x.x - 172.31.x.x 192.168.x.x Other reserved or commonly used addresses: 127.0.0.1 - The loopback interface address. All 127.x.x.x addresses are used by the loopback interface which copies data from the transmit buffer to the receive buffer of the NIC when used. 0.0.0.0 - This is reserved for hosts that don't know their address and use BOOTP or DHCP protocols to determine their addresses. 255 - The value of 255 is never used as an address for any part of the IP address. It is reserved for broadcast addressing. Please remember, this is exclusive of CIDR. When using CIDR, all bits of the address can never be all ones. 7 8 3 LAN TRANSMISSIONS The application in use, such as multimedia, database updates, e-mail, or file and print sharing, generally determines the type of data transmission. LAN transmissions fit into one of three categories: unicast multicast broadcast 9 3.1 UNICAST With unicast transmissions, a single packet is sent from the source to a destination on a network. The source-node addresses the packet by using the network address of the destination node. The packet is then forwarded to the destination network and the network passes the packet to its final destination. Figure 1 Unicast Network server 10 client client client 3.2 MULTICAST With a multicast transmission, a single data packet is copied and forwarded to a specific subset of nodes on the network. The source node addresses the packet by using a multicast address. For example, the TCP/IP suite uses 224.0.0.0 to 239.255.255.255. The packet is then sent to the network, which makes copies of the packet and sends a copy to each segment with a node that is part of the multicast address. Figure 2 Multicast Network server client client client 11 3.3 BROADCAST Broadcasts are found in LAN environments. Broadcasts do not traverse a WAN unless the Layer 3 edge-routing device is configured with a helper address to direct these broadcasts to a specified network address. This Layer 3 routing device acts as an interface between the local-area network (LAN) and the wide-area network (WAN). Figure 3 Broadcast Network server 12 client client client 4 LAN TOPOLOGIES There are five basic LAN topologies: Star Ring Bus Tree Mesh 13 4.1 STAR TOPOLOGY All stations are attached by cable to a central point, usually a wiring hub or other device operating in a similar function. Figure 4 Star Topology node server node 14 node node Several different cable types can be used for this point-to-point link, such as shielded twisted-pair (STP), unshielded twisted-pair (UTP), and fiber-optic cabling. Wireless media can also be used for communications links. The advantage of the star topology is that no cable segment is a single point of failure impacting the entire network. This allows for better management of the LAN. If one of the cables develops a problem, only that LAN-attached station is affected; all other stations remain operational. The centralized networking equipment can reduce costs in the long run by making network management much easier. The disadvantage of a star topology is the central hub device. This central hub is a single point-of-failure in that if it fails, every attached station is out of service. 4.2 RING TOPOLOGY All stations in a ring topology are considered repeaters and are enclosed in a loop. Unlike the star topology, a ring topology has no end points. The repeater in this case is a function of the LAN-attached station’s network interface card (NIC).Since each NIC in a LAN-attached station is a repeater, each LAN station will repeat any signal that is on the network, regardless of whether it is destined for that particular station. Figure 5 Ring Topology node node node node The major advantage of the ring topology is that no single device monopolizes the network. Moreover, the network function continues in slower speed after the full capacity is exceeded. However, if a LAN-attached station fails to perform its repeater function, the entire network could come down. When a station fails to operate, it is often difficult to troubleshoot. Furthermore, it is necessary to disrupt the network when adding or removing devices. 15 4.3 BUS TOPOLOGY Bus topology is a simple design that utilizes a single length of cable, also known as the medium, with directly attached LAN stations. All stations share this cable segment. Every station on this segment sees transmissions from every other station on the cable segment; this is known as a broadcast medium. The LAN attachment stations are definite endpoints to the cable segment and are known as bus network termination points. Figure 6 Bus Topology server 16 node node node It is a very economical topological model and it is easy to extent the network by adding cables with a repeater that boosts the signal and allows it to travel a longer distance. Network management is straightforward and inexpensive. There is a risk of a single point of failure. If the cable is broken, no LAN station will have connectivity or the ability to transmit and receive. The network becomes slow by heavy network traffic with a lot of devices because networks do not coordinate with each other to reserve times to transmit. 4.4 TREE TOPOLOGY The tree topology is a logical extension of the bus topology and could be described as multiple interconnected bus networks. The physical (cable) plant is known as a branching tree with all stations attached to it. The tree begins at the root, the pinnacle point, and expands to the network endpoints. This topology allows a network to expand dynamically with only one active data path between any two network endpoints. Figure 7 Tree Topology server node server server node node node node Tree topology is an extension of star and bus topologies, so in the networks where these topologies cannot be implemented individually for reasons related scalability, tree topology is the best alternative. With the nature of this topology, expansion is possible and easy, furthermore, network management, error detection, and correct are relatively easy. The critical factor to ensure the operation of the network depends on a main bus cable. If the main bus cable breaks, the entire network is crippled. 17 4.5 MESH TOPOLOGY In a mesh topology, each of the network node, computer, and other devices, are interconnected with one another. Every node not only sends its own signals but also relays data from other nodes. A true mesh topology is the one where every node is connected to every other node in the network. This type of topology is very expensive as there are many redundant connections. Figure 8 Mesh Topology server node node 18 node node The first advantage for a mesh topology is where data can be transmitted from different devices simultaneously. This topology can withstand high traffic. Due to the number of redundant connections, if one of the components fails there is always an alternative. With the number of redundant connections, maintenance and troubleshooting problems on a mesh topology is difficult and expensive. 5 NETWORK DEVICES The four primary devices used in LANs are: Hubs Bridges Switches Routers 19 5.1 HUBS Hubs operate at the physical layer (Layer 1) of the Open Systems Interconnection (OSI) model. A hub is used to connect devices so that they are on one shared LAN. If two devices are directly connected with LAN cables, a hub is needed to interconnect two or more devices on a single LAN. The cable termination points are the hub and the LAN device (host). Ethernet hubs send all the data from a network device on one port to all other hub ports. When network devices are connected via a hub, LANattached devices will hear all conversations across the LAN. Each station then examines the message header to determine if it is the intended recipient. If more than one LAN station transmits at the same time, a collision occurs and both stations initiate a backoff algorithm before attempting retransmission. 5.2 BRIDGES 20 This section focuses on transparent bridges, which can also be referred to as learning or Ethernet bridges. Bridges have a physical layer (Layer 1), but are said to operate at the data link layer (Layer 2) of the OSI model. Bridges forward data frames based on the destination MAC address. Bridges also forward frames based on frame header information. Bridges create multiple collision domains and are generally deployed to provide more useable bandwidth. Bridges do not stop broadcast traffic, instead they forward broadcast traffic out every port of each bridge device. Each port on a bridge has a separate bandwidth (collision) domain, but all ports are on the same broadcast domain. 5.3 SWITCHES LAN switches are used to connect a common broadcast domain (a hub). They are also used to provide frame-level filtering as well as dedicated port speed to specific end users. Some switches have limited routing capabilities and can provide Layer 3 routing functions at the most basic level. Some of the major benefits of using switches in a network are higher bandwidth to the desktop and ease of configuration. Switches are being deployed more often to replace hubs and bridges as more bandwidth-intensive applications are being implemented at all levels of an organization. 5.4 ROUTERS Routers are not usually active in simple LAN environments because routers are (Wide-Area Network) WAN devices. Routers are typically found at the edge of a LAN, interfacing with a WAN. Routers operate at the network layer (Layer 3) of the OSI model. Broadcast containment and security are needed in more complex environments. 21 22 6 REFERENCES Basic Addressing http://comptechdoc.org/independent/networking/guide/netaddress ing.html Network Basics http://comptechdoc.org/independent/networking/guide/netaddress ing.html Data Communications & Networking Chan, R. W. N., ISBN: 962-7548-44-8 LAN Topoogies http://media.techtarget.com/searchNetworking/Downloads/NetCons ultantsch2.pdf 23