Chapter 1 of Database Design, Application Development and
... Copyright © 2007 by The McGraw-Hill Companies, Inc. All rights reserved. ...
... Copyright © 2007 by The McGraw-Hill Companies, Inc. All rights reserved. ...
NAV-17 Dynamics NAV 2016 on Azure SQL
... a non-readable secondary database stored in the DR (disaster recovery) paired region. ERT < 30 sec ; RPO < 5 sec ...
... a non-readable secondary database stored in the DR (disaster recovery) paired region. ERT < 30 sec ; RPO < 5 sec ...
Database Study Guide Part I
... be used for keeping track of video game or movie collections, friends’ contact information, recipes and inventories for businesses. Schools keep track of student information such as contact, grades, classes etc. Have you ever bought something from a store and they ask you for your phone number or zi ...
... be used for keeping track of video game or movie collections, friends’ contact information, recipes and inventories for businesses. Schools keep track of student information such as contact, grades, classes etc. Have you ever bought something from a store and they ask you for your phone number or zi ...
404 - Rice Lake Weighing Systems
... TEL: 715-234-9171 • FAX: 715-234-6967 • www.ricelake.com An ISO Registered Company © 2013 Rice Lake Weighing Systems PN 153229 2/13 Specifications subject to change without notice. ...
... TEL: 715-234-9171 • FAX: 715-234-6967 • www.ricelake.com An ISO Registered Company © 2013 Rice Lake Weighing Systems PN 153229 2/13 Specifications subject to change without notice. ...
syllabus[1]. - ElCoM
... Silberschatz, Korth and Sudarshan, “Database System Concepts”, 4th edition, Mc Graw Hill, 2002. Thomas Connolly et. al., “Database Systems, A Practical Approach to Design, Implementation and Management”, Addison Wesley, ...
... Silberschatz, Korth and Sudarshan, “Database System Concepts”, 4th edition, Mc Graw Hill, 2002. Thomas Connolly et. al., “Database Systems, A Practical Approach to Design, Implementation and Management”, Addison Wesley, ...
Some Items for online
... • Trigger Examine (and have available online recent releases, say P11) • Run Quality Recording – Bits on each event (Terry Wyatt) rather than sep database • Each subdetector has a switch they can set to good, bad, questionable during run; avoids HAVING to make run boundaries if something dicey (HV) ...
... • Trigger Examine (and have available online recent releases, say P11) • Run Quality Recording – Bits on each event (Terry Wyatt) rather than sep database • Each subdetector has a switch they can set to good, bad, questionable during run; avoids HAVING to make run boundaries if something dicey (HV) ...
Introduction to Database Systems
... Search/query/update Change the structure Concurrent access to many user Recover from crashes Security ...
... Search/query/update Change the structure Concurrent access to many user Recover from crashes Security ...
Chapter 1: Introduction
... accounts and the relationship between them) Analogous to type information of a variable in a program Physical schema: database design at the physical level Logical schema: database design at the logical level ...
... accounts and the relationship between them) Analogous to type information of a variable in a program Physical schema: database design at the physical level Logical schema: database design at the logical level ...
Lecture 10 - cda college
... • SQL code represents a transaction because database was accessed • Improper or incomplete transactions can have devastating effect on database integrity – Some DBMSs provide means by which user can define enforceable constraints – Other integrity rules are enforced automatically by the DBMS Databas ...
... • SQL code represents a transaction because database was accessed • Improper or incomplete transactions can have devastating effect on database integrity – Some DBMSs provide means by which user can define enforceable constraints – Other integrity rules are enforced automatically by the DBMS Databas ...
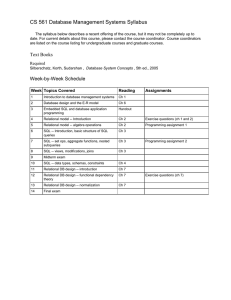
CS 561 Database Management Systems Syllabus
... CS 561 Database Management Systems Syllabus The syllabus below describes a recent offering of the course, but it may not be completely up to date. For current details about this course, please contact the course coordinator. Course coordinators are listed on the course listing for undergraduate cour ...
... CS 561 Database Management Systems Syllabus The syllabus below describes a recent offering of the course, but it may not be completely up to date. For current details about this course, please contact the course coordinator. Course coordinators are listed on the course listing for undergraduate cour ...
Publisher - Mat/Sta/CMP Department
... placed on the planning, administration, control and design of database systems. Students will develop applications using a popular DBMS software package. (4.5 lecture hours) Laboratory fee applies. COMPUTER CENTER REQUIREMENT Students should avail themselves of further study and/or educational assis ...
... placed on the planning, administration, control and design of database systems. Students will develop applications using a popular DBMS software package. (4.5 lecture hours) Laboratory fee applies. COMPUTER CENTER REQUIREMENT Students should avail themselves of further study and/or educational assis ...
02010_PPT_ch10
... • Not all transactions update database • SQL code represents a transaction because database was accessed • Improper or incomplete transactions can have devastating effect on database integrity – Some DBMSs provide means by which user can define enforceable constraints – Other integrity rules are enf ...
... • Not all transactions update database • SQL code represents a transaction because database was accessed • Improper or incomplete transactions can have devastating effect on database integrity – Some DBMSs provide means by which user can define enforceable constraints – Other integrity rules are enf ...
Thomas L. Brown ...
... Utilize a database modeling technique for a single entity class, a one-toone (1:1) relationship between entity classes, a one-to-many (1:M) relationship between entity classes, a many-to-many (M:M) relationship between entity classes, and recursive relationships; Define, develop and process single e ...
... Utilize a database modeling technique for a single entity class, a one-toone (1:1) relationship between entity classes, a one-to-many (1:M) relationship between entity classes, a many-to-many (M:M) relationship between entity classes, and recursive relationships; Define, develop and process single e ...
FUNDAMENTALS OF COMPUTER CONCEPTS (CPS 100)
... Evaluate the performance of a microcomputer based on the processor, memory, storage and other peripheral devices. Demonstrate an understating of the concepts in data communication in that they will be able to list and describe the function of communications hardware and software. Identify hardware a ...
... Evaluate the performance of a microcomputer based on the processor, memory, storage and other peripheral devices. Demonstrate an understating of the concepts in data communication in that they will be able to list and describe the function of communications hardware and software. Identify hardware a ...
Introduction to Database Systems
... Functionality of a DBMS The programmer sees SQL, which has two components: • Data Definition Language - DDL • Data Manipulation Language - DML – query language ...
... Functionality of a DBMS The programmer sees SQL, which has two components: • Data Definition Language - DDL • Data Manipulation Language - DML – query language ...
Advantages and Disadvantages of Database Systems
... crossed departmental boundaries. This feature provides more functionality and better services to the users. 11. Increased productivity The database approach provides all the low-level file-handling routines. The provision of these functions allows the programmer to concentrate more on the specific f ...
... crossed departmental boundaries. This feature provides more functionality and better services to the users. 11. Increased productivity The database approach provides all the low-level file-handling routines. The provision of these functions allows the programmer to concentrate more on the specific f ...
Colorado Plateau Cooperative Ecosystem Studies Unit
... The Wildlife database applications must be integrated within the GRCA Resource Information System (RIS) as currently developed, in particular the existing Vegetation database module, and as envisioned in the GRCA Database Management System Requirements Analysis document. Access to the database appl ...
... The Wildlife database applications must be integrated within the GRCA Resource Information System (RIS) as currently developed, in particular the existing Vegetation database module, and as envisioned in the GRCA Database Management System Requirements Analysis document. Access to the database appl ...
Acquire Pooled Data for Summaries of Clinical Safety
... analysis plans, database specifications) 2. Review analysis plans for clinical summary 3. Review database quality reports for individual studies 4. Assess study differences or constraints that could impact summary analyses, such as: a. Different target pops, inclusion/exclusion criteria, etc. b. Dif ...
... analysis plans, database specifications) 2. Review analysis plans for clinical summary 3. Review database quality reports for individual studies 4. Assess study differences or constraints that could impact summary analyses, such as: a. Different target pops, inclusion/exclusion criteria, etc. b. Dif ...
Software Engineering Syllabus
... What if the system fails? What if more than one user is concurrently updating the same data? A transaction is a collection of operations that performs a single logical function in a database application Transaction-management component ensures that the database remains in a consistent (correct) stat ...
... What if the system fails? What if more than one user is concurrently updating the same data? A transaction is a collection of operations that performs a single logical function in a database application Transaction-management component ensures that the database remains in a consistent (correct) stat ...
download
... – Process of constructing a model of information used in an enterprise based on a specific data model (e.g. relational), but independent of a particular DBMS and other physical considerations. ...
... – Process of constructing a model of information used in an enterprise based on a specific data model (e.g. relational), but independent of a particular DBMS and other physical considerations. ...




![syllabus[1]. - ElCoM](http://s1.studyres.com/store/data/003440566_1-d3723e4a6aeb1784970cf983e6eb9d59-300x300.png)