Physics 411: Introduction to Quantum Mechanics
... Physics 411 is the first semester of a two semester sequence (with 412) and is mandatory for all physics majors pursuing the Academic Physics Concentration. 411 will deal with the foundations of quantum mechanics and the development of formalism and techniques. The topics of Physics 411 will roughly ...
... Physics 411 is the first semester of a two semester sequence (with 412) and is mandatory for all physics majors pursuing the Academic Physics Concentration. 411 will deal with the foundations of quantum mechanics and the development of formalism and techniques. The topics of Physics 411 will roughly ...
Quantum Computing
... whether you can get a practical speedup this way over the best classical algorithms. We might just have to build QCs and test it! ...
... whether you can get a practical speedup this way over the best classical algorithms. We might just have to build QCs and test it! ...
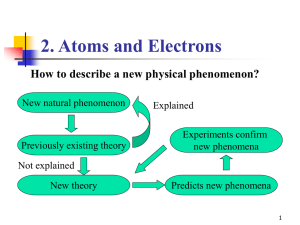
4.8-Quantum Mechanics
... Dirac’s Theory Dirac’s theory removed the paradox of particle-wave duality: It showed that if a particle was probed in a way that was meant to demonstrate its particle like properties - it would appear to be a particle…... …….if it was probed in a way that was meant to demonstrate its wave like pro ...
... Dirac’s Theory Dirac’s theory removed the paradox of particle-wave duality: It showed that if a particle was probed in a way that was meant to demonstrate its particle like properties - it would appear to be a particle…... …….if it was probed in a way that was meant to demonstrate its wave like pro ...
The quantum mechanics of photon addition and subtraction
... the other mode, without having to measure it. As shown in Figure 1(b), an initial field input to one mode will gain one extra photon heralded by a photon detected in the conjugate mode. By adding only one photon, any input state is converted into a nonclassical state that cannot be described by clas ...
... the other mode, without having to measure it. As shown in Figure 1(b), an initial field input to one mode will gain one extra photon heralded by a photon detected in the conjugate mode. By adding only one photon, any input state is converted into a nonclassical state that cannot be described by clas ...
Quantum Computing
... • However, transmissions easily interrupted – Denial of service – However, eavesdroppers are easily detected – Can intercept and retransmit, but it will be know ...
... • However, transmissions easily interrupted – Denial of service – However, eavesdroppers are easily detected – Can intercept and retransmit, but it will be know ...
SYLLABUS FOR PHY 662 Quantum Mechanics II
... SYLLABUS FOR PHY 662 Quantum Mechanics II We will continue the study of QM by applying the formalism to real world situations. This will involve using various approximations. The best way to acquire the necessary skills is to do problems so there will be many HW problems. HWs are due the Tuesday aft ...
... SYLLABUS FOR PHY 662 Quantum Mechanics II We will continue the study of QM by applying the formalism to real world situations. This will involve using various approximations. The best way to acquire the necessary skills is to do problems so there will be many HW problems. HWs are due the Tuesday aft ...
Physics PHYS 356 Spring Semester 2013 Quantum Mechanics (4 credit hours)
... In this class I would like for you to develop a “quantum worldview” – by which I mean that I would like to re-examine some of the concepts that you have previously, in classes like classical mechanics and electricity and magnetism, held as starting assumptions. In doing this, you will need to learn ...
... In this class I would like for you to develop a “quantum worldview” – by which I mean that I would like to re-examine some of the concepts that you have previously, in classes like classical mechanics and electricity and magnetism, held as starting assumptions. In doing this, you will need to learn ...
The Learnability of Quantum States
... over two-outcome measurements. Suppose we draw Result says nothing about the m measurements E1,…,Em independently from D, and computational complexity of preparing then output a “hypothesis state” such that a hypothesis state that agrees with |Tr(Ei)-Tr(Ei)|≤ for all i. Then provided /10 an ...
... over two-outcome measurements. Suppose we draw Result says nothing about the m measurements E1,…,Em independently from D, and computational complexity of preparing then output a “hypothesis state” such that a hypothesis state that agrees with |Tr(Ei)-Tr(Ei)|≤ for all i. Then provided /10 an ...
Non-linear gates enabling universal quantum computation
... In the above described endeavour, non-linear quantum systems are crucial. Given that, as said above, experimental research has recently seen impressive developments in terms of scalability, accessing to non-linearities would be the next big step. The reason is that non-linearities are necessary for ...
... In the above described endeavour, non-linear quantum systems are crucial. Given that, as said above, experimental research has recently seen impressive developments in terms of scalability, accessing to non-linearities would be the next big step. The reason is that non-linearities are necessary for ...
Quantum Physics 2005 Notes-6 Solving the Time Independent Schrodinger Equation
... A specific example #For a finite square well of width L, we expect the energies to be h2$ 2 of order: E0 = and useful lengths to be of order L. ...
... A specific example #For a finite square well of width L, we expect the energies to be h2$ 2 of order: E0 = and useful lengths to be of order L. ...
Quantum key distribution
Quantum key distribution (QKD) uses quantum mechanics to guarantee secure communication. It enables two parties to produce a shared random secret key known only to them, which can then be used to encrypt and decrypt messages. It is often incorrectly called quantum cryptography, as it is the most well known example of the group of quantum cryptographic tasks.An important and unique property of quantum key distribution is the ability of the two communicating users to detect the presence of any third party trying to gain knowledge of the key. This results from a fundamental aspect of quantum mechanics: the process of measuring a quantum system in general disturbs the system. A third party trying to eavesdrop on the key must in some way measure it, thus introducing detectable anomalies. By using quantum superpositions or quantum entanglement and transmitting information in quantum states, a communication system can be implemented which detects eavesdropping. If the level of eavesdropping is below a certain threshold, a key can be produced that is guaranteed to be secure (i.e. the eavesdropper has no information about it), otherwise no secure key is possible and communication is aborted.The security of encryption that uses quantum key distribution relies on the foundations of quantum mechanics, in contrast to traditional public key cryptography which relies on the computational difficulty of certain mathematical functions, and cannot provide any indication of eavesdropping at any point in the communication process, or any mathematical proof as to the actual complexity of reversing the one-way functions used. QKD has provable security based on information theory, and forward secrecy.Quantum key distribution is only used to produce and distribute a key, not to transmit any message data. This key can then be used with any chosen encryption algorithm to encrypt (and decrypt) a message, which can then be transmitted over a standard communication channel. The algorithm most commonly associated with QKD is the one-time pad, as it is provably secure when used with a secret, random key. In real world situations, it is often also used with encryption using symmetric key algorithms like the Advanced Encryption Standard algorithm. In the case of QKD this comparison is based on the assumption of perfect single-photon sources and detectors, that cannot be easily implemented.