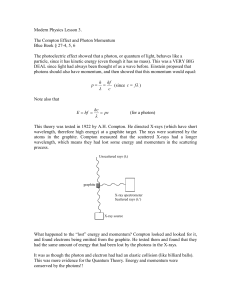
Adiabatic quantum computation and Boltzmann sampling with a
... R&D Center, Toshiba Corporation Adiabatic quantum computation and Boltzmann sampling with a network of driven nonlinear oscillators Last year, we proposed adiabatic quantum computation with a network of parametrically driven Kerr-nonlinear oscillators (KPO for short), where no dissipation was assume ...
... R&D Center, Toshiba Corporation Adiabatic quantum computation and Boltzmann sampling with a network of driven nonlinear oscillators Last year, we proposed adiabatic quantum computation with a network of parametrically driven Kerr-nonlinear oscillators (KPO for short), where no dissipation was assume ...
Quantum Computation
... But the result of QFT is stored as amplitudes, it can not be read. But QC can find periodicity. 1994-Peter Shor – can be used to factorize large numbers. Is RSA encryption in danger? ...
... But the result of QFT is stored as amplitudes, it can not be read. But QC can find periodicity. 1994-Peter Shor – can be used to factorize large numbers. Is RSA encryption in danger? ...
Lecture 20: Bell inequalities and nonlocality
... results are completely determined by her reduced state TrB |ψi hψ| and are independent of any operation that Bob could perform on his half of the state. The situation is similar for Bob. However, if both Alice and Bob perform measurements, then there can be interesting correlations between their mea ...
... results are completely determined by her reduced state TrB |ψi hψ| and are independent of any operation that Bob could perform on his half of the state. The situation is similar for Bob. However, if both Alice and Bob perform measurements, then there can be interesting correlations between their mea ...
The Future of Computer Science
... Theorem: Suppose U implements (say) a computationallyuniversal, reversible cellular automaton. Then after t=exp(n) iterations, C(|t) is superpolynomial in n, unless something very unlikely happens with complexity classes (PSPACEPP/poly) Proof Sketch: I proved in 2004 that PP=PostBQP Suppose C(| ...
... Theorem: Suppose U implements (say) a computationallyuniversal, reversible cellular automaton. Then after t=exp(n) iterations, C(|t) is superpolynomial in n, unless something very unlikely happens with complexity classes (PSPACEPP/poly) Proof Sketch: I proved in 2004 that PP=PostBQP Suppose C(| ...
Science
... In the wonderful world of quantum mechanics, electrons can, for example, have a left and a right spin at the same time. The possible combinations are unlimited, for example some right spin and a lot of left spin, or vice versa. Theoretically, this means that certain types of calculations can be perf ...
... In the wonderful world of quantum mechanics, electrons can, for example, have a left and a right spin at the same time. The possible combinations are unlimited, for example some right spin and a lot of left spin, or vice versa. Theoretically, this means that certain types of calculations can be perf ...
Quantum Mechanical Energy and You!
... Classically we have the fundamental quantites x and t which govern the dynamics of the system. For waves, x loses some of its meaning, so instead we talk of things such as the wave number, frequency, wavelength, etc… ...
... Classically we have the fundamental quantites x and t which govern the dynamics of the system. For waves, x loses some of its meaning, so instead we talk of things such as the wave number, frequency, wavelength, etc… ...
Noncommutative Quantum Mechanics
... Obtain a phase-space formulation of a noncommutative extension of QM in arbitrary number of dimensions; Show that physical previsions are independent of the chosen SW map. ...
... Obtain a phase-space formulation of a noncommutative extension of QM in arbitrary number of dimensions; Show that physical previsions are independent of the chosen SW map. ...
Abstract Submitted for the MAR12 Meeting of The
... Coupling quantum microwave circuits to quantum optics via cavity electro-optic modulators1 MANKEI TSANG, National University of Singapore — Experimental circuit quantum electrodynamics has made great strides in recent years, but it remains an open question how the quantum information stored in the m ...
... Coupling quantum microwave circuits to quantum optics via cavity electro-optic modulators1 MANKEI TSANG, National University of Singapore — Experimental circuit quantum electrodynamics has made great strides in recent years, but it remains an open question how the quantum information stored in the m ...
Introduction to Quantum Mechanics Course Instructor: Prof
... Adhering to high standards of academic integrity is an important part of your undergraduate experience. The standards are obvious when it comes to exams. Collaboration, such as working with others to conceptualize a problem, define approaches to the solution, or debug code, is often a gray area, and ...
... Adhering to high standards of academic integrity is an important part of your undergraduate experience. The standards are obvious when it comes to exams. Collaboration, such as working with others to conceptualize a problem, define approaches to the solution, or debug code, is often a gray area, and ...
Physics 212: Statistical mechanics II, Spring 2014 Course
... The first one-third to one-half of the course will cover strong and weak nonequilibrium statistical physics. The second part will cover the modern theory of scaling in equilibrium statistical physics (the “renormalization group”), applied to understand continuous phase transitions. At the end of the ...
... The first one-third to one-half of the course will cover strong and weak nonequilibrium statistical physics. The second part will cover the modern theory of scaling in equilibrium statistical physics (the “renormalization group”), applied to understand continuous phase transitions. At the end of the ...
Quantum key distribution
Quantum key distribution (QKD) uses quantum mechanics to guarantee secure communication. It enables two parties to produce a shared random secret key known only to them, which can then be used to encrypt and decrypt messages. It is often incorrectly called quantum cryptography, as it is the most well known example of the group of quantum cryptographic tasks.An important and unique property of quantum key distribution is the ability of the two communicating users to detect the presence of any third party trying to gain knowledge of the key. This results from a fundamental aspect of quantum mechanics: the process of measuring a quantum system in general disturbs the system. A third party trying to eavesdrop on the key must in some way measure it, thus introducing detectable anomalies. By using quantum superpositions or quantum entanglement and transmitting information in quantum states, a communication system can be implemented which detects eavesdropping. If the level of eavesdropping is below a certain threshold, a key can be produced that is guaranteed to be secure (i.e. the eavesdropper has no information about it), otherwise no secure key is possible and communication is aborted.The security of encryption that uses quantum key distribution relies on the foundations of quantum mechanics, in contrast to traditional public key cryptography which relies on the computational difficulty of certain mathematical functions, and cannot provide any indication of eavesdropping at any point in the communication process, or any mathematical proof as to the actual complexity of reversing the one-way functions used. QKD has provable security based on information theory, and forward secrecy.Quantum key distribution is only used to produce and distribute a key, not to transmit any message data. This key can then be used with any chosen encryption algorithm to encrypt (and decrypt) a message, which can then be transmitted over a standard communication channel. The algorithm most commonly associated with QKD is the one-time pad, as it is provably secure when used with a secret, random key. In real world situations, it is often also used with encryption using symmetric key algorithms like the Advanced Encryption Standard algorithm. In the case of QKD this comparison is based on the assumption of perfect single-photon sources and detectors, that cannot be easily implemented.