REF Chapter 3: Windows NT System Specifics
... have been designed to be valid for each of those systems. However, there are some aspects of BASIS commands and file naming conventions that differ among the various systems. To avoid unnecessary repetition in the documentation, information specific to each system has been gathered in separate chapt ...
... have been designed to be valid for each of those systems. However, there are some aspects of BASIS commands and file naming conventions that differ among the various systems. To avoid unnecessary repetition in the documentation, information specific to each system has been gathered in separate chapt ...
Installing and Upgrading Windows
... – Provides list of devices and software known to have issues with XP – Can be run by itself • From Microsoft’s Web site • Or winnt32 /checkupgradeonly ...
... – Provides list of devices and software known to have issues with XP – Can be run by itself • From Microsoft’s Web site • Or winnt32 /checkupgradeonly ...
Windows
... – Interrupts can be serviced on any processor – Any processor can cause another processor to reschedule what ...
... – Interrupts can be serviced on any processor – Any processor can cause another processor to reschedule what ...
Presentation Title Size 30PT
... This chapter labs might take more than one class period to complete. When installing an operating system, ensure that the computer is disconnected from the Internet. Students should install the Windows XP operating system, install service pack 2, connect to the Internet, and then check for updat ...
... This chapter labs might take more than one class period to complete. When installing an operating system, ensure that the computer is disconnected from the Internet. Students should install the Windows XP operating system, install service pack 2, connect to the Internet, and then check for updat ...
Section 3A: Windows forensics
... -The New Technology File System is more versatile because it uses the MFT to track information such as security items, the first 750 bytes of data, long and short filenames, and a list of nonresident attributes. -File slack, RAM slack, and drive slack are all areas in which valuable information may ...
... -The New Technology File System is more versatile because it uses the MFT to track information such as security items, the first 750 bytes of data, long and short filenames, and a list of nonresident attributes. -File slack, RAM slack, and drive slack are all areas in which valuable information may ...
Processes in Unix, Linux, and Windows
... • a set of processor registers – general purpose and status • a set of system resources – files, network connections, pipes, … – privileges, (human) user association, … ...
... • a set of processor registers – general purpose and status • a set of system resources – files, network connections, pipes, … – privileges, (human) user association, … ...
Windows 95/98/NT (Introduction)
... provides for the additional information for the hardware. The actual system interface to the hardware (or some software parts) is through a virtual device driver (VxD), which is a 32-bit, protected-mode driver. These keep track of the state of the device for each application and ensure that the devi ...
... provides for the additional information for the hardware. The actual system interface to the hardware (or some software parts) is through a virtual device driver (VxD), which is a 32-bit, protected-mode driver. These keep track of the state of the device for each application and ensure that the devi ...
9781111543709 _PPT_ch04
... Configuring Privacy Preferences in Internet Explorer • Use privacy features to set up a secure environment • Two types of cookies are saved on your computer: – Session cookies: deleted when the browser is closed – Persistent cookies: deleted at expiration date ...
... Configuring Privacy Preferences in Internet Explorer • Use privacy features to set up a secure environment • Two types of cookies are saved on your computer: – Session cookies: deleted when the browser is closed – Persistent cookies: deleted at expiration date ...
Understanding Computers, Chapter 5
... • File compression programs: Reduce the size of files so they take up less storage space on a storage medium or can be transmitted faster over the Internet – Both zip and unzip files – WinZip (Windows users) and Stuffit (Mac users) Chapter 5 ...
... • File compression programs: Reduce the size of files so they take up less storage space on a storage medium or can be transmitted faster over the Internet – Both zip and unzip files – WinZip (Windows users) and Stuffit (Mac users) Chapter 5 ...
WOSI-CRK-Description
... Here we introduce key operating system concepts found in Windows XP/Windows Server 2003, such as the Windows API, processes, threads, virtual memory, kernel mode and user mode, objects, handles, and security. The Windows (formerly known as Win32) application programming interface (API) is the primar ...
... Here we introduce key operating system concepts found in Windows XP/Windows Server 2003, such as the Windows API, processes, threads, virtual memory, kernel mode and user mode, objects, handles, and security. The Windows (formerly known as Win32) application programming interface (API) is the primar ...
Evolution of the Windows Kernel Architecture
... System cache, paged pool, pageable system code ...
... System cache, paged pool, pageable system code ...
Chapter 8
... Only contain the boot files Cannot start up Windows completely unless the system files are located on the hard disk Use when boot files are damaged on the hard drive Start with this disk to bypass the hard disk boot files Format floppy disk in Windows Copy to the floppy: NTLDR, NTDETECT. ...
... Only contain the boot files Cannot start up Windows completely unless the system files are located on the hard disk Use when boot files are damaged on the hard drive Start with this disk to bypass the hard disk boot files Format floppy disk in Windows Copy to the floppy: NTLDR, NTDETECT. ...
BackDoors
... avoid being logged and many times the machine can appear to have no one online even while an intruder is using it. Be able to get back into the machine with the least amount of time. Most intruders want to easily get back into the machine without having to do all the work of exploiting a hole to gai ...
... avoid being logged and many times the machine can appear to have no one online even while an intruder is using it. Be able to get back into the machine with the least amount of time. Most intruders want to easily get back into the machine without having to do all the work of exploiting a hole to gai ...
Document
... System Restore Restores your computer to how it was on a previous date. • Choose to restore to very last change to your system. • Or choose from a list of dates on the next screen to restore back to. • You are then prompted to restart .) •system restore (Microsoft video) •You can also create restor ...
... System Restore Restores your computer to how it was on a previous date. • Choose to restore to very last change to your system. • Or choose from a list of dates on the next screen to restore back to. • You are then prompted to restart .) •system restore (Microsoft video) •You can also create restor ...
Design a Mini-Operating System for Mobile Phone
... system in their manufacturing including Nokia and Sony Erickson. The reason is the wide choices for the programmer because the system is developed using C++ with plug INS that facilitate its easy use and added features. The system allows the administrators to access remote to the user's mobile to ad ...
... system in their manufacturing including Nokia and Sony Erickson. The reason is the wide choices for the programmer because the system is developed using C++ with plug INS that facilitate its easy use and added features. The system allows the administrators to access remote to the user's mobile to ad ...
Improve Your Windows 7 Registry With 7 Easy Tweaks | PCWorld
... To perform any of the Registry modifications outlined in this article, you must first access Windows 7's built-in Registry Editor. To do so, click the Start button, type regedit in the search field, and press Enter. The Windows Registry Editor will open and present you with what looks like a never-e ...
... To perform any of the Registry modifications outlined in this article, you must first access Windows 7's built-in Registry Editor. To do so, click the Start button, type regedit in the search field, and press Enter. The Windows Registry Editor will open and present you with what looks like a never-e ...
Work with Files and Directories
... TCP/IP on BSD UNIX. • TCP/IP is a set of protocols used by the Internet for communication. • The incorporation of TCP/IP into UNIX and its use as the basis of development were two key factors in the rapid growth of the Internet (and UNIX). ...
... TCP/IP on BSD UNIX. • TCP/IP is a set of protocols used by the Internet for communication. • The incorporation of TCP/IP into UNIX and its use as the basis of development were two key factors in the rapid growth of the Internet (and UNIX). ...
A. Windows Networking – (Supplementary/Advanced)
... Here we introduce key operating system concepts found in Windows XP/WS 2003, such as the Windows API, processes, threads, virtual memory, kernel mode and user mode, objects, handles, and security. The Windows (formerly known as Win32) application programming interface (API) is the primary programmin ...
... Here we introduce key operating system concepts found in Windows XP/WS 2003, such as the Windows API, processes, threads, virtual memory, kernel mode and user mode, objects, handles, and security. The Windows (formerly known as Win32) application programming interface (API) is the primary programmin ...
Introduction to Operating Systems
... have an optional CLI that runs in a window. Figure 1–2 shows the Windows 10 Command Prompt for the user Jane: white characters against a black screen, with a blinking cursor waiting for you to type a command at the keyboard. A cursor in a CLI is merely a marker for the current position where what yo ...
... have an optional CLI that runs in a window. Figure 1–2 shows the Windows 10 Command Prompt for the user Jane: white characters against a black screen, with a blinking cursor waiting for you to type a command at the keyboard. A cursor in a CLI is merely a marker for the current position where what yo ...
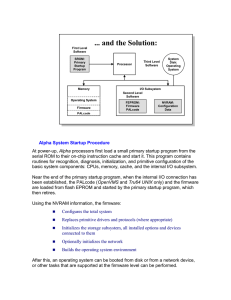
Alpha System Startup Procedure
... some systems with AlphaBIOS have EISA and PCI expansion slots, others have ISA and PCI expansion slots, and some new Compaq AlphaServer systems such as DS10 and ES40 have PCI expansion slots only. As a result, EISA setup options appear in the AlphaBIOS screens for the systems with EISA slots, and no ...
... some systems with AlphaBIOS have EISA and PCI expansion slots, others have ISA and PCI expansion slots, and some new Compaq AlphaServer systems such as DS10 and ES40 have PCI expansion slots only. As a result, EISA setup options appear in the AlphaBIOS screens for the systems with EISA slots, and no ...
Resource Guide for Windows Server 2008 R2 Early Adopters
... and Budgeting (PMB) infrastructure. This infrastructure promotes energy efficiency on computer systems by providing power consumption and management features. Additionally, PMB provides additional options to configure power metering and budgeting. System manufacturers, IT professionals, and end user ...
... and Budgeting (PMB) infrastructure. This infrastructure promotes energy efficiency on computer systems by providing power consumption and management features. Additionally, PMB provides additional options to configure power metering and budgeting. System manufacturers, IT professionals, and end user ...
Device Drivers: Their Function in an Operating System
... The effort required to support different brands of peripheral devices was one of the major reasons DOS gave way to the Windows operating system. For example, with DOS systems, in order to provide reliable control over the printing of a document, each application provides its own set of printer drive ...
... The effort required to support different brands of peripheral devices was one of the major reasons DOS gave way to the Windows operating system. For example, with DOS systems, in order to provide reliable control over the printing of a document, each application provides its own set of printer drive ...
Chapter 5
... better This upgrade This upgrade different used point-and-click PC system runs Offers a new graphics toWindows Windows to NT includes faster operating graphical commands user with multi-user capabilities 95 and and offers additional file and more system interface a mousewith and (GUI) desktop as int ...
... better This upgrade This upgrade different used point-and-click PC system runs Offers a new graphics toWindows Windows to NT includes faster operating graphical commands user with multi-user capabilities 95 and and offers additional file and more system interface a mousewith and (GUI) desktop as int ...
CH12
... Vista Upgrade DVD (cont’d.) • Steps to get around error – 1. Boot from Vista upgrade DVD, start the installation • Do not enter product key • Uncheck Automatically activate Windows when I’m ...
... Vista Upgrade DVD (cont’d.) • Steps to get around error – 1. Boot from Vista upgrade DVD, start the installation • Do not enter product key • Uncheck Automatically activate Windows when I’m ...
RootkitRevealer v1.71 - Big
... presence from a directory listing, for example, will be seen by RootkitRevealer as a discrepancy between the information returned by the Windows API and that seen in the raw scan of a FAT or NTFS volume's file system structures. Can a Rootkit hide from RootkitRevealer It is theoretically possible fo ...
... presence from a directory listing, for example, will be seen by RootkitRevealer as a discrepancy between the information returned by the Windows API and that seen in the raw scan of a FAT or NTFS volume's file system structures. Can a Rootkit hide from RootkitRevealer It is theoretically possible fo ...
Windows Phone 8.1
Windows Phone 8.1, rolled out at Microsoft's Build Conference in San Francisco, California, on April 2, 2014, is the third generation of Microsoft's Windows Phone mobile operating system, succeeding Windows Phone 8. It was released in final form to Windows Phone developers on April 14, 2014 and reached general availability on July 15, 2014. All Windows Phones running Windows Phone 8 will be upgraded to Windows Phone 8.1, with release dependent on carrier rollout dates.Windows Phone 8.1 is also the last version that will be under the Windows Phone brand name and will be succeeded by Windows 10 Mobile. Most Windows Phone 8.1 devices will be capable of being upgraded to Windows 10 Mobile, subject to device compatibility.