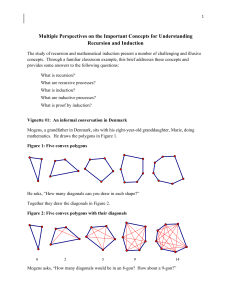
LEC01 - aiub study guide
... of the input (not only the length n). This is modeled by tj. In the case of insertion sort the time tj depends on the original sorting of the input array. ...
... of the input (not only the length n). This is modeled by tj. In the case of insertion sort the time tj depends on the original sorting of the input array. ...
Smooth Tradeoffs between Insert and Query Complexity in
... content-based search [KG09, LJW+ 07], collaborative filtering [DDGR07], pattern classification [CH67], clustering [Ber02]. In the similarity search problem the algorithm is given a database of objects to preprocess and is then required to find, for each query object q, the object in the database tha ...
... content-based search [KG09, LJW+ 07], collaborative filtering [DDGR07], pattern classification [CH67], clustering [Ber02]. In the similarity search problem the algorithm is given a database of objects to preprocess and is then required to find, for each query object q, the object in the database tha ...
Efficient Deep Feature Learning and Extraction via StochasticNets
... fundamental properties of the network architecture of a certain type of deep neural network is preserved, the probability p(i → j) must be designed in such a way that these properties are enforced appropriately in the resultant random graph realization. Let us consider a general deep feedforward neu ...
... fundamental properties of the network architecture of a certain type of deep neural network is preserved, the probability p(i → j) must be designed in such a way that these properties are enforced appropriately in the resultant random graph realization. Let us consider a general deep feedforward neu ...
as a PDF
... network. In this figure, the vertices X and Y are constraints, and vertices R1 through R4 are initial events (roots). A parent set consists of one parent for X and one for Y (e.g., {P1(X), P3(Y)}, {P3(X), P3(Y)} ). The first part of the search iteration begins by computing the CMPPs for each parent ...
... network. In this figure, the vertices X and Y are constraints, and vertices R1 through R4 are initial events (roots). A parent set consists of one parent for X and one for Y (e.g., {P1(X), P3(Y)}, {P3(X), P3(Y)} ). The first part of the search iteration begins by computing the CMPPs for each parent ...
Handling the Class Imbalance Problem in Binary Classification
... Natural processes often generate some observations more frequently than others. These processes result in an unbalanced distributions which cause the classifiers to bias toward the majority class especially because most classifiers assume a normal distribution. The quantity and the diversity of imba ...
... Natural processes often generate some observations more frequently than others. These processes result in an unbalanced distributions which cause the classifiers to bias toward the majority class especially because most classifiers assume a normal distribution. The quantity and the diversity of imba ...
Probably About Probability p < .05
... addition rule is given by: p(A or B) = p(A) + p(B) - p(A and B) p(A and B) is the probability that both event A and event B occur simultaneously This formula can always be used as the addition rule because p(A and B) equals zero when the events are mutually exclusive ...
... addition rule is given by: p(A or B) = p(A) + p(B) - p(A and B) p(A and B) is the probability that both event A and event B occur simultaneously This formula can always be used as the addition rule because p(A and B) equals zero when the events are mutually exclusive ...
Longest Common Substring with Approximately k Mismatches
... sequences. This task can be formalised in many different ways, from the longest common substring problem to the edit distance problem. The longest common substring problem can be solved in optimal linear time and space, while the best known algorithms for the edit distance problem require n2−o(1) ti ...
... sequences. This task can be formalised in many different ways, from the longest common substring problem to the edit distance problem. The longest common substring problem can be solved in optimal linear time and space, while the best known algorithms for the edit distance problem require n2−o(1) ti ...
Full Text
... with many theoretical and practical applications in artificial intelligence and mathematical logic. Heuristic local search algorithms are widely recognized as the most effective approaches used to solve them. However, their performance depends both on their complexity and their tuning parameters whi ...
... with many theoretical and practical applications in artificial intelligence and mathematical logic. Heuristic local search algorithms are widely recognized as the most effective approaches used to solve them. However, their performance depends both on their complexity and their tuning parameters whi ...
Induction and Decision Trees
... •The algorithm we are going to present can be easily extended to non-Boolean classification problems • That is, problems in which there are 3 or more possible classes • Example of such problems? ...
... •The algorithm we are going to present can be easily extended to non-Boolean classification problems • That is, problems in which there are 3 or more possible classes • Example of such problems? ...
Spiking Neural Networks: Principles and Challenges
... Hebbian learning, and its spiking generalisations such as STDP. The detection of correlations can be a goal in itself, but it can also be used subsequently, for example to cluster or classify data. In its “standard form” STDP is understood as a process that strengthens a synaptic weight, if the post ...
... Hebbian learning, and its spiking generalisations such as STDP. The detection of correlations can be a goal in itself, but it can also be used subsequently, for example to cluster or classify data. In its “standard form” STDP is understood as a process that strengthens a synaptic weight, if the post ...
Artificial Intelligence Meets the Mainstream
... missing data, but in general it’s better to work with the most complete and enriched data possible. ...
... missing data, but in general it’s better to work with the most complete and enriched data possible. ...
Artificial Intelligence Chapter 7 - Computer Science
... • It is a well-known and interesting psychological phenomenon that if a cold stimulus is applied to a person’s skin for a short period of time, the person will perceive heat. • However, if the same stimulus is applied for a longer period of time, the person will perceive cold. The use of discrete ti ...
... • It is a well-known and interesting psychological phenomenon that if a cold stimulus is applied to a person’s skin for a short period of time, the person will perceive heat. • However, if the same stimulus is applied for a longer period of time, the person will perceive cold. The use of discrete ti ...
Reinforcement Learning for Neural Networks using Swarm Intelligence
... described in [18]. As shown in Fig. 2, a cart is placed on a 4.8 meter track, and two poles of length of 1 meter and 0.1 meter respectively are attached to the top of the cart via hinges. Both poles have a linear density of 0.1 kilogram per meter. The mass of the cart is 1 kilogram. The state of the ...
... described in [18]. As shown in Fig. 2, a cart is placed on a 4.8 meter track, and two poles of length of 1 meter and 0.1 meter respectively are attached to the top of the cart via hinges. Both poles have a linear density of 0.1 kilogram per meter. The mass of the cart is 1 kilogram. The state of the ...