SCENERY RECONSTRUCTION: AN OVERVIEW 1
... A related topic: distinguishing sceneries. A related important problem is to distinguish sceneries: Let η1 and η2 be two given sceneries. Assume that either η1 or η2 is observed along a random walk path, but we do not know which one. Can we figure out which of the two sceneries was taken? The proble ...
... A related topic: distinguishing sceneries. A related important problem is to distinguish sceneries: Let η1 and η2 be two given sceneries. Assume that either η1 or η2 is observed along a random walk path, but we do not know which one. Can we figure out which of the two sceneries was taken? The proble ...
Blackbox on Sokoban problems
... planner which generates a truly optimal plan rather than one that runs marginally quicker than others. We can define plan quality as the following three components: plan length, plan time, and resources consumed. Plan length is simply the number of unique actions occurring in a plan. Plan time is th ...
... planner which generates a truly optimal plan rather than one that runs marginally quicker than others. We can define plan quality as the following three components: plan length, plan time, and resources consumed. Plan length is simply the number of unique actions occurring in a plan. Plan time is th ...
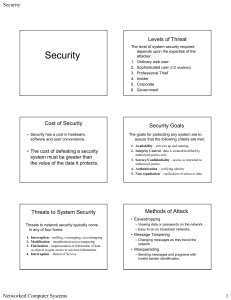
Chapter 1 Security Problems in Computing
... Popular Encryption Algorithms – Merkle-Hellman Knapsacks – RSA Encryption – El Gamal Algorithms – DES Hashing Algorithms ...
... Popular Encryption Algorithms – Merkle-Hellman Knapsacks – RSA Encryption – El Gamal Algorithms – DES Hashing Algorithms ...
AANA Journal Course, AANA Journal, August 1998
... The periosteum of the femur is innervated primarily by the femoral nerve. The distal and proximal portions of the femur contain contributing innervation from the obturator nerve and sciatic nerve. Although other analgesic and anesthetic techniques could be utilized for femur fractures, the femoral n ...
... The periosteum of the femur is innervated primarily by the femoral nerve. The distal and proximal portions of the femur contain contributing innervation from the obturator nerve and sciatic nerve. Although other analgesic and anesthetic techniques could be utilized for femur fractures, the femoral n ...
Public-Key Cryptosystems Based on Hard Problems
... In this type of cryptosystems, users have two types of keys: a public and a private. The public key - which is known by everyone - is used only for encryption. On the other hand, messages can be decrypted with the private one. The private key is secret and only the recipient owns it. First of all, w ...
... In this type of cryptosystems, users have two types of keys: a public and a private. The public key - which is known by everyone - is used only for encryption. On the other hand, messages can be decrypted with the private one. The private key is secret and only the recipient owns it. First of all, w ...
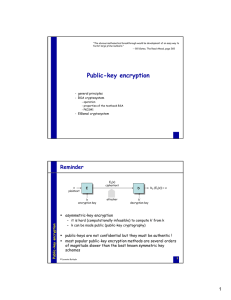
Public-key encryption
... to improve efficiency of encryption, it is desirable to select a small exponent e (e.g., e = 3 is typical) a group of entities may use the same exponent, but different moduli (e.g., e = 3, and n1, n2, …) in this case, an attacker may find a plaintext m efficiently, if m is sent to several (at ...
... to improve efficiency of encryption, it is desirable to select a small exponent e (e.g., e = 3 is typical) a group of entities may use the same exponent, but different moduli (e.g., e = 3, and n1, n2, …) in this case, an attacker may find a plaintext m efficiently, if m is sent to several (at ...
PK b
... (H1, H2-queries 2/2) B adds to the H1-list and responds
to A by setting H1(Wi)=hi.
Note that hi is uniform in G1 and is independent
of A’s current view as required.
Similarly, A queries to H2. B responds to H2(t) by
picking a new random V {0,1}log p for each new t and
setting H2(t) ...
... (H1, H2-queries 2/2) B adds
Apply encryption to network and system security
... Encryption is the process of taking some information or data, manipulating or changing its format in a way that stops it from being used or read by unauthorized people or systems. Encryption involves scrambling data so that it needs to be unscrambled, or decrypted, to be read. Encryption can be appl ...
... Encryption is the process of taking some information or data, manipulating or changing its format in a way that stops it from being used or read by unauthorized people or systems. Encryption involves scrambling data so that it needs to be unscrambled, or decrypted, to be read. Encryption can be appl ...
MT311-14
... applets were sensational because they provided a cross-platform solution for making a webpage more interesting. To safeguard users from malicious applets, applets are run in a sandbox, which imposes rather stringent restrictions on what the applets can do. ...
... applets were sensational because they provided a cross-platform solution for making a webpage more interesting. To safeguard users from malicious applets, applets are run in a sandbox, which imposes rather stringent restrictions on what the applets can do. ...
Devireddy
... Wired Equivalent Privacy (WEP), a security protocol for wireless local area networks (WLANs) defined in the 802.11b standard. LANs are more secure than WLANs. WLANs, which are over radio waves are more vulnerable to tampering. WEP provides security by encrypting data ...
... Wired Equivalent Privacy (WEP), a security protocol for wireless local area networks (WLANs) defined in the 802.11b standard. LANs are more secure than WLANs. WLANs, which are over radio waves are more vulnerable to tampering. WEP provides security by encrypting data ...
30. basic pediatric regional anesthesia
... may spread further than the provider intends. Additionally, because the local anesthetic spreads easily in children, the duration of the block may be shortened compared to an adult. In general, as the patient’s age increases, local anesthetic latency of onset and duration of action increases as well ...
... may spread further than the provider intends. Additionally, because the local anesthetic spreads easily in children, the duration of the block may be shortened compared to an adult. In general, as the patient’s age increases, local anesthetic latency of onset and duration of action increases as well ...
CN 2015 5 - SNGCE DIGITAL LIBRARY
... authentication and access control to protect the networks from unauthorized traffic. This is known as firewalls Firewall system is an electronic security guard and electronic ...
... authentication and access control to protect the networks from unauthorized traffic. This is known as firewalls Firewall system is an electronic security guard and electronic ...
How to Encrypt with the LPN Problem
... where a sender and a receiver share a secret key. Up to now, most of the work in this field has concentrated on studying various operating modes to use with a secure block cipher [2]. Departing from this approach, we will construct a symmetric encryption scheme that does not appeal to any assumption ...
... where a sender and a receiver share a secret key. Up to now, most of the work in this field has concentrated on studying various operating modes to use with a secure block cipher [2]. Departing from this approach, we will construct a symmetric encryption scheme that does not appeal to any assumption ...
Composing semantic Web services under constraints
... Composing semantic Web services under constraints E.Karakoc, P.Senkul Journal: Expert Systems with Applications ...
... Composing semantic Web services under constraints E.Karakoc, P.Senkul Journal: Expert Systems with Applications ...
View File - University of Engineering and Technology, Taxila
... – Speech can tolerate much higher bit errors (10 -2 depending on encoding/compression algorithm) • Error Control Coding used to overcome BER TI - 1011 ...
... – Speech can tolerate much higher bit errors (10 -2 depending on encoding/compression algorithm) • Error Control Coding used to overcome BER TI - 1011 ...
ABSOLUTE DEPENDENT MOTION ANALYSIS OF TWO
... heavy objects. The total lifting force required from the truck depends on the acceleration of the cabinet. How can we determine the acceleration and velocity of the cabinet if the acceleration of the truck is known? ...
... heavy objects. The total lifting force required from the truck depends on the acceleration of the cabinet. How can we determine the acceleration and velocity of the cabinet if the acceleration of the truck is known? ...
Slides on Security
... • Key servers are computers that have a database of public keys. • Upon receiving a request for a public key, a key server sends the client the desired public key. • The messages from the key server are ...
... • Key servers are computers that have a database of public keys. • Upon receiving a request for a public key, a key server sends the client the desired public key. • The messages from the key server are ...
Enhancement of Security through a Cryptographic Algorithm
... Pulkit Singhal, 2Narendra Kumar Verma, 3Aurobinda Laha, 4Prof. Pranam Paul and 5Prof. A K Bhattacharjee ...
... Pulkit Singhal, 2Narendra Kumar Verma, 3Aurobinda Laha, 4Prof. Pranam Paul and 5Prof. A K Bhattacharjee ...
Packaging Information: Data Compression and
... Encryption keys are used to encode plaintext as encoded ciphertext Decryption keys are used to decode ciphertext and recover the original plaintext Decryption keys are sometimes discovered by brute force methods employing computers to search large potential key spaces ...
... Encryption keys are used to encode plaintext as encoded ciphertext Decryption keys are used to decode ciphertext and recover the original plaintext Decryption keys are sometimes discovered by brute force methods employing computers to search large potential key spaces ...
Second Midterm Exam Solutions
... and thus the collision is inelastic. (b) In the graph below, sketch the force that each object exerts on the other during the collision, as a function of time. (Your sketch only needs to be qualitatively correct, not quantitatively accurate). Clearly indicate (label!) which curve belongs to which fo ...
... and thus the collision is inelastic. (b) In the graph below, sketch the force that each object exerts on the other during the collision, as a function of time. (Your sketch only needs to be qualitatively correct, not quantitatively accurate). Clearly indicate (label!) which curve belongs to which fo ...
Blue Border - Courant Institute of Mathematical Sciences
... Zp[x]/(xn-1)=polynomials of degree at most n-1, with coefficients in Zp ...
... Zp[x]/(xn-1)=polynomials of degree at most n-1, with coefficients in Zp ...
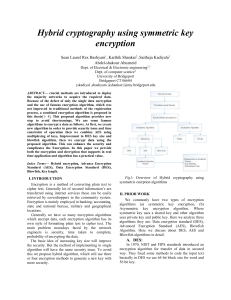
Hybrid cryptography using symmetric key encryption
... bits and 96 bits are split into 2 parts as 84 and 12 bits, where 12 bits are allotted for parity bits the rest 84 bits are altered and complex operation is done as follows. Fig 6, shows the improved des using 96-bits, where 84 bits are splatted into three blocks as 48, 28 and 8 bits, where the 8 bit ...
... bits and 96 bits are split into 2 parts as 84 and 12 bits, where 12 bits are allotted for parity bits the rest 84 bits are altered and complex operation is done as follows. Fig 6, shows the improved des using 96-bits, where 84 bits are splatted into three blocks as 48, 28 and 8 bits, where the 8 bit ...
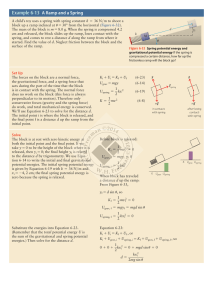
Example 6-13 A Ramp and a Spring
... In our solution we assumed that the final spring potential energy is zero, which means that the spring ends up neither compressed nor stretched. In other words, we assumed that the block moves so far up the ramp that it loses contact with the spring. That’s consistent with our result: The block move ...
... In our solution we assumed that the final spring potential energy is zero, which means that the spring ends up neither compressed nor stretched. In other words, we assumed that the block moves so far up the ramp that it loses contact with the spring. That’s consistent with our result: The block move ...