CISSP Guide to Security Essentials, Ch4
... • Based upon flow of information rather than on access controls • Data objects are assigned to a class or level of security • Flow of objects are controlled by security policy that specifies where objects of various levels are permitted to flow ...
... • Based upon flow of information rather than on access controls • Data objects are assigned to a class or level of security • Flow of objects are controlled by security policy that specifies where objects of various levels are permitted to flow ...
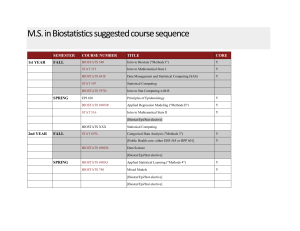
M.S. in Biostatistics suggested course sequence
... M.S. in Biostatistics suggested course sequence 1st YEAR ...
... M.S. in Biostatistics suggested course sequence 1st YEAR ...
Giovanna Sissa Osservatorio Tecnologico MIUR
... •It allows the students to learn more because they can better understand how computers and operating systems work; •It widens the learning spectrum of the students promoting the creation of different skills; •It makes possible to reuse obsolete hardware systems still available at school, thus helpin ...
... •It allows the students to learn more because they can better understand how computers and operating systems work; •It widens the learning spectrum of the students promoting the creation of different skills; •It makes possible to reuse obsolete hardware systems still available at school, thus helpin ...
On Software Engineering Repositories and Their Open Problems
... composed of a large number of attributes, however, many of those attributes are missing values that need to be discarded in order to apply machine learning algorithms. There are also inconsistencies in the way information is stored [27]. In this particular dataset, cleaning inconsistencies (e.g., la ...
... composed of a large number of attributes, however, many of those attributes are missing values that need to be discarded in order to apply machine learning algorithms. There are also inconsistencies in the way information is stored [27]. In this particular dataset, cleaning inconsistencies (e.g., la ...
Slide 1
... of isn’t the operating system depends on used very frequently, might not need system ifofreasonable the OS could providing parts of the SK … Few OS’s come with part the TCB at definition all, ifbiometric the TCB By any of theis whether or not the security architecture to be continuously memory resid ...
... of isn’t the operating system depends on used very frequently, might not need system ifofreasonable the OS could providing parts of the SK … Few OS’s come with part the TCB at definition all, ifbiometric the TCB By any of theis whether or not the security architecture to be continuously memory resid ...
Secure your remote access with VASCO and
... Combining Juniper Networks’ firewalls, VPN solutions and network access security appliances with VASCO’s DIGIPASS strong authentication enhances the security of your network and remote access, while remaining easy-to-use When employees use their PC, they want to read e-mail, use software and documen ...
... Combining Juniper Networks’ firewalls, VPN solutions and network access security appliances with VASCO’s DIGIPASS strong authentication enhances the security of your network and remote access, while remaining easy-to-use When employees use their PC, they want to read e-mail, use software and documen ...
On Software Engineering Repositories and Their Open Problems
... have to refute contradictory results because of lack of generalisation. However, gathering a large amount of software and data for empirical studies can be a cumbersome task, prone to the introduction of unintentional errors, and potentially causing more problems than they solve. The popularization ...
... have to refute contradictory results because of lack of generalisation. However, gathering a large amount of software and data for empirical studies can be a cumbersome task, prone to the introduction of unintentional errors, and potentially causing more problems than they solve. The popularization ...
The wild world of malware: Keeping your
... Now even the smallest companies can enjoy levels of protection that essentially inoculate them from many forms of malware. And these companies can do so cost effectively. By recognizing the threat contemporary malware represents, and by implementing a contemporary security solution, the wild world o ...
... Now even the smallest companies can enjoy levels of protection that essentially inoculate them from many forms of malware. And these companies can do so cost effectively. By recognizing the threat contemporary malware represents, and by implementing a contemporary security solution, the wild world o ...
Guide to Firewalls and Network Security with Intrusion Detection and
... Value generated by an algorithm that can also be processed by an algorithm to encrypt or decrypt text Length of the key determines how secure the level of encryption is ...
... Value generated by an algorithm that can also be processed by an algorithm to encrypt or decrypt text Length of the key determines how secure the level of encryption is ...
Introduction to OS cornell 414
... modification, editors, linker/loaders, etc • An important one is the command interpreter (or shell), which parses user input, interprets it, and executes it • Shells can either execute the command, or invoke other system programs or system calls to do it. • Trade-offs: performance, increasing/updati ...
... modification, editors, linker/loaders, etc • An important one is the command interpreter (or shell), which parses user input, interprets it, and executes it • Shells can either execute the command, or invoke other system programs or system calls to do it. • Trade-offs: performance, increasing/updati ...
Document
... – Replace every two – three years – Use with all devices that have solid-state components ...
... – Replace every two – three years – Use with all devices that have solid-state components ...
Net+ Chapter 1
... • Kerberos is a secure system, using strong encryption processes that are designed to provide authentication for users and services that need to communicate and be validated on a network. • Kerberos provides a way to prove identity in order to gain access to other network resources. • Kerberos works ...
... • Kerberos is a secure system, using strong encryption processes that are designed to provide authentication for users and services that need to communicate and be validated on a network. • Kerberos provides a way to prove identity in order to gain access to other network resources. • Kerberos works ...
Access Control
... Memory and Address Protection • Prevent program from corrupting other programs or data, operating system and maybe itself – Often, the OS can exploit hardware support for this protection, so it’s cheap ...
... Memory and Address Protection • Prevent program from corrupting other programs or data, operating system and maybe itself – Often, the OS can exploit hardware support for this protection, so it’s cheap ...
pps - AquaLab - Northwestern University
... – Free program made available to unsuspecting user – Actually contains code to do harm – Place altered version of utility program (e.g. ls) on victim's computer & trick user into running it ...
... – Free program made available to unsuspecting user – Actually contains code to do harm – Place altered version of utility program (e.g. ls) on victim's computer & trick user into running it ...
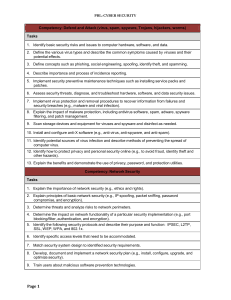
Competency: Defend and Attack (virus, spam, spyware - FBLA-PBL
... 7. Distinguish between public key encryption and digital signatures. 8. Describe cryptographic protocols and applications, like digital cash, password-authenticated key agreement, multi-party key agreement, and time stamping service. Competency: Authentication Tasks 1. Describe authentication proces ...
... 7. Distinguish between public key encryption and digital signatures. 8. Describe cryptographic protocols and applications, like digital cash, password-authenticated key agreement, multi-party key agreement, and time stamping service. Competency: Authentication Tasks 1. Describe authentication proces ...
Remote Laboratory for Industrial Automation
... - They’re limited to timetables - Require a presence of a tutor or a technician ...
... - They’re limited to timetables - Require a presence of a tutor or a technician ...
USING A RASPBERRY PI AS A MAIN DEVICE IN HIGHER
... keyboard and mouse. If you wish to connect anything else then you will instead need to connect to a powered USB hub. Ethernet cable: An Ethernet cable is required to connect the Raspberry Pi to a router. Either CAT‐5e or CAT‐6 cables can be used. The port is limited to 100Mbps so there is no be ...
... keyboard and mouse. If you wish to connect anything else then you will instead need to connect to a powered USB hub. Ethernet cable: An Ethernet cable is required to connect the Raspberry Pi to a router. Either CAT‐5e or CAT‐6 cables can be used. The port is limited to 100Mbps so there is no be ...
PPT - GPU : a Global Processing Unit
... world, via the Internet, to look for extra-terrestrial radio signals, to look for prime numbers so large that they have more than ten million digits, and to find more effective drugs to fight cancer and the AIDS virus. These projects run when the computer is idle These projects are so large, and ...
... world, via the Internet, to look for extra-terrestrial radio signals, to look for prime numbers so large that they have more than ten million digits, and to find more effective drugs to fight cancer and the AIDS virus. These projects run when the computer is idle These projects are so large, and ...
CIS 442_Chapter5_
... A hoax, like other rumors, can persist for a long time before it dies off, and its cumulative effect (wasting users’ time and causing pain and suffering) may be out of proportion to the work needed to start it. A hoax can inspire new viruses (the opposite is also true). The “good time” hoax, for exa ...
... A hoax, like other rumors, can persist for a long time before it dies off, and its cumulative effect (wasting users’ time and causing pain and suffering) may be out of proportion to the work needed to start it. A hoax can inspire new viruses (the opposite is also true). The “good time” hoax, for exa ...
Hardware abstraction layer for microcontrollers
... source: ubmdesign.com / http://www.slideshare.net/MTKDMI/2013-embedded-market-study-final 10 ...
... source: ubmdesign.com / http://www.slideshare.net/MTKDMI/2013-embedded-market-study-final 10 ...
Chap12 Presentation
... Data collected every Data combined time you fill out with information form or click from public advertisement on sources Web Merchants Merchants sell sell the Marketing firms contents of their sell your databases to electronic profile national marketing Next to any company firms and Internet p.12.27 ...
... Data collected every Data combined time you fill out with information form or click from public advertisement on sources Web Merchants Merchants sell sell the Marketing firms contents of their sell your databases to electronic profile national marketing Next to any company firms and Internet p.12.27 ...
Lock down security exposures in your Domino web
... Basic authentication: Name and password access • User submits name and password, which Domino compares to Person document in a Domino directory or to a record in an LDAP directory • Easy to set up and administer. Just create Person and Group documents. • Problem: Name and password cross network as ...
... Basic authentication: Name and password access • User submits name and password, which Domino compares to Person document in a Domino directory or to a record in an LDAP directory • Easy to set up and administer. Just create Person and Group documents. • Problem: Name and password cross network as ...
Intro to OS
... user needs to know the name/type/location of everything • Distributed OSs (e.g., Amoeba, Mach, Locus) provide transparency to user, yielding one huge virtual machine! • Specialized OSs are built for specific purposes: routing engines (Networking), lisp machines (AI), time constrained applications (R ...
... user needs to know the name/type/location of everything • Distributed OSs (e.g., Amoeba, Mach, Locus) provide transparency to user, yielding one huge virtual machine! • Specialized OSs are built for specific purposes: routing engines (Networking), lisp machines (AI), time constrained applications (R ...
Manage security settings with Action Center
... A firewall is software or hardware that checks information coming from the Internet or a network and then either turns it away or allows it to pass through to your computer. In this way, a firewall helps prevent hackers and malicious software from gaining access to your computer. Even if you think t ...
... A firewall is software or hardware that checks information coming from the Internet or a network and then either turns it away or allows it to pass through to your computer. In this way, a firewall helps prevent hackers and malicious software from gaining access to your computer. Even if you think t ...