Open resource
... In February 2013 the President issues Executive Order 13636: Improving Critical Infrastructure Cybersecurity One component of that Executive Order directed the National Institute of Standards and Technology (NIST) to work with stakeholders to develop a voluntary framework – based on existing sta ...
... In February 2013 the President issues Executive Order 13636: Improving Critical Infrastructure Cybersecurity One component of that Executive Order directed the National Institute of Standards and Technology (NIST) to work with stakeholders to develop a voluntary framework – based on existing sta ...
US SAFE WEB Act - Higher Education Compliance Alliance
... from the report included: organizations lack of risk assessment policies, concerns with sensitive systems and data, lack of encryption, unclassified and unmanaged data, and under-staffed and under-funded departments managing cyber security. This report highlighted the many vulnerabilities of the ind ...
... from the report included: organizations lack of risk assessment policies, concerns with sensitive systems and data, lack of encryption, unclassified and unmanaged data, and under-staffed and under-funded departments managing cyber security. This report highlighted the many vulnerabilities of the ind ...
InterScan Messaging Security Solutions
... • ActiveAction provides automated responses to viruses, spyware, and other malware ...
... • ActiveAction provides automated responses to viruses, spyware, and other malware ...
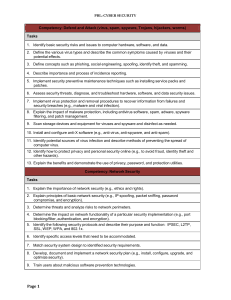
Competency: Defend and Attack (virus, spam, spyware - FBLA-PBL
... 1. Explain concepts such as denial of service, hacking/cracking, intrusion, and intellectual property. 2. Assess security threats and develop plan to address. 3. Analyze and inspect the system’s configuration and vulnerabilities to detect inadvisable settings. 4. Inspect the password files to detect ...
... 1. Explain concepts such as denial of service, hacking/cracking, intrusion, and intellectual property. 2. Assess security threats and develop plan to address. 3. Analyze and inspect the system’s configuration and vulnerabilities to detect inadvisable settings. 4. Inspect the password files to detect ...
10.2 BASIC E-COMMERCE SECURITY ISSUES AND LANDSCAPE
... Drivers for EC security management: The laws and regulations with which organizations must comply. The conduct of global EC. Information assets have become critical to the operation of many businesses. New and faster information technologies are shared throughout organizations. The complexit ...
... Drivers for EC security management: The laws and regulations with which organizations must comply. The conduct of global EC. Information assets have become critical to the operation of many businesses. New and faster information technologies are shared throughout organizations. The complexit ...
Professional Malware is a Pandemic
... Espionage Isn’t Just for Govt’s April 3rd, 2008 "Espionage used to be a problem for the FBI, CIA and military, but now it's a problem for corporations. It's no longer a cloak-and-dagger thing. It's about computer architecture and the soundness of electronic systems.“ - Joel Brenner - Office of the ...
... Espionage Isn’t Just for Govt’s April 3rd, 2008 "Espionage used to be a problem for the FBI, CIA and military, but now it's a problem for corporations. It's no longer a cloak-and-dagger thing. It's about computer architecture and the soundness of electronic systems.“ - Joel Brenner - Office of the ...
Computer and Information Security
... – Example: Newspaper prints info leaked from White House and gives wrong source ...
... – Example: Newspaper prints info leaked from White House and gives wrong source ...
Systeemanalyse in Ontwerpprojecten
... management procedures, identification of risks from a third party, user training, physical entry controls, backing-up of data, clear desk/screen policy, controls against malicious software, user registration, forcing correct use of passwords, intrusion detection, system recovery procedures • Securit ...
... management procedures, identification of risks from a third party, user training, physical entry controls, backing-up of data, clear desk/screen policy, controls against malicious software, user registration, forcing correct use of passwords, intrusion detection, system recovery procedures • Securit ...
SMALL FIRMS CYBERSECURITY GUIDANCE
... internet such as smartphones, email, social media, and cloud computing services in an effort to increase efficiency and revenues. Through this dependence they become larger targets for cybercriminals looking to exploit technological vulnerabilities. Cybersecurity firm Symantec reports that in 2012, ...
... internet such as smartphones, email, social media, and cloud computing services in an effort to increase efficiency and revenues. Through this dependence they become larger targets for cybercriminals looking to exploit technological vulnerabilities. Cybersecurity firm Symantec reports that in 2012, ...
WHAT IS EC SECURITY? - Joseph H. Schuessler, PhD
... A network that uses the public Internet to carry information but remains private by using encryption to scramble the communications, authentication to ensure that information has not been tampered with, and access control to verify the identity of anyone using the network protocol tunneling ...
... A network that uses the public Internet to carry information but remains private by using encryption to scramble the communications, authentication to ensure that information has not been tampered with, and access control to verify the identity of anyone using the network protocol tunneling ...
Network Security
... algorithms and protocols underlying network security applications, including encryption, hash functions, digital signatures, and key exchange. • Part Two : Examines the use of cryptographic algorithms and security protocols to provide security over networks and the Internet. Topics covered include u ...
... algorithms and protocols underlying network security applications, including encryption, hash functions, digital signatures, and key exchange. • Part Two : Examines the use of cryptographic algorithms and security protocols to provide security over networks and the Internet. Topics covered include u ...
Network Security
... algorithms and protocols underlying network security applications, including encryption, hash functions, digital signatures, and key exchange. • Part Two : Examines the use of cryptographic algorithms and security protocols to provide security over networks and the Internet. Topics covered include u ...
... algorithms and protocols underlying network security applications, including encryption, hash functions, digital signatures, and key exchange. • Part Two : Examines the use of cryptographic algorithms and security protocols to provide security over networks and the Internet. Topics covered include u ...
45.3% of employees are aware that their workplace can be
... ■ Device used to communicate business emails: Desktop PC provided by company (46.1%); Laptop PC provided by company (37.9%); Personal smartphone (13.6%). ■ In terms of security policies in the workplace, 60.7% said “yes, we have security policies”, 31.3% said “no, we do not have policies”, and 8.0% ...
... ■ Device used to communicate business emails: Desktop PC provided by company (46.1%); Laptop PC provided by company (37.9%); Personal smartphone (13.6%). ■ In terms of security policies in the workplace, 60.7% said “yes, we have security policies”, 31.3% said “no, we do not have policies”, and 8.0% ...
Cybersecurity for Asset Managers: Shielding Your Firm
... It’s their job. Similarly, those leading the cybersecurity charge—and everyone for that matter—need to be as dedicated to building defenses as those who seek to topple them. When developing their cybersecurity initiatives, firms need to weigh the potential threats against their appetite for risk by ...
... It’s their job. Similarly, those leading the cybersecurity charge—and everyone for that matter—need to be as dedicated to building defenses as those who seek to topple them. When developing their cybersecurity initiatives, firms need to weigh the potential threats against their appetite for risk by ...
Babu Madhav Institute of Information Technology, UTU 2017
... with respect to specific topic or subjects. 13. When a criminal uses someone else’s identity for his/her own illegal purposes is known as _______________. 14. ___________________ is the art of breaking into phone or other communication systems. 15. The goal of crimes targeted at individuals is to ex ...
... with respect to specific topic or subjects. 13. When a criminal uses someone else’s identity for his/her own illegal purposes is known as _______________. 14. ___________________ is the art of breaking into phone or other communication systems. 15. The goal of crimes targeted at individuals is to ex ...
Babu Madhav Institute of Information Technology, UTU 2015
... 10. _________________ mean visual deception. 11. ___________________ are the people who coerce minors to engage in sexual activities. 12. ________________ is a popular means of sharing and distributing information on the web with respect to specific topic or subjects. 13. When a criminal uses someon ...
... 10. _________________ mean visual deception. 11. ___________________ are the people who coerce minors to engage in sexual activities. 12. ________________ is a popular means of sharing and distributing information on the web with respect to specific topic or subjects. 13. When a criminal uses someon ...
Licens
... • Adoption of appropriate legislation against the misuse of ICTs for criminal or disruptive purposes, including activities intended to affect the integrity of national critical information infrastructures. • Threats can originate from anywhere around the globe, the challenges are inherently interna ...
... • Adoption of appropriate legislation against the misuse of ICTs for criminal or disruptive purposes, including activities intended to affect the integrity of national critical information infrastructures. • Threats can originate from anywhere around the globe, the challenges are inherently interna ...
CNCERT/CC Annual Report 2008
... Figure 3 Samples Capturing Times Status According to the data, the average number of new samples captured everyday is 427. That means new malicious codes were emerging endlessly. ...
... Figure 3 Samples Capturing Times Status According to the data, the average number of new samples captured everyday is 427. That means new malicious codes were emerging endlessly. ...
Phishing and whaling – Don`t get hooked!
... 1. Awareness training – Ensure everyone in your team is made aware of the risks. The more people are aware of the dangers, the less likelihood of being fooled by such attacks. 2. Payment authorisation control basics – ensure your controls such as payment authorisation delegated authorities and contr ...
... 1. Awareness training – Ensure everyone in your team is made aware of the risks. The more people are aware of the dangers, the less likelihood of being fooled by such attacks. 2. Payment authorisation control basics – ensure your controls such as payment authorisation delegated authorities and contr ...
slides
... It used to be many forms of Viruses. Worms, Trojans spread via mail – Attract download software/applet (some pretend to help against a virus) – Phishing grows quickly – Spoof sender address and identity – Huge economic cost due to destruction, traffic, cleanup costs – At its peak, 8% of emails wer ...
... It used to be many forms of Viruses. Worms, Trojans spread via mail – Attract download software/applet (some pretend to help against a virus) – Phishing grows quickly – Spoof sender address and identity – Huge economic cost due to destruction, traffic, cleanup costs – At its peak, 8% of emails wer ...
National Initiative For Cybersecurity Education (NICE)
... NICE will “enhance the overall cybersecurity posture of the United States by accelrating the availability of educational and training resources designed to improve the cyber behavior, skills, and knowledge of every segment of the population.” NIST, as the interagency lead for NICE, will promote the ...
... NICE will “enhance the overall cybersecurity posture of the United States by accelrating the availability of educational and training resources designed to improve the cyber behavior, skills, and knowledge of every segment of the population.” NIST, as the interagency lead for NICE, will promote the ...
The United States Secret Service - Federal Reserve Bank of San
... New York Electronic Crimes Task Force model, throughout the United States for the purpose of preventing, detecting, and investigating various forms of electronic crimes, including potential terrorist attacks against critical infrastructure and financial payment systems. ...
... New York Electronic Crimes Task Force model, throughout the United States for the purpose of preventing, detecting, and investigating various forms of electronic crimes, including potential terrorist attacks against critical infrastructure and financial payment systems. ...
Emerging Threats to Business Security
... Mass mailer viruses were still quite prevalent in the first half of 2007, but other threat categories are becoming more significant, although e-mail is still a preferred medium for other types of attacks. Adware is seeing increasing use, as it carries lesser legal danger for the perpetrators. The pr ...
... Mass mailer viruses were still quite prevalent in the first half of 2007, but other threat categories are becoming more significant, although e-mail is still a preferred medium for other types of attacks. Adware is seeing increasing use, as it carries lesser legal danger for the perpetrators. The pr ...
NetDay Cyber Security Kit for Schools
... and, likewise, a compromised or “hacked” network can prove very damaging. School administrators must take responsibility for making sure they understand the issues involved in securing computer networks and electronic data. Talk to your technology team and find out if your school district is “cyber ...
... and, likewise, a compromised or “hacked” network can prove very damaging. School administrators must take responsibility for making sure they understand the issues involved in securing computer networks and electronic data. Talk to your technology team and find out if your school district is “cyber ...
Chapter 1: Introduction to security
... • Information security services traditionally focused on confidentiality, integrity and authentication, but over the years the list has expanded to: ...
... • Information security services traditionally focused on confidentiality, integrity and authentication, but over the years the list has expanded to: ...