Introduction to Operating System
... clusters. Even a 512byte file uses 16K of space just to exist under FAT32 on a 64GB volume. That means FAT32 does not store data efficiently on larger volumes. ...
... clusters. Even a 512byte file uses 16K of space just to exist under FAT32 on a 64GB volume. That means FAT32 does not store data efficiently on larger volumes. ...
CS2254-QB
... 8) Is Os a resource Manager? If so justify your answer 9) What is the kernel? 10) What are the three main purposes of an operating system? 11) List the four steps that are necessary to run a program on a completely ...
... 8) Is Os a resource Manager? If so justify your answer 9) What is the kernel? 10) What are the three main purposes of an operating system? 11) List the four steps that are necessary to run a program on a completely ...
Slides
... There are none The best one can do is collect together a sequence of contiguous (or nearby) sectors for writing Write them in a single sequence of disk actions Caching for later writing is (usually) a bad idea Application has no confidence that data is actually written before a failure ...
... There are none The best one can do is collect together a sequence of contiguous (or nearby) sectors for writing Write them in a single sequence of disk actions Caching for later writing is (usually) a bad idea Application has no confidence that data is actually written before a failure ...
UNIX Operating System
... drives, tape drives, CD-ROM drives, printers, and scanners faster and more flexibly than previous interfaces. Developed at Apple Computer and still used in the Macintosh, the present set of SCSIs are parallel interfaces. SCSI ports continue to be built into many personal computers today and are supp ...
... drives, tape drives, CD-ROM drives, printers, and scanners faster and more flexibly than previous interfaces. Developed at Apple Computer and still used in the Macintosh, the present set of SCSIs are parallel interfaces. SCSI ports continue to be built into many personal computers today and are supp ...
File System
... Reliability can be a problem (a bug or disk failure might result in picking up a wrong pointer, which could result in corrupting other parts of the file system) ...
... Reliability can be a problem (a bug or disk failure might result in picking up a wrong pointer, which could result in corrupting other parts of the file system) ...
Windows Server 2008 - Dr. Edward E. Boas, Jr., Professor
... – Looks for orphaned files without names, bad directory pointers, inode problems, directories that do not exist, bad links, bad blocks, duplicated blocks, and pathname problems – If it finds problems – give the opportunity to fix or disregard ...
... – Looks for orphaned files without names, bad directory pointers, inode problems, directories that do not exist, bad links, bad blocks, duplicated blocks, and pathname problems – If it finds problems – give the opportunity to fix or disregard ...
Structuring of the Windows Operating System
... Debug Version (“Checked Build”) ! Special debug version of system called “Checked Build” ! Multiprocessor versions only (runs on UP systems) ! helps catch synchronization bugs that are more visible on MP systems ! Primarily for driver testing, but can be useful for catching timing bugs in m ...
... Debug Version (“Checked Build”) ! Special debug version of system called “Checked Build” ! Multiprocessor versions only (runs on UP systems) ! helps catch synchronization bugs that are more visible on MP systems ! Primarily for driver testing, but can be useful for catching timing bugs in m ...
AIX is building momentum as the leading, UNIX operating system for
... A file system is a hierarchical structure (file tree) of files and directories. This type of structure resembles an inverted tree with the roots at the top and branches at the bottom. This file tree uses directories to organize data and programs into groups, allowing the management of several direct ...
... A file system is a hierarchical structure (file tree) of files and directories. This type of structure resembles an inverted tree with the roots at the top and branches at the bottom. This file tree uses directories to organize data and programs into groups, allowing the management of several direct ...
File System Management
... The file system is used not only to store users’ programs and data, but also to support and represent significant portions of the operating system itself. Stallings introduces the traditional file system concepts of: fields represent the smallest logical item of data “understood” by a file-system: e ...
... The file system is used not only to store users’ programs and data, but also to support and represent significant portions of the operating system itself. Stallings introduces the traditional file system concepts of: fields represent the smallest logical item of data “understood” by a file-system: e ...
File System Maintenance (continued)
... – -d lists directories – -f displays files in an unsorted list – The remainder are listed on page 498 of the textbook ...
... – -d lists directories – -f displays files in an unsorted list – The remainder are listed on page 498 of the textbook ...
from Plan BeII Labs .
... to enable machines to access files on remote systems. Above this, we built a naming system that lets people and their computing agents build customized views of the resources in the network. This is where Plan 9 first began to look different: a Plan 9 user builds a private computing environment and ...
... to enable machines to access files on remote systems. Above this, we built a naming system that lets people and their computing agents build customized views of the resources in the network. This is where Plan 9 first began to look different: a Plan 9 user builds a private computing environment and ...
THE USER VIEW OF OPERATING SYSTEMS
... controlling and operating the system facilities. In this chapter, we take a closer look at the operating system from the perspective of service to the user. Much of the material in this chapter is at least superficially very familiar to you. You have worked closely with at least one type of computer ...
... controlling and operating the system facilities. In this chapter, we take a closer look at the operating system from the perspective of service to the user. Much of the material in this chapter is at least superficially very familiar to you. You have worked closely with at least one type of computer ...
Copyright © 2011 Pearson Education, Inc. Publishing as Prentice Hall
... Recommended that you use Windows ?? “Upgrade Advisor” – Can download this program. It scans your computer to see what software (and drivers for hardware) are on your computer and whether compatible with Win 7. – Then if software not compatible, you need to research it to find its update -- or uninst ...
... Recommended that you use Windows ?? “Upgrade Advisor” – Can download this program. It scans your computer to see what software (and drivers for hardware) are on your computer and whether compatible with Win 7. – Then if software not compatible, you need to research it to find its update -- or uninst ...
Chapter 9: File-System Interface
... Directory implement unified access to information needed for remote computing ...
... Directory implement unified access to information needed for remote computing ...
Embedding Object Files in an Existing Operating System: A Practical Approach
... Then the original text file would be realized by the applicationPath attribute in order to be sent to the supported applications such as MS Word or Notepad. We manipulated and modified the extracted Object File (original text file) using an application, then saved it. The modified file was stored as ...
... Then the original text file would be realized by the applicationPath attribute in order to be sent to the supported applications such as MS Word or Notepad. We manipulated and modified the extracted Object File (original text file) using an application, then saved it. The modified file was stored as ...
File Systems
... – Unix mount system call does this • mounting does not make two file systems into one file system – it merely creates a single, hierarchical namespace that combines the namespaces of two file systems – the new namespace is temporary - it exists only until the file system is ...
... – Unix mount system call does this • mounting does not make two file systems into one file system – it merely creates a single, hierarchical namespace that combines the namespaces of two file systems – the new namespace is temporary - it exists only until the file system is ...
Windows 95/98/NT (Introduction)
... • IFS (Installable File System) Manager. This is the arbiter for the access to different file system components. On MS-DOS and Windows 3.x it was provided by interrupt 21h. Unfortunately, some add-on components did not run correctly and interfered with other installed drivers. It also did not direct ...
... • IFS (Installable File System) Manager. This is the arbiter for the access to different file system components. On MS-DOS and Windows 3.x it was provided by interrupt 21h. Unfortunately, some add-on components did not run correctly and interfered with other installed drivers. It also did not direct ...
Plan 9 from Bell Labs
... cons files for the window as usual in /dev; it does not know whether the files are local. It just reads and writes them to control the window; the network connection is already there and multiplexed. The intended style of use is to run interactive applications such as the window sys tem and text ed ...
... cons files for the window as usual in /dev; it does not know whether the files are local. It just reads and writes them to control the window; the network connection is already there and multiplexed. The intended style of use is to run interactive applications such as the window sys tem and text ed ...
Operating System Services
... memory and to run that program, end execution, either normally or abnormally (indicating error) ...
... memory and to run that program, end execution, either normally or abnormally (indicating error) ...
Slide 1
... that are important to understand. Which of the following statements is correct? A. iOS is built on the Windows kernel, so it is ideal for smartphones because it has good resistance to malware. B. If you don’t like the user interface for Windows but want to run the vast variety of Windows softwar ...
... that are important to understand. Which of the following statements is correct? A. iOS is built on the Windows kernel, so it is ideal for smartphones because it has good resistance to malware. B. If you don’t like the user interface for Windows but want to run the vast variety of Windows softwar ...
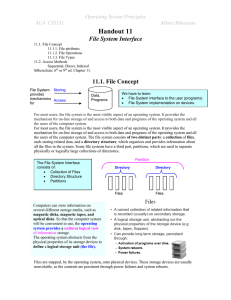
H 10.1. File-System Interface
... A common technique for implementing file types is to include the type as part of the file name. The name is split into two parts-a name and an extension, usually separated by a period character. In this way, the user and the operating system can tell from the name alone what the type of a file is. F ...
... A common technique for implementing file types is to include the type as part of the file name. The name is split into two parts-a name and an extension, usually separated by a period character. In this way, the user and the operating system can tell from the name alone what the type of a file is. F ...