Document
... Recommended that you use Windows 7 Upgrade advisor – Can download this program. It scans your computer to see what software (and drivers for hardware) are on your computer and whether compatible with Win 7. – Then if software not compatible, you need to research it to find its update -- or uninstall ...
... Recommended that you use Windows 7 Upgrade advisor – Can download this program. It scans your computer to see what software (and drivers for hardware) are on your computer and whether compatible with Win 7. – Then if software not compatible, you need to research it to find its update -- or uninstall ...
Operating Systems and File Management
... contains your computer’s current settings and device drivers • Norton Ghost is a product of Symantec, which also provides a more specialized recovery disk called the Symantec Recovery Disk ...
... contains your computer’s current settings and device drivers • Norton Ghost is a product of Symantec, which also provides a more specialized recovery disk called the Symantec Recovery Disk ...
INTRODUCTION TO THE STUDY OF CONSUMER BEHAVIOUR
... Because high-end networked computers fall into two primary categories, Microsoft separated Windows NT into two products: Windows NT Workstation and the first Windows version for network servers, Windows NT Server. The server product was optimized to run on dedicated network servers. Although Windows ...
... Because high-end networked computers fall into two primary categories, Microsoft separated Windows NT into two products: Windows NT Workstation and the first Windows version for network servers, Windows NT Server. The server product was optimized to run on dedicated network servers. Although Windows ...
Presentation - Virtual Office
... – Keep a manageable number of directories in the root directory – Keep operating system files in the default directories recommended by the vendor – Keep different versions of software in their own directories – Keep data files in directories on the basis of their functions – Design home directories ...
... – Keep a manageable number of directories in the root directory – Keep operating system files in the default directories recommended by the vendor – Keep different versions of software in their own directories – Keep data files in directories on the basis of their functions – Design home directories ...
operating system
... mode kernel and virtual machine monitor. For the duration of a Windows session, it created one or more virtual 8086 environments and provided device virtualization for the video card, keyboard, mouse, timer and interrupt controller inside each of them. The user-visible consequence was that it be ...
... mode kernel and virtual machine monitor. For the duration of a Windows session, it created one or more virtual 8086 environments and provided device virtualization for the video card, keyboard, mouse, timer and interrupt controller inside each of them. The user-visible consequence was that it be ...
Windows
... – Special kit only for vendors that must write custom HALs – requires approval from Microsoft – see http://www.microsoft.com/whdc/ddk/HALkit/default.mspx ...
... – Special kit only for vendors that must write custom HALs – requires approval from Microsoft – see http://www.microsoft.com/whdc/ddk/HALkit/default.mspx ...
2-OS
... – 64-bit OS requires that device drivers operating in kernel mode be 64-bit drivers – Application is compiled to process 64 bits or 32 bits – 32-bit OS can only address up to 4 GB of memory – Benefit from 64-bit computing if: • Many applications open at the same time • You have high computing needs ...
... – 64-bit OS requires that device drivers operating in kernel mode be 64-bit drivers – Application is compiled to process 64 bits or 32 bits – 32-bit OS can only address up to 4 GB of memory – Benefit from 64-bit computing if: • Many applications open at the same time • You have high computing needs ...
Operating System Security
... Sticky Bit in Unix Sticky Bit: Mainly used to avoid some other user deleting a file though she has a write permission on the folder If Sticky bit is enabled on a folder, the folder contents are deleted by only owner who created them and the root user. This is a security measure to avoid delet ...
... Sticky Bit in Unix Sticky Bit: Mainly used to avoid some other user deleting a file though she has a write permission on the folder If Sticky bit is enabled on a folder, the folder contents are deleted by only owner who created them and the root user. This is a security measure to avoid delet ...
Processes in Unix, Linux, and Windows
... Linux Kernel Implementation • Kernel may execute in either Process context vs. Interrupt context • In Process context, kernel has access to • Virtual memory, files, other process resources • May sleep, take page faults, etc., on behalf of process ...
... Linux Kernel Implementation • Kernel may execute in either Process context vs. Interrupt context • In Process context, kernel has access to • Virtual memory, files, other process resources • May sleep, take page faults, etc., on behalf of process ...
Lecture 6 File Systems
... • Different users may need different types of access to a file or directory. • The most general scheme to implement identity-dependent access is to associate with each file and directory an Access-Control List (ACL) specifying user names and the types of access allowed for each user. ...
... • Different users may need different types of access to a file or directory. • The most general scheme to implement identity-dependent access is to associate with each file and directory an Access-Control List (ACL) specifying user names and the types of access allowed for each user. ...
The Fallacy of Software Write Protection in Computer Forensics
... standard Windows boot up? Most people are not aware that data may be written to a drive during the boot process. If any changes gets through, your evidence is now questionable. With the complexity of today’s operating systems, you just can’t tell how many programs will load during the boot sequence. ...
... standard Windows boot up? Most people are not aware that data may be written to a drive during the boot process. If any changes gets through, your evidence is now questionable. With the complexity of today’s operating systems, you just can’t tell how many programs will load during the boot sequence. ...
Blue Background
... The shell provides an interface between the kernel and the user. It can be described as an interpreter. It interprets commands entered by the user and sends them to the kernel. There are two cateories of Shells: Command Line Grafical User Interface (GUI) - GUI's have many window managers (fvwm, ...
... The shell provides an interface between the kernel and the user. It can be described as an interpreter. It interprets commands entered by the user and sends them to the kernel. There are two cateories of Shells: Command Line Grafical User Interface (GUI) - GUI's have many window managers (fvwm, ...
A+ Guide to Managing and Maintaining your PC, 6e
... • OS functions: providing a user interface, managing files, managing applications, and managing hardware • Windows desktop: primary graphical interface to OS • Windows Explorer: used to navigate directory and manipulate files and folders ...
... • OS functions: providing a user interface, managing files, managing applications, and managing hardware • Windows desktop: primary graphical interface to OS • Windows Explorer: used to navigate directory and manipulate files and folders ...
Copyright © 2011 Pearson Education, Inc. Publishing as Prentice Hall
... BIOS - Basic Input Output System ...
... BIOS - Basic Input Output System ...
Ceng 334 - Operating Systems
... Nice is a value between –20 to 20 (default 0). Nice system call can be used to set this value 0-20 Base is a system parameter in UNIX source code The scheduler forces CPU bound (on positive queues) get any service that is left over when all I/O bound and interactive processes are blocked ...
... Nice is a value between –20 to 20 (default 0). Nice system call can be used to set this value 0-20 Base is a system parameter in UNIX source code The scheduler forces CPU bound (on positive queues) get any service that is left over when all I/O bound and interactive processes are blocked ...
PDF
... installation. The utility helps you reduce the overall time required to set up your servers. USC-SCU is intended for system administrators responsible for upgrading, troubleshooting, and configuring the configuration utility. As a system administrator, you can use it to update a server with the most ...
... installation. The utility helps you reduce the overall time required to set up your servers. USC-SCU is intended for system administrators responsible for upgrading, troubleshooting, and configuring the configuration utility. As a system administrator, you can use it to update a server with the most ...
BIOS Startup Firmware
... OS. In the meantime, the basic functionality in the SMMbased applications continues to remain available, increasing the system’s overall availability. One way to provide such monitoring is for the system developer to create a list of sensitive software objects such as CMOS settings and key files on ...
... OS. In the meantime, the basic functionality in the SMMbased applications continues to remain available, increasing the system’s overall availability. One way to provide such monitoring is for the system developer to create a list of sensitive software objects such as CMOS settings and key files on ...
PDF.
... be handed to the VM. After the VM passes through BIOS that detects some of the available hardware, specially bootable storage, the appropriate bootloader starts. After a configurable timeout, the OS kernel is loaded into memory, and starts initialization of various devices such as cores, memory, dis ...
... be handed to the VM. After the VM passes through BIOS that detects some of the available hardware, specially bootable storage, the appropriate bootloader starts. After a configurable timeout, the OS kernel is loaded into memory, and starts initialization of various devices such as cores, memory, dis ...
The Styx Architecture for Distributed Systems
... bootstrapping is done by copying the control software for the card into the memory file and writing a reset message to ctl. Once the line card is running, the other files present an interface to the higher-level structure of the device: pack is the port through which IP packets are transferred to an ...
... bootstrapping is done by copying the control software for the card into the memory file and writing a reset message to ctl. Once the line card is running, the other files present an interface to the higher-level structure of the device: pack is the port through which IP packets are transferred to an ...
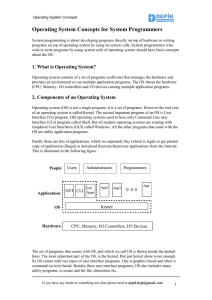
Operating System Concepts for System Programmers
... program will match with this start address. The BIOS program initializes various I/O controllers and I/O devices. Finally it identifies the boot device (as stored in battery backup memory (CMOS memory)). Typical boot devices are floppy, Hard disk, CD, USB flash stick and finally Network. The BIOS pr ...
... program will match with this start address. The BIOS program initializes various I/O controllers and I/O devices. Finally it identifies the boot device (as stored in battery backup memory (CMOS memory)). Typical boot devices are floppy, Hard disk, CD, USB flash stick and finally Network. The BIOS pr ...
H 10.3. File-System Interface
... /home, as in /home/jane. Mounting that file system under /users would result in the path name /users/jane to reach the same directory. To illustrate file mounting, consider the file system depicted in Figure below, where the triangles represent subtrees of directories that are of interest. In Figure ...
... /home, as in /home/jane. Mounting that file system under /users would result in the path name /users/jane to reach the same directory. To illustrate file mounting, consider the file system depicted in Figure below, where the triangles represent subtrees of directories that are of interest. In Figure ...
CHAPTER 1 Concepts and Tools n this chapter, we`ll introduce the
... Interestingly, Win32 wasn’t slated to be the original programming interface to what was then called Windows NT. Because the Windows NT project started as a replacement for OS/2 version 2, the primary programming interface was the 32-bit OS/2 Presentation Manager API. A year into the project, however ...
... Interestingly, Win32 wasn’t slated to be the original programming interface to what was then called Windows NT. Because the Windows NT project started as a replacement for OS/2 version 2, the primary programming interface was the 32-bit OS/2 Presentation Manager API. A year into the project, however ...