parallel multilevel preconditioners
... In this paper, we provide techniques for the development and analysis of parallel multilevel preconditioners for the discrete systems which arise in numerical approximation of symmetric elliptic boundary value problems. These preconditioners are defined as a sum of independent operators on a sequenc ...
... In this paper, we provide techniques for the development and analysis of parallel multilevel preconditioners for the discrete systems which arise in numerical approximation of symmetric elliptic boundary value problems. These preconditioners are defined as a sum of independent operators on a sequenc ...
Genetic algorithm, particle swarm optimization and hybrid scheme
... use the artificial intelligence techniques to solve the problem of shipping route planning in restricted waters. In current literature, a large number of artificial intelligence methods have attracted increasing attention due to their great potential for solving complex real-world problems, such as ...
... use the artificial intelligence techniques to solve the problem of shipping route planning in restricted waters. In current literature, a large number of artificial intelligence methods have attracted increasing attention due to their great potential for solving complex real-world problems, such as ...
Streaming algorithms for embedding and computing edit distance in
... for computing the edit distance of a string of parenthesis of various types from the set of well parenthesized expressions. The main idea of the algorithm presented in [Sah14] is to process the string left to right, push opening parenthesis on a stack and match them against closing parenthesis. When ...
... for computing the edit distance of a string of parenthesis of various types from the set of well parenthesized expressions. The main idea of the algorithm presented in [Sah14] is to process the string left to right, push opening parenthesis on a stack and match them against closing parenthesis. When ...
Counting Inversions, Offline Orthogonal Range Counting, and Related Problems Timothy M. Chan
... of improved algorithms and data structures. sense to look at the preprocessing time more carefully. Unfortunately, it is not known how to construct a Offline orthogonal range counting. A slightly data structure with optimal query performance in linear trickier version (Section 2.2) of our initial√ a ...
... of improved algorithms and data structures. sense to look at the preprocessing time more carefully. Unfortunately, it is not known how to construct a Offline orthogonal range counting. A slightly data structure with optimal query performance in linear trickier version (Section 2.2) of our initial√ a ...
E - Read
... The challenge for designing randomized algorithms are usually in (asymptotic) analysis for (time and space) complexity. ...
... The challenge for designing randomized algorithms are usually in (asymptotic) analysis for (time and space) complexity. ...
3. Keyword Cover Search Module
... dimension. Objects close to each other geographically may have very different ratings and thus they are in different nodes of KRR*-tree. If more weight is assigned to keyword ratings, KRR*-tree tends to have more pruning power by distinguishing the objects close to each other but with different key ...
... dimension. Objects close to each other geographically may have very different ratings and thus they are in different nodes of KRR*-tree. If more weight is assigned to keyword ratings, KRR*-tree tends to have more pruning power by distinguishing the objects close to each other but with different key ...
Lecture Notes for Algorithm Analysis and Design
... insecurity among many students who are not adept at writing down notes as well as participating in class discussions so important for a course like algorithms. (As a corollary, this may make it easier for some of the students to skip some lectures.) (iv) Gives me some flexibility about asking studen ...
... insecurity among many students who are not adept at writing down notes as well as participating in class discussions so important for a course like algorithms. (As a corollary, this may make it easier for some of the students to skip some lectures.) (iv) Gives me some flexibility about asking studen ...
An Improved Ant Colony Optimisation Algorithm for the 2D HP
... as well as by a shared memory containing experience gathered by the ants in previous iterations (“pheromone trails”). Following the seminal work by Dorigo et al. [5], ACO algorithms have been successfully applied to a broad range of hard combinatorial problems (see, e.g., [6, 7]). In this paper, we ...
... as well as by a shared memory containing experience gathered by the ants in previous iterations (“pheromone trails”). Following the seminal work by Dorigo et al. [5], ACO algorithms have been successfully applied to a broad range of hard combinatorial problems (see, e.g., [6, 7]). In this paper, we ...
Data-Oblivious Data Structures
... is the size of the input (or the capacity of the data structure, as appropriate), and the entire memory consists of poly(n) words.1 The RAM has a constant number of public and secret registers, and can perform arbitrary operations (of circuit size poly(log n)) on a constant number of registers in co ...
... is the size of the input (or the capacity of the data structure, as appropriate), and the entire memory consists of poly(n) words.1 The RAM has a constant number of public and secret registers, and can perform arbitrary operations (of circuit size poly(log n)) on a constant number of registers in co ...
Shortest Paths in Directed Planar Graphs with Negative Lengths: a
... Intra-part boundary-distances:. For each graph Gi we use a method due to Klein [2005] to compute all distances in Gi between boundary nodes. This takes O(n log n) time. Single-source inter-part boundary distances:. A shortest path in G passes back and forth between G0 and G1 . Refer to Fig. 1 and F ...
... Intra-part boundary-distances:. For each graph Gi we use a method due to Klein [2005] to compute all distances in Gi between boundary nodes. This takes O(n log n) time. Single-source inter-part boundary distances:. A shortest path in G passes back and forth between G0 and G1 . Refer to Fig. 1 and F ...
6.896 Project Presentations
... Design and implement a dynamic processorallocation system for adaptively parallel jobs (jobs for which the number of processors that can be used without waste varies during execution) The problem of allocating processors to adaptively parallel jobs is called the adaptively parallel processor-allocat ...
... Design and implement a dynamic processorallocation system for adaptively parallel jobs (jobs for which the number of processors that can be used without waste varies during execution) The problem of allocating processors to adaptively parallel jobs is called the adaptively parallel processor-allocat ...
Introduction to Computer Science
... An informal definition No generally accepted formal definition of algorithm exists yet. As the term is popularly understood, algorithm mean the way of doing sth, recipe for sth or formula for sth. More formal definition In mathematic and computer science, algorithm mean finite, ordered sequence of c ...
... An informal definition No generally accepted formal definition of algorithm exists yet. As the term is popularly understood, algorithm mean the way of doing sth, recipe for sth or formula for sth. More formal definition In mathematic and computer science, algorithm mean finite, ordered sequence of c ...
Optimal Resource Allocation for MIMO Ad Hoc Cognitive Radio
... Although the focus of this paper is on any-to-any CR networks, problems similar to (P1) arise naturally when applying dual decomposition to a cross-layer network optimization play the role of Lagrange problem, where the weights multipliers associated with the physical layer link capacity constraints ...
... Although the focus of this paper is on any-to-any CR networks, problems similar to (P1) arise naturally when applying dual decomposition to a cross-layer network optimization play the role of Lagrange problem, where the weights multipliers associated with the physical layer link capacity constraints ...
Algorithms for Manipulating Algebraic Functions
... the field k[x]/(f (x)). Therefore k[α] is isomorphic to k[A] under an isomorphism which maps α to A. We now have two alternative representations for elements of k(α), either as polynomials in α reduced modulo the minimal polynomial, fα (x), or as n × n matrices in k[A]. Most previous references to a ...
... the field k[x]/(f (x)). Therefore k[α] is isomorphic to k[A] under an isomorphism which maps α to A. We now have two alternative representations for elements of k(α), either as polynomials in α reduced modulo the minimal polynomial, fα (x), or as n × n matrices in k[A]. Most previous references to a ...
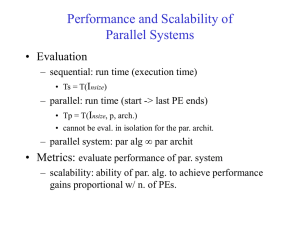
Performance and Scalability of Parallel Systems
... Problem size should grow at least as plogp s.t. parallel algorithm is scalable. ...
... Problem size should grow at least as plogp s.t. parallel algorithm is scalable. ...
On the Complexity of Fixed-Size Bit
... explicit bit-width belongs to bit-vector operators, and, therefore, the bit-width of a compound term is implicit, i.e., can be calculated. Let t[n] denote the fact that the bit-vector term t is of bit-width n. We even omit an explicit bit-width if it can be deduced from the context. In our proofs we ...
... explicit bit-width belongs to bit-vector operators, and, therefore, the bit-width of a compound term is implicit, i.e., can be calculated. Let t[n] denote the fact that the bit-vector term t is of bit-width n. We even omit an explicit bit-width if it can be deduced from the context. In our proofs we ...
Reference Point Based Multi-objective Optimization Through
... regions on Pareto-optimal front which are of interest to the decision maker. Since it is difficult for the decision makers to determine the weight of each objective directly, instead, they provide a maximum acceptable trade-off between each objective pair. The definition of dominance is modified acc ...
... regions on Pareto-optimal front which are of interest to the decision maker. Since it is difficult for the decision makers to determine the weight of each objective directly, instead, they provide a maximum acceptable trade-off between each objective pair. The definition of dominance is modified acc ...
Clusterpath: An Algorithm for Clustering using Convex
... Thus the simple FLSA algorithm of complexity O(n log n) without split checks is sufficient to calculate the `1 clusterpath for 1 dimension using the identity weights. Furthermore, since the clusterpath is strictly agglomerative on each dimension, it is also strictly agglomerative when independently ...
... Thus the simple FLSA algorithm of complexity O(n log n) without split checks is sufficient to calculate the `1 clusterpath for 1 dimension using the identity weights. Furthermore, since the clusterpath is strictly agglomerative on each dimension, it is also strictly agglomerative when independently ...