2_threads
... – If M[address]==reg1 sets M[address]=reg2 and returns success, otherwise returns failure ...
... – If M[address]==reg1 sets M[address]=reg2 and returns success, otherwise returns failure ...
Introduction
... All I/O instructions are privileged instructions I/O devices and CPU can execute concurrently CPU moves data between main memory and device controllers' buffers (done by device drivers) Device controllers interrupt upon completion Interrupts or Traps enable mode switching Operating syste ...
... All I/O instructions are privileged instructions I/O devices and CPU can execute concurrently CPU moves data between main memory and device controllers' buffers (done by device drivers) Device controllers interrupt upon completion Interrupts or Traps enable mode switching Operating syste ...
Operating Systems, 082
... All I/O instructions are privileged instructions I/O devices and CPU can execute concurrently CPU moves data between main memory and device controllers' buffers (done by device drivers) Device controllers interrupt upon completion Interrupts or Traps enable mode switching Operating syste ...
... All I/O instructions are privileged instructions I/O devices and CPU can execute concurrently CPU moves data between main memory and device controllers' buffers (done by device drivers) Device controllers interrupt upon completion Interrupts or Traps enable mode switching Operating syste ...
INF 5070 – Media Storage and Distribution Systems
... priority – high priority tasks should not suffer from low priority tasks proportional sharing – allocate resources proportionally and distribute unused resources (work conserving) tradeoff immediate fairness – less competitive processes (short-lived, interactive, I/O-bound, ...) get a higher s ...
... priority – high priority tasks should not suffer from low priority tasks proportional sharing – allocate resources proportionally and distribute unused resources (work conserving) tradeoff immediate fairness – less competitive processes (short-lived, interactive, I/O-bound, ...) get a higher s ...
Interrupts and Exceptions
... Interrupt: a change in execution caused by an external event devices: disk, network, keyboard, etc. clock for timesharing (multitasking) ...
... Interrupt: a change in execution caused by an external event devices: disk, network, keyboard, etc. clock for timesharing (multitasking) ...
Figure 5.01
... Increased responsiveness to user: A program continues running with other threads even if part of it is blocked or performing a lengthy operation in one thread. Resource Sharing Threads share memory and resources of their process. Economy Less time consuming to create and manage threads t ...
... Increased responsiveness to user: A program continues running with other threads even if part of it is blocked or performing a lengthy operation in one thread. Resource Sharing Threads share memory and resources of their process. Economy Less time consuming to create and manage threads t ...
Slides
... – It is raised by one process (or hardware) to call another process’s attention to an event – It can be caught (or ignored) by the subject process ...
... – It is raised by one process (or hardware) to call another process’s attention to an event – It can be caught (or ignored) by the subject process ...
CS350-03a-procs+threads
... unit of execution within a process (often called a lightweight process – an "lwp") also called a "task" Share address space, data and devices with other threads within the process Private stack, status (IC, state, etc) ...
... unit of execution within a process (often called a lightweight process – an "lwp") also called a "task" Share address space, data and devices with other threads within the process Private stack, status (IC, state, etc) ...
Lecture 1: Course Introduction and Overview
... » Everyone in group must have logged into their cs162-xx accounts once before you register the group, Select at least 3 potential sections ...
... » Everyone in group must have logged into their cs162-xx accounts once before you register the group, Select at least 3 potential sections ...
Figure 5.01
... application may allow a program to continue running even if part of it is blocked or is performing a length operation, thereby increasing responsiveness to the user. For example, a multithreaded Web browser could allow user interaction in one thread while an image was being loaded in another thread. ...
... application may allow a program to continue running even if part of it is blocked or is performing a length operation, thereby increasing responsiveness to the user. For example, a multithreaded Web browser could allow user interaction in one thread while an image was being loaded in another thread. ...
Chapter 1 – 15 Essay Question Review
... operations (i.e., cache, random access memory, etc.). Virtual memory is a method through which programs can be executed that requires space larger than that available in physical memory by using disk memory as a backing store for main memory. Logical memory is an abstraction of the computer’s differ ...
... operations (i.e., cache, random access memory, etc.). Virtual memory is a method through which programs can be executed that requires space larger than that available in physical memory by using disk memory as a backing store for main memory. Logical memory is an abstraction of the computer’s differ ...
Chapter 1
... Program counter: next instruction to fetch Stack pointer: the top of the current stack PSW: program status word, priority, mode… ...
... Program counter: next instruction to fetch Stack pointer: the top of the current stack PSW: program status word, priority, mode… ...
Chapter 3 - reduced
... Zombie: when a child process terminates, its association with its parent survives until parent terminates or calls wait, then the child process entry remains in the process table as a defunct or zombie process If parent terminated without invoking wait , child process is an orphan ...
... Zombie: when a child process terminates, its association with its parent survives until parent terminates or calls wait, then the child process entry remains in the process table as a defunct or zombie process If parent terminated without invoking wait , child process is an orphan ...
PPT
... Linux refers to them as tasks rather than threads Thread creation is done through clone() system call clone() allows a child task to share the address space ...
... Linux refers to them as tasks rather than threads Thread creation is done through clone() system call clone() allows a child task to share the address space ...
developing a saas-cloud integrated development environment (ide)
... application that runs as a desktop. The characteristics of cloud computing changed the paradigm of application usage. Users do not need to install various types of applications, only need to install a browser on a computer connected to the internet and can use applications. This leads to minimize th ...
... application that runs as a desktop. The characteristics of cloud computing changed the paradigm of application usage. Users do not need to install various types of applications, only need to install a browser on a computer connected to the internet and can use applications. This leads to minimize th ...
xv6 - PDOS-MIT
... and to provide a more useful set of services than the hardware alone supports. The operating system manages and abstracts the low-level hardware, so that, for example, a word processor need not concern itself with which type of disk hardware is being used. It also multiplexes the hardware, allowing ...
... and to provide a more useful set of services than the hardware alone supports. The operating system manages and abstracts the low-level hardware, so that, for example, a word processor need not concern itself with which type of disk hardware is being used. It also multiplexes the hardware, allowing ...
Chapter 6: Process/thread Synchronization
... Could now have busy waiting in critical section implementation" ! But ...
... Could now have busy waiting in critical section implementation" ! But ...
operating system functions
... unauthorized access to file, by the external code or user. Elimination of duplicate effects: Once the as developers write the routines for all the I/O operation each application programmer does not have to code them again & again. They’re by the programmers. When the application program writes “Read ...
... unauthorized access to file, by the external code or user. Elimination of duplicate effects: Once the as developers write the routines for all the I/O operation each application programmer does not have to code them again & again. They’re by the programmers. When the application program writes “Read ...
Desktop Scheduling: How Can We Know What the
... Only a subset of the peripheral devices in the system are of interest when trying to quantify the volume of interactions between the user and the various processes. These include the keyboard, mouse, screen, joystick, sound card, etc., and will be referred to collectively as HuC devices. The common ...
... Only a subset of the peripheral devices in the system are of interest when trying to quantify the volume of interactions between the user and the various processes. These include the keyboard, mouse, screen, joystick, sound card, etc., and will be referred to collectively as HuC devices. The common ...
Homework Assignment 1 Practice the following questions based on
... appropriate arguments. The advantage of the first method is speed and overall simplicity. The disadvantage to this technique is that new commands require rewriting the interpreter program which, after a number of modifications, may get complicated, messy, or too large. The advantage to the second me ...
... appropriate arguments. The advantage of the first method is speed and overall simplicity. The disadvantage to this technique is that new commands require rewriting the interpreter program which, after a number of modifications, may get complicated, messy, or too large. The advantage to the second me ...
Figure 5.01 - Texas A&M University
... A default signal handler that is run by the kernel when handling that signal. ...
... A default signal handler that is run by the kernel when handling that signal. ...
Desktop scheduling: how can we know what the user wants?
... Only a subset of the peripheral devices in the system are of interest when trying to quantify the volume of interactions between the user and the various processes. These include the keyboard, mouse, screen, joystick, sound card, etc., and will be referred to collectively as HuC devices. The common ...
... Only a subset of the peripheral devices in the system are of interest when trying to quantify the volume of interactions between the user and the various processes. These include the keyboard, mouse, screen, joystick, sound card, etc., and will be referred to collectively as HuC devices. The common ...
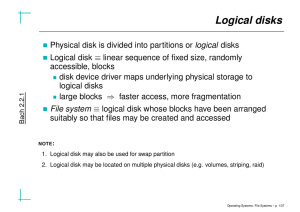
File Systems
... of device being unmounted; release inode of special file. 3. Get mount table entry, based on major/minor #. 4. Check whether files on the f.s. are still in use: 4.1 search inode table for all files whose dev. # matches the f.s. to be unmounted; 4.2 if any such file has ref. count > 0 (current direct ...
... of device being unmounted; release inode of special file. 3. Get mount table entry, based on major/minor #. 4. Check whether files on the f.s. are still in use: 4.1 search inode table for all files whose dev. # matches the f.s. to be unmounted; 4.2 if any such file has ref. count > 0 (current direct ...
Module 6: CPU Scheduling - University of South Florida
... 1. t n actual length of n th CPU burst 2. n 1 predicted value for the next CPU burst ...
... 1. t n actual length of n th CPU burst 2. n 1 predicted value for the next CPU burst ...