Java Threads
... n Linux refers to them as tasks rather than threads. n Thread creation is done through clone() system call. n Clone() allows a child task to share the address space of ...
... n Linux refers to them as tasks rather than threads. n Thread creation is done through clone() system call. n Clone() allows a child task to share the address space of ...
OS REVIEW
... WebOS is a mobile operating system that runs on the Linux kernel. WebOS was initially developed by Palm as the successor to its Palm OS mobile operating system. It is a proprietary Mobile OS which was eventually acquired by HP and now referred to as webOS (lower-case w) in HP literature. HP uses web ...
... WebOS is a mobile operating system that runs on the Linux kernel. WebOS was initially developed by Palm as the successor to its Palm OS mobile operating system. It is a proprietary Mobile OS which was eventually acquired by HP and now referred to as webOS (lower-case w) in HP literature. HP uses web ...
Micro-CernVM: Slashing the Cost of Building and
... /.ucernvm_bootstrap This is a shell script provided by the operating system repository. It is sourced just before the root file system is switched and allows for custom actions. Special care has to be taken in the shutdown script of the operating system. Typically, the shutdown script does not expe ...
... /.ucernvm_bootstrap This is a shell script provided by the operating system repository. It is sourced just before the root file system is switched and allows for custom actions. Special care has to be taken in the shutdown script of the operating system. Typically, the shutdown script does not expe ...
Understanding Computers, 10/e, Chapter 6
... Disk management programs—diagnose and repair problems related to the hard drive. Disk defragmentation programs rearrange the files on a hard drive to store them in contiguous locations to speed up performance. ...
... Disk management programs—diagnose and repair problems related to the hard drive. Disk defragmentation programs rearrange the files on a hard drive to store them in contiguous locations to speed up performance. ...
Chapter I Introduction
... • Prevents programs from accessing any memory location outside their own address space • Requires special memory protection hardware – Memory Management Unit (MMU) • Memory protection hardware – Checks every reference issued by program – Generates an interrupt when it detects a protection violation ...
... • Prevents programs from accessing any memory location outside their own address space • Requires special memory protection hardware – Memory Management Unit (MMU) • Memory protection hardware – Checks every reference issued by program – Generates an interrupt when it detects a protection violation ...
LSD1518 - Control Cloud Data Access Privilege
... Cloud computing is a revolutionary computing paradigm, which enables flexible, on-demand, and low-cost usage of computing resources, but the data is outsourced to some cloud servers, and various privacy concerns emerge from it. Various schemes based on the attribute-based encryption have been propos ...
... Cloud computing is a revolutionary computing paradigm, which enables flexible, on-demand, and low-cost usage of computing resources, but the data is outsourced to some cloud servers, and various privacy concerns emerge from it. Various schemes based on the attribute-based encryption have been propos ...
Basic System and Application Software_LAS
... educational packages that they offer, which involve a whole course or lessons bundled together on a particular subject with tests and other materials. We can view this software as ‘computer-formatted’ classroom software that allows an individual to gain learning experience without being physically p ...
... educational packages that they offer, which involve a whole course or lessons bundled together on a particular subject with tests and other materials. We can view this software as ‘computer-formatted’ classroom software that allows an individual to gain learning experience without being physically p ...
OS-DS-Arch
... while coexisting with a non-real-time application such as web browsing. That is kernel would provide only the most basic mechanisms upon which the general resource management tasks at a node are carried out. Server modules would be dynamically loaded as required, to implement the required RM policie ...
... while coexisting with a non-real-time application such as web browsing. That is kernel would provide only the most basic mechanisms upon which the general resource management tasks at a node are carried out. Server modules would be dynamically loaded as required, to implement the required RM policie ...
Chapter 1. Introduction to Data Communications
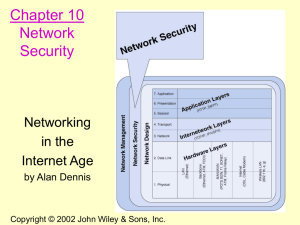
... • The limits of what users have access to on a network are determined by user profiles assigned to each user account by the net manager. • The profile specifies access details such as what data and network resources a user can access and the type of access (e.g., read, write, create, delete). • Most ...
... • The limits of what users have access to on a network are determined by user profiles assigned to each user account by the net manager. • The profile specifies access details such as what data and network resources a user can access and the type of access (e.g., read, write, create, delete). • Most ...
PPT - Surendar Chandra
... Designing an Operating Systems Goal is to understand how the technologies that we studied so far apply to typical machines First we focus on PDAs and Laptops Both are mobile, inexpensive Battery is a big concern ...
... Designing an Operating Systems Goal is to understand how the technologies that we studied so far apply to typical machines First we focus on PDAs and Laptops Both are mobile, inexpensive Battery is a big concern ...
slides
... • A virtual machine takes the layered approach to its logical conclusion. It treats hardware and the operating system kernel as though they were all hardware. • A virtual machine provides an interface identical to the underlying bare hardware. • The operating system creates the illusion of multiple ...
... • A virtual machine takes the layered approach to its logical conclusion. It treats hardware and the operating system kernel as though they were all hardware. • A virtual machine provides an interface identical to the underlying bare hardware. • The operating system creates the illusion of multiple ...
Cutting Edge VoIP Security Issues Color
... If you know or can guess the name of a configuration or firmware file, you can download it without even specifying a password The files are downloaded in the clear and can be easily sniffed Configuration files have usernames, passwords, IP addresses, etc. in them ...
... If you know or can guess the name of a configuration or firmware file, you can download it without even specifying a password The files are downloaded in the clear and can be easily sniffed Configuration files have usernames, passwords, IP addresses, etc. in them ...
Security and Ethical Challenges
... of legal principles derived from issues that had nothing to do with cyberspace ...
... of legal principles derived from issues that had nothing to do with cyberspace ...
No Slide Title
... 1991 by Linus Torvalds, with the major design goal of UNIX compatibility. Its history has been one of collaboration by many users from all around the world, corresponding almost exclusively over the Internet. It has been designed to run efficiently and reliably on common PC hardware, but also runs o ...
... 1991 by Linus Torvalds, with the major design goal of UNIX compatibility. Its history has been one of collaboration by many users from all around the world, corresponding almost exclusively over the Internet. It has been designed to run efficiently and reliably on common PC hardware, but also runs o ...
1. Introduction about operating system. 2. What is 32 bit
... Type your product key in the text-box and click Next. You can also skip this step and simply click Next if you want to type the product key later. Windows will run only for 30 days if you do that. ...
... Type your product key in the text-box and click Next. You can also skip this step and simply click Next if you want to type the product key later. Windows will run only for 30 days if you do that. ...
Booting process is in progress
... Type your product key in the text-box and click Next. You can also skip this step and simply click Next if you want to type the product key later. Windows will run only for 30 days if you do that. ...
... Type your product key in the text-box and click Next. You can also skip this step and simply click Next if you want to type the product key later. Windows will run only for 30 days if you do that. ...
Embedded And Real
... Virtually all kinds of computing systems Temporal determinism Time required to process any task is finite and predictable Less concerned with average response time than worst-case response time Must have a guarantee on the upper time limit ...
... Virtually all kinds of computing systems Temporal determinism Time required to process any task is finite and predictable Less concerned with average response time than worst-case response time Must have a guarantee on the upper time limit ...
S - FSU Computer Science Department
... Therefore users are placed in groups, and derive access from a user’s group. ...
... Therefore users are placed in groups, and derive access from a user’s group. ...
What are Applications Software?
... Each software recommendation must be accompanied with a suitable reason (2-3 sentences) and an image representing it (why have you chosen it, what does it allows you to do in a school environment?). ...
... Each software recommendation must be accompanied with a suitable reason (2-3 sentences) and an image representing it (why have you chosen it, what does it allows you to do in a school environment?). ...
Curriculum Group Report-F2011
... Operating Systems , Programming Languages, and Software Designs) but also their implications of using those components on building a real-time system, 3. Demonstrate understanding of the fundamental theory (e.g., real-time scheduling algorithms) of real-time systems, 4. Analyze non-functional requir ...
... Operating Systems , Programming Languages, and Software Designs) but also their implications of using those components on building a real-time system, 3. Demonstrate understanding of the fundamental theory (e.g., real-time scheduling algorithms) of real-time systems, 4. Analyze non-functional requir ...
Resource - Rogue Wave Software
... platform, with its certified library of hundreds of open source software packages. OpenLogic provides a free web site where companies can find, research, and download certified, enterprise-ready open source packages on demand. OpenLogic is continually updated with new releases and security patches t ...
... platform, with its certified library of hundreds of open source software packages. OpenLogic provides a free web site where companies can find, research, and download certified, enterprise-ready open source packages on demand. OpenLogic is continually updated with new releases and security patches t ...
Chapter 2: System Structures
... 4 Many types of resources - Some (such as CPU cycles, main memory, and file storage) may have special allocation code, others (such as I/O devices) may have general request and release code l Accounting - To keep track of which users use how much and what kinds of computer resources l Protection and ...
... 4 Many types of resources - Some (such as CPU cycles, main memory, and file storage) may have special allocation code, others (such as I/O devices) may have general request and release code l Accounting - To keep track of which users use how much and what kinds of computer resources l Protection and ...
Document
... We need to keep track of which user keeps track of how many and which kind of computer resources. ...
... We need to keep track of which user keeps track of how many and which kind of computer resources. ...
xwindows - WordPress.com
... standard GUI for Unix systems, similar to Microsoft Windows. Windows only runs locally on the machine, but X Windows uses the X Protocol to separate the processing and display for an application. It provides remote display feature. Unlike Microsoft Windows, X is not part of the operating system. Alt ...
... standard GUI for Unix systems, similar to Microsoft Windows. Windows only runs locally on the machine, but X Windows uses the X Protocol to separate the processing and display for an application. It provides remote display feature. Unlike Microsoft Windows, X is not part of the operating system. Alt ...
Chapter-3-OpratingSystemSupport
... distributed operating system is that users tend to prefer to have a degree of autonomy for their machines, even in a organization. Unix and Windows are two examples of network operating systems. Those have a networking capability built into them and so can be used to access remote resources usin ...
... distributed operating system is that users tend to prefer to have a degree of autonomy for their machines, even in a organization. Unix and Windows are two examples of network operating systems. Those have a networking capability built into them and so can be used to access remote resources usin ...