Real Time Network Protection for Educational Institutions
... support the procurement and ongoing management of a complete network protection system that addresses the full range of threats to their computing systems' security and integrity. As a result, most educational institutions are under-protected and exposed to significant risks. Lack of Real Time Prote ...
... support the procurement and ongoing management of a complete network protection system that addresses the full range of threats to their computing systems' security and integrity. As a result, most educational institutions are under-protected and exposed to significant risks. Lack of Real Time Prote ...
lecture4-sept13
... • Parent may terminate execution of children processes (abort) – Child has exceeded allocated resources – Task assigned to child is no longer required – If parent is exiting • Some operating system do not allow child to continue if its parent terminates – All children terminated - cascading terminat ...
... • Parent may terminate execution of children processes (abort) – Child has exceeded allocated resources – Task assigned to child is no longer required – If parent is exiting • Some operating system do not allow child to continue if its parent terminates – All children terminated - cascading terminat ...
Introduction to UNIX System
... The shell acts as a command interpreter; it takes each command you enter and passes it to the operating system kernel to be acted upon. Finally, it displays the results of this operation on your screen. ...
... The shell acts as a command interpreter; it takes each command you enter and passes it to the operating system kernel to be acted upon. Finally, it displays the results of this operation on your screen. ...
Midterm1-su13
... e) Where was the first operating system with a graphical user interface developed? ...
... e) Where was the first operating system with a graphical user interface developed? ...
1.5 In a multiprogramming and time
... Answer: Benefits typically include the following (a) adding a new service does not require modifying the kernel, (b) it is more secure as more operations are done in user mode than in kernel mode, and (c) a simpler kernel design and functionality typically results in a more reliable operating system ...
... Answer: Benefits typically include the following (a) adding a new service does not require modifying the kernel, (b) it is more secure as more operations are done in user mode than in kernel mode, and (c) a simpler kernel design and functionality typically results in a more reliable operating system ...
Application of CYBEX (Cybersecurity Information Exchange)
... What about Future Networks/NGNs? A potential implementation of a CYBEX reference model for NGNs is depicted in the following diagrams SCAP should be ubiquitous in the models This approach is adapted from a similar approach already being taken for NGN Identity Management NGN providers would play a s ...
... What about Future Networks/NGNs? A potential implementation of a CYBEX reference model for NGNs is depicted in the following diagrams SCAP should be ubiquitous in the models This approach is adapted from a similar approach already being taken for NGN Identity Management NGN providers would play a s ...
Processes
... Fig. 2-21. A solution to the readers and writers problem : a writer has to wait until no more reader is active Tanenbaum & Woodhull, Operating Systems: Design and Implementation, (c) 2006 Prentice-Hall ...
... Fig. 2-21. A solution to the readers and writers problem : a writer has to wait until no more reader is active Tanenbaum & Woodhull, Operating Systems: Design and Implementation, (c) 2006 Prentice-Hall ...
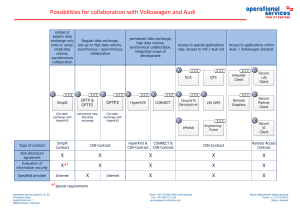
Possibilities for collaboration with Volkswagen
... If users are absent from their workplaces, they have to remove the authorization objects (PKI card or similar) provided to them for performing their activities from the working environment and from the terminal and personally hold them in safe keeping. The commissioning department and/or corporate s ...
... If users are absent from their workplaces, they have to remove the authorization objects (PKI card or similar) provided to them for performing their activities from the working environment and from the terminal and personally hold them in safe keeping. The commissioning department and/or corporate s ...
Nachos Overview - Computer and Information Science | Brooklyn
... Nachos. On the other hand, Nachos was originally developed for use on DEC MIPS systems (DEC was acquired by Compaq years ago, which was acquired in turn by HP recently.) and user programs are in binary format, making Nachos real enough avoiding the sense of ”toy”. Nachos includes a MIPS simulator to ...
... Nachos. On the other hand, Nachos was originally developed for use on DEC MIPS systems (DEC was acquired by Compaq years ago, which was acquired in turn by HP recently.) and user programs are in binary format, making Nachos real enough avoiding the sense of ”toy”. Nachos includes a MIPS simulator to ...
Chap 01 -Tbook.Ver.9
... Protection and Security Protection – any mechanism for controlling access of processes or ...
... Protection and Security Protection – any mechanism for controlling access of processes or ...
The Windows NT 4.0 Environment
... Different applications can run at the same time. Threaded Background applications can continue while a user works in the foreground. Multiple threads in an application can operate simultaneously. Security features protect network and local resources. Features include mandatory logon, discretionary a ...
... Different applications can run at the same time. Threaded Background applications can continue while a user works in the foreground. Multiple threads in an application can operate simultaneously. Security features protect network and local resources. Features include mandatory logon, discretionary a ...
Abstract View of System Components
... – Pthreads are defined as a set of C language programming types and procedure calls, implemented with a pthread.h header/include file and a thread library. ...
... – Pthreads are defined as a set of C language programming types and procedure calls, implemented with a pthread.h header/include file and a thread library. ...
Threads
... Supported by the Kernel Kernel threads is slower to create and manage than user threads If a thread performs a blocking system call, the kernel can schedule ...
... Supported by the Kernel Kernel threads is slower to create and manage than user threads If a thread performs a blocking system call, the kernel can schedule ...
All of the above.
... • All processors run the same operating system in an SMP system. • Most modern desktop operating systems are SMP systems because of multiple cores. • SMP allocates one processor to be the master processor and the other processors are slave processors. • SMP systems are tightly coupled. ...
... • All processors run the same operating system in an SMP system. • Most modern desktop operating systems are SMP systems because of multiple cores. • SMP allocates one processor to be the master processor and the other processors are slave processors. • SMP systems are tightly coupled. ...
Week-3
... underlying machine VM software can run in kernel mode. The VMs should execute only in user mode Guest OSes also have user and kernel modes Virtual user mode – virtual kernel mode ...
... underlying machine VM software can run in kernel mode. The VMs should execute only in user mode Guest OSes also have user and kernel modes Virtual user mode – virtual kernel mode ...
system programs
... • System calls allow the OS to hide the low-level hardware from application programs. • In a virtual machine these system calls are executed by a program which emulates the hardware. • This hardware may, or may not be the same as the actual hardware. NETW3005 (Operating Systems) ...
... • System calls allow the OS to hide the low-level hardware from application programs. • In a virtual machine these system calls are executed by a program which emulates the hardware. • This hardware may, or may not be the same as the actual hardware. NETW3005 (Operating Systems) ...
Chapter 19: Malicious Logic - Welcome to nob.cs.ucdavis.edu!
... records when one particular record is deleted – The “particular record” is usually that of the person writing the logic bomb – Idea is if (when) he or she is fired, and the payroll record deleted, the company loses all those records November 1, 2004 ...
... records when one particular record is deleted – The “particular record” is usually that of the person writing the logic bomb – Idea is if (when) he or she is fired, and the payroll record deleted, the company loses all those records November 1, 2004 ...
Introduction to Operating Systems
... operating system” is good approximation but varies widely. • “The one program running at all times on the computer” is the Kernel. • Everything else is either a system program (ships with the operating system) or an application program. ...
... operating system” is good approximation but varies widely. • “The one program running at all times on the computer” is the Kernel. • Everything else is either a system program (ships with the operating system) or an application program. ...
ppt
... • Task assigned to child is no longer required. • Parent is exiting – OS does not allow child to continue if parent terminates – Cascading termination Principles of Operating Systems I/O Structures and Storage ...
... • Task assigned to child is no longer required. • Parent is exiting – OS does not allow child to continue if parent terminates – Cascading termination Principles of Operating Systems I/O Structures and Storage ...
presentation source
... requirements Must provide functionality of a multiprogramming OS plus additional features to support multiple processors Simultaneous concurrent processes or threads: kernel routines need to be reentrant Scheduling done by any processor, can create conflicts. Synchronization through locks is ...
... requirements Must provide functionality of a multiprogramming OS plus additional features to support multiple processors Simultaneous concurrent processes or threads: kernel routines need to be reentrant Scheduling done by any processor, can create conflicts. Synchronization through locks is ...
AISE PoIS4E_PP_ch02_57
... • Many organizations create or support the development of intellectual property as part of their business operations. • Intellectual property (IP): “ownership of ideas and control over the tangible ملموسor virtual representation of those ideas” • Intellectual property for an organization includes ...
... • Many organizations create or support the development of intellectual property as part of their business operations. • Intellectual property (IP): “ownership of ideas and control over the tangible ملموسor virtual representation of those ideas” • Intellectual property for an organization includes ...
Web Site Development Tools
... devices make “sniffers” impractical • Using laptops with default IrDA port settings in public places (such as airports) automatically allows networking with other IrDA devices without authentication or passwords • Bluetooth uses 128-bit link key, private encryption keys, user PIN and device addresse ...
... devices make “sniffers” impractical • Using laptops with default IrDA port settings in public places (such as airports) automatically allows networking with other IrDA devices without authentication or passwords • Bluetooth uses 128-bit link key, private encryption keys, user PIN and device addresse ...
Network Security Threats CERT Centers, Software Engineering Institute Carnegie Mellon University
... Internet: Network of Networks • Connected by routers, no central control • Using common set of protocols TCP/IP - Two-level package of protocols for Internet • Transmission Control Protocol (TCP) -- sequencing of series of packets to transmit data reliably over Internet • Internet Protocol (IP) -- f ...
... Internet: Network of Networks • Connected by routers, no central control • Using common set of protocols TCP/IP - Two-level package of protocols for Internet • Transmission Control Protocol (TCP) -- sequencing of series of packets to transmit data reliably over Internet • Internet Protocol (IP) -- f ...
2.01 - Kangwon
... hFile - [in] A handle to the file to be read. lpBuffer - [out] A pointer to the buffer that receives the data read from a file. nNumberOfBytesToRead - [in] The maximum number of bytes to read. lpNumberOfBytesRead - [out] A pointer to the variable that receives the number of bytes read. lpOverlapped ...
... hFile - [in] A handle to the file to be read. lpBuffer - [out] A pointer to the buffer that receives the data read from a file. nNumberOfBytesToRead - [in] The maximum number of bytes to read. lpNumberOfBytesRead - [out] A pointer to the variable that receives the number of bytes read. lpOverlapped ...