Chapter 1
... presence of malicious code have resulted primarily from system outages and staff time involved in repairing the systems • Costs can be significant ...
... presence of malicious code have resulted primarily from system outages and staff time involved in repairing the systems • Costs can be significant ...
L4_L6_System_Structu..
... Exact type and amount of information vary according to OS and call Three general methods used to pass parameters to the OS Simplest: pass the parameters in registers In some cases, may be more parameters than registers Parameters stored in a block, or table, in memory, and address of block p ...
... Exact type and amount of information vary according to OS and call Three general methods used to pass parameters to the OS Simplest: pass the parameters in registers In some cases, may be more parameters than registers Parameters stored in a block, or table, in memory, and address of block p ...
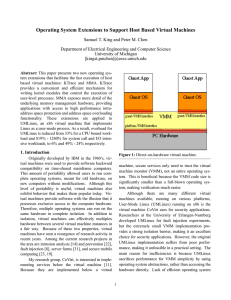
Operating System Extensions to Support Host Based Virtual Machines
... the power of the underling memory management haware are known to contribute to this performance degradation. In an effort to improve performance, I developed two new abstractions: KTrace and memory management abstractions (MMA). KTrace is a mechanism through which kernel modules can register callbac ...
... the power of the underling memory management haware are known to contribute to this performance degradation. In an effort to improve performance, I developed two new abstractions: KTrace and memory management abstractions (MMA). KTrace is a mechanism through which kernel modules can register callbac ...
$doc.title
... advantages in using Linux, for example a lower cost of acquisition than that of proprietary operating systems, wide availability on different platforms and avoidance of dependence on one supplier. Linux is also perceived as being reliable, and the availability of the Linux source text provides the a ...
... advantages in using Linux, for example a lower cost of acquisition than that of proprietary operating systems, wide availability on different platforms and avoidance of dependence on one supplier. Linux is also perceived as being reliable, and the availability of the Linux source text provides the a ...
Advanced Operating Systems
... Jump to ROM code Load in the boot loader from stable storage Jump to the boot loader Load the rest of the operating system Initialize and run ...
... Jump to ROM code Load in the boot loader from stable storage Jump to the boot loader Load the rest of the operating system Initialize and run ...
Cyberespionage campaign hits energy companies
... that supports bidirectional reading/writing of process variables, but does not provide more advanced capabilities like device con guration and rmware updates. OPC is a standard way for process control systems, applications and devices to interact with each other. It is important to note that not al ...
... that supports bidirectional reading/writing of process variables, but does not provide more advanced capabilities like device con guration and rmware updates. OPC is a standard way for process control systems, applications and devices to interact with each other. It is important to note that not al ...
ch02_computer_struct
... CPU moves data from/to main memory to/from local buffers I/O is from the device to local buffer of controller Device controller informs CPU that it has finished its operation by ...
... CPU moves data from/to main memory to/from local buffers I/O is from the device to local buffer of controller Device controller informs CPU that it has finished its operation by ...
Module 3: Operating
... protection of system resources since each virtual machine is isolated from all other virtual machines. This isolation, however, permits no direct sharing of resources. A virtual-machine system is a perfect vehicle for operating-systems research and development. System development is done on the vi ...
... protection of system resources since each virtual machine is isolated from all other virtual machines. This isolation, however, permits no direct sharing of resources. A virtual-machine system is a perfect vehicle for operating-systems research and development. System development is done on the vi ...
What is an Operating System? - E
... Protection and Security Protection – any mechanism for controlling access of processes or ...
... Protection and Security Protection – any mechanism for controlling access of processes or ...
ch2
... I/O devices and the CPU can execute concurrently Each device controller is in charge of a particular device type ...
... I/O devices and the CPU can execute concurrently Each device controller is in charge of a particular device type ...
Convergence of Desktop and Web Applications on a Multi-Service OS
... tion is treated as a principal on the browser platform and that its origin labels the principal [19]. However, today’s browsers have never been designed and constructed as an OS for these web applications: different principals may coexist in the same protection domain, and there is no coherent supp ...
... tion is treated as a principal on the browser platform and that its origin labels the principal [19]. However, today’s browsers have never been designed and constructed as an OS for these web applications: different principals may coexist in the same protection domain, and there is no coherent supp ...
PPT - LSU CCT - Louisiana State University
... • Protection – any mechanism for controlling access of processes or users to resources defined by the OS • Security – defense of the system against internal and external attacks – Huge range, including denial-of-service, worms, viruses, identity theft, theft of service ...
... • Protection – any mechanism for controlling access of processes or users to resources defined by the OS • Security – defense of the system against internal and external attacks – Huge range, including denial-of-service, worms, viruses, identity theft, theft of service ...
Lecture 6: Synchronization
... Exercise 7.10 A single-lane bridge connects the two Vermont villages of North Tunbridge and South Tunbridge. Farmers in the two villages use this bridge to deliver their produce to the neighboring town. The bridge can become deadlocked if both a northbound and a southbound farmer get on the bridge ...
... Exercise 7.10 A single-lane bridge connects the two Vermont villages of North Tunbridge and South Tunbridge. Farmers in the two villages use this bridge to deliver their produce to the neighboring town. The bridge can become deadlocked if both a northbound and a southbound farmer get on the bridge ...
Document
... effectively taking over the machine. • Buffer overflows are not easy to discover and even when one is discovered, it is generally extremely difficult to exploit. • Well known and documented over an array of products and components. ...
... effectively taking over the machine. • Buffer overflows are not easy to discover and even when one is discovered, it is generally extremely difficult to exploit. • Well known and documented over an array of products and components. ...
Lecture 5 - The University of Texas at Dallas
... “There are two types of RIM devices within each model class. The Exchange Edition is meant for use in a corporate environment while the Internet Edition works with standard POP email accounts. The Exchange Edition employs Triple-DES encryption to send and receive but the Internet Edition communicate ...
... “There are two types of RIM devices within each model class. The Exchange Edition is meant for use in a corporate environment while the Internet Edition works with standard POP email accounts. The Exchange Edition employs Triple-DES encryption to send and receive but the Internet Edition communicate ...
www.isa.org/intech May/June 2014 Integrating DCS I/O Embedded vision
... network security devices (e.g., firewalls) for isolation from the plant IT system. Only workstations and servers within the ICS that act as gateways should allow ICS access through these ICS perimeter security devices. This prevents other devices on the ICS control network from being directly access ...
... network security devices (e.g., firewalls) for isolation from the plant IT system. Only workstations and servers within the ICS that act as gateways should allow ICS access through these ICS perimeter security devices. This prevents other devices on the ICS control network from being directly access ...
[ppt
... can change between the time that Janus resolves a path relative to that inode to check an access Assume the current working directory of Process A is /tmp/foo/bar and that Janus allows the monitored application read and write access only to the contents of the /tmp directory. Process A calls open(". ...
... can change between the time that Janus resolves a path relative to that inode to check an access Assume the current working directory of Process A is /tmp/foo/bar and that Janus allows the monitored application read and write access only to the contents of the /tmp directory. Process A calls open(". ...
Operating Systems Should Provide Transactions
... tures, and database transactions provide consistent updates update system resources results in serious security and to database-managed secondary storage. programmability problems. The example in Figure 1 ilUnfortunately, the POSIX system call API has lagged lustrates a time-of-check-to-time-of-use ...
... tures, and database transactions provide consistent updates update system resources results in serious security and to database-managed secondary storage. programmability problems. The example in Figure 1 ilUnfortunately, the POSIX system call API has lagged lustrates a time-of-check-to-time-of-use ...
Real Time Network Protection for Educational Institutions
... support the procurement and ongoing management of a complete network protection system that addresses the full range of threats to their computing systems' security and integrity. As a result, most educational institutions are under-protected and exposed to significant risks. Lack of Real Time Prote ...
... support the procurement and ongoing management of a complete network protection system that addresses the full range of threats to their computing systems' security and integrity. As a result, most educational institutions are under-protected and exposed to significant risks. Lack of Real Time Prote ...