Trusted Infrastructure - CSE
... system or other hardware so the rootkit can start before Windows. Bootkits. These kits replace the operating system’s bootloader (the small piece of software that starts the operating system) so that the PC loads the bootkit before the operating system. Kernel rootkits. These kits replace a portion ...
... system or other hardware so the rootkit can start before Windows. Bootkits. These kits replace the operating system’s bootloader (the small piece of software that starts the operating system) so that the PC loads the bootkit before the operating system. Kernel rootkits. These kits replace a portion ...
Design a Mini-Operating System for Mobile Phone
... mobile terminals and provides a reliable environment as it has been designed so that user data is never lost and the device running the operating system will never have to be rebooted. Approximately 72% of mobile devices use Symbian and major mobile companies adopt this operating system in their man ...
... mobile terminals and provides a reliable environment as it has been designed so that user data is never lost and the device running the operating system will never have to be rebooted. Approximately 72% of mobile devices use Symbian and major mobile companies adopt this operating system in their man ...
No Slide Title
... from 16 to 31. The variable class contains threads having priorities from 0 to 15. Characteristics of 2000’s priority strategy. Trends to give very good response times to interactive threads that are using the mouse and windows. Enables I/O-bound threads to keep the I/O devices busy. Compl ...
... from 16 to 31. The variable class contains threads having priorities from 0 to 15. Characteristics of 2000’s priority strategy. Trends to give very good response times to interactive threads that are using the mouse and windows. Enables I/O-bound threads to keep the I/O devices busy. Compl ...
ch22
... adapt to changes in the hardware configuration. When new devices are added (for example, PCI or ...
... adapt to changes in the hardware configuration. When new devices are added (for example, PCI or ...
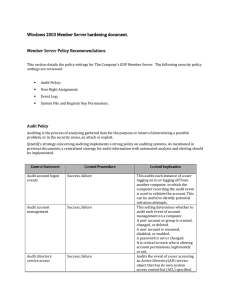
Server hardening - Cisco Security Solutions
... global objects’ user privilege to members of the local administrators and service groups could mitigate the risk. However Microsoft set this by default on a default setup therfore this option does not need to be explicitly set (i.e not defined). Users with this privilege could expose sensitive data ...
... global objects’ user privilege to members of the local administrators and service groups could mitigate the risk. However Microsoft set this by default on a default setup therfore this option does not need to be explicitly set (i.e not defined). Users with this privilege could expose sensitive data ...
Chapter 14
... • How to access MS-DOS emulators from other operating systems • How MS-DOS provided a foundation for early Microsoft Windows releases • The basics of command-driven systems and how to construct simple batch files • How one processor can be shared among multiple processes • The limitations of MS-DOS ...
... • How to access MS-DOS emulators from other operating systems • How MS-DOS provided a foundation for early Microsoft Windows releases • The basics of command-driven systems and how to construct simple batch files • How one processor can be shared among multiple processes • The limitations of MS-DOS ...
Module 3: Operating
... secondary storage to back up main memory Most modern computer systems use disks as the principle on-line storage medium, for both programs and data The operating system is responsible for the following activities in connection with disk management: Free space management Storage allocation ...
... secondary storage to back up main memory Most modern computer systems use disks as the principle on-line storage medium, for both programs and data The operating system is responsible for the following activities in connection with disk management: Free space management Storage allocation ...
What is an Operating System?
... bits, it is amazing how many things a computer can represent: numbers, letters, images, movies, sounds, documents, and programs, to name a few. A byte is 8 bits, and on most computers it is the smallest convenient chunk of storage. For example, most computers don’t have an instruction to move a bit ...
... bits, it is amazing how many things a computer can represent: numbers, letters, images, movies, sounds, documents, and programs, to name a few. A byte is 8 bits, and on most computers it is the smallest convenient chunk of storage. For example, most computers don’t have an instruction to move a bit ...
No Slide Title
... Distinction between user-level and kernel-level threads When threads supported, threads scheduled, not processes Many-to-one and many-to-many models, thread library schedules user-level ...
... Distinction between user-level and kernel-level threads When threads supported, threads scheduled, not processes Many-to-one and many-to-many models, thread library schedules user-level ...
CN 2015 5 - SNGCE DIGITAL LIBRARY
... Cryptographic techniques allow sender to mask data. Cryptographic techniques allow receiver to recover data from masked data. It is the study of Encryption and Decryption methods. Encryption—Plain text to cipher text Decryption—Cipher text to Plain text ...
... Cryptographic techniques allow sender to mask data. Cryptographic techniques allow receiver to recover data from masked data. It is the study of Encryption and Decryption methods. Encryption—Plain text to cipher text Decryption—Cipher text to Plain text ...
Operating Systems
... map of the clusters (basic units of logical storage on a hard disk) that a file has been stored in • When you write a new file to a hard disk, the file is stored in one or more clusters that are not necessarily next to each other; they may be rather scattered over the disk ©2003 The McGraw-Hill Comp ...
... map of the clusters (basic units of logical storage on a hard disk) that a file has been stored in • When you write a new file to a hard disk, the file is stored in one or more clusters that are not necessarily next to each other; they may be rather scattered over the disk ©2003 The McGraw-Hill Comp ...
11 Secure electronic communication
... Portable devices (memory devices, backup media) are kept secure Wireless networks configured securely Policy on the use of mobile devices developed Remote access protection in place (eg. VPN) ...
... Portable devices (memory devices, backup media) are kept secure Wireless networks configured securely Policy on the use of mobile devices developed Remote access protection in place (eg. VPN) ...
Project proposal
... • To provide a solution for using Bluetooth from Java with all ‘Java’ benefits – portability being the main one – so one could use the same stack to access a mobile phones Bluetooth abilities and a Bluetooth PC Card connected to a standard PC running Linux or Windows ...
... • To provide a solution for using Bluetooth from Java with all ‘Java’ benefits – portability being the main one – so one could use the same stack to access a mobile phones Bluetooth abilities and a Bluetooth PC Card connected to a standard PC running Linux or Windows ...
Introduction to Healthcare Information Technology
... – Provides cryptographic services to all devices – Prevents computer from booting if system files or data have been altered – If hard drive is moved to a different computer, user must enter a recovery password to gain access ...
... – Provides cryptographic services to all devices – Prevents computer from booting if system files or data have been altered – If hard drive is moved to a different computer, user must enter a recovery password to gain access ...
Process
... Resource ownership - process includes a virtual address space to hold the process image Scheduling/execution- follows an execution path that may be interleaved with other processes These two characteristics are treated independently by the operating system ...
... Resource ownership - process includes a virtual address space to hold the process image Scheduling/execution- follows an execution path that may be interleaved with other processes These two characteristics are treated independently by the operating system ...
Operating Systems
... Command interpreter: Interface between OS and your fingers (or mouth…or toes!) Commands to manipulate files, run and kill programs, access remote machines, change protections on files, etc. Some OS’s have “built-in” command interfaces, some allow an interface to be “plugged in” Unix: “shell” (csh, t ...
... Command interpreter: Interface between OS and your fingers (or mouth…or toes!) Commands to manipulate files, run and kill programs, access remote machines, change protections on files, etc. Some OS’s have “built-in” command interfaces, some allow an interface to be “plugged in” Unix: “shell” (csh, t ...
A high-performance, POSIX compatible, multicore real-time
... reduction when running applications on different cores a fact which also ensures linear performance scalability. As the number of cores increases, OSE and its scalable IPC reward you with bare-metal performance characteristics and highly deterministic latency. Easy migration and portability Enea OSE ...
... reduction when running applications on different cores a fact which also ensures linear performance scalability. As the number of cores increases, OSE and its scalable IPC reward you with bare-metal performance characteristics and highly deterministic latency. Easy migration and portability Enea OSE ...
Linux+ Guide to Linux Certification
... hierarchical and indented list – Options allow user to delete files while tree is being generated – TREE /F displays names of files in each directory – Can also be used to delete file that’s duplicated on several different directories ...
... hierarchical and indented list – Options allow user to delete files while tree is being generated – TREE /F displays names of files in each directory – Can also be used to delete file that’s duplicated on several different directories ...
SOE Build Guidelines - Windows v3.0
... 4. Do not install any form of “value adding” software, such as browser toolbars or helpers, unless they are explicitly required. Where they are automatically installed, but not required, take remedial action to remove or permanently disable them. 5. To be compliant with the WofG COE Policy, the appr ...
... 4. Do not install any form of “value adding” software, such as browser toolbars or helpers, unless they are explicitly required. Where they are automatically installed, but not required, take remedial action to remove or permanently disable them. 5. To be compliant with the WofG COE Policy, the appr ...
the Mach kernel
... The kernel also must process pointers to out-of-line data, as a pointer to data in the sender’s address space would be invalid if the receiver’s -- especially if the sender and receiver reside on different systems! To make it more efficient, Mach will modify the address map of the receiving task ...
... The kernel also must process pointers to out-of-line data, as a pointer to data in the sender’s address space would be invalid if the receiver’s -- especially if the sender and receiver reside on different systems! To make it more efficient, Mach will modify the address map of the receiving task ...
Chapter 2: Operating
... Many types of resources - Some (such as CPU cycles, main memory, and file storage) may have special allocation code, others (such as I/O devices) may have general request and release code ...
... Many types of resources - Some (such as CPU cycles, main memory, and file storage) may have special allocation code, others (such as I/O devices) may have general request and release code ...
Introduction
... Given enough bits, it is amazing how many things a computer can represent: numbers, letters, images, movies, sounds, documents, and programs, to name a few. A byte is 8 bits, and on most computers it is the smallest convenient chunk of storage. For example, most computers don’t have an instruction t ...
... Given enough bits, it is amazing how many things a computer can represent: numbers, letters, images, movies, sounds, documents, and programs, to name a few. A byte is 8 bits, and on most computers it is the smallest convenient chunk of storage. For example, most computers don’t have an instruction t ...