Operating-System Structures
... DWORD bytesToRead—the number of bytes to be read into the buffer LPDWORD bytesRead—the number of bytes read during the last read LPOVERLAPPED ovl—indicates if overlapped I/O is being used ...
... DWORD bytesToRead—the number of bytes to be read into the buffer LPDWORD bytesRead—the number of bytes read during the last read LPOVERLAPPED ovl—indicates if overlapped I/O is being used ...
Cyber-Insurance--I Do Not Think That Word
... Sophisticated threats targeting specific computer systems and organizations big and small But strict sub-limits ...
... Sophisticated threats targeting specific computer systems and organizations big and small But strict sub-limits ...
Protocols used by the virtual private network.
... Internet Protocol Security (IPsec). The main protocol for VPNs is called Internet Protocol Security (IPsec). It isn't actually a protocol in itself. Instead, it is an entire set of protocols. IPsec works at Layer 3 of the OSI model or above. It is the most common suite of protocols used to secure a ...
... Internet Protocol Security (IPsec). The main protocol for VPNs is called Internet Protocol Security (IPsec). It isn't actually a protocol in itself. Instead, it is an entire set of protocols. IPsec works at Layer 3 of the OSI model or above. It is the most common suite of protocols used to secure a ...
Chapter 13 I/O Hardware
... If device can serve only one request at a time i.e., Printing Device reservation - provides exclusive access to a ...
... If device can serve only one request at a time i.e., Printing Device reservation - provides exclusive access to a ...
ch1
... Given enough bits, it is amazing how many things a computer can represent: numbers, letters, images, movies, sounds, documents, and programs, to name a few. A byte is 8 bits, and on most computers it is the smallest convenient chunk of storage. For example, most computers don’t have an instruction t ...
... Given enough bits, it is amazing how many things a computer can represent: numbers, letters, images, movies, sounds, documents, and programs, to name a few. A byte is 8 bits, and on most computers it is the smallest convenient chunk of storage. For example, most computers don’t have an instruction t ...
Physical Security
... the Internet, from web servers to browsers. • When a secure connection is needed, SSL/TLS is used and appears in the address as https://. • If the protocol is https:, your connection is secure. • If the protocol is http:, then the connection is carried by plaintext for anyone to see. ...
... the Internet, from web servers to browsers. • When a secure connection is needed, SSL/TLS is used and appears in the address as https://. • If the protocol is https:, your connection is secure. • If the protocol is http:, then the connection is carried by plaintext for anyone to see. ...
ppt - Stanford Crypto group
... • Frame-Frame relationships – canScript(A,B) • Can Frame A execute a script that manipulates arbitrary/nontrivial DOM elements of Frame B? – canNavigate(A,B) • Can Frame A change the origin of content for Frame B? • Frame-principal relationships – readCookie(A,S), writeCookie(A,S) • Can Frame A read ...
... • Frame-Frame relationships – canScript(A,B) • Can Frame A execute a script that manipulates arbitrary/nontrivial DOM elements of Frame B? – canNavigate(A,B) • Can Frame A change the origin of content for Frame B? • Frame-principal relationships – readCookie(A,S), writeCookie(A,S) • Can Frame A read ...
Chapter 1: Introduction
... Storage Definitions and Notation Review The basic unit of computer storage is the bit. A bit can contain one of two values, 0 and 1. All other storage in a computer is based on collections of bits. Given enough bits, it is amazing how many things a computer can represent: numbers, letters, images, ...
... Storage Definitions and Notation Review The basic unit of computer storage is the bit. A bit can contain one of two values, 0 and 1. All other storage in a computer is based on collections of bits. Given enough bits, it is amazing how many things a computer can represent: numbers, letters, images, ...
A user-mode port of the Linux kernel
... by the tracing thread. It needs to ptrace all new processes, and that is simpli ed if it's their parent. The new thread starts life in a trampoline which does some initialization. It sets up its signal handlers for SIGSEGV, SIGIO, and SIGVTALRM, initializes the timer, and sets itself to be ptraced b ...
... by the tracing thread. It needs to ptrace all new processes, and that is simpli ed if it's their parent. The new thread starts life in a trampoline which does some initialization. It sets up its signal handlers for SIGSEGV, SIGIO, and SIGVTALRM, initializes the timer, and sets itself to be ptraced b ...
Introduction - McMaster Computing and Software
... The basic unit of computer storage is the bit. A bit can contain one of two values, 0 and 1. All other storage in a computer is based on collections of bits. Given enough bits, it is amazing how many things a computer can represent: numbers, letters, images, movies, sounds, documents, and programs, ...
... The basic unit of computer storage is the bit. A bit can contain one of two values, 0 and 1. All other storage in a computer is based on collections of bits. Given enough bits, it is amazing how many things a computer can represent: numbers, letters, images, movies, sounds, documents, and programs, ...
3 MB 3rd Nov 2014 ch1
... Protection and Security Protection – any mechanism for controlling access of ...
... Protection and Security Protection – any mechanism for controlling access of ...
Errors and Exception Handling
... Booting is akin to application start-up Debugging is easier (run debugger on virtual machine) Useful for networking, fs, etc development ...
... Booting is akin to application start-up Debugging is easier (run debugger on virtual machine) Useful for networking, fs, etc development ...
Chapter 2 Computer-System Structures 2
... routine in the OS, and the mode bit is set to monitor mode. – The monitor verifies that the parameters are correct and legal, executes the request, and returns control to the instruction following the system call. ...
... routine in the OS, and the mode bit is set to monitor mode. – The monitor verifies that the parameters are correct and legal, executes the request, and returns control to the instruction following the system call. ...
Embedded Operating Systems for Real
... system. Here each task runs until it is finished and only after that next task is started. In shortest job first scheduler each time a running task completes or blocks itself, next task selected is one that will require the least amount of processor time to complete. Round robin is the only scheduli ...
... system. Here each task runs until it is finished and only after that next task is started. In shortest job first scheduler each time a running task completes or blocks itself, next task selected is one that will require the least amount of processor time to complete. Round robin is the only scheduli ...
Fundamental Concepts
... – Interrupt handler for a device executes at processor priority equal to device priority. – Effect: An interrupt handler can only be interrupted by devices of higher priority. ...
... – Interrupt handler for a device executes at processor priority equal to device priority. – Effect: An interrupt handler can only be interrupted by devices of higher priority. ...
Introduction
... Mode bit provided by hardware Provides ability to distinguish when system is running user code or kernel code Some instructions designated as privileged, only executable in kernel mode System call changes mode to kernel, return from call resets it to user ...
... Mode bit provided by hardware Provides ability to distinguish when system is running user code or kernel code Some instructions designated as privileged, only executable in kernel mode System call changes mode to kernel, return from call resets it to user ...
Power Point - ECE Users Pages - Georgia Institute of Technology
... • Failure to implement patches! ...
... • Failure to implement patches! ...
SSH - Information Services and Technology
... Taskforce (IETF) SECSH working group • The IETF is an open standards organization that has ...
... Taskforce (IETF) SECSH working group • The IETF is an open standards organization that has ...
Introduction to Linux/Unix
... Redirection and Pipe File/Directory Permissions Process Management The nano Text Editor ...
... Redirection and Pipe File/Directory Permissions Process Management The nano Text Editor ...
File
... Ans: The modular approach combines the benefits of both the layered and microkernel design techniques. In a modular design, the kernel needs only to have the capability to perform the required functions and know how to communicate between modules. However, if more functionality is required in the ke ...
... Ans: The modular approach combines the benefits of both the layered and microkernel design techniques. In a modular design, the kernel needs only to have the capability to perform the required functions and know how to communicate between modules. However, if more functionality is required in the ke ...
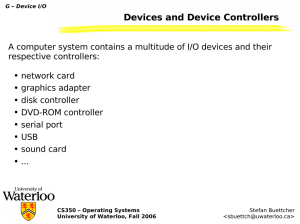
Devices and Device Controllers
... Monolithic Kernels vs. Micro-Kernels In many operating systems (Linux, Windows, ...), device drivers are part of the operating system kernel with complete access to the entire system. This can sometimes be convenient for the device driver developer, but may lead to severe security problems. What if ...
... Monolithic Kernels vs. Micro-Kernels In many operating systems (Linux, Windows, ...), device drivers are part of the operating system kernel with complete access to the entire system. This can sometimes be convenient for the device driver developer, but may lead to severe security problems. What if ...
Import Settings: Base Settings: Brownstone Default Highest Answer
... Ans: The modular approach combines the benefits of both the layered and microkernel design techniques. In a modular design, the kernel needs only to have the capability to perform the required functions and know how to communicate between modules. However, if more functionality is required in the ke ...
... Ans: The modular approach combines the benefits of both the layered and microkernel design techniques. In a modular design, the kernel needs only to have the capability to perform the required functions and know how to communicate between modules. However, if more functionality is required in the ke ...
Chapter 1 - cse.sc.edu
... Given enough bits, it is amazing how many things a computer can represent: numbers, letters, images, movies, sounds, documents, and programs, to name a few. A byte is 8 bits, and on most computers it is the smallest convenient chunk of storage. For example, most computers don’t have an instruction t ...
... Given enough bits, it is amazing how many things a computer can represent: numbers, letters, images, movies, sounds, documents, and programs, to name a few. A byte is 8 bits, and on most computers it is the smallest convenient chunk of storage. For example, most computers don’t have an instruction t ...
UNIX Foundations - Computer Science
... Saves resource usage statistics and exit status in the proc structure. Changes state to SZOMB, and puts the proc on the zombie process list. Makes the init process inherit any live children of the exiting process. Releases the address space, u area, ATM, and swap space. Notifies the parent by sendin ...
... Saves resource usage statistics and exit status in the proc structure. Changes state to SZOMB, and puts the proc on the zombie process list. Makes the init process inherit any live children of the exiting process. Releases the address space, u area, ATM, and swap space. Notifies the parent by sendin ...