Process
... thread management is done in user space, so it is efficient Entire process will block if a thread makes a blocking call to the kernel Because only one thread can access kernel at a time, no parallelism on multiprocessors is possible ...
... thread management is done in user space, so it is efficient Entire process will block if a thread makes a blocking call to the kernel Because only one thread can access kernel at a time, no parallelism on multiprocessors is possible ...
SecureSwitch: BIOS-Assisted Isolation and Switch between Trusted
... switching time. The basic input/output system (BIOS) is the only trusted computing base that ensures the resource isolation between the two OSes and enforces a trusted path for switching between the two OSes. The attack surface in our system is significantly smaller than hypervisor- or software-base ...
... switching time. The basic input/output system (BIOS) is the only trusted computing base that ensures the resource isolation between the two OSes and enforces a trusted path for switching between the two OSes. The attack surface in our system is significantly smaller than hypervisor- or software-base ...
MODERN OPERATING SYSTEMS Third Edition ANDREW S
... E.g., need to be very careful to avoid race conditions, deadlocks and other problems ...
... E.g., need to be very careful to avoid race conditions, deadlocks and other problems ...
Anonymous Proxy Detection and Control
... An anonymous proxy server is intended to conceal a user’s identity. One of the more common approaches is the open proxy. An open proxy is a proxy server that can be accessed by any Internet user. Anonymous open proxies allow any user of the Internet to conceal his or her IP address, identity and loc ...
... An anonymous proxy server is intended to conceal a user’s identity. One of the more common approaches is the open proxy. An open proxy is a proxy server that can be accessed by any Internet user. Anonymous open proxies allow any user of the Internet to conceal his or her IP address, identity and loc ...
Structures - IDA.LiU.se - Linköpings universitet
... § Command Line Interpreter (CLI) allows direct command entry ...
... § Command Line Interpreter (CLI) allows direct command entry ...
VPN: Virtual Private Network
... authentication from VPN server. If mutual authentication is used, the VPN client also authenticates the VPN server, which provides protection against computers that are masquerading as VPN servers. ...
... authentication from VPN server. If mutual authentication is used, the VPN client also authenticates the VPN server, which provides protection against computers that are masquerading as VPN servers. ...
The Application Kernel Approach - a Novel Approach for Adding
... fine grained locking scheme to allow several processors to execute in the kernel concurrently. Finegrained systems allow for better scalability since processes can run with less blocking on kernel-access. However, they also require more careful implementation, since more places in the kernel must be ...
... fine grained locking scheme to allow several processors to execute in the kernel concurrently. Finegrained systems allow for better scalability since processes can run with less blocking on kernel-access. However, they also require more careful implementation, since more places in the kernel must be ...
Operating Systems
... 1. protect applications from each other, yet 2. share physical resources between them. • Also usually want to abstract away from grungy harware, i.e. OS provides a virtual machine: – share CPU (in time) and provide each app with a virtual processor, – allocate and protect memory, and provide applica ...
... 1. protect applications from each other, yet 2. share physical resources between them. • Also usually want to abstract away from grungy harware, i.e. OS provides a virtual machine: – share CPU (in time) and provide each app with a virtual processor, – allocate and protect memory, and provide applica ...
CounterACT: Powerful, Automated Network Protection
... to say: “our network is perfectly safe – CounterACT’s automatic zero-day threat prevention provided us with the 24/7/365 protection we have come to expect and rely on!” Conficker (aka Downup, Downadup and Kido) is an aggressive worm that targets Windows-based systems. It’s been estimated that the bu ...
... to say: “our network is perfectly safe – CounterACT’s automatic zero-day threat prevention provided us with the 24/7/365 protection we have come to expect and rely on!” Conficker (aka Downup, Downadup and Kido) is an aggressive worm that targets Windows-based systems. It’s been estimated that the bu ...
Chapter 22 - Windows XP
... First type is suitable for small messages, up to 256 bytes; port's message queue is used as intermediate storage, and the messages are copied from one process to the other. ...
... First type is suitable for small messages, up to 256 bytes; port's message queue is used as intermediate storage, and the messages are copied from one process to the other. ...
SNMP
... simple version of IP and UDP on their devices. Thus the software requirements are kept simple enough, and, can, in most cases, be stored in ROM. UDP is well suited to the brief request / response message used in network ...
... simple version of IP and UDP on their devices. Thus the software requirements are kept simple enough, and, can, in most cases, be stored in ROM. UDP is well suited to the brief request / response message used in network ...
CWNA Guide to Wireless LANs,Third Edition
... and procedures • Securing the devices so that unauthorized users are prohibited from gaining physical access to the equipment is an important security procedure ...
... and procedures • Securing the devices so that unauthorized users are prohibited from gaining physical access to the equipment is an important security procedure ...
Computers and Operating Systems - Ms. Wade`s Page
... Server operating systems are sometimes called network operating systems. Each client on a network has its own personal operating system. The server operating system manages the requests for services from the client computers. An expert called the network administrator uses the server operating syste ...
... Server operating systems are sometimes called network operating systems. Each client on a network has its own personal operating system. The server operating system manages the requests for services from the client computers. An expert called the network administrator uses the server operating syste ...
ppt - Computer and Information Science
... Tanenbaum & Bo, Modern Operating Systems:4th ed., (c) 2013 Prentice-Hall, Inc. All rights reserved. ...
... Tanenbaum & Bo, Modern Operating Systems:4th ed., (c) 2013 Prentice-Hall, Inc. All rights reserved. ...
Proceedings of the General Track: 2003 USENIX Annual Technical Conference
... called UMLinux [Buchacker01]. UMLinux was developed by researchers at the University of Erlangen-Nürnberg for use in fault-injection experiments. UMLinux is a Type II VMM: the guest operating system and all guest applications run as a single process (the guestmachine process) on a host Linux operati ...
... called UMLinux [Buchacker01]. UMLinux was developed by researchers at the University of Erlangen-Nürnberg for use in fault-injection experiments. UMLinux is a Type II VMM: the guest operating system and all guest applications run as a single process (the guestmachine process) on a host Linux operati ...
Chapter 13: I/O Systems
... Kernel keeps state info for I/O components, including open file tables, network connections, character device state ...
... Kernel keeps state info for I/O components, including open file tables, network connections, character device state ...
Module 7: Process Synchronization
... Solution to Critical-Section Problem 1. Mutual Exclusion - If process Pi is executing in its critical section, then no other processes can be executing in their critical sections 2. Progress - If no process is executing in its critical section and there exist some processes that wish to enter their ...
... Solution to Critical-Section Problem 1. Mutual Exclusion - If process Pi is executing in its critical section, then no other processes can be executing in their critical sections 2. Progress - If no process is executing in its critical section and there exist some processes that wish to enter their ...
Protection of user process data in a secure platform architecture
... another process. A root user can use the “ptrace( )” system call to peek at another user’s memory, or cause code to be executed as if the other user requested the execution. A root user can also use “/dev/kmem” to look at other users’ information. A root user can also simply install a driver ...
... another process. A root user can use the “ptrace( )” system call to peek at another user’s memory, or cause code to be executed as if the other user requested the execution. A root user can also use “/dev/kmem” to look at other users’ information. A root user can also simply install a driver ...
Week_3 Operating system File
... A thread is a basic unit of CPU utilization; it comprises a thread ID, a program counter, a register set, and a stack. If a process has multiple threads of control, it can perform more than one task at a time. In certain situations, a single application may be required to perform several simil ...
... A thread is a basic unit of CPU utilization; it comprises a thread ID, a program counter, a register set, and a stack. If a process has multiple threads of control, it can perform more than one task at a time. In certain situations, a single application may be required to perform several simil ...
Introduction to Object Technology
... • Takes less time to create a new thread than a process • Less time to terminate a thread than a process • Less time to switch between two threads within the same process • Since threads within the same process share memory and files, they can communicate with each other without invoking the kernel ...
... • Takes less time to create a new thread than a process • Less time to terminate a thread than a process • Less time to switch between two threads within the same process • Since threads within the same process share memory and files, they can communicate with each other without invoking the kernel ...
Hands-On Ethical Hacking and Network Defense Second Edition
... • Recycling common code and reusing technologies – Sound software engineering practices – Also introduce common points of failure • Viruses, worms, Trojans, and other attack vectors ...
... • Recycling common code and reusing technologies – Sound software engineering practices – Also introduce common points of failure • Viruses, worms, Trojans, and other attack vectors ...
9781435486096_PPT_ch09
... • Recycling common code and reusing technologies – Sound software engineering practices – Also introduce common points of failure • Viruses, worms, Trojans, and other attack vectors ...
... • Recycling common code and reusing technologies – Sound software engineering practices – Also introduce common points of failure • Viruses, worms, Trojans, and other attack vectors ...
Notes by Guydosh on Thread managment
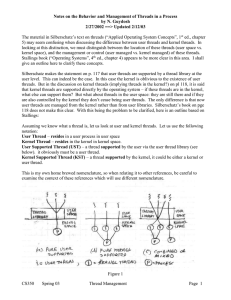
... In a “pure” UST scheme, all thread management for user threads is done by the application in user space. The kernel is oblivious to the user threads, all it sees is the user process. This is depicted in Fig. 1a. All thread support code is in the threads library in user space. The library contains co ...
... In a “pure” UST scheme, all thread management for user threads is done by the application in user space. The kernel is oblivious to the user threads, all it sees is the user process. This is depicted in Fig. 1a. All thread support code is in the threads library in user space. The library contains co ...