Notes
... • System calls provide the interface between a running program and the operating system. – For example – open input file, create output file, print message to console, terminate with error or normally – Generally available as routines written in C and C++ – Certain low-level tasks (direct hardware a ...
... • System calls provide the interface between a running program and the operating system. – For example – open input file, create output file, print message to console, terminate with error or normally – Generally available as routines written in C and C++ – Certain low-level tasks (direct hardware a ...
Remote Access—Attack Vectors
... First, the VPN transmits sensitive information over public and shared networks. The extension of the network outside the perimeter makes assets much more accessible for attackers. The hackers no longer have to breach a perimeter to find data that is sensitive. Just one remote access flaw could be su ...
... First, the VPN transmits sensitive information over public and shared networks. The extension of the network outside the perimeter makes assets much more accessible for attackers. The hackers no longer have to breach a perimeter to find data that is sensitive. Just one remote access flaw could be su ...
ch13
... Kernel Data Structures Kernel keeps state info for I/O components, including open file ...
... Kernel Data Structures Kernel keeps state info for I/O components, including open file ...
Operating Systems, 082
... Operating Systems as extended Machines The problems: Bare machine has complex structure o Processors o Many difficult-to-program devices ...
... Operating Systems as extended Machines The problems: Bare machine has complex structure o Processors o Many difficult-to-program devices ...
5_disk_scheduling
... • Swap-space — Virtual memory uses disk space as an extension of main memory • Swap-space can be carved out of the normal file system, or, more commonly, it can be in a separate disk partition • Swap-space management – 4.3BSD allocates swap space when process starts; holds text segment (the program) ...
... • Swap-space — Virtual memory uses disk space as an extension of main memory • Swap-space can be carved out of the normal file system, or, more commonly, it can be in a separate disk partition • Swap-space management – 4.3BSD allocates swap space when process starts; holds text segment (the program) ...
Operating Systems
... 1. protect applications from each other, yet 2. share physical resources between them. • Also usually want to abstract away from grungy harware, i.e. OS provides a virtual machine: – share CPU (in time) and provide each app with a virtual processor, – allocate and protect memory, and provide applica ...
... 1. protect applications from each other, yet 2. share physical resources between them. • Also usually want to abstract away from grungy harware, i.e. OS provides a virtual machine: – share CPU (in time) and provide each app with a virtual processor, – allocate and protect memory, and provide applica ...
Cafe Cracks: Attacks on Unsecured Wireless Networks
... In order to spoof an unsecured, public wireless network, the attacker must be mobile and unassuming. If the attacker is not mobile, it would be easy to find the spoofed wireless network since it would consistently occur in the same area, despite identity changes to the wireless broadcast. Also, if s ...
... In order to spoof an unsecured, public wireless network, the attacker must be mobile and unassuming. If the attacker is not mobile, it would be easy to find the spoofed wireless network since it would consistently occur in the same area, despite identity changes to the wireless broadcast. Also, if s ...
OSPP: The Kernel Abstraction
... Kernel Stacks • Per-process, located in kernel memory – There may still be a per-processor interrupt stack ...
... Kernel Stacks • Per-process, located in kernel memory – There may still be a per-processor interrupt stack ...
Introduction
... Operating Systems as extended Machines The problems: Bare machine has complex structure o Processors o Many difficult-to-program devices ...
... Operating Systems as extended Machines The problems: Bare machine has complex structure o Processors o Many difficult-to-program devices ...
doc.gold.ac.uk
... • Today’s computing – Requires comprehensive computer security plans Electronic Commerce, Tenth Edition ...
... • Today’s computing – Requires comprehensive computer security plans Electronic Commerce, Tenth Edition ...
File Management
... 4 File Management Metaphors Storage metaphors help you visualize and mentally organize the files on your disks and other storage devices ...
... 4 File Management Metaphors Storage metaphors help you visualize and mentally organize the files on your disks and other storage devices ...
Introduction to Operating Systems
... laptops, server systems, and handheld devices. – Most, if not all, current operating systems provide a user interface, job management, task management, memory management, file management, device management, and security. – There are four categories of operating systems: single-user / single-tasking, ...
... laptops, server systems, and handheld devices. – Most, if not all, current operating systems provide a user interface, job management, task management, memory management, file management, device management, and security. – There are four categories of operating systems: single-user / single-tasking, ...
WebPod: Persistent Web Browsing Sessions with
... WebPod session. This involves first authenticating the user by asking for a password. Authentication can also be done without passwords by using biometric technology in the form of built-in fingerprint readers available on some USB drives [13]. Once a user is authorized, WebPod mounts its encrypted ...
... WebPod session. This involves first authenticating the user by asking for a password. Authentication can also be done without passwords by using biometric technology in the form of built-in fingerprint readers available on some USB drives [13]. Once a user is authorized, WebPod mounts its encrypted ...
Operating Systems and File Management
... OS, Linux, Android, and iOS. Each has strengths and weaknesses that are important to understand. Which of the following statements is correct? A. iOS is built on the Windows kernel, so it is ideal for smartphones because it has good resistance to malware. B. If you don’t like the user interface ...
... OS, Linux, Android, and iOS. Each has strengths and weaknesses that are important to understand. Which of the following statements is correct? A. iOS is built on the Windows kernel, so it is ideal for smartphones because it has good resistance to malware. B. If you don’t like the user interface ...
Chapter 4 Notes
... Kernel threads - Supported by the Kernel Examples – virtually all general purpose operating systems, including: ...
... Kernel threads - Supported by the Kernel Examples – virtually all general purpose operating systems, including: ...
module_23
... – Must guarantee that whenever a process requests a resource, it does not hold any other resources. – Require process to request and be allocated all its resources before it begins execution, or allow process to request resources only when the process has none. – Low resource utilization; starvation ...
... – Must guarantee that whenever a process requests a resource, it does not hold any other resources. – Require process to request and be allocated all its resources before it begins execution, or allow process to request resources only when the process has none. – Low resource utilization; starvation ...
AIX is building momentum as the leading, UNIX operating system for
... A file system is a hierarchical structure (file tree) of files and directories. This type of structure resembles an inverted tree with the roots at the top and branches at the bottom. This file tree uses directories to organize data and programs into groups, allowing the management of several direct ...
... A file system is a hierarchical structure (file tree) of files and directories. This type of structure resembles an inverted tree with the roots at the top and branches at the bottom. This file tree uses directories to organize data and programs into groups, allowing the management of several direct ...
OS - PESIT South
... The process has arrived in the order p1, p2, p3, p4, p5 all at time 0. a. Draw Gantt charts for the execution of these processes using FCFS, SJF, a nonpreemptive priority and RR (quantum=1) scheduling. b. What is the turnaround time and waiting time of each process for each of the scheduling algorit ...
... The process has arrived in the order p1, p2, p3, p4, p5 all at time 0. a. Draw Gantt charts for the execution of these processes using FCFS, SJF, a nonpreemptive priority and RR (quantum=1) scheduling. b. What is the turnaround time and waiting time of each process for each of the scheduling algorit ...
Introduction
... Large number of small tasks Need a large amount of inter-task communication Not good for distributed system (good for Parallel system) ...
... Large number of small tasks Need a large amount of inter-task communication Not good for distributed system (good for Parallel system) ...
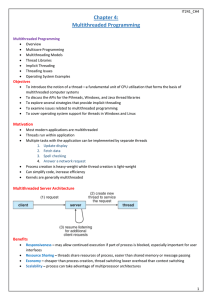
Multithreaded Programming
... To explore several strategies that provide implicit threading To examine issues related to multithreaded programming To cover operating system support for threads in Windows and Linux ...
... To explore several strategies that provide implicit threading To examine issues related to multithreaded programming To cover operating system support for threads in Windows and Linux ...
Hands-On Ethical Hacking and Network Security
... Kerberos is used on LANs for authentication Uses Tickets and Keys Used by Windows 2000, XP, and 2003 Server by default Not common on WLANS (I think) ...
... Kerberos is used on LANs for authentication Uses Tickets and Keys Used by Windows 2000, XP, and 2003 Server by default Not common on WLANS (I think) ...


![[slides] I/O systems](http://s1.studyres.com/store/data/008422726_1-2cb56c8336d4c09c42da15c554c4a466-300x300.png)